Network security event traceability analysis method and device, medium and electronic equipment
A technology of network security and analysis method, which is applied in the field of devices, media and electronic equipment, and network security event traceability and analysis method, which can solve the problems such as false reporting of events, and achieve the effect of making up for false positives and the inability to trace the source globally
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
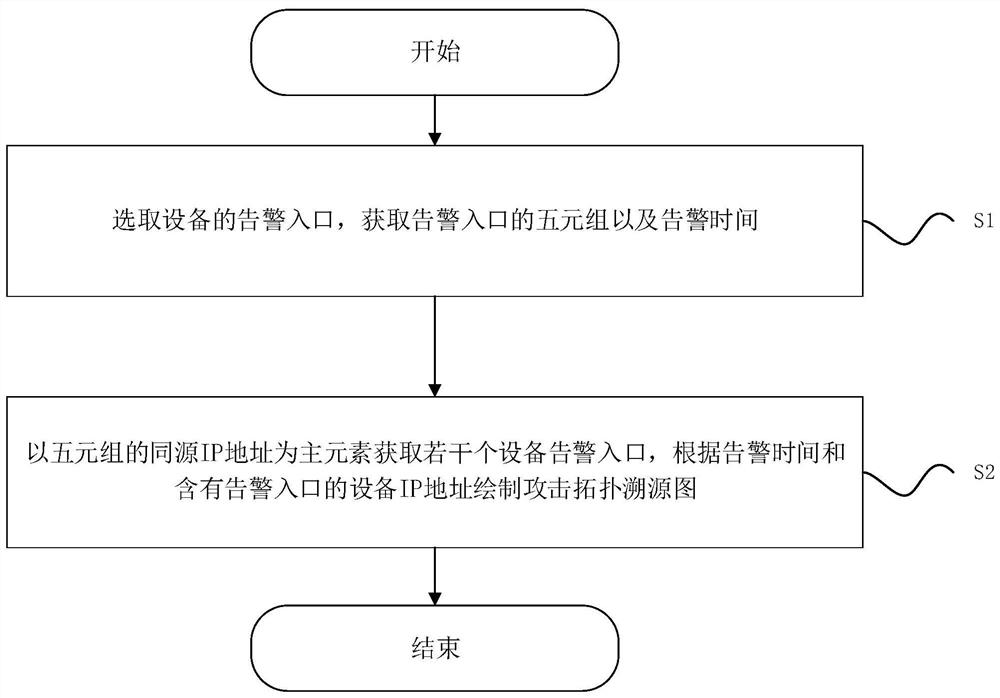
[0031] Embodiment 1 provides a network security event source tracing analysis method, such as figure 1 shown, including the following steps:
[0032] S1, select the alarm entry of the device, obtain the quintuple of the alarm entry and the alarm time;
[0033] S2. Obtain several device alarm entries with the same-source IP address of the quintuple as the main element, and draw an attack topology traceability diagram according to the alarm time and the IP address of the device containing the alarm entry.
[0034] Specifically, in S1, an alarm entry of the device is selected, and the quintuple and alarm time of the alarm entry are obtained; the quintuple includes source IP address, source port, destination IP address, destination port, and transport layer protocol.
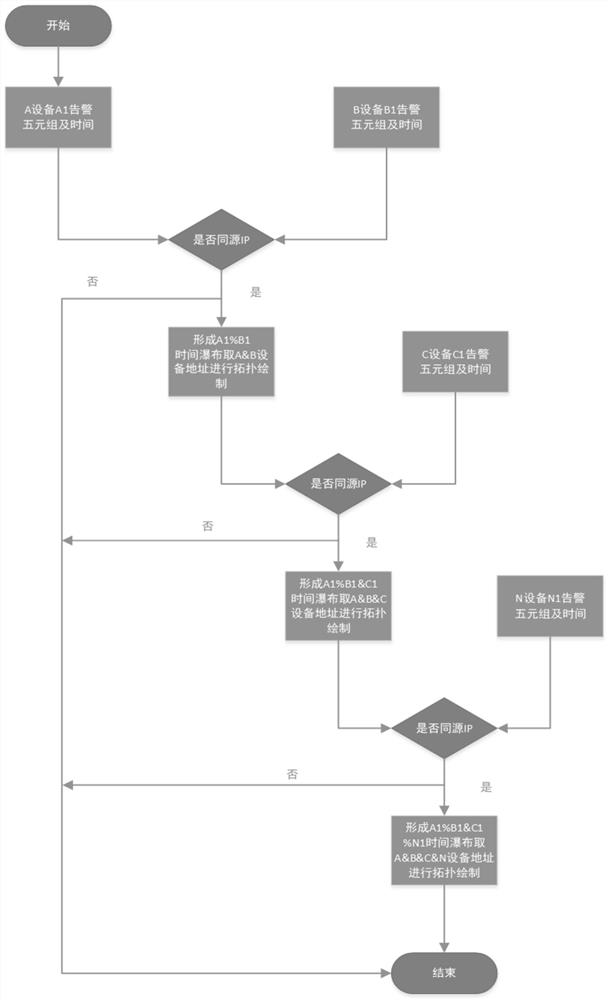
[0035] In S2, several device alarm entries are obtained with the same-source IP address of the five-tuple of the alarm entry as the main element, and an attack topology traceability map is drawn according to the al...
