Method for authentication of elements of a group
A component and verification request technology, which is applied in the field of component verification to achieve the effect of reducing time and storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
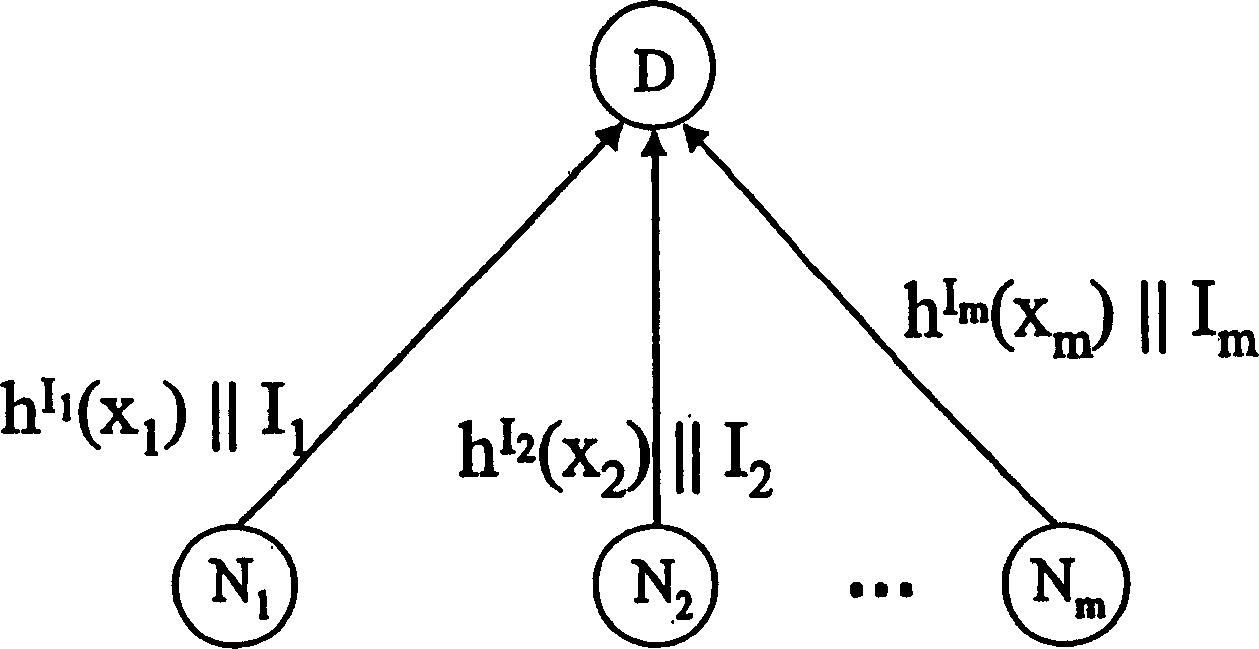
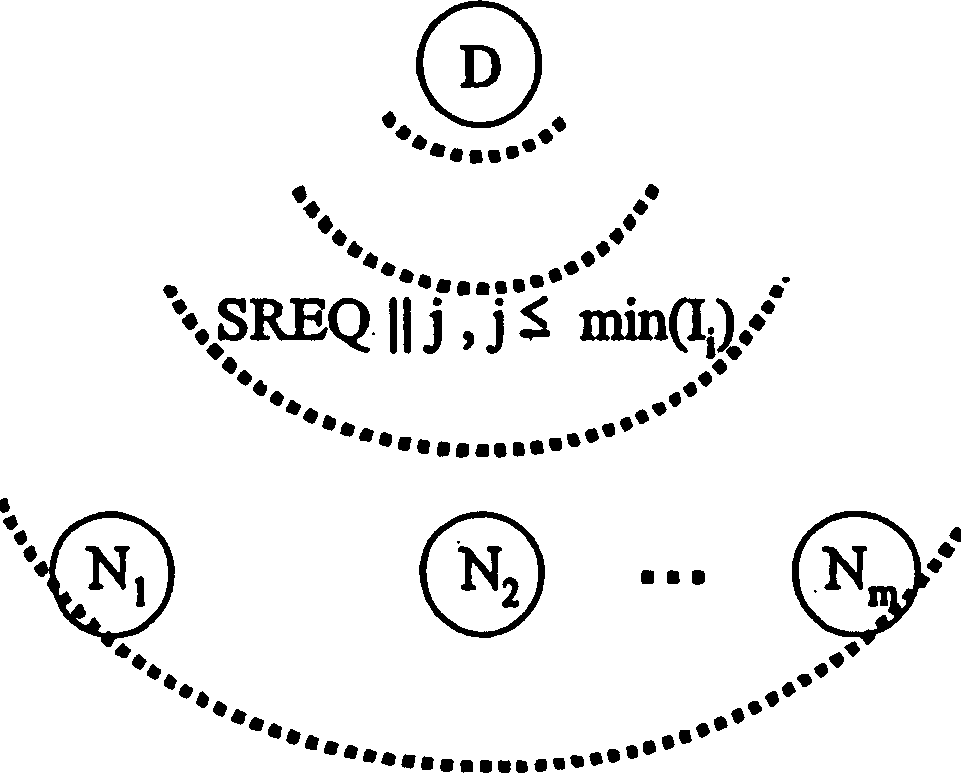
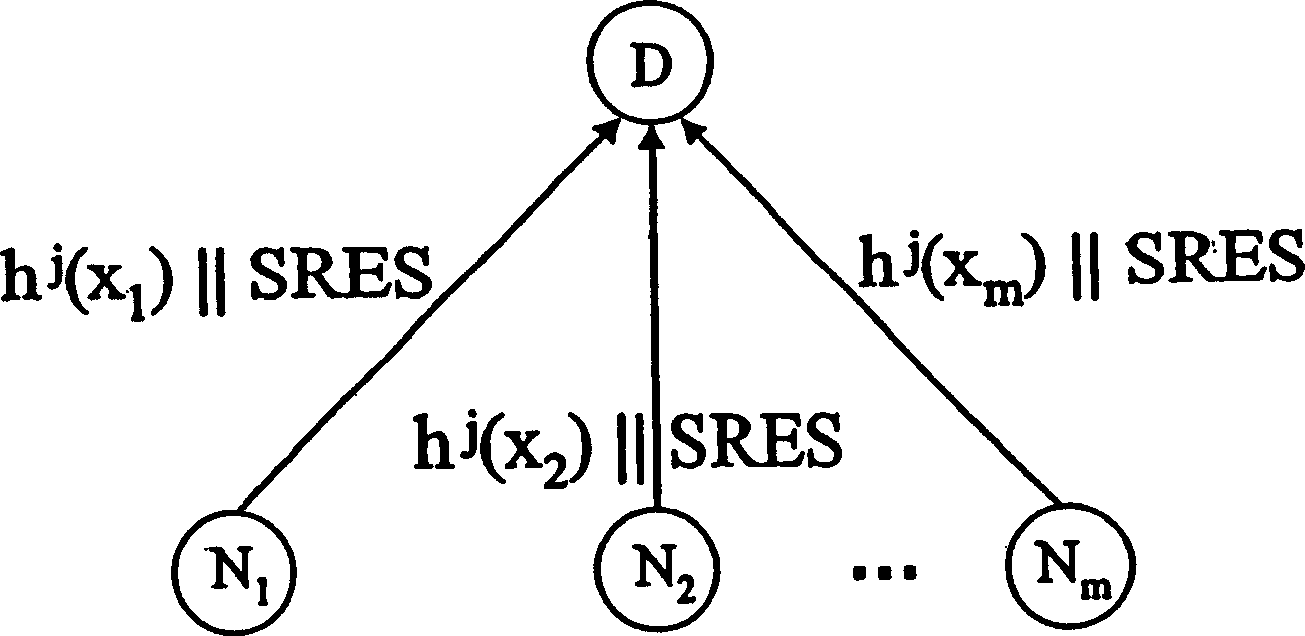
[0024] refer to figure 1 , shows the initialization phase before the actual verification process. The group shown includes a leading element D and a total of m components N i (here, i=1,...,m), where, for clarity, only three elements N are shown 1 , N 2 and N m . It should be appreciated that initialization occurs in a protected environment where potential attacks can be excluded. In the case of wireless sensor networks, the initialization phase can be performed in the ensemble, or in parts thereof, before configuring the individual sensor nodes.
[0025] During the initialization phase, the component N i First of all, they are all unified to the shared hash function h(). In addition, each component N i (where i=1,...,m) defines a key x known only to the component itself i . For example, key x i Can be component N i generated random number. According to the key x i , each component N i Perform the hash function iteratively, that is, for the first pair of keys xi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com