Data compliance management and control method and system based on security capability scenarized arrangement
A technology of security capabilities and scenarios, which is applied in the field of data compliance control methods and systems based on scenario-based arrangement of security capabilities, can solve problems such as failure of protection strategies, unusable data, and inconsistent security strategies, and achieve consistency and flexibility The effect of management and deployment, and good protection performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
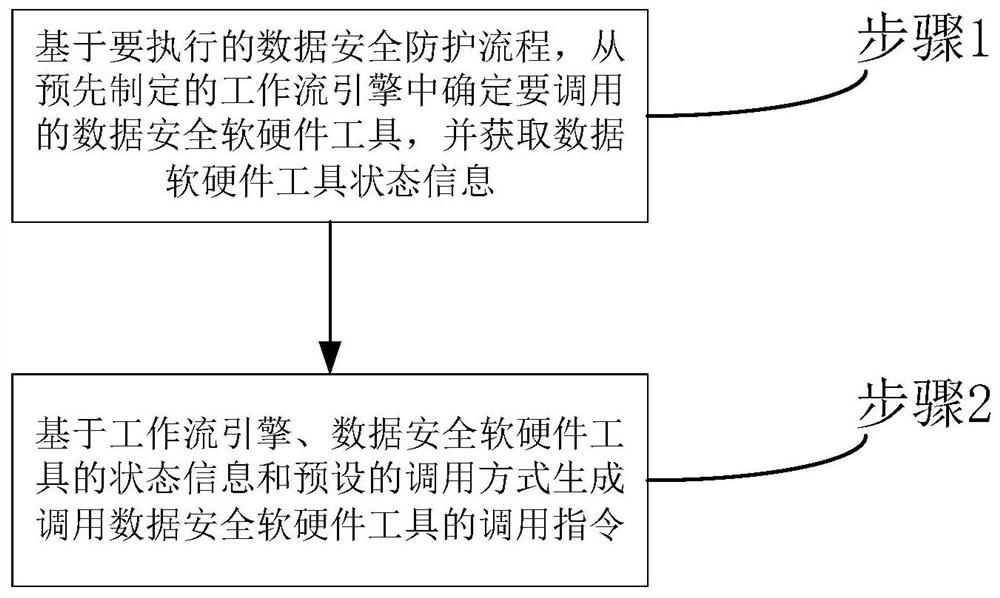
[0066] Embodiment 1: The present invention provides a data compliance management and control method based on scenario-based orchestration of security capabilities, such as figure 1 shown, including:
[0067] Step 1: Based on the data security protection process to be executed, determine the data security software and hardware tools to be called from the pre-established workflow engine, and obtain the status information of the data software and hardware tools;
[0068] Step 2: Based on the status information of the workflow engine, the data security software and hardware tools, and the preset calling method, generate a call command to call the data security software and hardware tool;
[0069] Among them, the workflow engine is obtained by using computer language to describe the security policy involved in the data security protection process, the data security software and hardware tools required by the security policy, and the cooperative relationship between the data securit...
Embodiment 2
[0090] Based on the same inventive concept, the present invention also provides a data compliance management and control system based on scenario-based orchestration of security capabilities, including: a data security capability scheduling module;
[0091] The data security capability scheduling module is used to determine the data security software and hardware tools from the pre-established workflow engine according to the data security protection process to be executed, and obtain the status information fed back by the data security software and hardware tools, and generate a call instruction;
[0092] Wherein, the workflow engine is obtained by using computer language to describe the security policy involved in the data security protection process, the data security software and hardware tools required by the security policy, and the cooperative relationship between the data security software and hardware tools.
[0093] A data compliance management and control system bas...
Embodiment 3
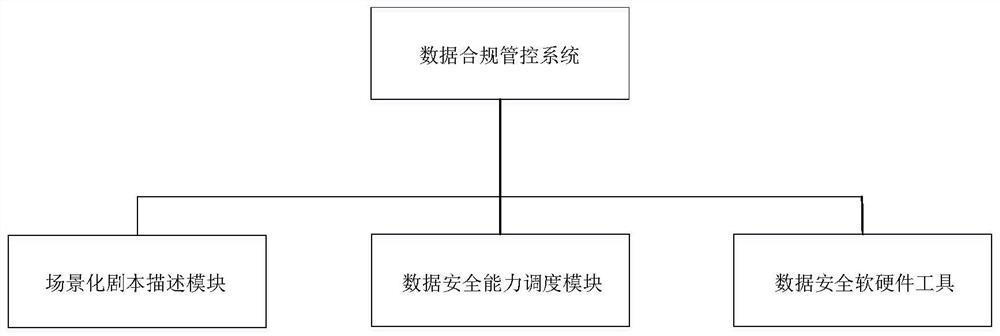
[0129] Based on the same inventive concept, the present invention also provides a data compliance management and control method based on scenario-based arrangement of security capabilities, including: the scenario-based script description module uses computer language to describe the security policies corresponding to each scenario and the data security required by the security policies. Describe the software and hardware tools, the mutual cooperation relationship between each data security software and hardware tool, and the calling method, and obtain the workflow engine corresponding to each scene, and send it to the data security scheduling module;
[0130] The data security capability scheduling module generates call instructions according to the workflow engine sent by the scenario script description module and the status information fed back by the data security software and hardware tools, and sends them to the data security software and hardware tools;
[0131] Data sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com