Network penetration method and device, electronic equipment and storage medium
A technology of network penetration and equipment, applied in the field of computer network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
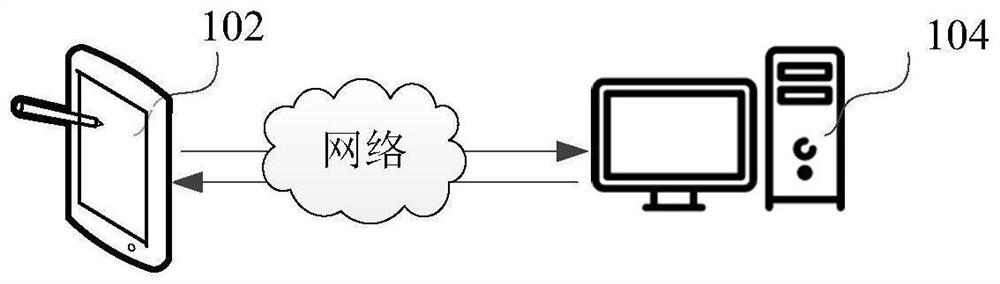
[0038] The network penetration method provided by this application can be applied to such as figure 1 in the application environment shown. The network penetration method is applied to a network penetration device. The network penetration device may be configured on the terminal 102 or the server 104, or partially configured on the terminal 102 and partially configured on the server 104, and the terminal 102 interacts with the server 104 to complete the network penetration method.
[0039] Wherein, the terminal 102 and the server 104 can communicate through the network.
[0040] The terminal 102 can be, but is not limited to, various personal computers, notebook computers, smart phones, tablet computers and portable wearable devices. The terminal 102 needs to have the functions of receiving, viewing, editing, and sharing the shared 3D model scene. The server 104 can It can be implemented with an independent server or a server cluster composed of multiple servers.
[0041] I...
Embodiment 2
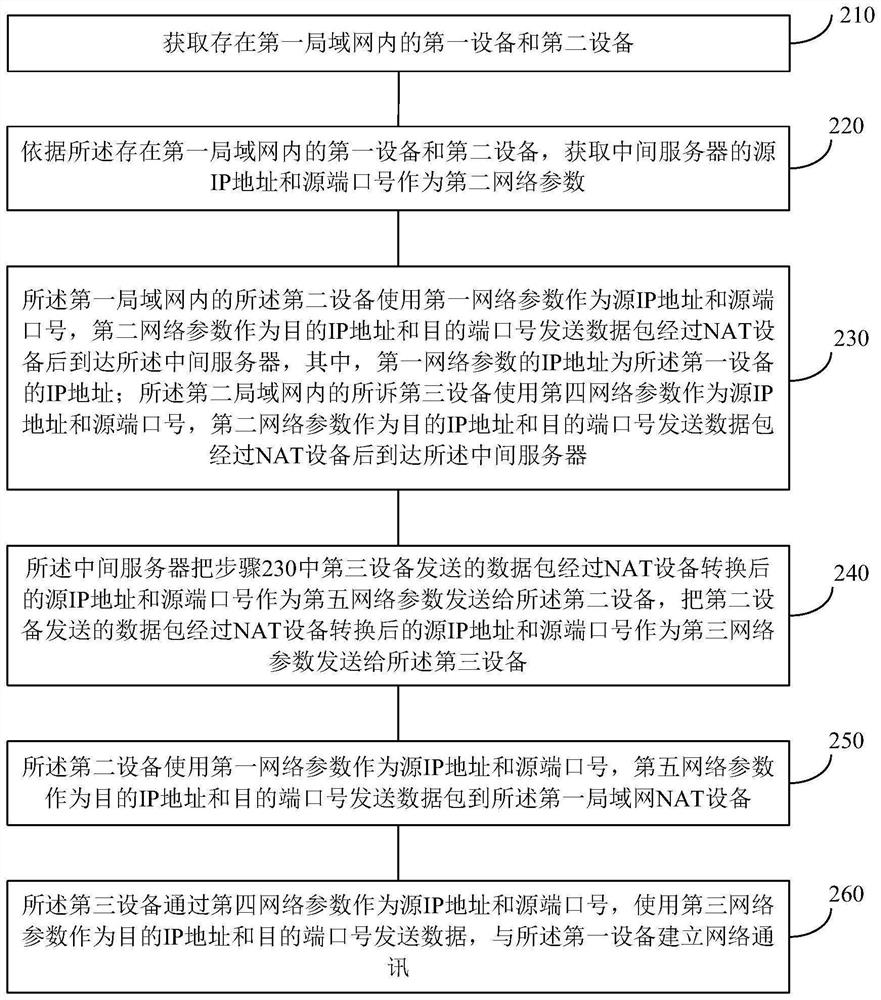
[0048] like figure 2 As shown, the network penetration method includes:
[0049] Step 210: Obtain the first device and the second device existing in the first local area network;
[0050] Step 220: According to the first device and the second device existing in the first local area network, obtain the source IP address and source port number of the intermediate server as the second network parameter.
[0051] Step 230: The second device in the first local area network uses the first network parameters as the source IP address and the source port number, and the second network parameters as the destination IP address and the destination port number to send data packets through the NAT device to reach the destination. The intermediate server, wherein the IP address of the first network parameter is the IP address of the first device; the third device in the second local area network uses the fourth network parameter as the source IP address and source port number, and the seco...
Embodiment 3
[0058] In one embodiment, an electronic device is provided, the electronic device may be a terminal, and its internal structure diagram may be as follows Figure 4 shown. The electronic device includes a processor, a memory, a communication interface, a display screen, and an input device connected by a system bus. Among them, the processor of the electronic device is used to provide computing and control capabilities. The memory of the electronic device includes a non-volatile storage medium and an internal memory. The nonvolatile storage medium stores an operating system and a computer program. The internal memory provides an environment for the execution of the operating system and computer programs in the non-volatile storage medium. The communication interface of the electronic device is used for wired or wireless communication with an external terminal, and the wireless communication can be realized by WIFI, operator network, near field communication (NFC) or other te...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap