Method and apparatus for secure distribution of public/private key pairs
A secret key and public key technology, applied in the field of cryptography, can solve problems such as the difficulty of using the hand-delivery distribution system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
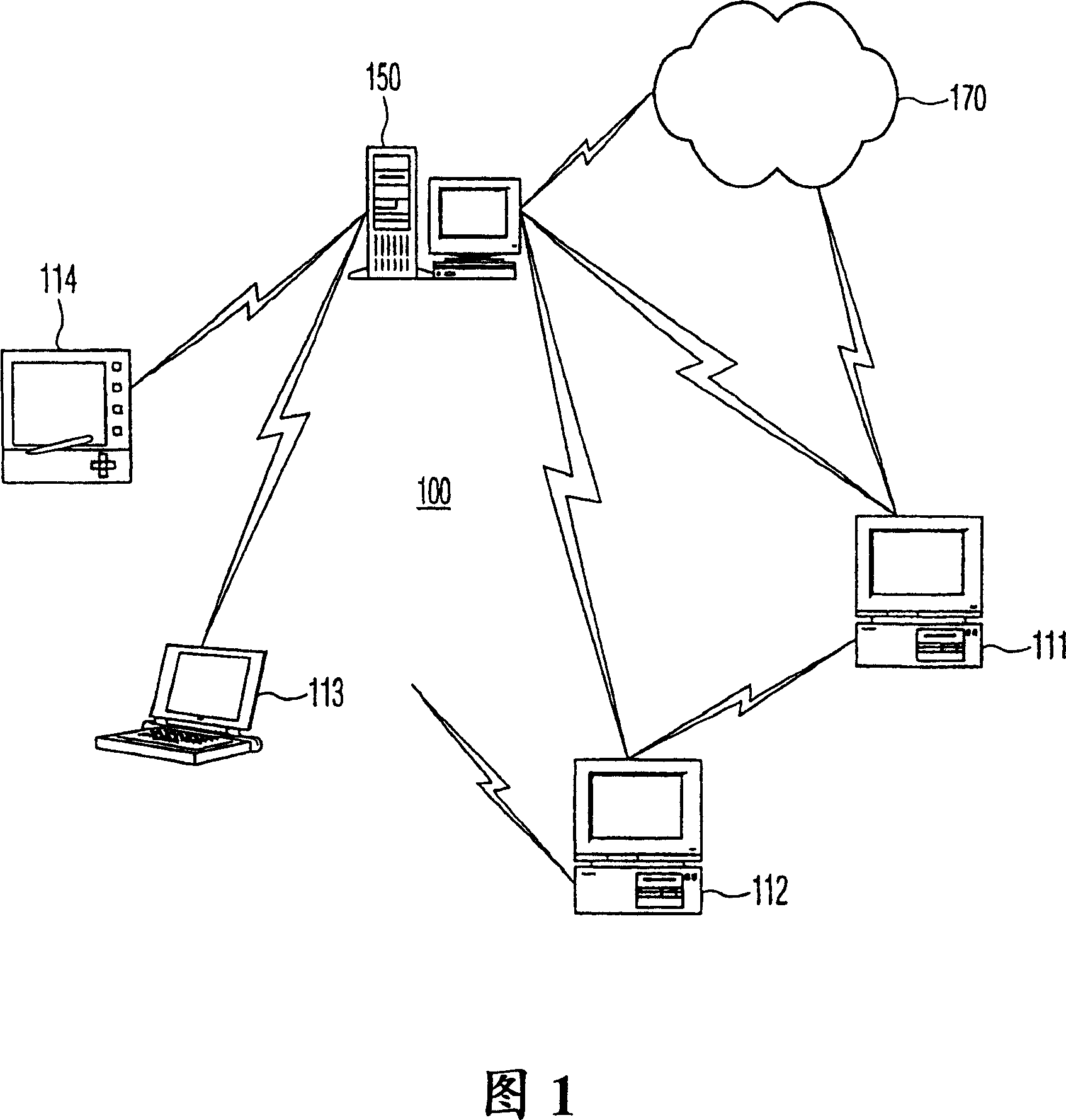
[0019] FIG. 1 depicts a network system 100 including a server processor 150 and client processors 111-114. Various client processors 111 - 114 are in communication with server processor 150 and may communicate with each other and with other network 170 . The network system 100 may be a local area network, a home control network, a private network, a public network such as the Internet, or the like. Client-server networks have significant advantages especially with regard to resource utilization. For ease of understanding, the following uses the corporate network as an example of a network system. As new members join the company, consider adding new users to the corporate network. As described above, the administrator routinely generates a public / secret key pair for the new employee on the secure processor and hands the new employee a floppy disk containing the assigned public / secret key pair.
