Role-based access control system, method and computer program product
A computer program and access control technology, applied in computer security devices, computing, transmission systems, etc., can solve problems such as limited protection of individual resource instances, and achieve the effect of simplifying access control system management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
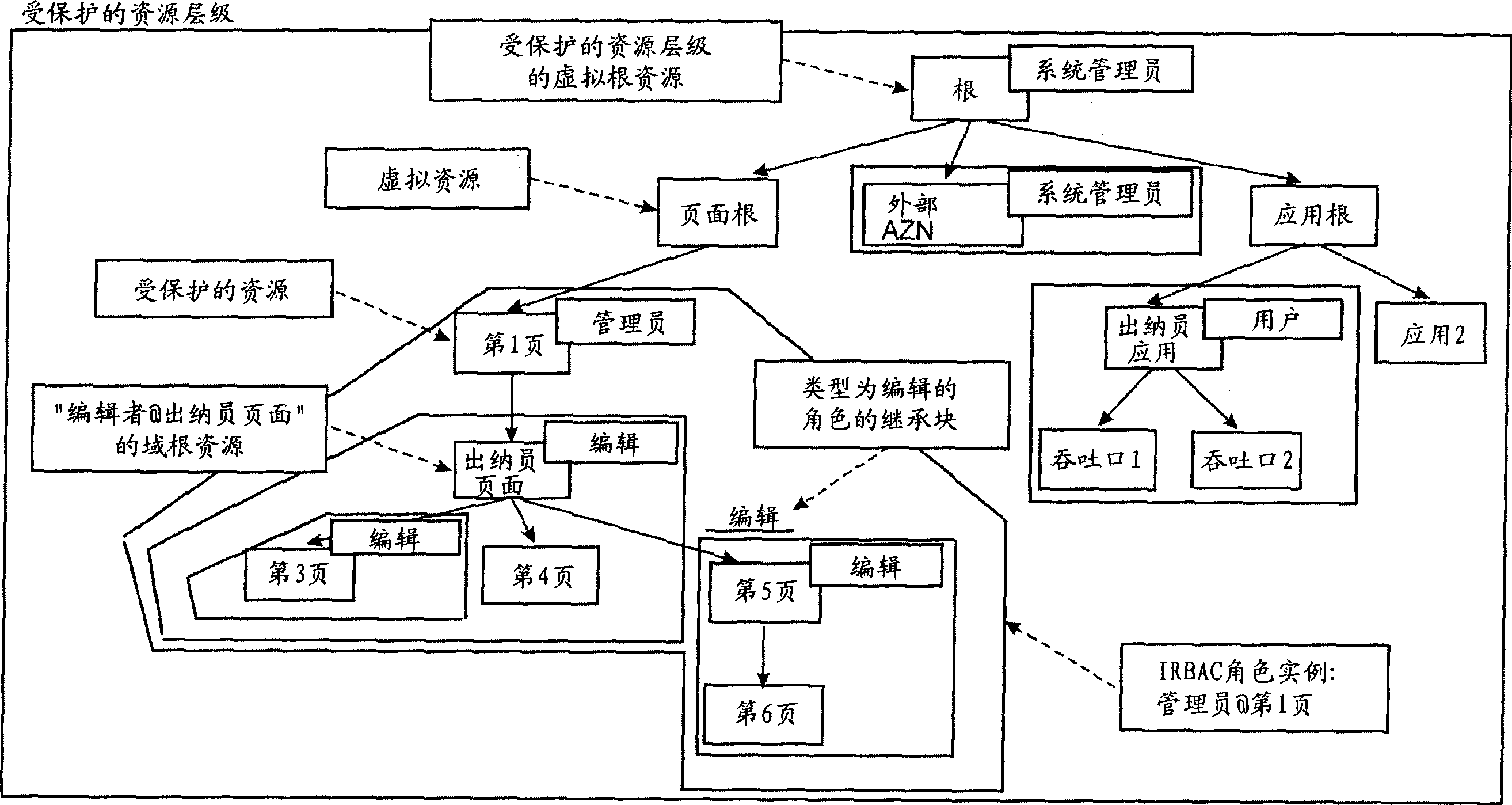
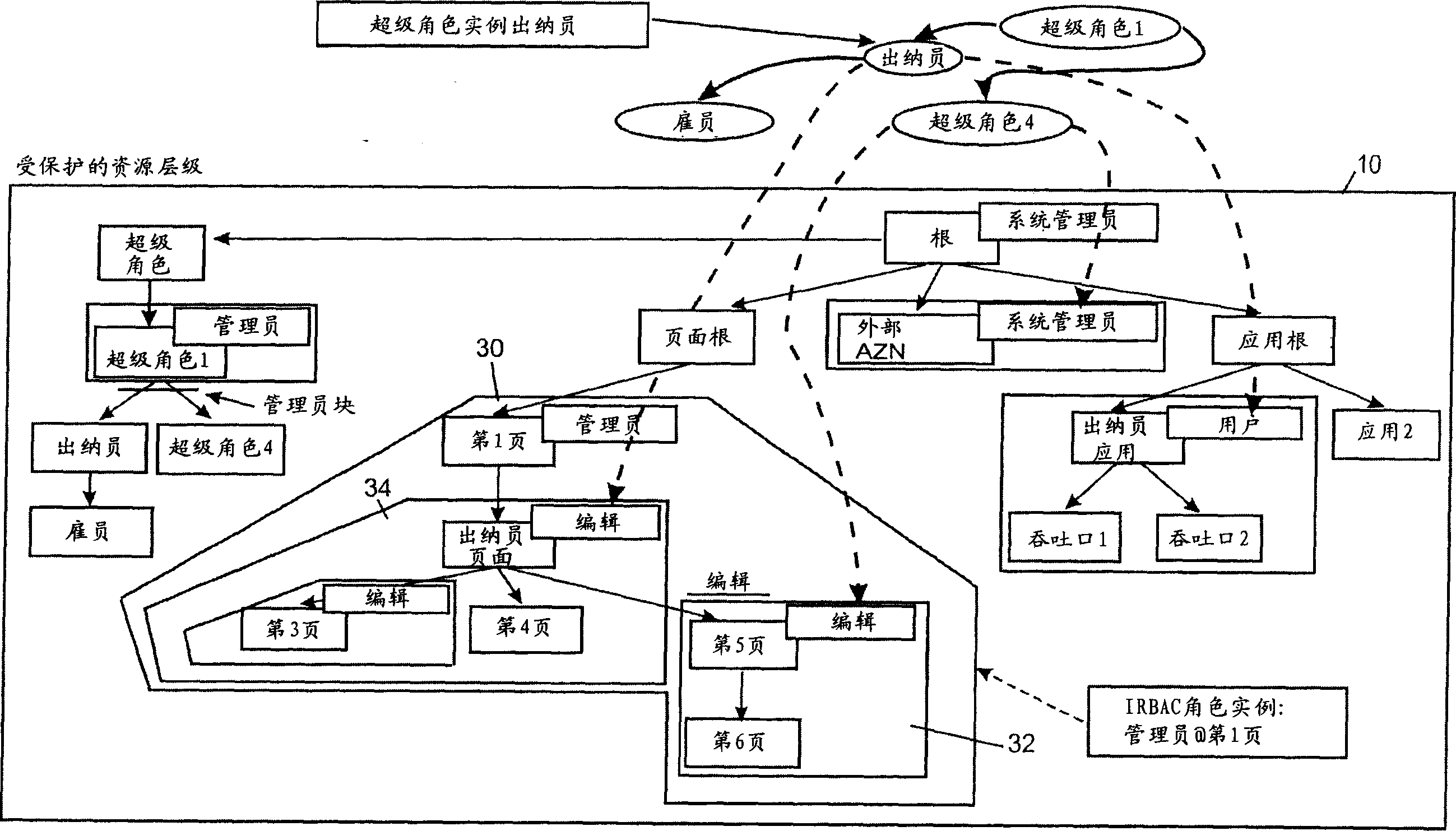
[0050] figure 1 Possible scenarios according to the IRBAC model are described. Each role within the IRBAC model has an associated role type. A role type is first a set of actions and models a specific way of interacting with a resource in terms of job responsibilities. For example, since editors are typically responsible for modifying resources and creating new resources, the Editor role type could include View, Edit, Add Child, and so on. Additionally, each role instance has an associated domain root resource. The naming convention for IRBAC role instances is "role@domain root resource". figure 1 A role instance of type "Administrator" is depicted, for example, tied to resource "Page 1", called "Administrator@Page 1". The set of permissions contained in a particular IRBAC role instance is defined by establishing the set of actions contained in the corresponding role type and the set of resources contained in the subtree rooted at the role's domain root Calculus, the so-c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com