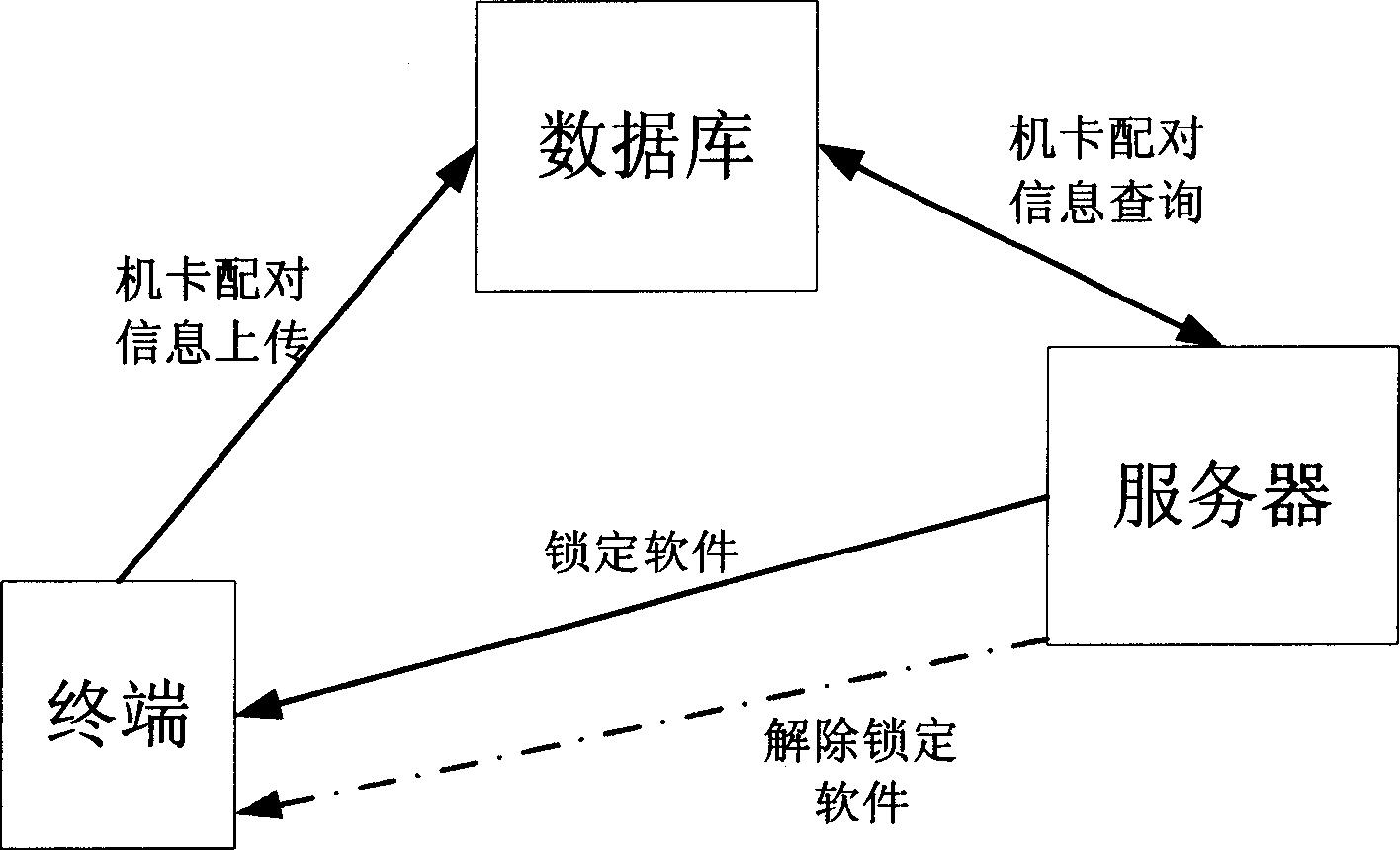
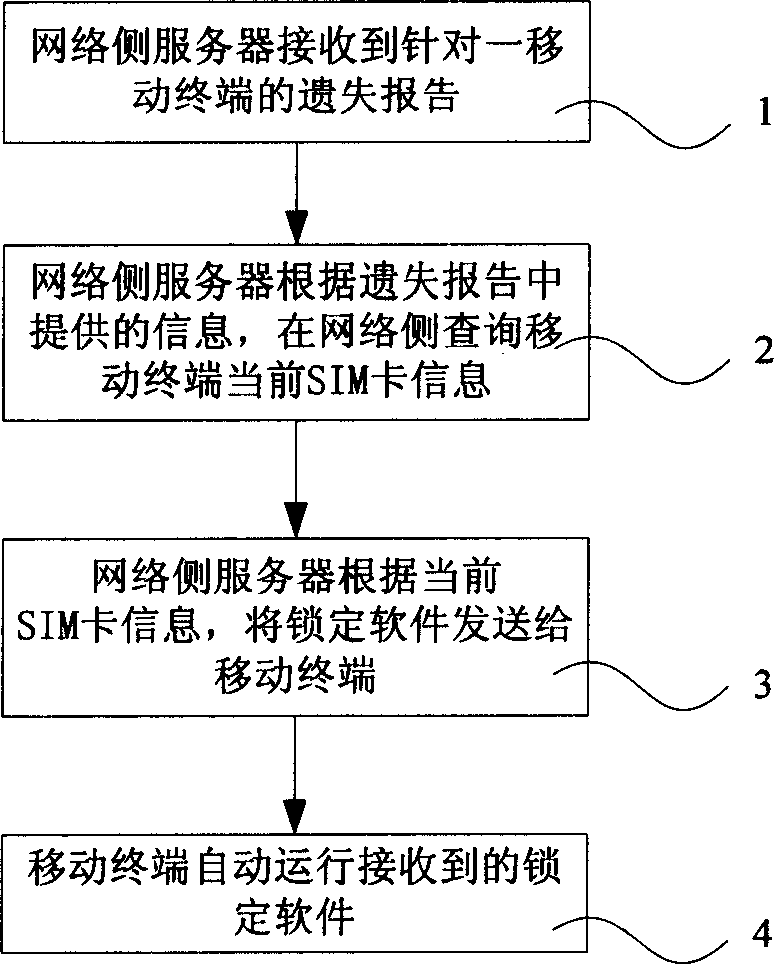
Method for realizing mobile terminal data protection
A mobile terminal and data protection technology, which is applied in the direction of security devices, electrical components, radio/inductive link selection arrangements, etc., to achieve the effects of convenient and flexible unlocking, avoiding leakage, and avoiding embezzlement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
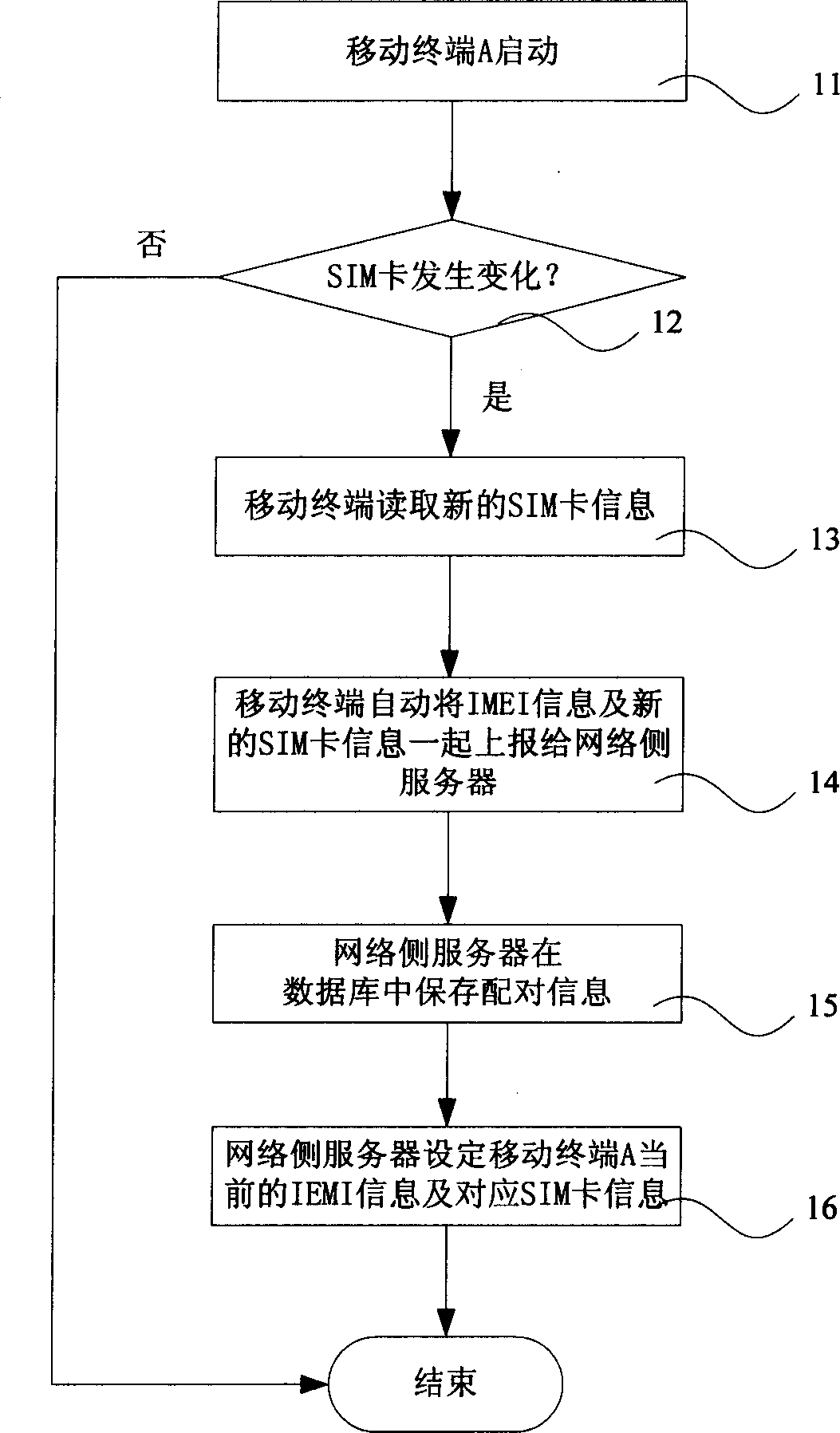
[0107] This embodiment provides a method for realizing data protection of a mobile terminal when the SIM card is replaced. Specifically: when mobile terminal A with the original SIM card number 1234567890 is lost, user B picks up and replaces his own SIM card into mobile terminal A to continue using, and the replaced SIM card number is 0123456789. The flow chart of the method for realizing the data protection of the mobile terminal in this embodiment is as follows: Figure 6 shown, including the following steps:
