Encrypted video traffic content analysis method based on sequence similarity
A sequence similarity and content analysis technology, applied in selective content distribution, image communication, electrical components, etc., can solve the problems of insufficient scalability of the recognition model and inability to handle unknown types of network flows, etc., to achieve accurate analysis results and ensure content Sexually safe, low-complexity effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present application, and are not intended to limit the present application.
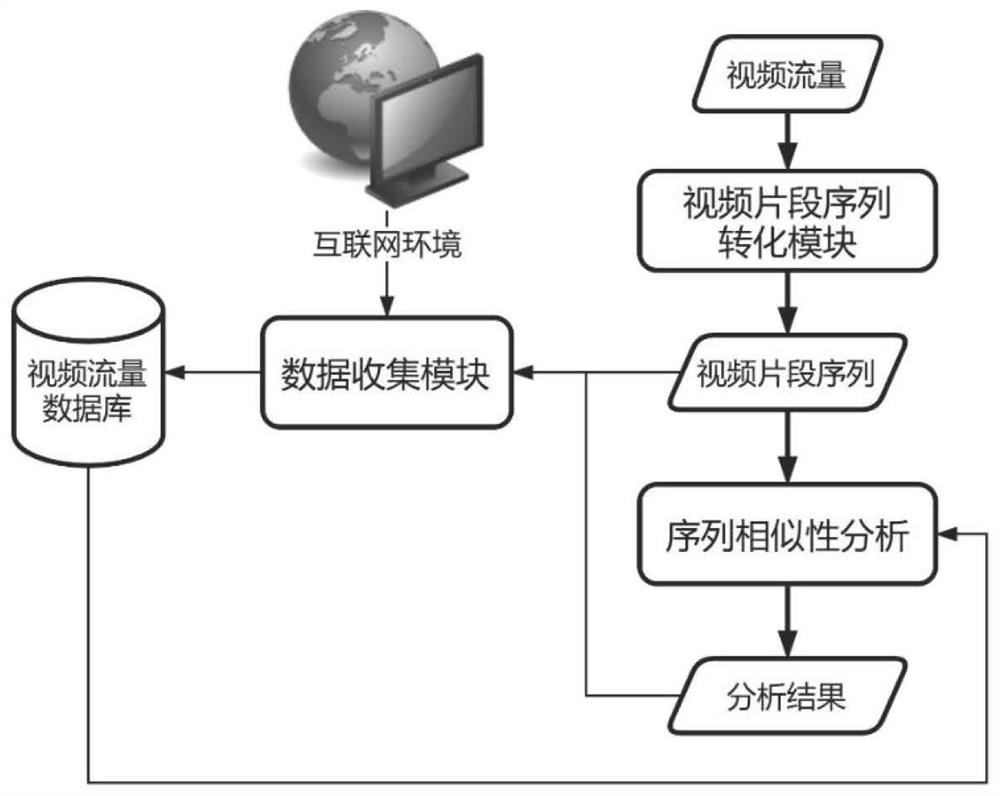
[0040] The present invention designs a method for analyzing content of encrypted video traffic based on sequence similarity, the frame diagram of the method is as follows figure 2 shown, including:
[0041] In the first step, tagged video traffic data is collected from the network and classified and managed to form a video traffic database, which contains multiple records.
[0042] In order to realize the automated collection of encrypted video traffic, it is first necessary to use automated testing technology as a support to realize automatic video playback. Automated ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap