Security protection system and method applied in computer system
A computer system and security protection technology, applied in the direction of program loading/starting, program control devices, etc., can solve problems such as inconvenient use, inconvenient working environment, and inability to activate the protection state in real time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
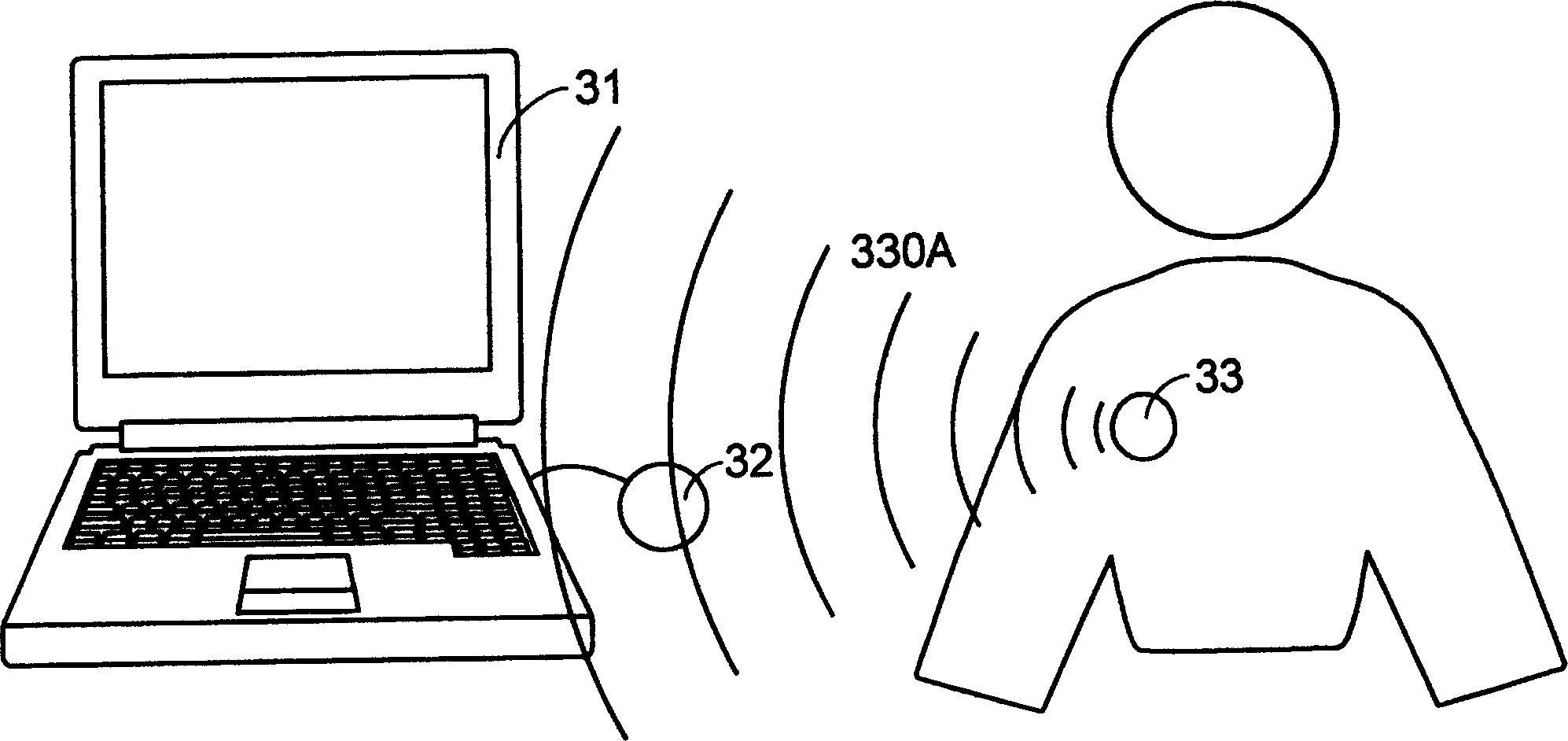
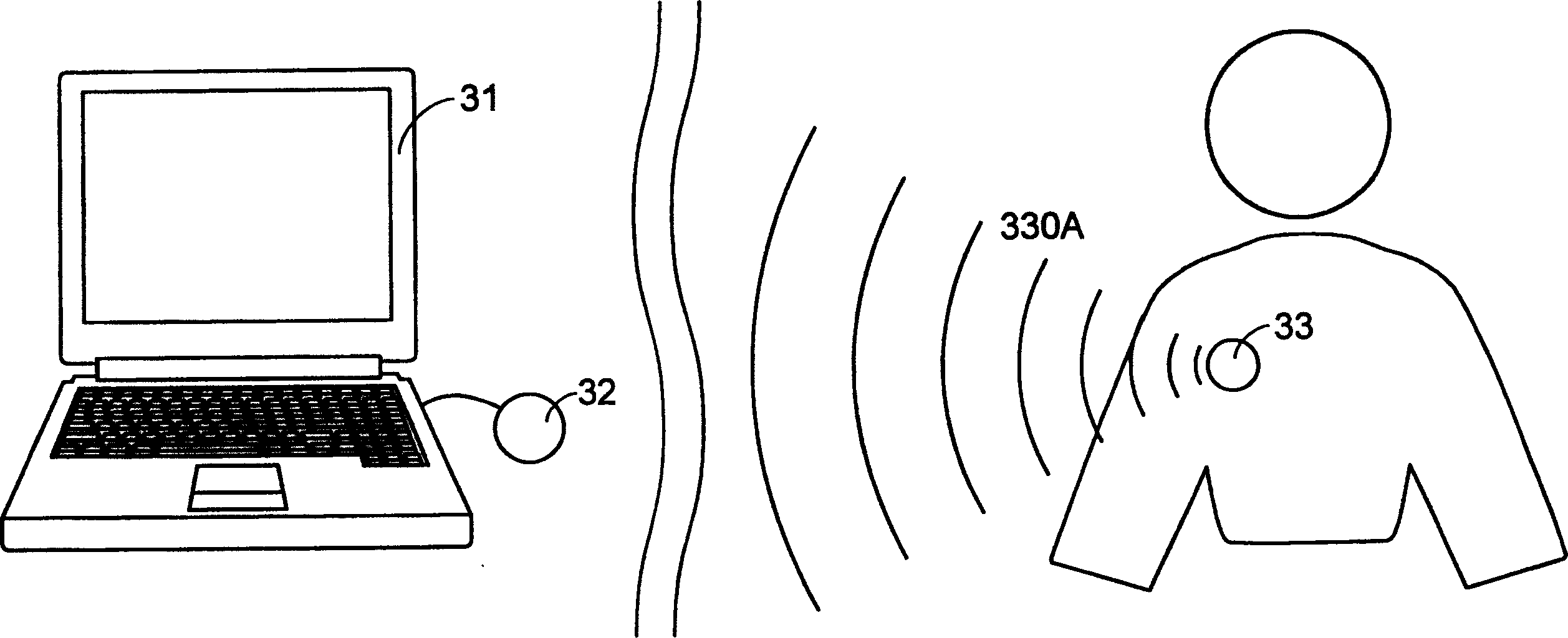
[0035] Such as Figure 2A , Figure 2B , Figure 2C As shown, it is a functional schematic diagram of a preferred embodiment developed by the safety protection system of the present invention to improve common means. The safety protection system can be applied to a computer system 31, including a wireless sending component 33 and electrically connected to A wireless receiving component 32 of the computer system. The user wears a wireless sending unit 33 on the body, and when the wireless sending unit 33 continuously sends out a specific radio signal 330A and is received by the wireless receiving unit 32, the safety protection system will not execute any action, the user can freely operate the computer system such as Figure 2A shown. Such as Figure 2B , Figure 2C As shown, when the user leaves the computer system for a certain distance, the wireless receiving component 32 will not be able to receive the specific radio signal 330A, and at this time the wireless receivin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com