Byzantine fault-tolerant method and device with high fault-tolerant expandability and storage medium
A Byzantine, consensus technology, applied in the field of devices and storage media, Byzantine fault tolerance method, can solve the problem of not being able to guarantee decentralization and democratization, achieve fault tolerance and scalability improvement, reduce communication complexity, improve The effect of scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
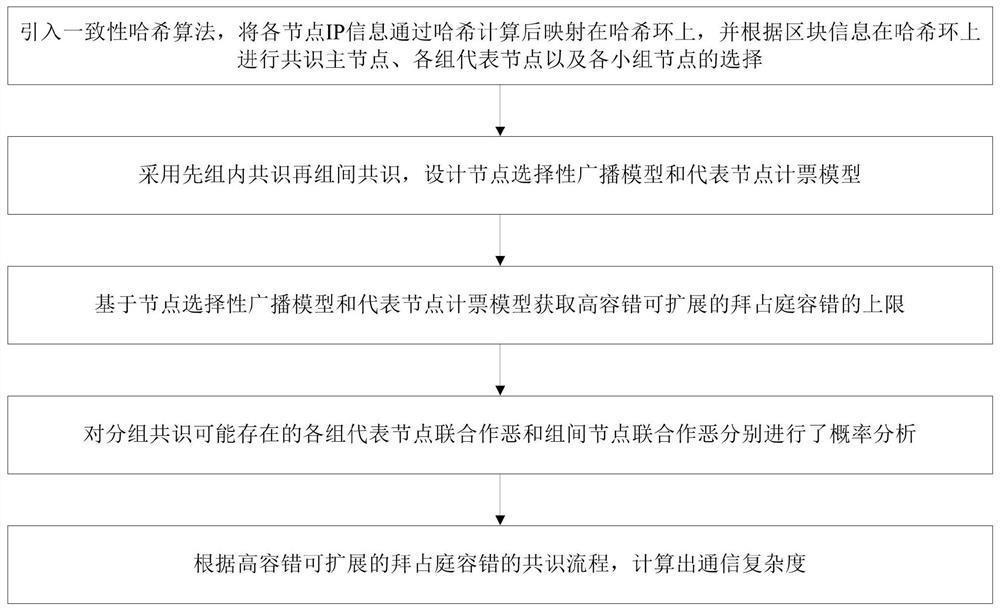
[0048] The embodiment of the present invention provides a Byzantine fault tolerance method with high fault tolerance and scalability, see figure 1 and figure 2 , the method includes the following steps:
[0049] Step 101: Introduce a consistent hash algorithm, map the IP information of each node on the hash ring after hash calculation, and carry out consensus on the hash ring according to the block information master node, each group representative node and each group node s Choice;
[0050] The embodiment of the present invention makes the selection of consensus nodes not require a centralized mechanism through the above-mentioned design, and hides the identity of the nodes in advance to achieve the purpose of restraining the nodes from doing evil.
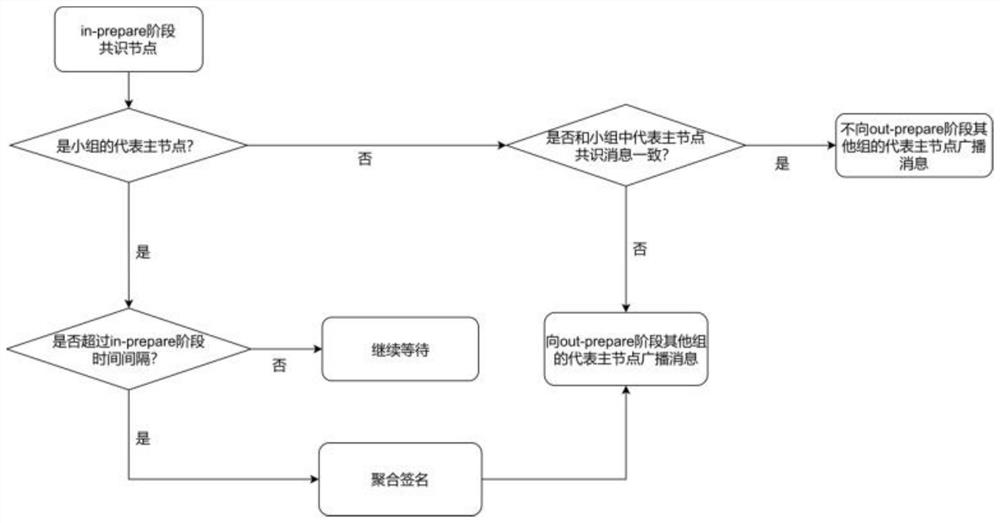
[0051]Step 102: Design the node selective broadcast model and the representative node vote counting model by adopting the consensus within the group first and then the consensus between the groups;
[0052] Among them, the co...
