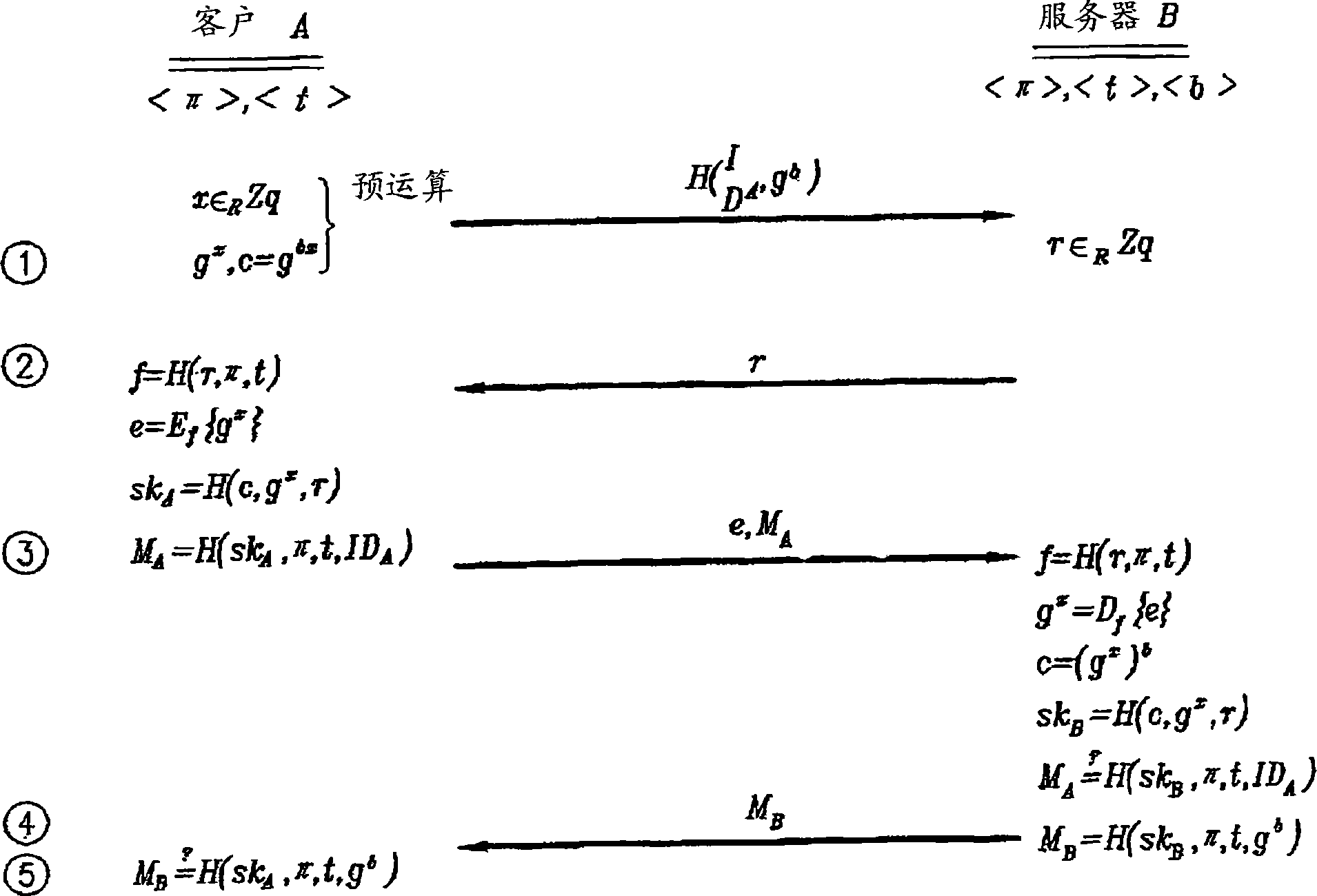Two-factor authenticated key exchange method and authentication method using the same, and recording medium storing program including the same
A key exchange and factor technology, applied to the usage of multiple keys/algorithms, and key distribution, can solve problems such as the inability of passwords to resist dictionary attacks, written on paper or used in many places, and password exposure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In the following detailed description, there are shown and described only the preferred embodiments of the invention by way of illustration of the best mode contemplated by the inventors for carrying out the invention. As will be realized, the invention is capable of modifications in various obvious respects, all without departing from the invention. Accordingly, the drawings and description are to be regarded as illustrative of substance, and not as restrictive. Components not described in the specification are omitted for clarity, and those components for which similar descriptions are provided have the same reference numerals.