[0108] Step 101. When the mobile terminal A is started for the first time, the network side server receives and uses the IMEI information XXXXXXYYZZZZZZB and the corresponding SIM card information 1234567890 automatically reported by the mobile terminal as the IMEI information and the corresponding SIM card information;
[0109] Step 102, the network side server receives the IMEI information XXXXXXYYZZZZZZB and the corresponding SIM card information 0123456789 autom...
Embodiment 2
[0125] Such as Figure 7 As shown, the present embodiment provides a flow chart of a method for realizing data protection of a mobile terminal when the information provided in the loss report is the original SIM card information under the same situation as that of Embodiment 1, including the following steps:
[0126] Step 201, when the mobile terminal A starts for the first time, the network side server receives and uses the IMEI information XXXXXXYYZZZZZZB and the corresponding SIM card information 1234567890 automatically reported by the mobile terminal as the IMEI information and the corresponding SIM card information, and saves the received time information;
[0127] Step 202, the network side server receives the IMEI information XXXXXXYYZZZZZZB and the corresponding SIM card information 0123456789 that is automatically reported when the mobile terminal A detects that the SIM card changes, as the current IMEI information and the corresponding SIM card information of the mo...
Embodiment 3
[0142] Such as Figure 8 As shown, this embodiment provides on the basis of Embodiment 1 or 2 to prevent the SIM card lost or stolen along with the terminal from being replaced into the mobile terminal B for continued use, including the following steps:
[0143] Step 301-step 305 is the same as step 101-step 105;
[0144] Step 306, the network side server verifies that the current SIM card 0123456789 is different from the original SIM card information 1234567890 before the lost time;
[0145] Step 307, the network side server checks whether the SIM card whose number is 0123456789 and / or the SIM card whose number is 1234567890 is in use, if yes, execute step 310, otherwise execute step 308;
[0146] Step 308, the network side server identification number is 0123456789 and / or the SIM card information whose number is 1234567890;
[0147] Step 309, the network side server detects whether the number is 0123456789 and / or whether the SIM card whose number is 1234567890 is activated...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com