Fax encryption method and device based on national secret algorithm, equipment and medium
A technology of national secret algorithm and encryption method, applied in equipment and media, fax encryption method and device field based on national secret algorithm, can solve the problems of national and social loss, endangering national security, information being easily leaked, tampering and counterfeiting, etc. , to achieve the effect of data security assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] This embodiment provides a fax encryption method based on the national-reliente algorithm (ie the national commercial cryptographic algorithm), using key distribution technology, threshold key sharing technology, and security packet packaging technology, and can be transmitted for the fax data. Provide safe protection, improve transmission security and reliability, where:
[0050] (1) Key distribution
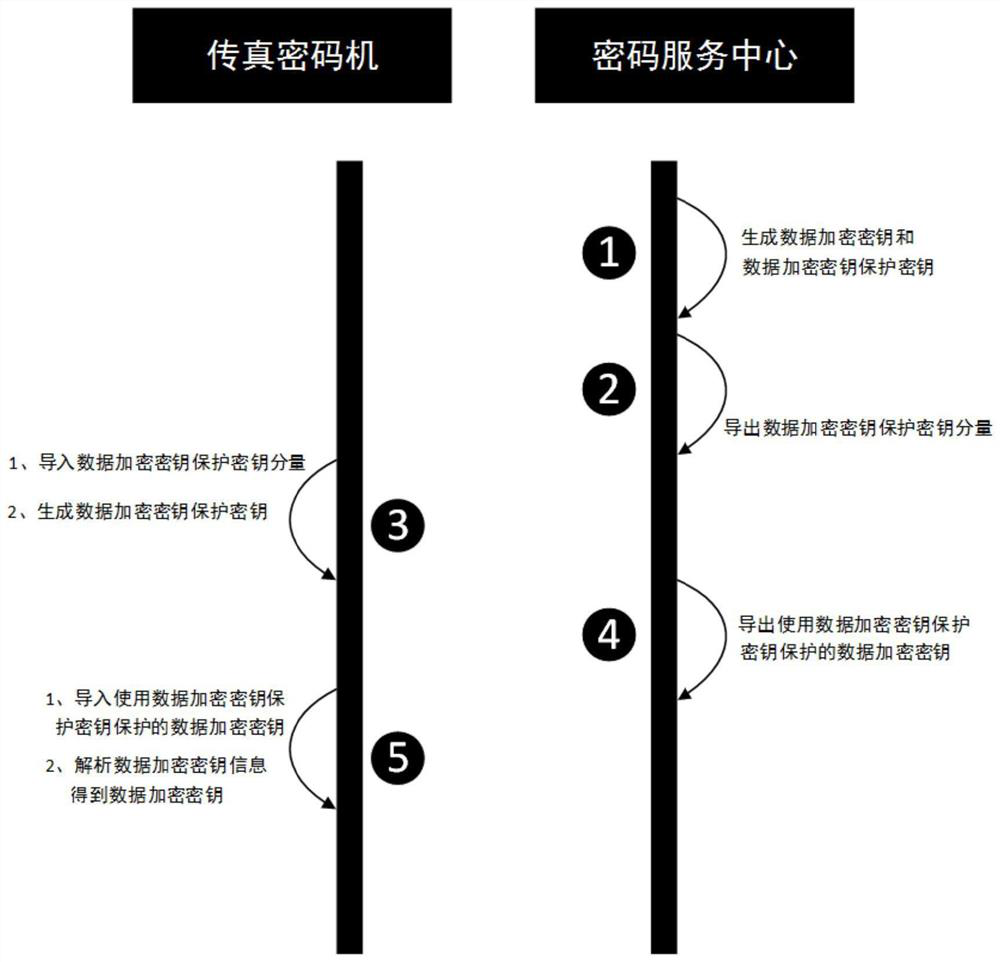
[0051] This embodiment loads the fax data symmetric password operation key by UKEY offline. figure 1 As shown, the key distribution includes the following steps:
[0052] S101. Key Management Center Generates Data Encryption Key and Data Encryption Key Protection Key;
[0053] S102. Export data encryption key protection key components;
[0054] S103. Import the data encryption key protection key to the facsimile cryptography;
[0055] S104. Use Ukey Export Data Encryption Key Protection Using Data Encryption Key Protection Key Protection in the Key Management Center to UKEY;...
