Block chain transaction monitoring method and system based on static characteristics and dynamic instrumentation
A block chain and static detection technology, applied in the field of computer security, can solve the problems of high false alarm rate of vulnerabilities, inability to detect lightning loan vulnerabilities, and inability to detect vulnerabilities, so as to reduce the detection false positive rate, improve detection accuracy, and improve The effect of detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Below in conjunction with the accompanying drawings, the present invention is further described by means of embodiments, but the scope of the present invention is not limited in any way.
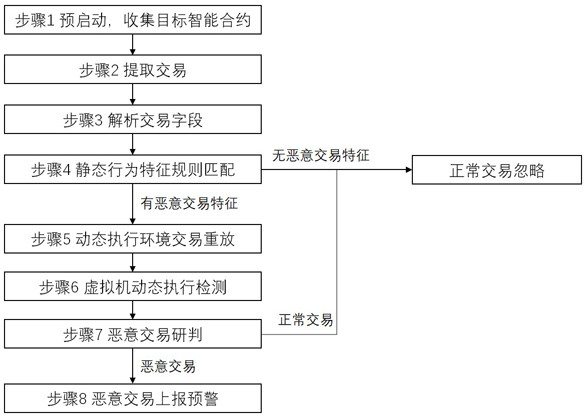
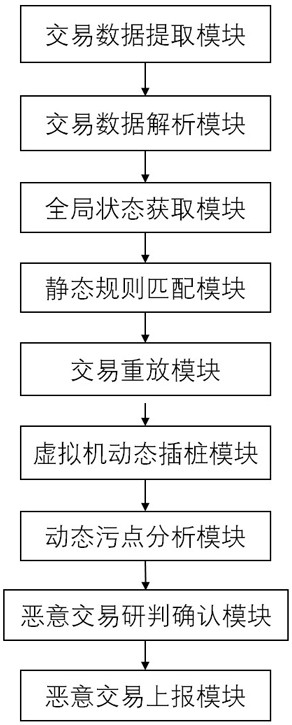
[0030] like figure 1 The flow of the blockchain transaction detection method shown, the specific implementation includes four stages:
[0031] Stage 1. Transaction data extraction and analysis stage;
[0032] Stage 2, transaction data static detection stage;
[0033] Stage 3: The dynamic execution test stage of transaction data;
[0034] The fourth stage is the transaction confirmation and reporting stage.
[0035] The first stage includes the following steps:
[0036] Step 1, run the blockchain main network node client to collect the smart contract addresses to be monitored;
[0037] Among them, the smart contract addresses to be monitored include but are not limited to:
[0038] Addresses of DeFi contract projects with large funds, such as Aave, Curve, Maker, Compound, WBTC, U...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com