Embodiment 2
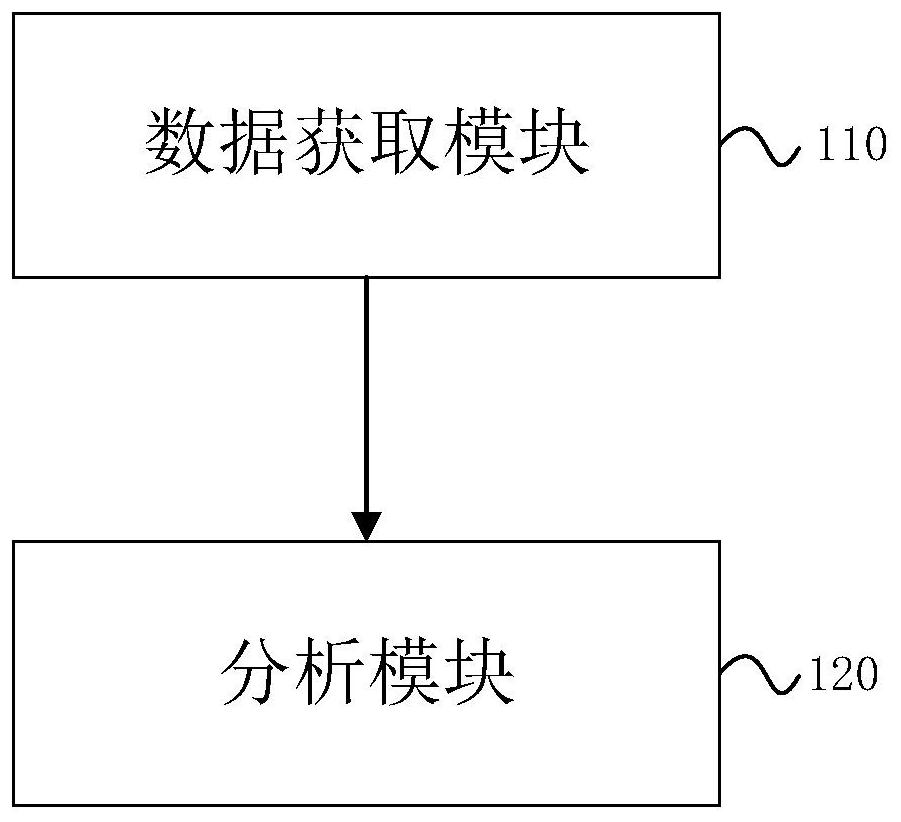
[0051] The second embodiment provides a network security event traceability analysis device, which is used to implement the specific steps of the network security event traceability analysis method described in the first embodiment, which will not be repeated here, as image 3 as shown, image 3 The frame diagram of each module of the analysis device provided by an embodiment of the present invention, the device includes the following modules,
[0052] The data acquisition module 110 is used to select the alarm entry of the device, and obtain the quintuple of the alarm entry and the alarm time;
[0053] The analysis module 120 is used to select several device alarm entries based on the same-source IP address of the quintuple, and draw an attack topology traceability diagram according to the alarm time and the device IP address.
[0054] In summary, the present invention provides a network security event traceability analysis device that collects alarm logs generated by variou...
Embodiment 3
[0056] The third embodiment provides a computer-readable storage medium, on which a computer program is stored. When the program is executed by a processor, the steps of the method for adjusting the enameled wire paint film thickness described in any one of the above contents are implemented. Those skilled in the art should understand that the embodiments of the present invention may be provided as methods, systems, or computer program products. Accordingly, the present invention can take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present invention may take the form of a computer program product embodied on one or more computer-usable storage media (including but not limited to disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein. Those of ordinary skill in the art can understand that realizing all or part of the processes i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com