Location privacy protection method based on virtual trajectory generation mechanism
A technology of virtual trajectory and generation mechanism, applied in location-based services, security devices, electrical components, etc., can solve the problems of inaccurate results, leakage of mobile user location privacy, large computing overhead, etc., to achieve short time and guaranteed experience Level, the effect of protecting location privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
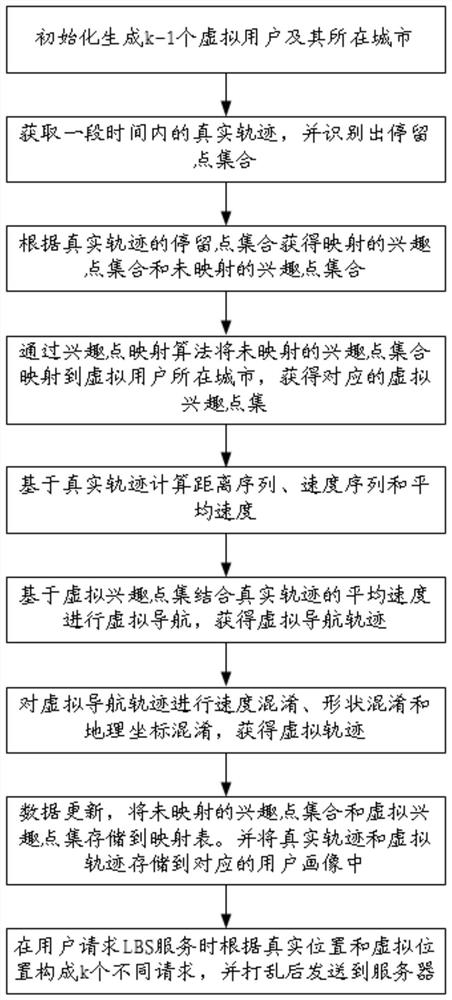
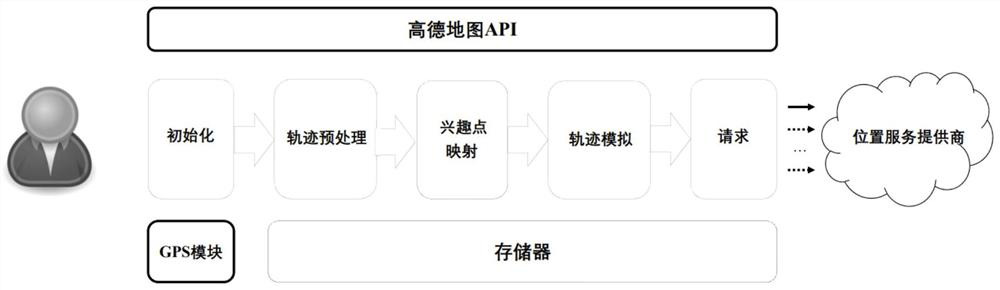
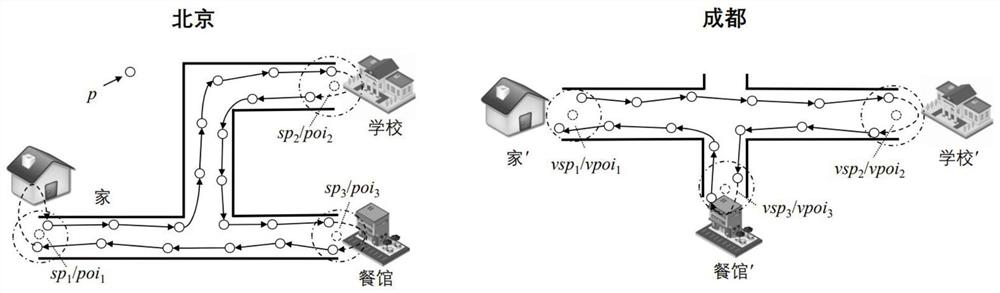
[0060] like Figure 1 to Figure 3 As shown in the figure, the location privacy protection method based on the virtual trajectory generation mechanism is configured on the mobile terminal used by the user, and uses the AutoNavi map APP as the map data base, including client initialization, trajectory preprocessing, interest point mapping, trajectory simulation, customer There are five main processes such as client request query. The specific process is as follows:
[0061] Client initialization
[0062] Step S10, initialize and generate k-1 virtual users and their corresponding cities; when the client system just starts running, the user selects k-1 different cities {city 1 , city 2 ,…,city k-1 }, used to represent the cities where k-1 virtual users are located. At the same time, users can choose to import their own historical tracks, or they can choose not to import them. This embodiment mainly introduces the case where the user chooses not to import.
[0063] Trajector...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com