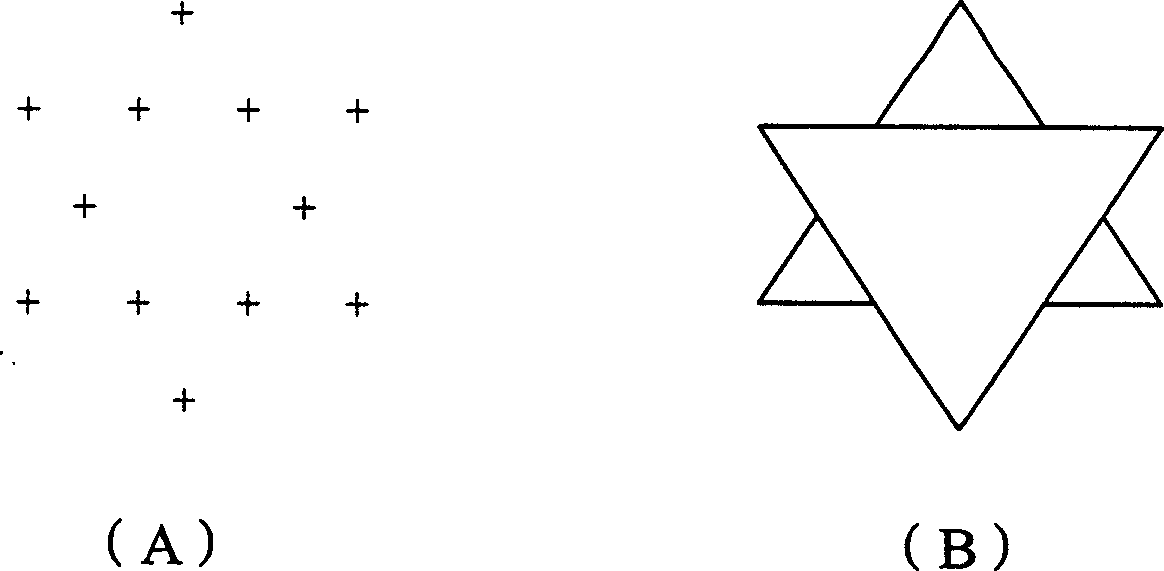A super password generation and authentication method
A super password and user authentication technology, applied in user identity/authority verification, data exchange details, digital transmission system, etc., can solve the problems of high matching probability, intrusion, fast string matching speed, etc., to achieve convenient use and network security , safe to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
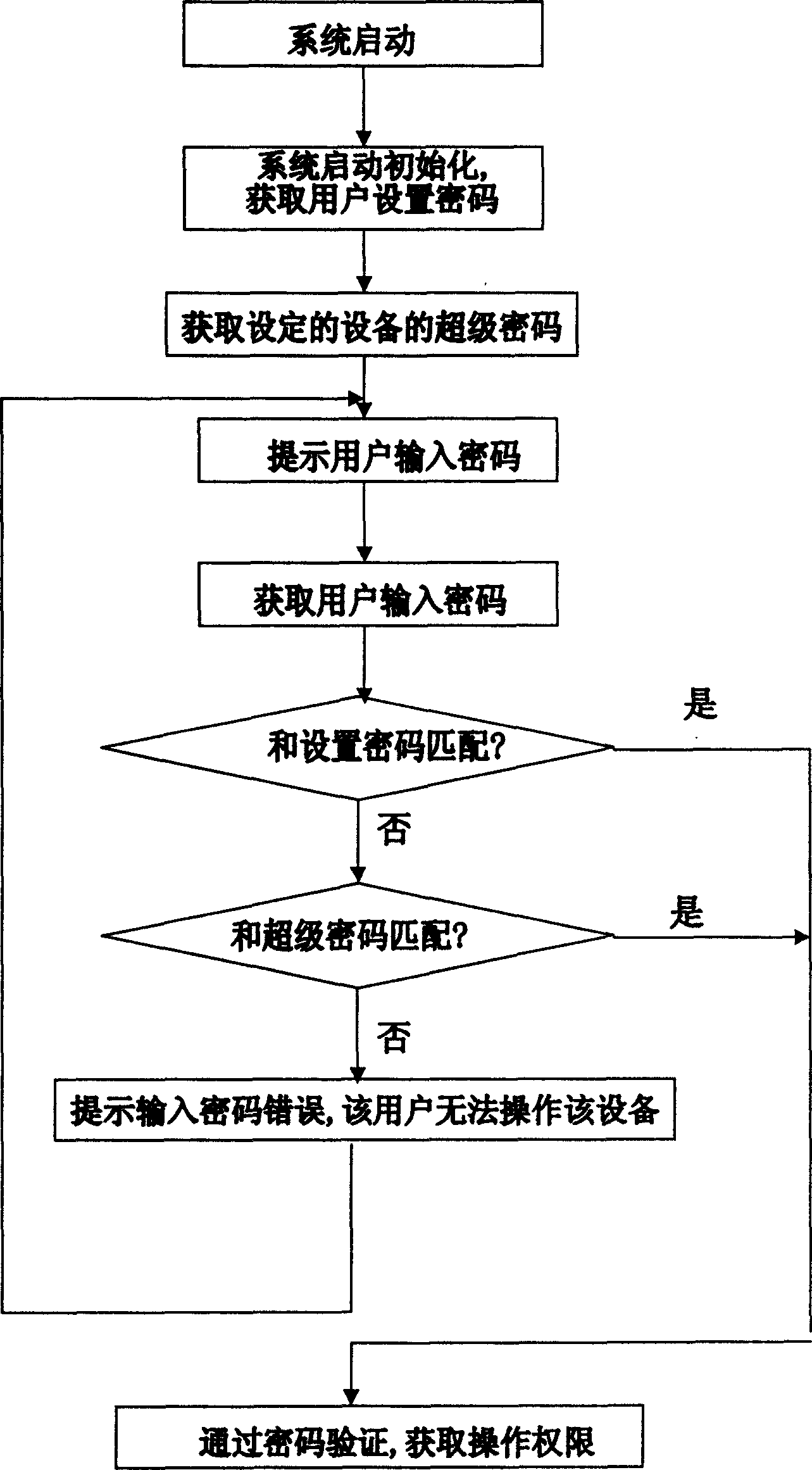
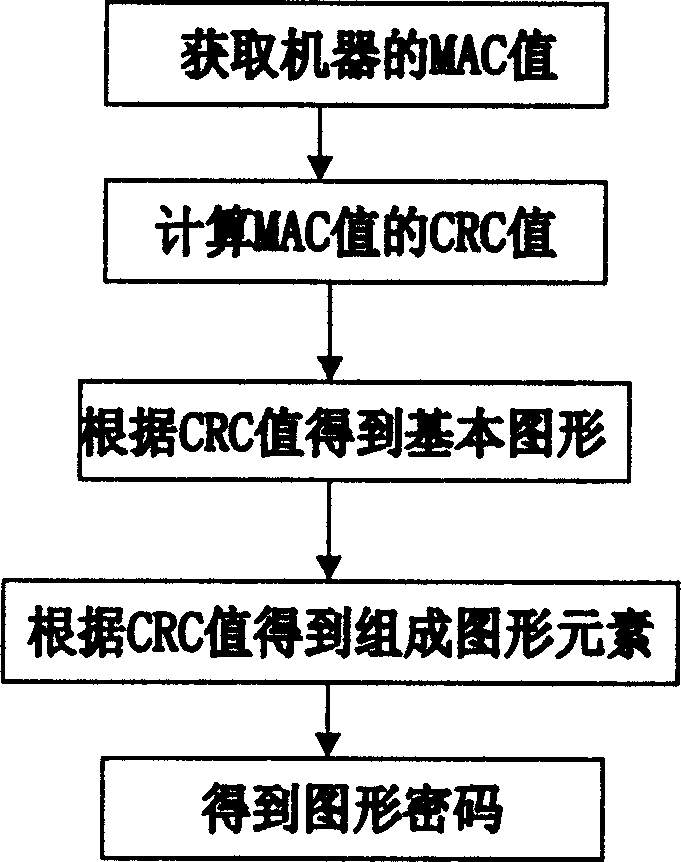
[0021] Each network device has its own network MAC (Media Access Control) address, which is used to identify the device in the network. The MAC address is unique, and the MAC addresses of different devices are different. With this unique MAC address, a unique super password can be customized for the device. The method of realization is that the equipment supplier uses a super password generation software to encrypt the MAC address into a set of character strings to form a unique super password valid only for the device and provide it to the user. The super password generation program of the super password generation software can adopt the MD5 encryption algorithm (Message-Digest Algorithm 5, information-digest algorithm), and can also refer to the MD5 encryption algorithm for proper modification.
[0022] For example: improve the MD5 algori...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com