Complex structure data automatic encryption and decryption method and system
A technology of encryption and decryption and complex structure, which is applied in the direction of digital data protection, etc., to achieve the effect of reducing later maintenance costs and reducing the amount of code modification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
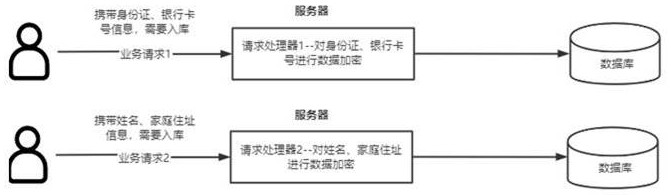
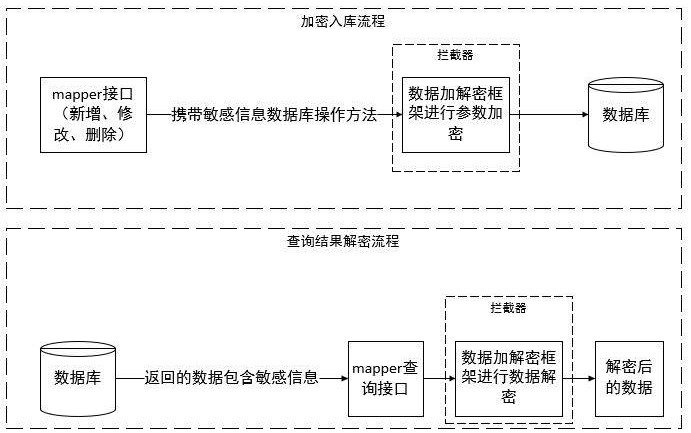
[0064] In one embodiment, in order to overcome the problems existing in the prior art, an automatic encryption and decryption method for complex structure data is proposed, and the method of uniformly processing all database operations carrying sensitive information is referred to as the mapper method. This method builds data security The encryption and decryption framework, according to the actual application requirements, uses the data security encryption and decryption framework to encrypt or decrypt the received data.
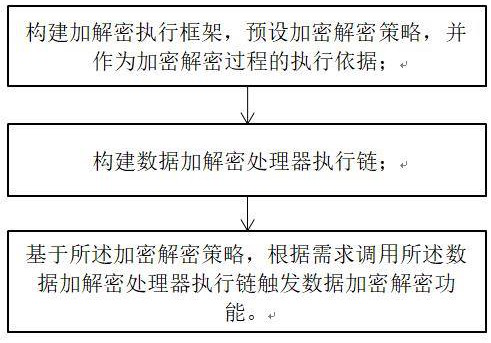
[0065] Specifically, such as image 3 As shown, a complex structure data automatic encryption and decryption method includes the following steps:
[0066] Step 1. Construct the encryption and decryption execution framework, and preset the encryption and decryption strategy, and use it as the basis for the execution of the encryption and decryption process;
[0067] Step 2. Construct the data encryption and decryption processor execution chain;
[0068] St...
Embodiment 2
[0072] In a further embodiment based on Embodiment 1, the implementation process of encryption includes:
[0073] a. Trigger the corresponding parameter encryption processor according to the data received by the data security encryption and decryption framework;
[0074] b. Execute the parameter encryption processor to obtain the encryption parameters, and call the execution chain of the data encryption and decryption processor to trigger the data encryption and decryption processor to perform data encryption;
[0075] c. Store the encrypted data in the database.
[0076] In a further embodiment, when the automatic encryption process obtains the data received by the data security encryption and decryption framework, it first stores the data through the constructed cache center; secondly, loads the metadata information of the data stored in the cache center and triggers parameter encryption The processor parses the parameters that need to be encrypted; then, the execution chai...
Embodiment 3
[0108] In a further embodiment based on the first embodiment, the implementation process of decryption includes:
[0109] a. Read the data to be decrypted in the database and trigger the corresponding result parser;
[0110] b. The execution result parser obtains the decryption field, and calls the data encryption and decryption processor to execute the chain to decrypt the data;
[0111] c. Output the decrypted data.
[0112] In a further embodiment, when the result parser obtains the decrypted field, if the required data information cannot be loaded, the obtained data is parsed through the reflection mechanism, and the parsing result is stored in the cache center for use as the next Metadata for one read.
[0113] In a further embodiment, a result parsing factory is constructed to generate a result parser object. In the process of triggering the result parser to parse the parameters that need to be decrypted, if it fails to load into the corresponding result parser, creat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com