Computer-implemented method and system for securely identifying disconnected objects and their location
A technology of disconnection and safe identification, which is applied in the direction of safety devices, safety communication devices, transmission systems, etc., and can solve problems such as system exposure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
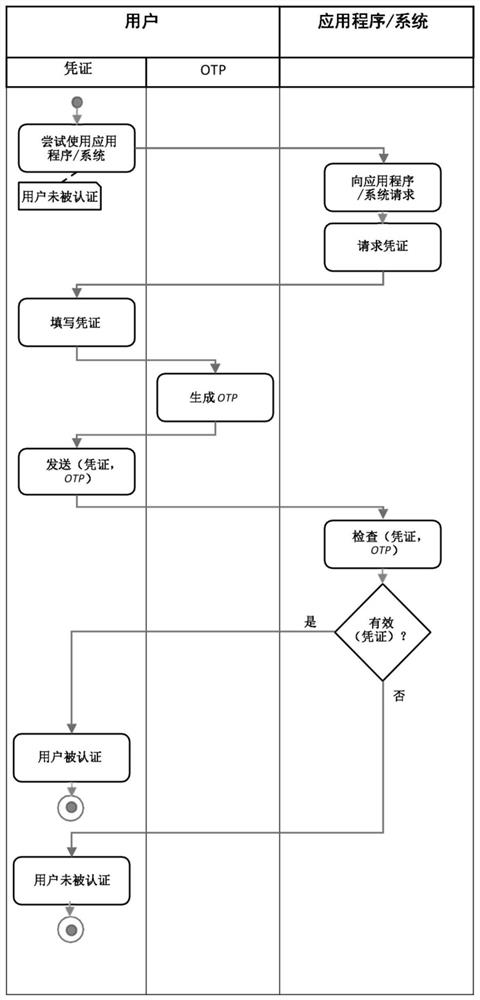
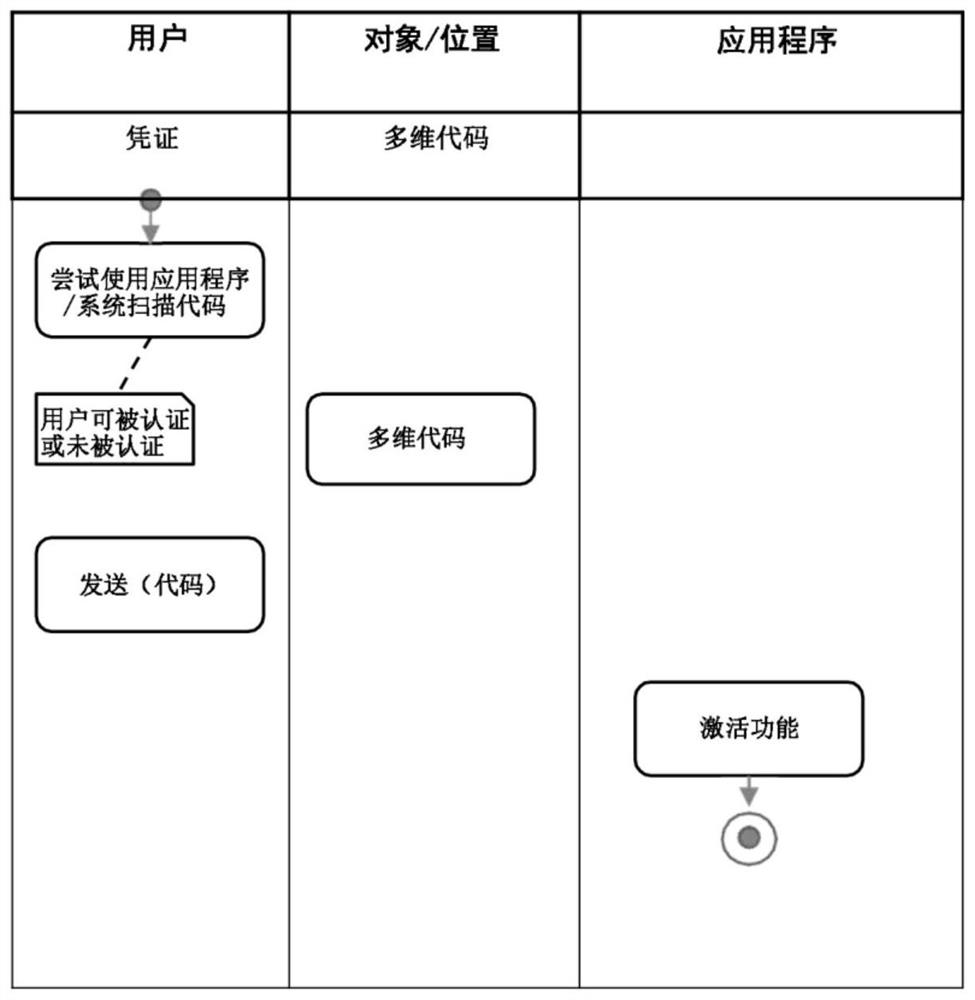
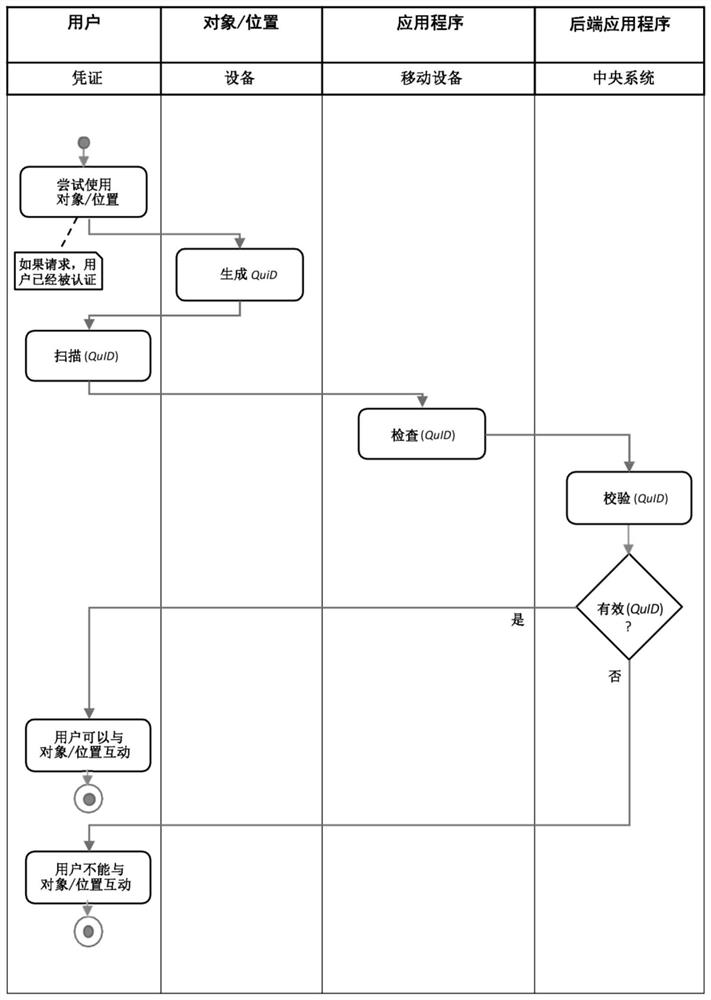
[0078] Generally speaking, the present disclosure describes a computer-implemented method and system for identifying and authenticating a device to a central system using one-time password (OTP), especially using a one-time-based graphic code (preferably a two-dimensional code or similar code). The computer-implemented method can identify the device and locate the device in a specific place.
[0079] The device is configured to generate a one-time-based graphic code that at least partially includes device attributes. Attributes of devices can include, but are not limited to, hardware feature ID or system attributes, device settings (both software and hardware).
[0080] Generally speaking, device attributes are usually device-specific and cannot be copied on another device.
[0081] The system according to the present invention includes a device, a central system, and a mobile device. The device is physically connected to an object in a precise location or is usually placed in a s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com