Embodiment 2
[0088] Based on the embodiment 1:
[0089] This embodiment provides a fax encryption device based on national integral algorithm, including:
[0090] The key distribution module is used to load the fax data symmetrical password computing key by UKEY offline.
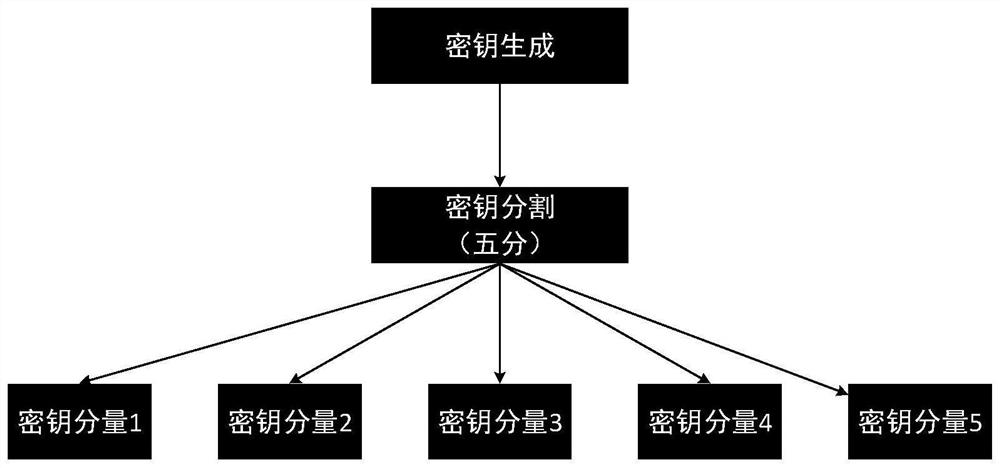
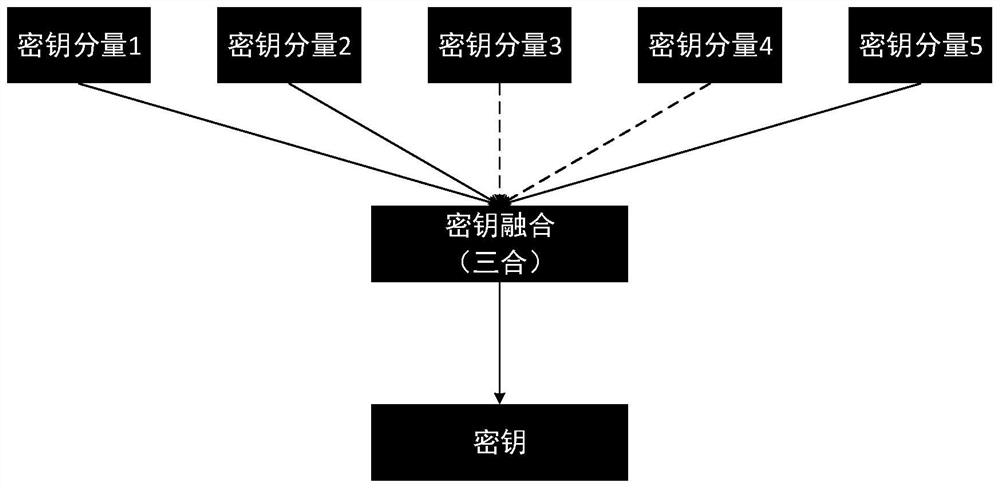
[0091] The threshold key module is used to post the data encryption key protection key of the key service center to the facsimile cryptography via the threshold key sharing technology;
[0092] The security packet package module is used to use the national commercial cryptographic algorithm for safe addition / decryption transmission of the fax data. Use the national commercial password SM1 symmetric cryptographic algorithm to add / decrypt the data. Use the national commercial password SM3 summary password algorithm to complete the data. Sexual verification.
[0093] Specifically, the fax encryption device is deployed between the facsimile and the PSTN line in the application environment, and the specific deployment method ...
Embodiment 3
[0095] Based on the embodiment 1:
[0096] This embodiment provides a computer device, including a memory and a processor, which stores a computer program that implements the step of implementing the fax encryption method based on the English-based algorithm of Embodiment 1 when the computer program performs the computer program. The computer program can be a source code form, an object code form, an executable file, or some intermediate form.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com