Reverse analysis method for executable binary file format
A binary file, reverse analysis technology, applied in the field of reverse analysis of executable binary file format, can solve problems such as increasing the difficulty of reverse engineering, unable to directly implement reverse analysis of executable binary files, etc., to reduce dependencies, strong practicability, application wide range of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
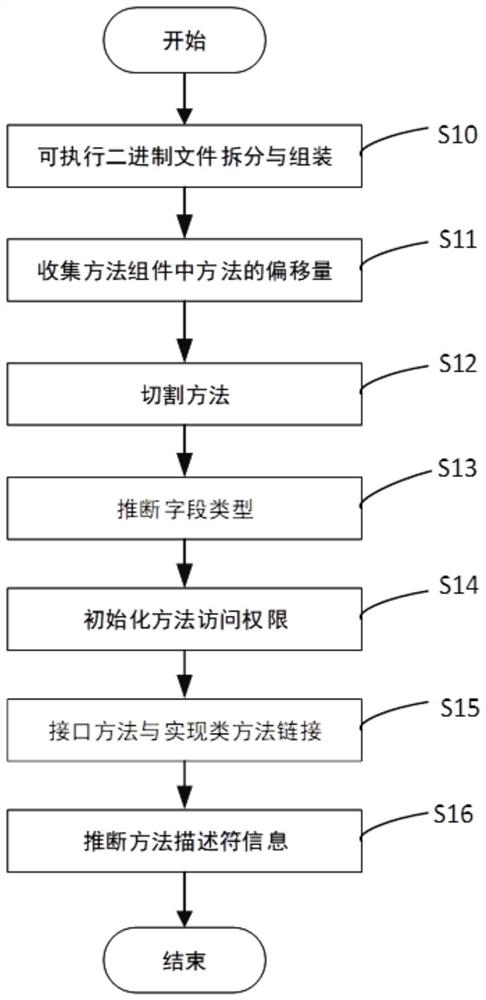
[0054] as Figure 1 As shown, the present invention discloses a reversed analysis method of performing binary file formats, comprising the following steps:
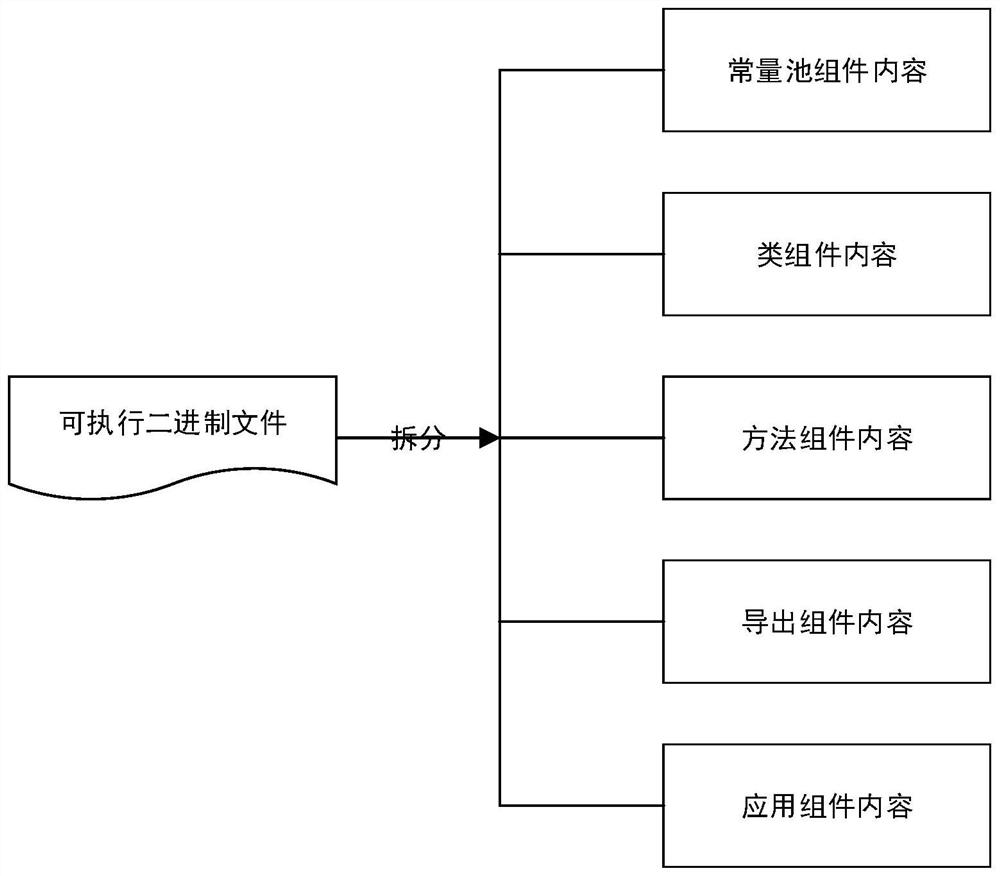
[0055] S10, the executable binary content is obtained by streaming, split according to its file structure, and reencapsulated into component content.
[0056] asFigure 2 as shown, recapsulating the executable binary content into constant pool component content, class component content, method component content, export component content, and app component content.
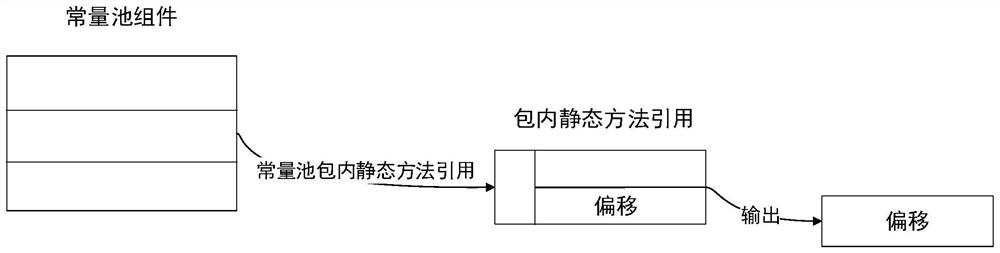
[0057] S11, collect the method offset contained in the method component in the component content, and form a list of method offsets.
[0058] The size and starting offset of each method are not stated in the Method component, and the method offset contained in the Method component is collected, and the method size is calculated from adjacent offsets.
[0059] as Figure 3 As shown, offsets are obtained from references in the constant pool component that describe the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com