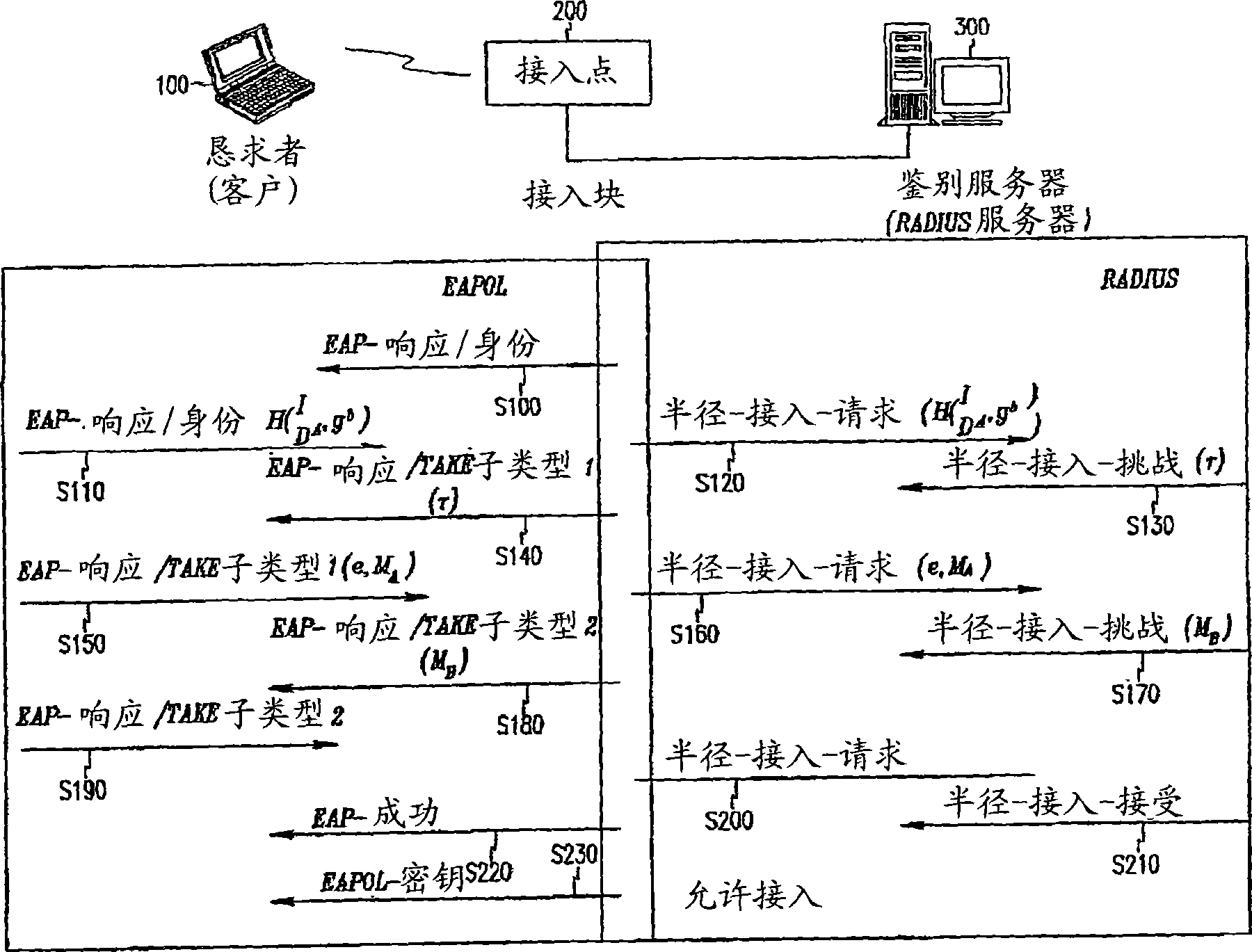
[0043] An authentication method using the TAKE protocol according to an embodiment of the present invention will be described.
[0044] figure 1 A flowchart of the TAKE protocol according to a preferred embodiment of the present invention is shown.
[0045] The symbols described in the preferred embodiments are defined as follows.
[0046...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com