Trusting method of network information system based on family genes
A network information and family technology, applied in transmission systems, electrical components, etc., can solve problems such as high cost, user centralized registration and identity verification methods are difficult to adapt to actual user applications, and certificate subject information is unclear.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
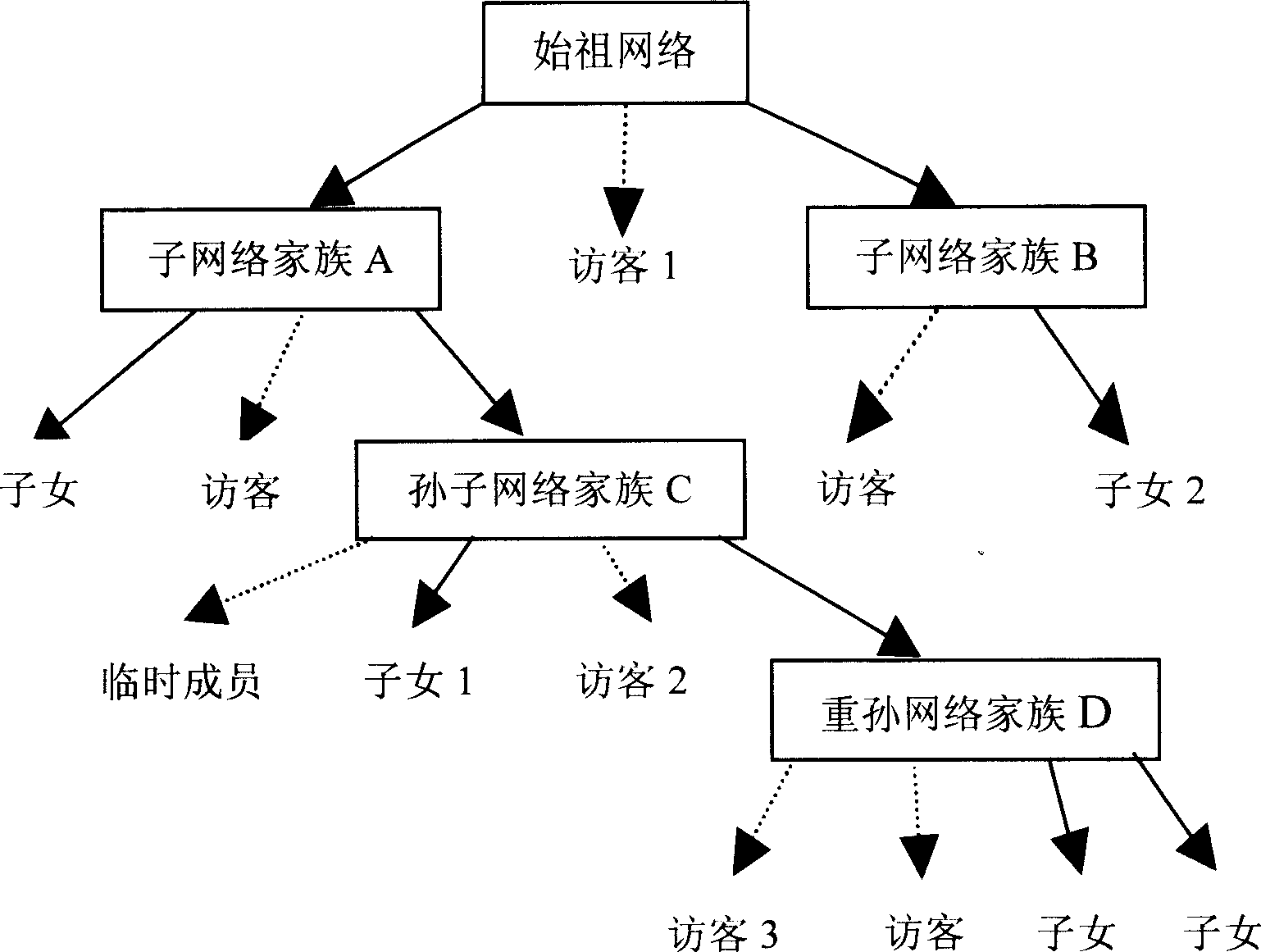
[0038] figure 1 is the evolution graph of the network family.