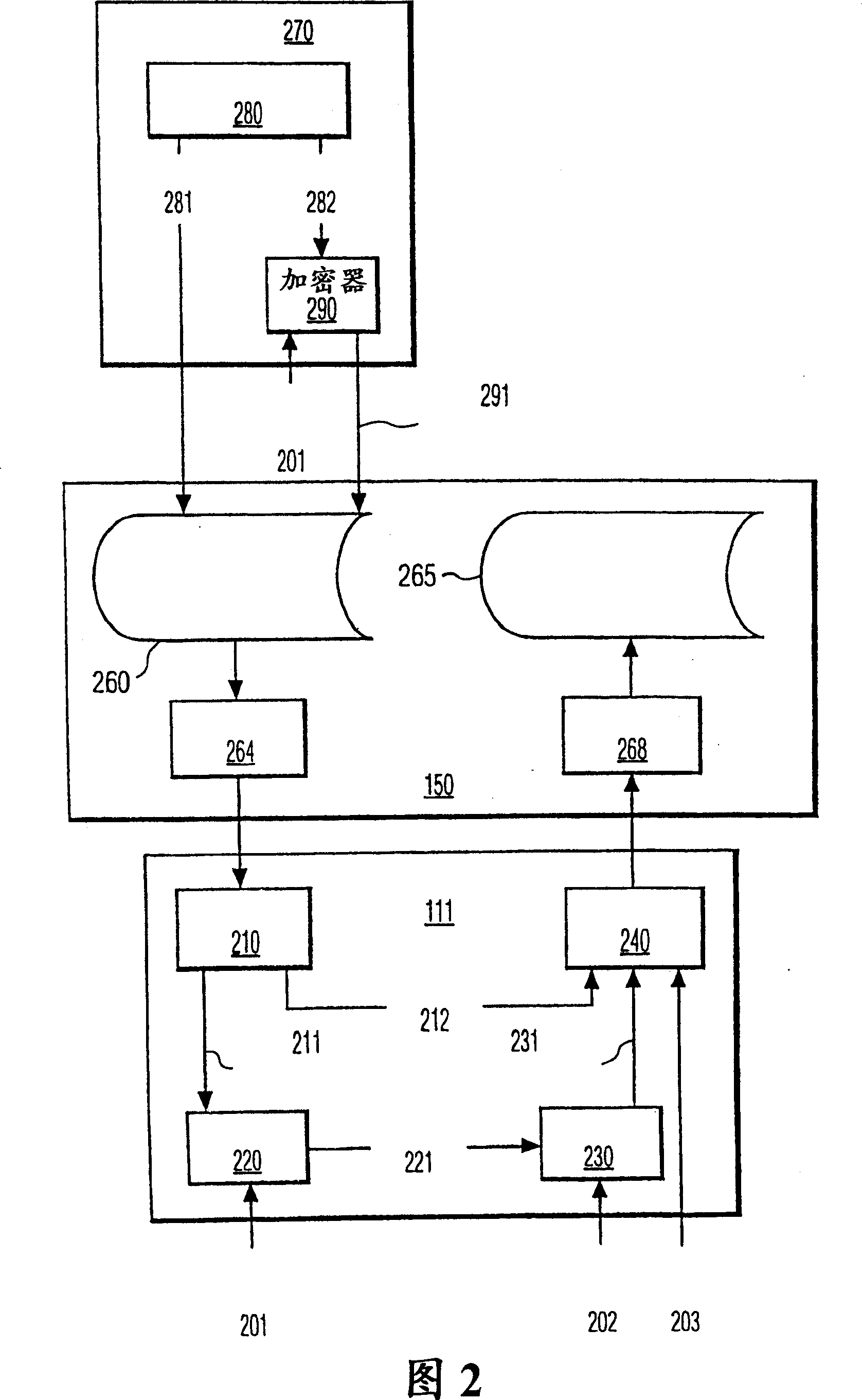
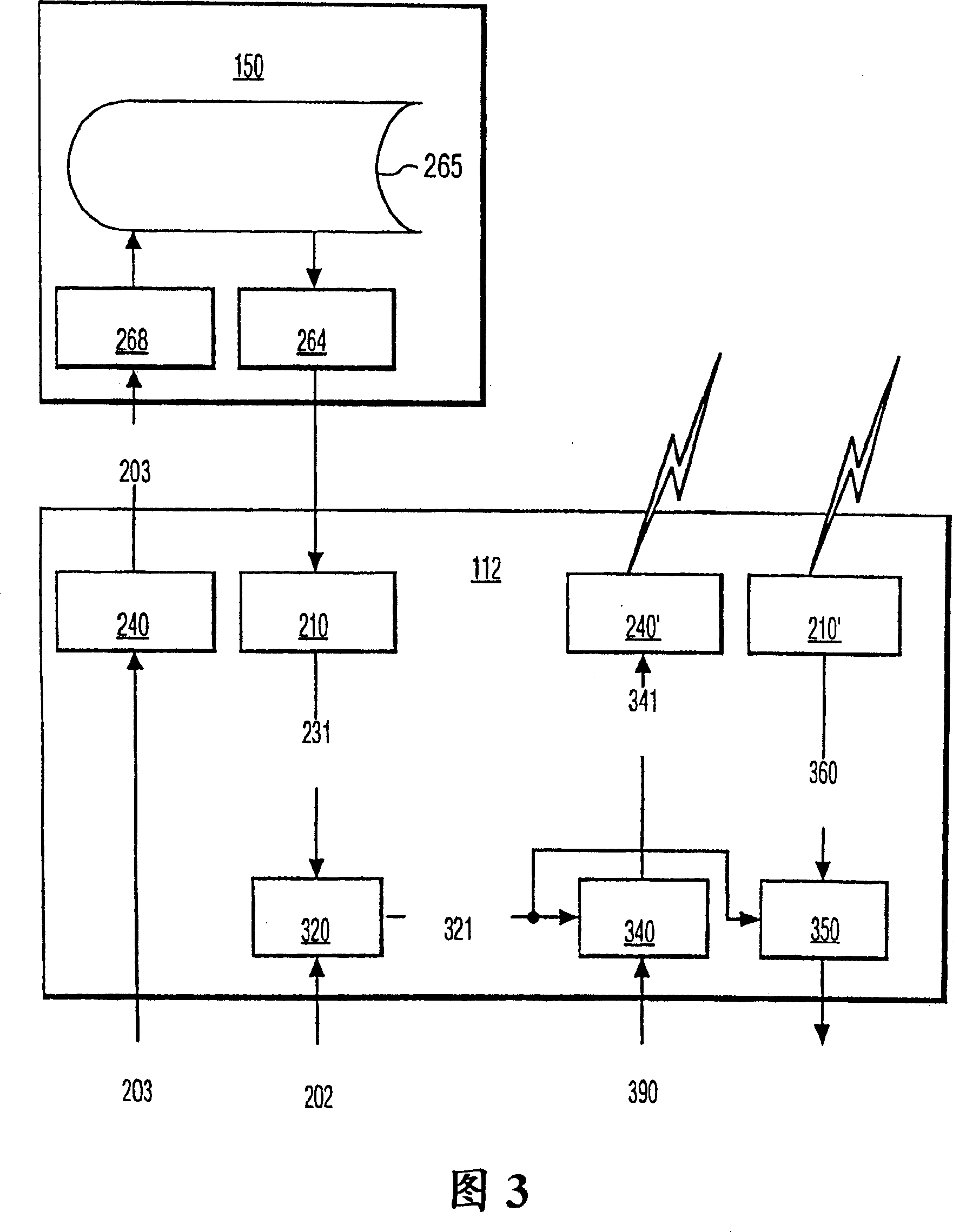
[0020] Figure 2 depicts a typical server processor and client processor illustra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com