Embodiment 2
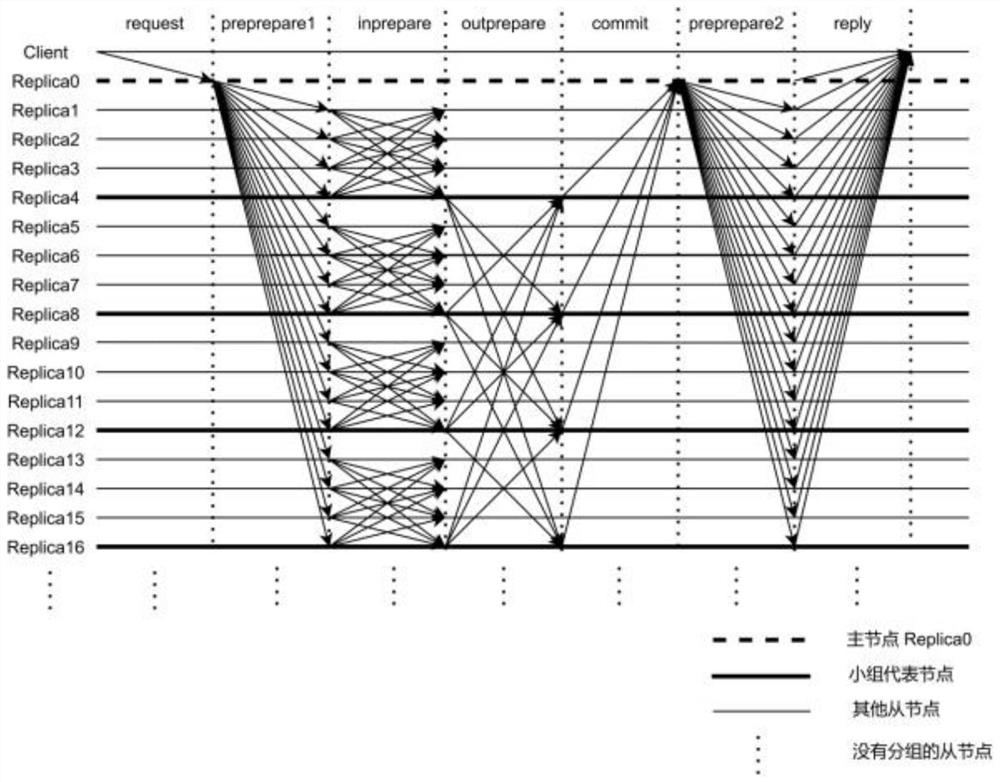
[0063] Combine below Figure 2-Figure 6 The scheme in Example 1 is further introduced, see the following description for details:
[0064] Step 201: Introduce the consistent hash algorithm, map the IP information of each node on the hash ring after hash calculation, and carry out consensus on the hash ring according to the block information. Selection: In order to ensure the anonymity and decentralization of consensus nodes, the embodiment of the present invention adopts a consistent hash algorithm for grouping, selection of representative nodes, and selection of master nodes. Each node according to hash (node ip ) to calculate its own hash value (where node ip Represents the node IP), because the consistent hash algorithm has anti-collision and balanced decentralization. Therefore, the mapping values of each node can be distributed as evenly as possible between 0 and 2 32 on the hash ring. In each round of consensus, first according to hash(master ip +previous hash +...
Embodiment 3
[0094] Combine below Figure 7 The scheme in embodiment 1 and 2 is carried out feasibility verification, see the following description for details:
[0095] Introduce the FND model (faulty number determined model) and combine the two models established to simulate the consensus experiment. When m=4, experiments were carried out when the network size was 101, 201, and 301. In the experiment, Byzantine nodes were randomly assigned to each group independently of each other, and the change of the system consensus success rate with the number of Byzantine nodes in the network was analyzed. . Under each number of Byzantine nodes, 200 simulation experiments were carried out, and the number of consensus successes was counted to obtain the consensus success rate.
[0096] The final experimental results are as Figure 7 As shown, it can be seen that the upper limit of fault tolerance does exceed 1 / 3. When the number of Byzantine nodes is less than 1 / 3 of the number of network nodes,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com