Super-threshold multi-party privacy set intersection method based on oblivious pseudo-random secret sharing
A technology of secret sharing and multi-party privacy, applied in the field of intersection of multi-party privacy sets beyond the threshold, it can solve problems such as inability to complete efficiently, and achieve the effect of optimal computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
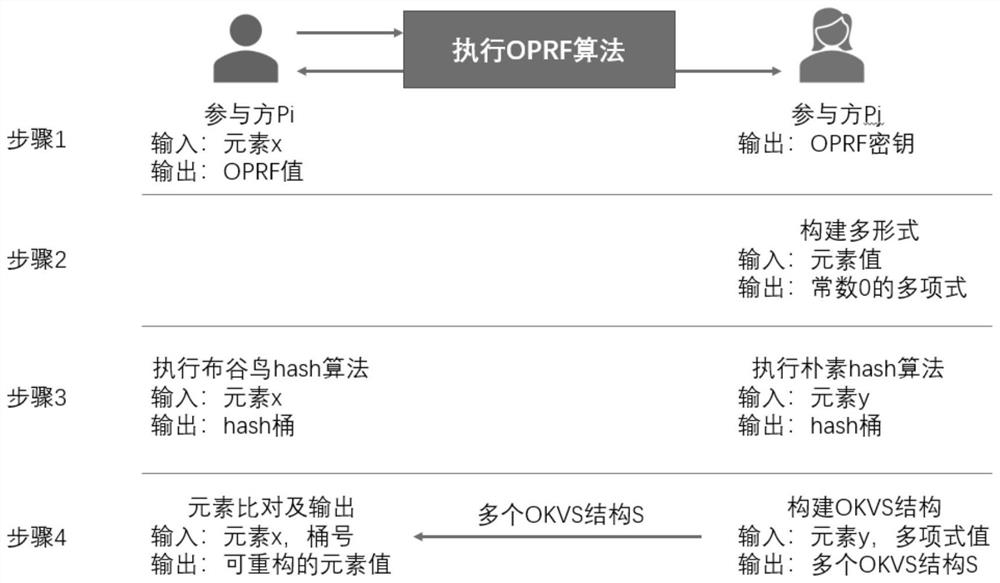
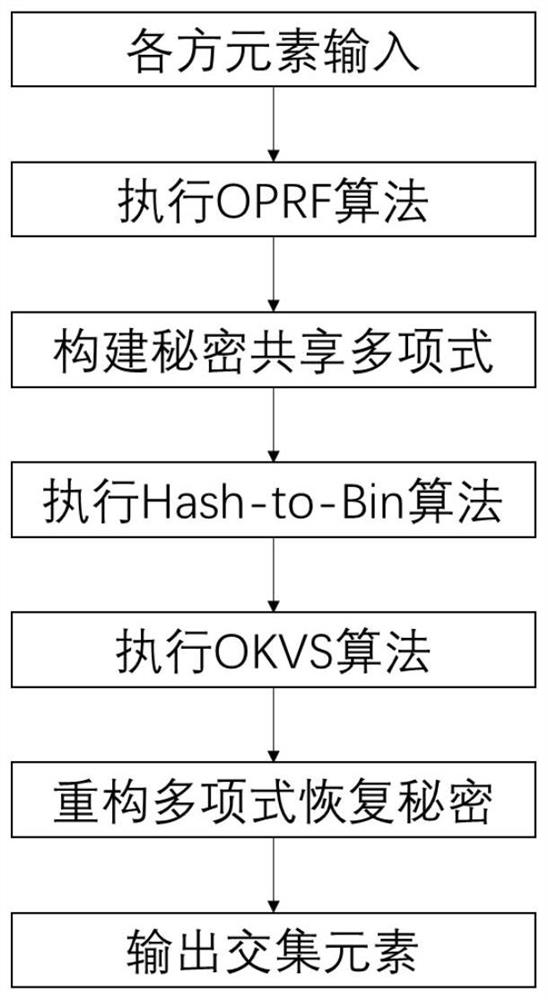
[0049] like figure 1 , 3 As shown in the figure, a method for intersection of super-threshold multi-party privacy sets based on inadvertent pseudo-random secret sharing, based on OPPRF components and SS components, design inadvertently programmable pseudo-random secret sharing (OPPR-SS) protocol, the protocol structure is as follows:
[0050] Parameters: sender S, owns set Y: {y 1 ,...,y n }. The receiver R, owns the element x. OPRF function, OKVS function: F k ( ), j∈[1,n]
[0051] Input: The receiver inputs element x.
[0052] Inadvertently programmable pseudo-random secret sharing protocol, abbreviated as OPPR-SS protocol in English.
[0053] Design an inadvertently programmable pseudorandom secret sharing (OPPR-SS) protocol, including the following stages:
[0054] S1.OPRF stage:
[0055] The receiver R and the sender S execute an OPRF function:
[0056] S11. The receiver outputs the OPRF value: F k (x);
[0057] S12. The sender outputs the OPRF function key: k...
Embodiment 2
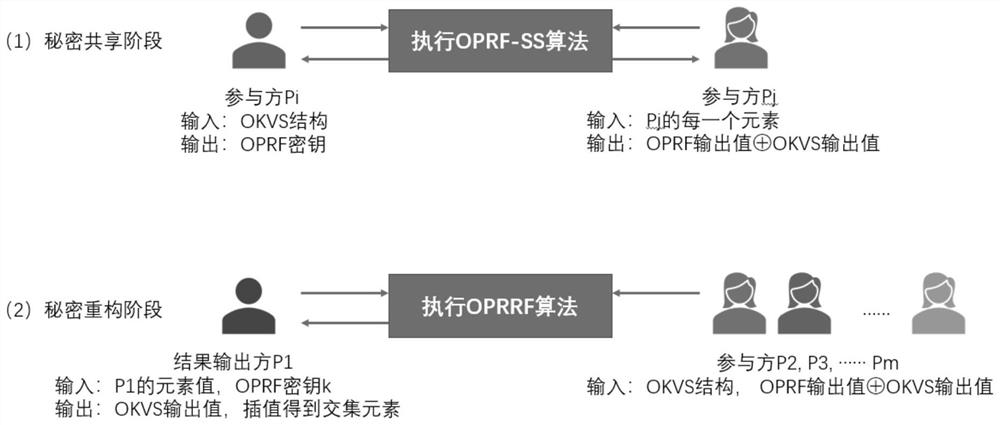
[0074] like figure 2 , 3 As shown, the OT-MP-PSI protocol can be easily constructed through the OPPR-SS component, and this embodiment can be implemented by simply constructing the technology of the present invention. The OT-MP-PSI protocol provided by this embodiment can be divided into two stages :
[0075] (1) Shared generation stage: Participants execute the OPPR-SS protocol in pairs: Suppose P i (i∈m) is the sender, P j (j∈m) is the receiver. sender P i Randomly generate t-1 random numbers for each element in its set, which are used to construct a polynomial P with a constant term of t order 0 to achieve element-wise secret shared value generation for all participants. Participant P j input collection element Participant P i Enter OKVS (k∈n,k i,j for the participant P i with P j key selected when implementing the OPPR-SS protocol). Participant P j output where m is the number of participants and n is the set size.
[0076] (2) Reconstruction stage: Par...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com