Data integrity protection method
A data integrity and integrity protection technology, applied in the direction of electrical digital data processing, digital data processing components, instruments, etc., can solve problems such as the inability to guarantee that the code is not malicious, the inability to detect malicious code, and the inability to prevent malicious code, etc., to achieve Real-time integrity protection, good availability, and little impact on system performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
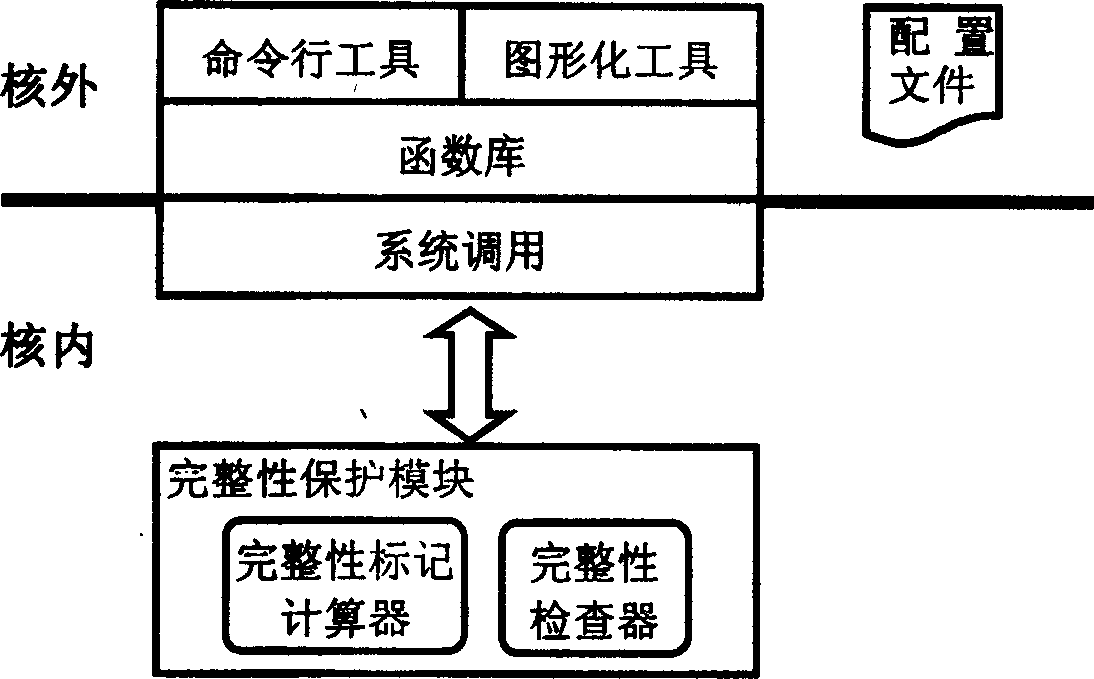
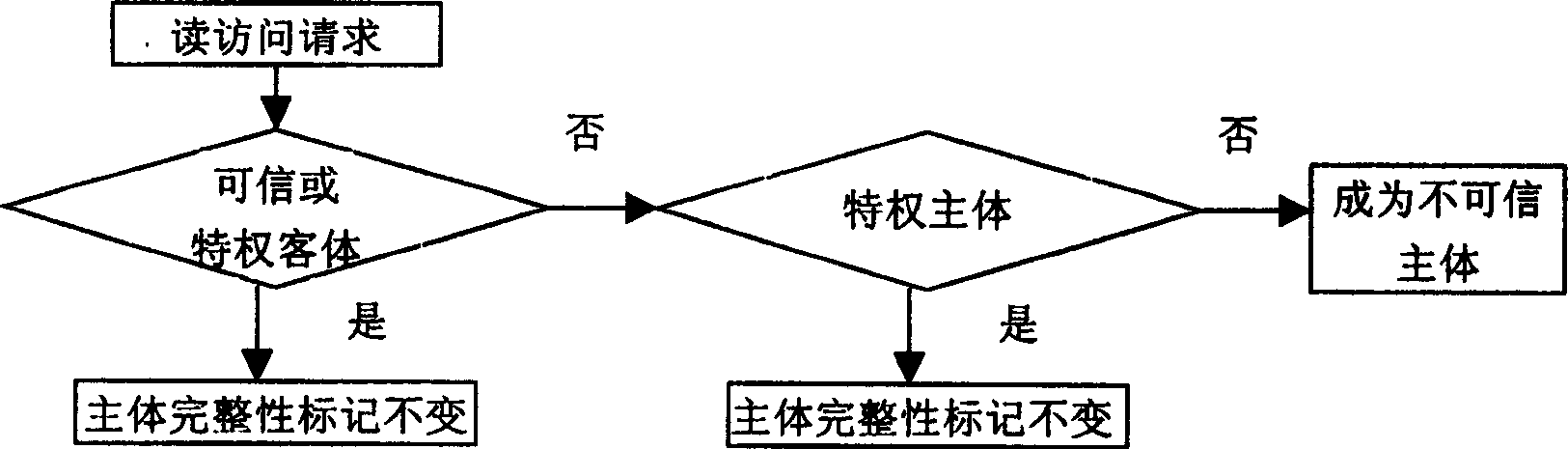
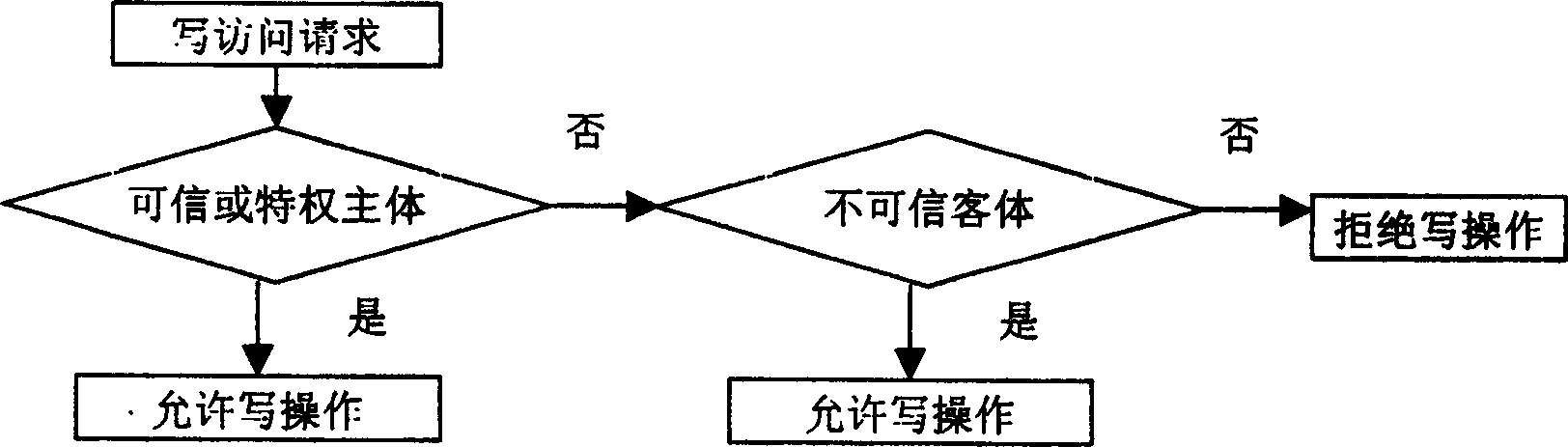
[0040] figure 1 It is the structural diagram of the integrity protection model. The model is divided into two parts: inner core and outer core. The inner core is composed of integrity protection modules and system calls realized in the form of dynamic modules, and the outer core is composed of function libraries, command line tools and graphical tools. The integrity protection module mainly includes an integrity mark calculator and an integrity checker. The integrity mark calculator calculates the integrity mark of the subject or object according to the integrity logic relationship when creating or reading an object; Or the execution operation point judges whether the subject can operate the object according to the access control rules, and protects the integrity of the system. The integrity protection module provides the user layer with the functions of viewing the integrity marks of the subject and objects and setting the integrity marks of the objects by means of system ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com