Hierarchical network information content managing method based on public key basic facilities
A public key infrastructure and network information technology, which is applied in the field of Internet information content security supervision, can solve the problems of labeling the responsibility of label forgers or label issuers, relying on the self-discipline of network users, and managing safe and unsafe network media content. To achieve the effect of reducing redundant construction, simplifying system structure and realizing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The following is based on figure 1 And Fig. 2 provides a preferred embodiment of the present invention.
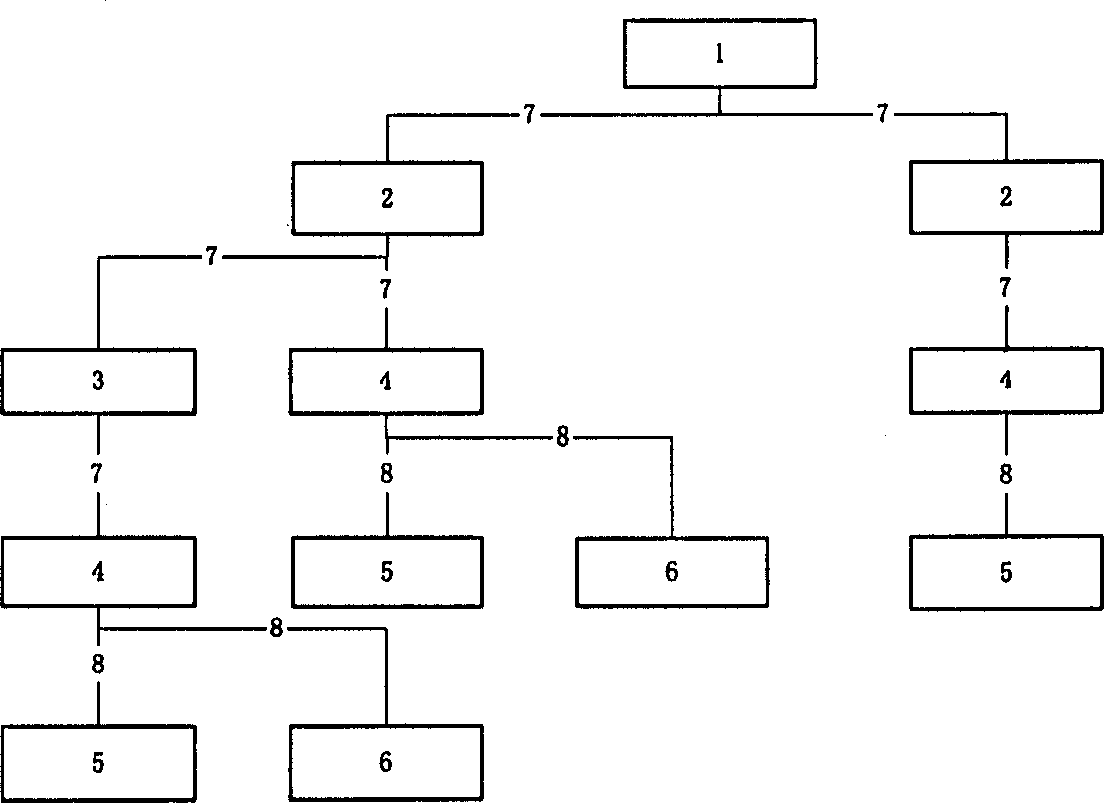
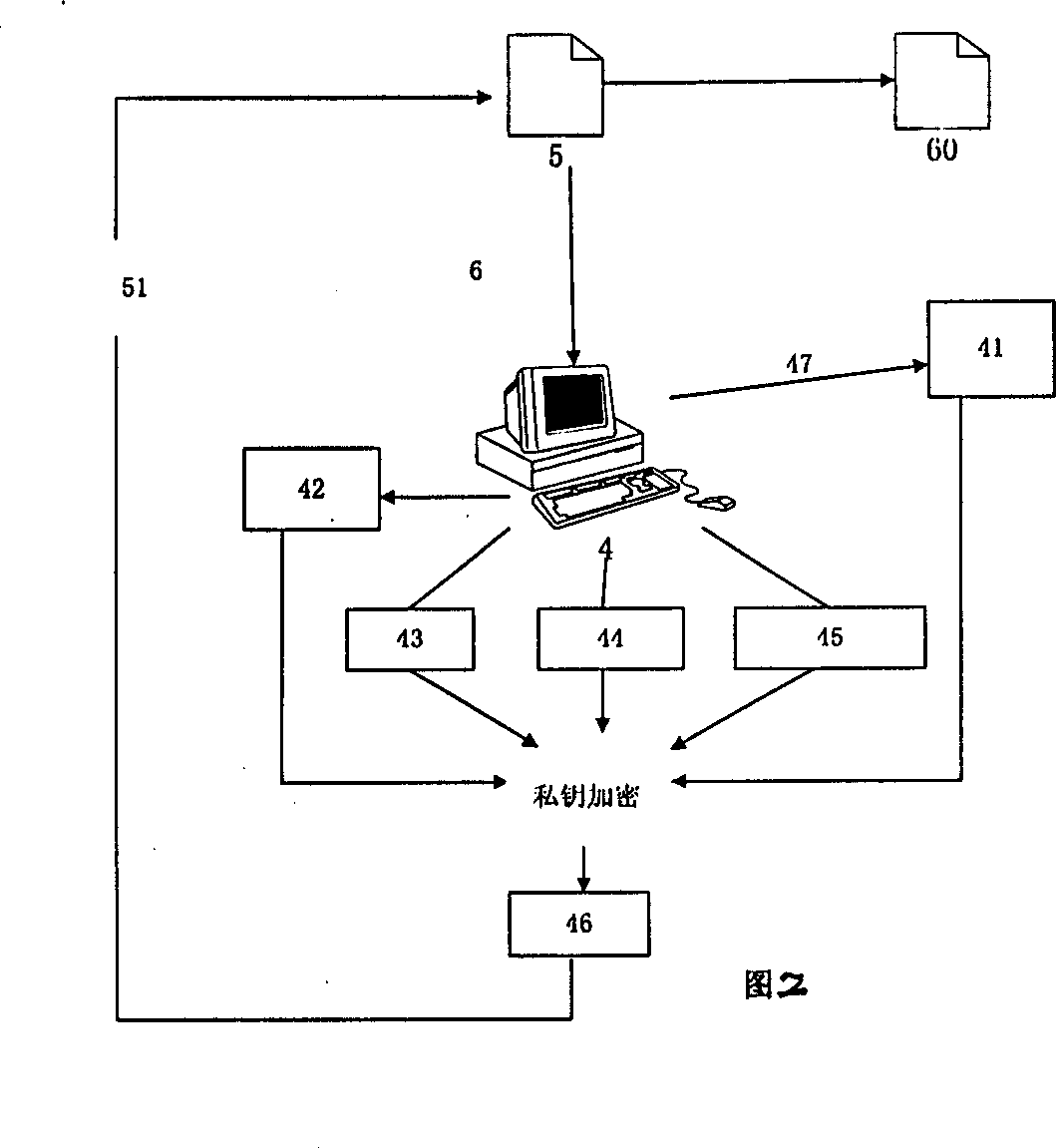
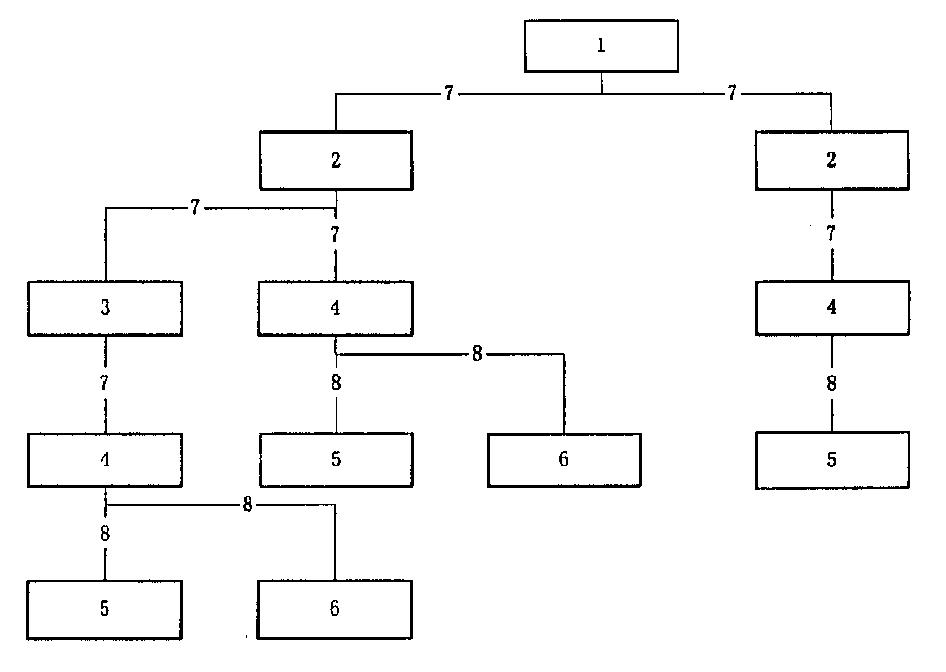
[0040] see figure 1 , as shown in the figure: A hierarchical management center system based on PKI has been established, and the RA structure of each part is described as follows: the labels shown in the figure are:
[0041] 1: Grading Standard Center RSA 2: (Level 1) Label Management Center LMA
[0042] 3: (subordinate) label management center LMA 4; label adding center LAA
[0043] 5: Web site to be rated 6: Web page to be rated
[0044] 7: Authorization 8: Distribution Adding tags
[0045]It can be seen from the figure that the system of this embodiment is a tree structure, and the root node is the classification standard center (RSA) 1, which is the highest point and is also the organization responsible for formulating the general strategy of the entire classification system. Below it is the first Level label management center (LMA) 2, under this (LMA) 2 ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com