Computer information protection method and device
A computer and control device technology, applied in the field of computer information protection, can solve the problems of not making full use of BIOS, etc., and achieve the effects of avoiding theft of user data, high security, and convenient and quick use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
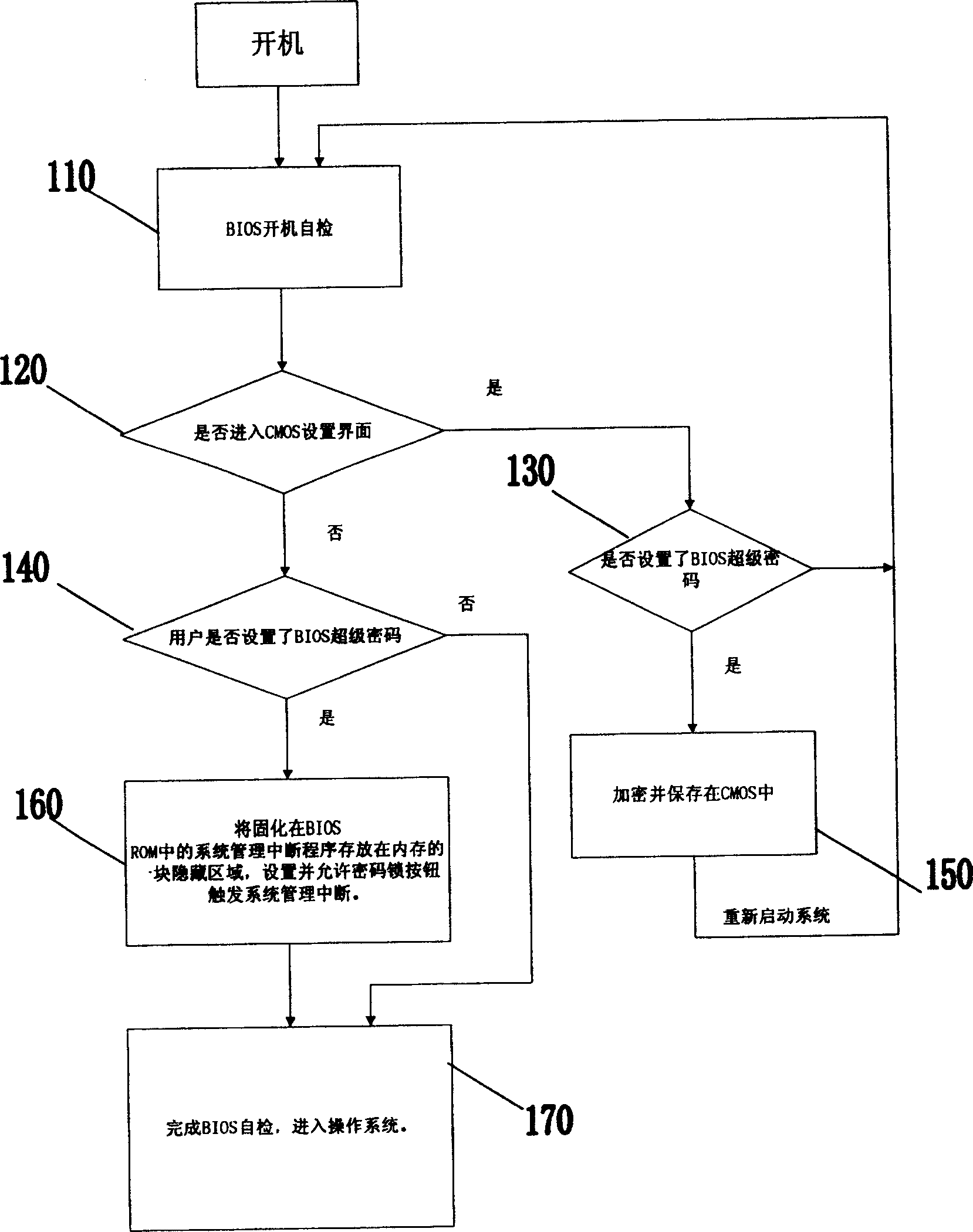
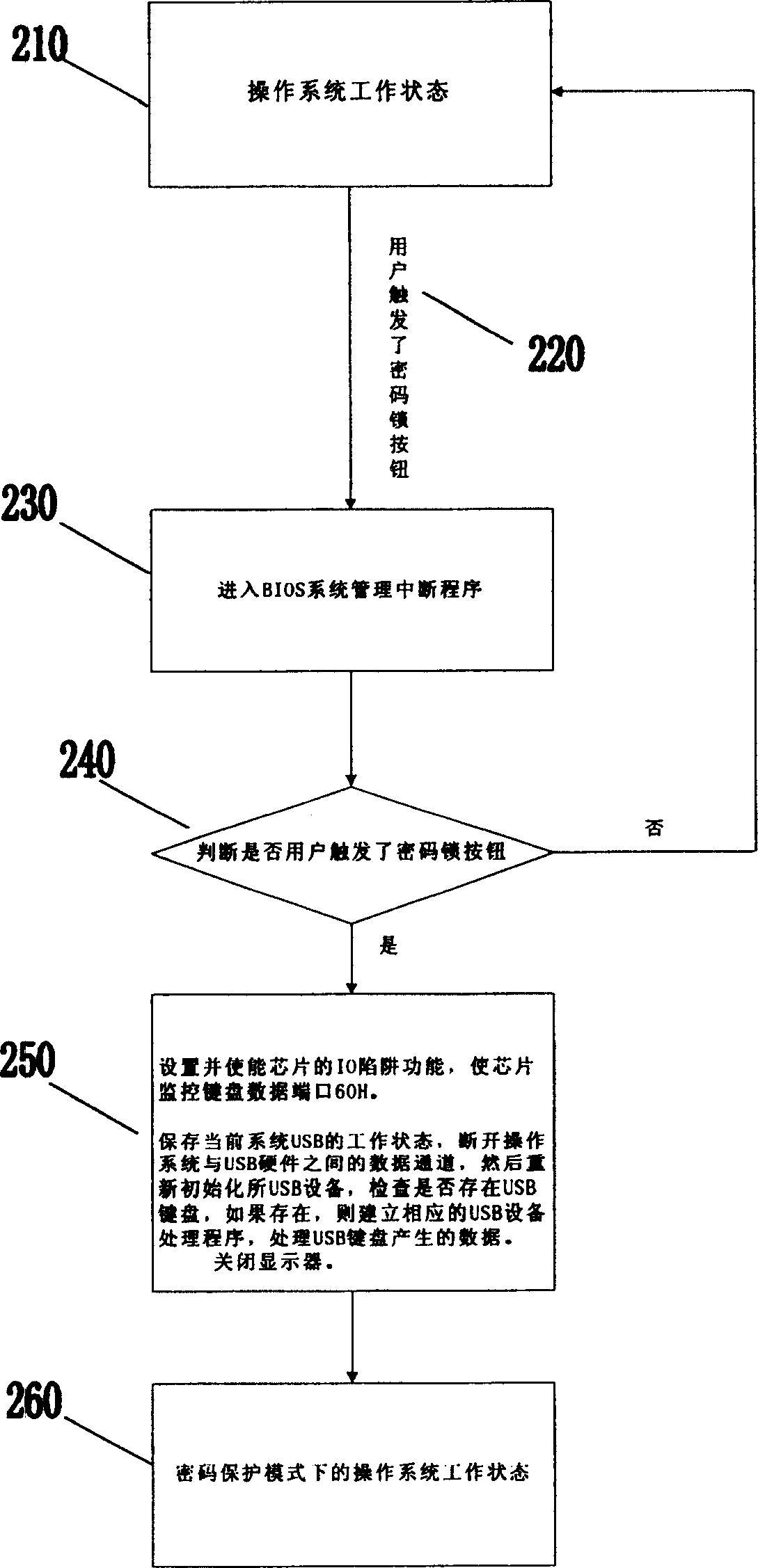
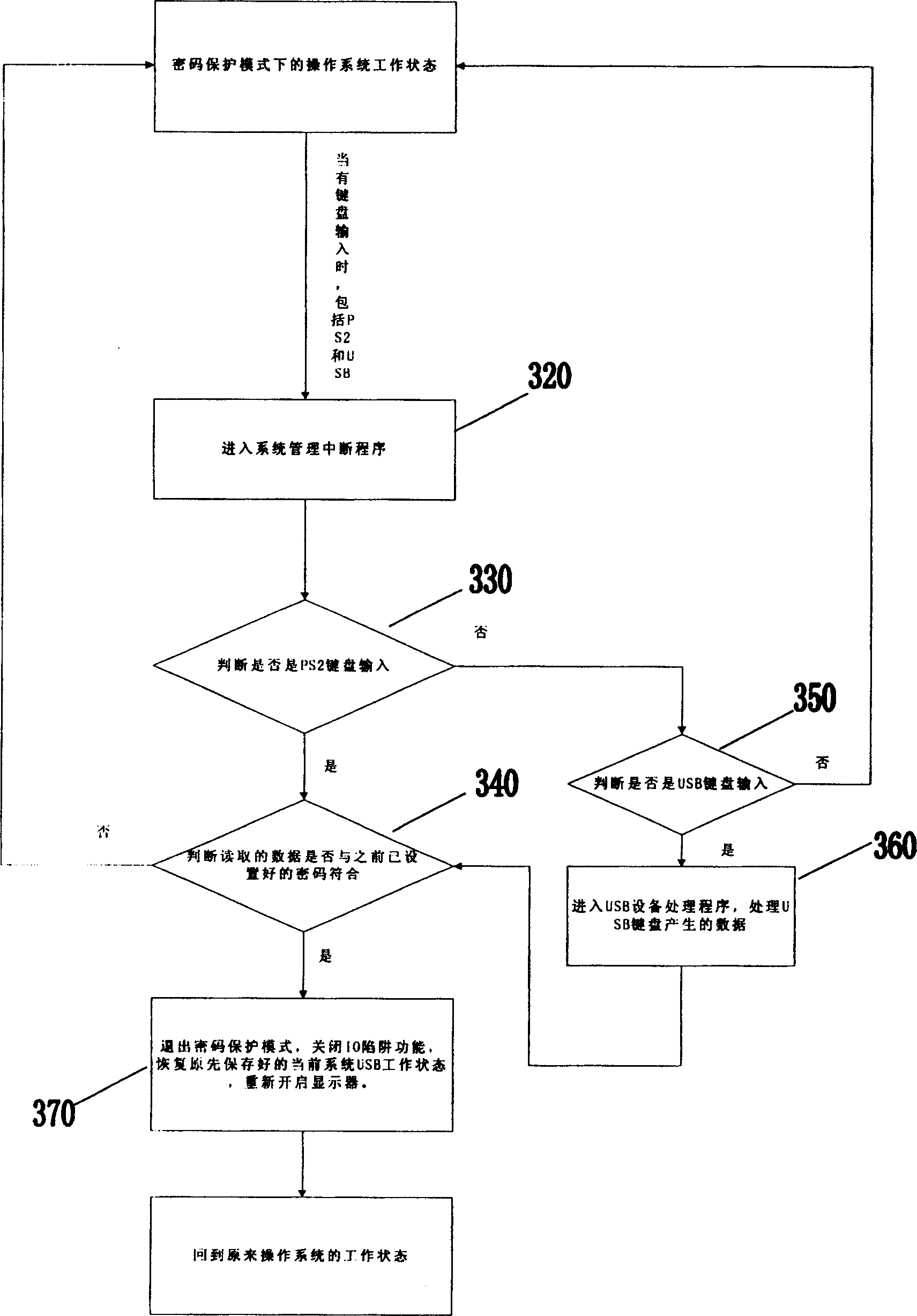
[0036] The current PC system chip has the I / O trap function, which can detect the I / O operation on the current PC system bus. When the I / O operation on the bus meets its set requirements, this function can be realized. The I / O operation is intercepted, and a system management interrupt is triggered, and the result of the I / O operation is determined by the system management interrupt program. Such as: realize the actual operation result of this I / O. Cut off the operation of the I / O to invalidate the operation of the I / O.
[0037] Working principle of the present invention utilizes these I / O trap functions exactly, by the setting of I / O trap function, after corresponding register fills in the I / O port value that needs interception, then enable its system management to interrupt, like this, Once there is an I / O port access operation that meets the settings on the system bus, the chip will intercept the I / O operation and prevent it from being passed down (executed), and at the sa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com