System and method for realizing secure cross-network access under network partition
An access system and security technology, applied in the field of secure cross-network access systems, can solve problems such as security hazards, internal information leakage, and lack of a good solution, and achieve the effect of ensuring data security, ensuring network security, and preserving convenience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
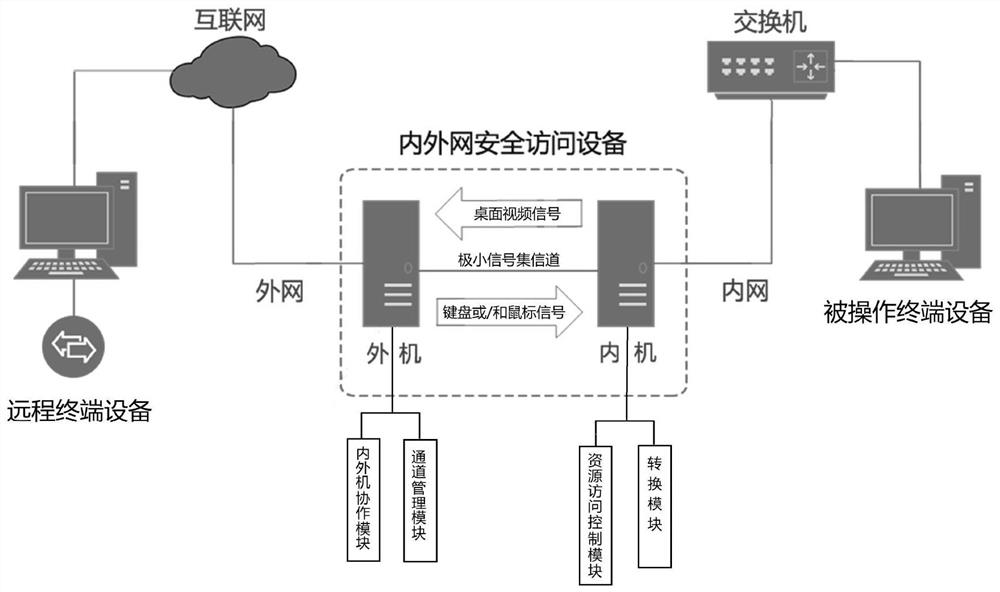
[0045] The secure cross-network access system provided by this embodiment to realize network isolation, such as figure 1 shown. It includes remote terminal equipment, internal and external network security access equipment and operated terminal equipment.
[0046] The above-mentioned internal and external network security access equipment includes an external machine and an internal machine connected through a minimum signal set channel. The external unit communicates with the remote terminal equipment through the Internet. The internal unit communicates with the operated terminal equipment through the switch.
[0047] The above-mentioned remote terminal equipment, external machine and internal machine all refer to computers, and its operating system can be Windows or UNIX. The operated terminal equipment can be computers, production equipment, monitoring equipment, etc.
[0048] The remote terminal equipment communicates with the external machine through VPN, P2P or other...
Embodiment 2
[0055] This embodiment provides a method for implementing secure cross-network access under network isolation, using the safe cross-network access system given in Embodiment 1 to operate according to the following steps:
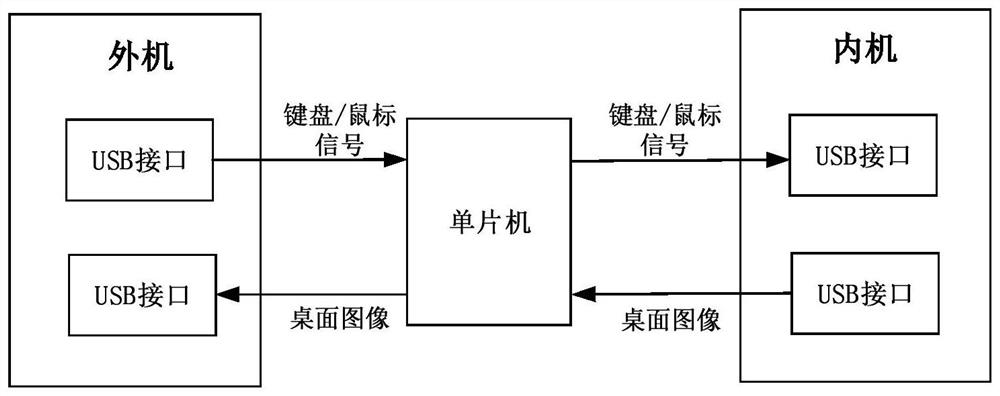
[0056] S1 The remote terminal device sends the login request of the external machine to the external machine that securely accesses the device via the Internet; after the login is successful, the external machine sends the corresponding desktop video signal to the remote terminal device of the external machine, and starts the internal and external machine cooperation module.
[0057] The login request here includes the user name and password of the external machine. When the user name and password received by the external machine are valid, the external machine operating system login is successful, and the external machine sends the corresponding desktop video signal to the remote terminal device of the external machine, and starts the internal and external m...
Embodiment 3
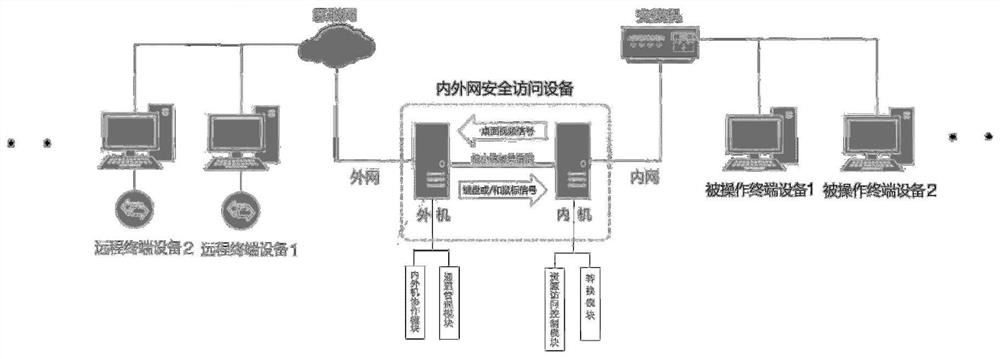
[0068] The secure cross-network access system provided by this embodiment to realize network isolation, such as image 3 shown. It includes remote terminal equipment, internal and external network security access equipment and operated terminal equipment.
[0069] Such as Figure 4 The security access equipment for the internal and external network shown above includes an external unit and an internal unit connected via a minimal signal set channel. The external unit communicates with the remote terminal equipment through the Internet. The internal unit communicates with the operated terminal equipment through the switch.
[0070] The above-mentioned remote terminal equipment, external machine and internal machine all refer to computers, and its operating system can be Windows or UNIX. The operated terminal equipment can be computers, production equipment, monitoring equipment, etc.
[0071] The remote terminal equipment communicates with the external machine through VPN,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com