Network access method, device and terminal
A network access and network technology, applied in the field of communications, can solve problems such as the terminal's long time to search the network, and achieve the effects of reducing air interface signaling, saving network resources, and shortening the duration.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0063] Embodiment 1: The first information is disaster identification information.
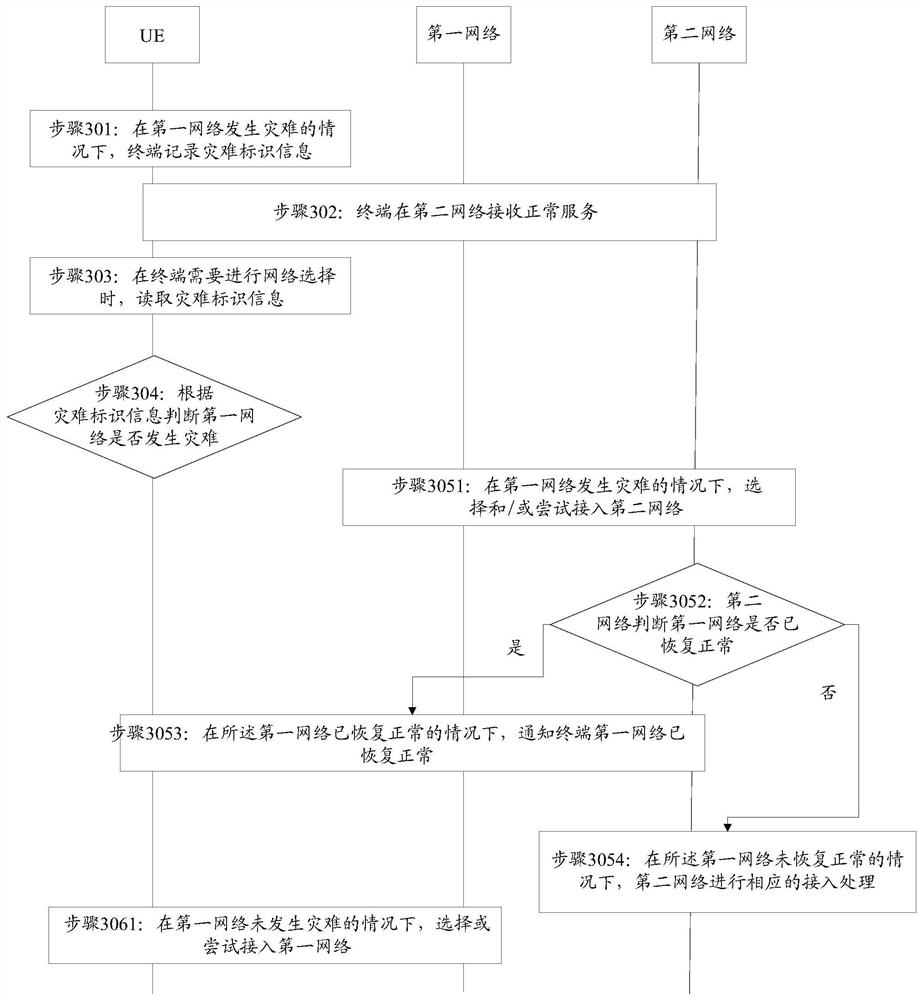
[0064] like image 3 As shown, the network access method of the present application includes:
[0065] Step 301: In the case of a disaster in the first network, the terminal records the disaster identification information.
[0066] Here, if the UE learns from the network side that the first network is back to normal, the terminal updates the disaster identification information or deletes the disaster identification information.
[0067] Step 302: The terminal receives normal services in the second network.
[0068] Step 303: When the terminal needs to select a network, read the disaster identification information.
[0069] For example, the disaster identification information is read when the system is powered on, or after the coverage area is restored, or when the background searches and selects the network.
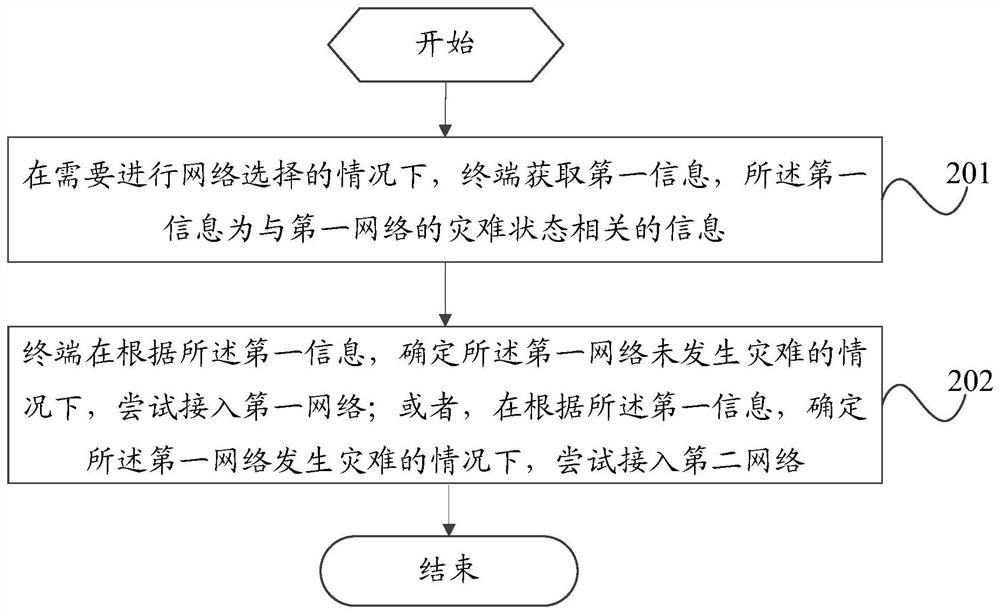
[0070] Step 304: Determine whether a disaster has occurred in the first network ...
Embodiment 2
[0102]Embodiment 2: The first information is the time duration or the running state of the timer.
[0103] like Figure 4 As shown, the network access method includes:
[0104] Step 401: In the case of network selection, determine whether the timer has timed out. In the case that the above-mentioned timer has timed out, go to step 4021, and / or 4022, and / or 4023, and in the case that the above-mentioned timer has not timed out, go to step 4031, and / or 4032.
[0105] Step 4021: When the timer expires, obtain disaster state information of the first network from the network, and the disaster state information indicates that the first network is back to normal.
[0106] If the disaster information indicates that the first network has not recovered to normal, it is considered that the first network is still in disaster, and an attempt is made to access the second network.
[0107] Step 4022: Determine that the first network is back to normal.
[0108] Step 4023: Attempt to acces...
Embodiment 3
[0122] Embodiment 3: The first information is a first location range, and the first location range is a location range where a disaster occurs in the first network.
[0123] like Figure 5 As shown, the network access method includes:
[0124] Step 501: Acquire the location range where the disaster occurs in the first network.
[0125] Optionally, the first network or the second network sends, through signaling, the effective location range of the disaster in the first network, such as which TA areas, which latitude and longitude locations, and which satellite coverage areas.
[0126] Alternatively, the UE estimates the location information through other means, for example, the location information obtained through satellite or Wireless Local Area Network (WLAN), or estimates the location information from the air interface information of the first network or the second network, for example, according to the first network The TA information in the registration success message...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com