[0039] From figure 1 It can be seen that the entire network evolved from an "ancestor network", which means that the "ancestor network" is the starting point of trust in the entire network. The evolution graph of a network family is similar to an inverted tree, denoted by T, and each node n of the tree T can represent a parent, child, visitor, or temporary member (the root node represents the ancestor network).
[0040] The specific steps to construct a network family are as follows:
[0041] (1) The steps of "ancestor network" generation:
[0042] 1) Initially, set the network family evolution graph T to be empty;
[0043] 2) Create "ancestor network" node n 0 , n 0 ∈ F,n 0 It is the starting point of trust in the entire network;
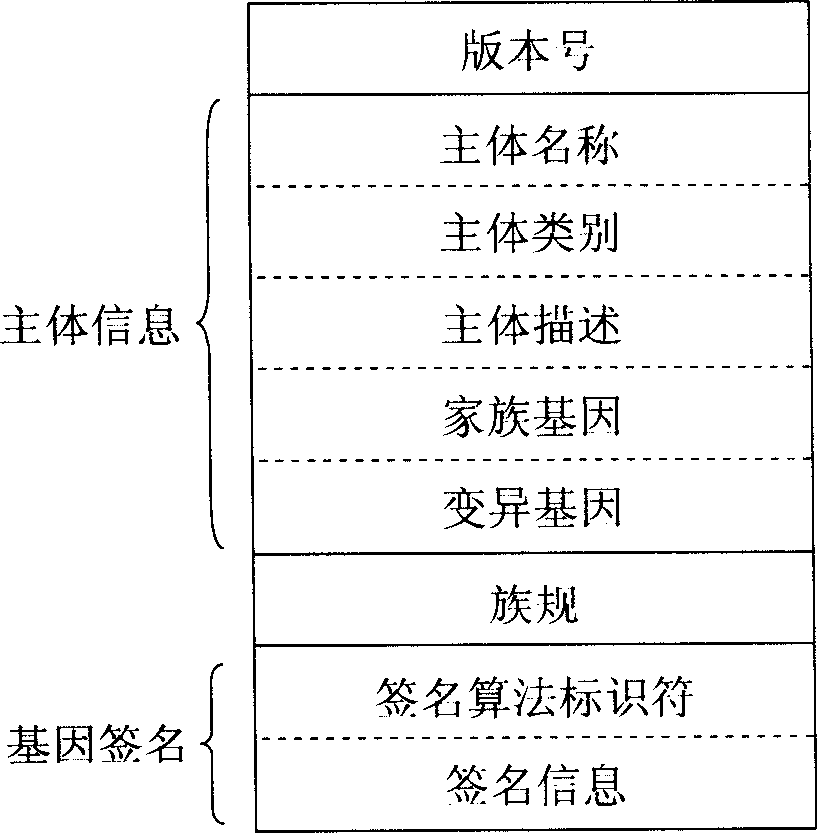
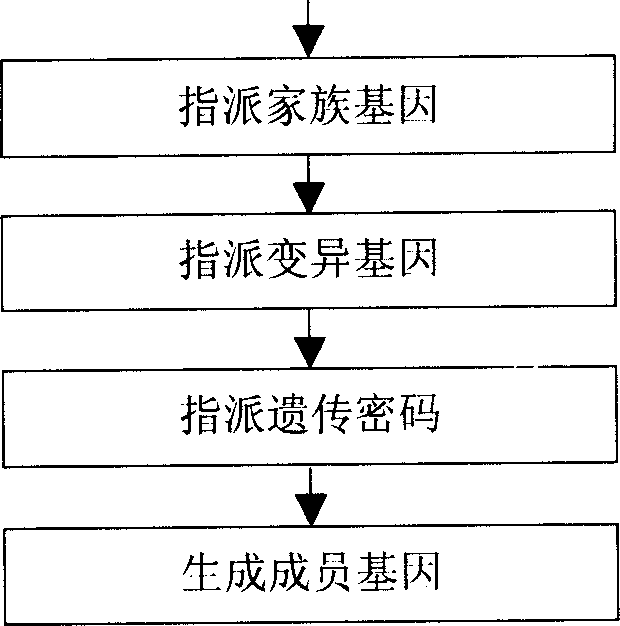
[0044] 3) Set the "ancestor network" node, including:
[0045] ① Set the node name category: n 0 .name = network ancestor, n 0 .type=parent;
[0046] ②Assigned family gene:...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap