Detecting method for illegal memory reading and writing
A memory, illegal technology, applied in the field of memory read and write detection, can solve the problem of only one or two memory blocks, and achieve the effect of flexible use and cost reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
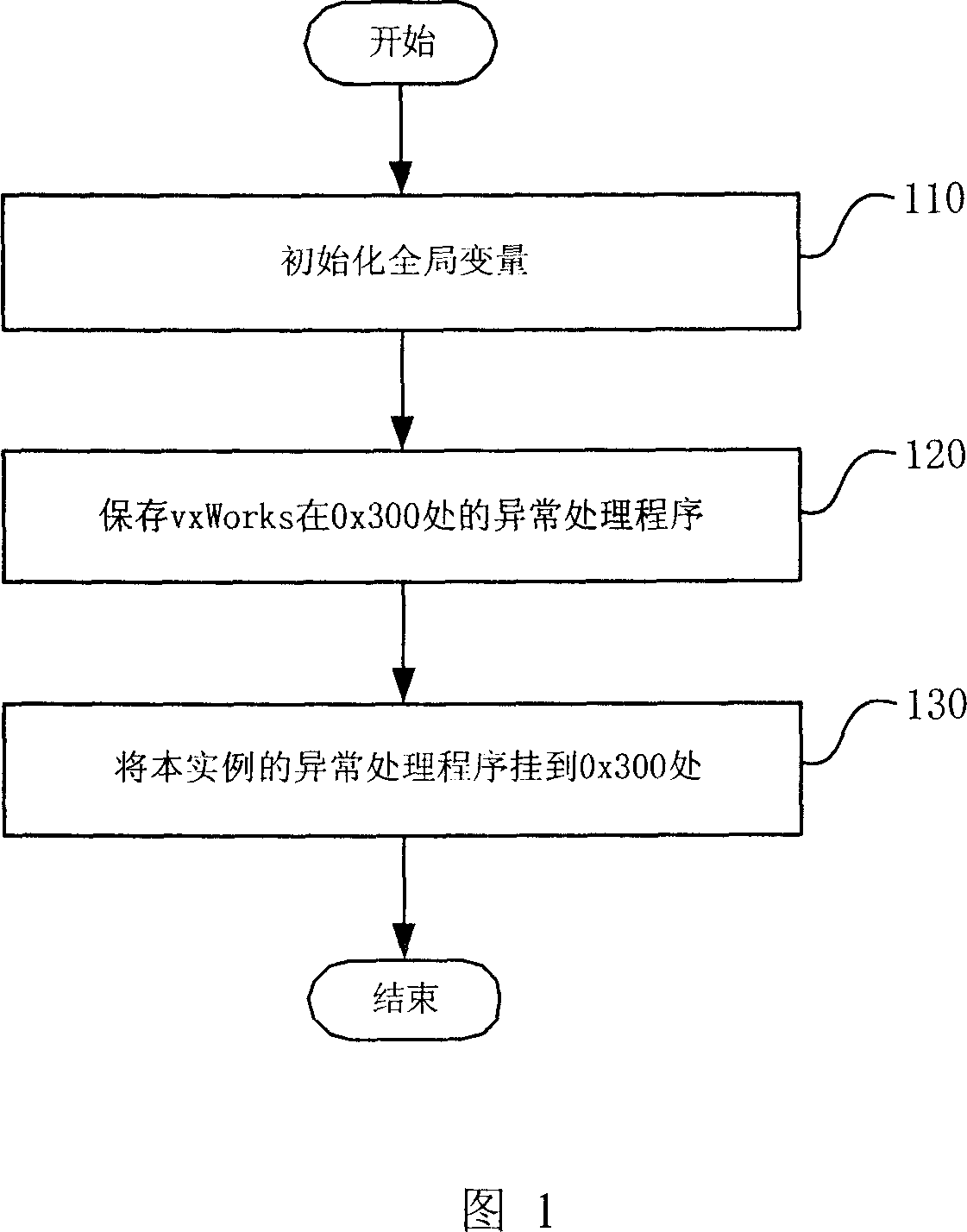
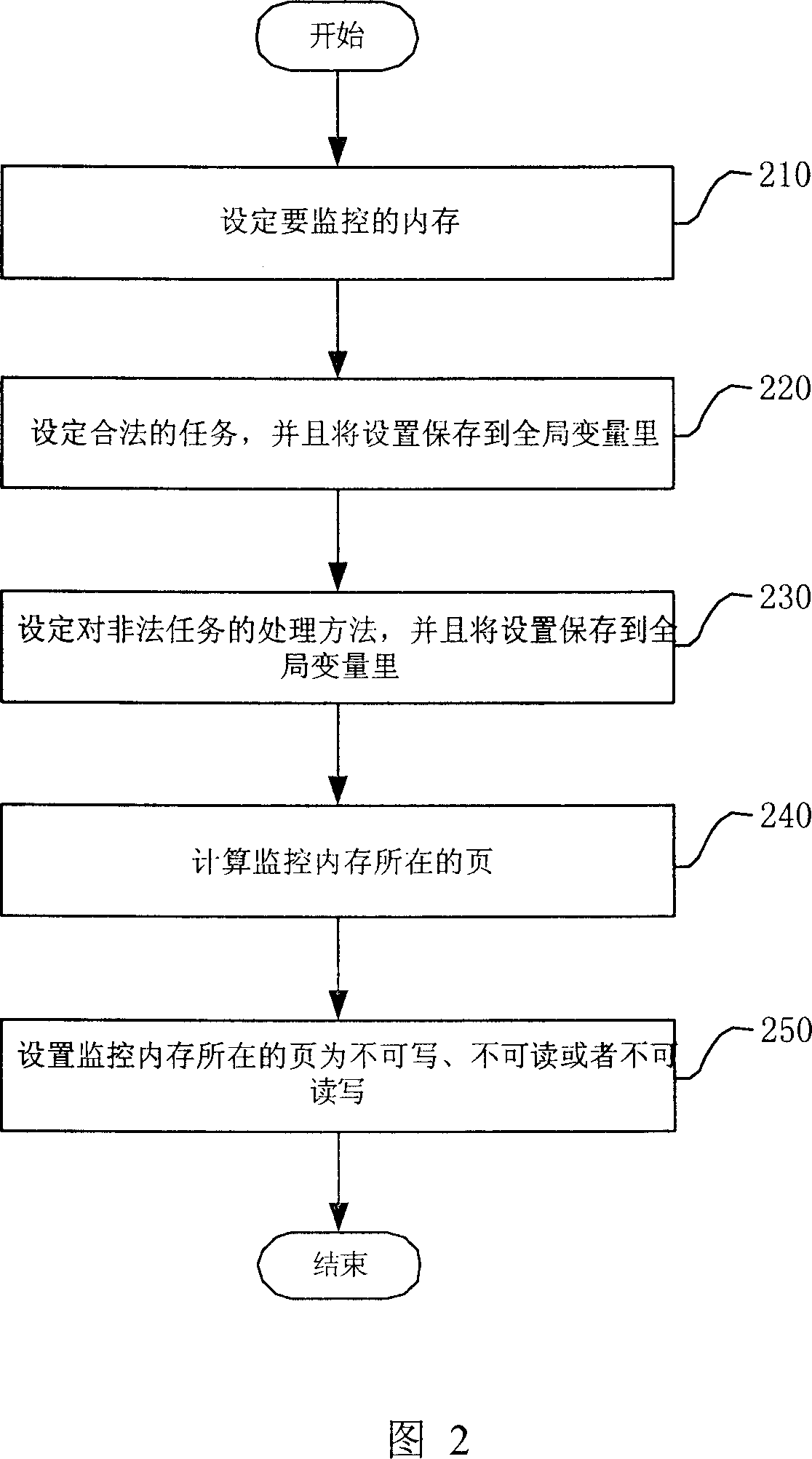
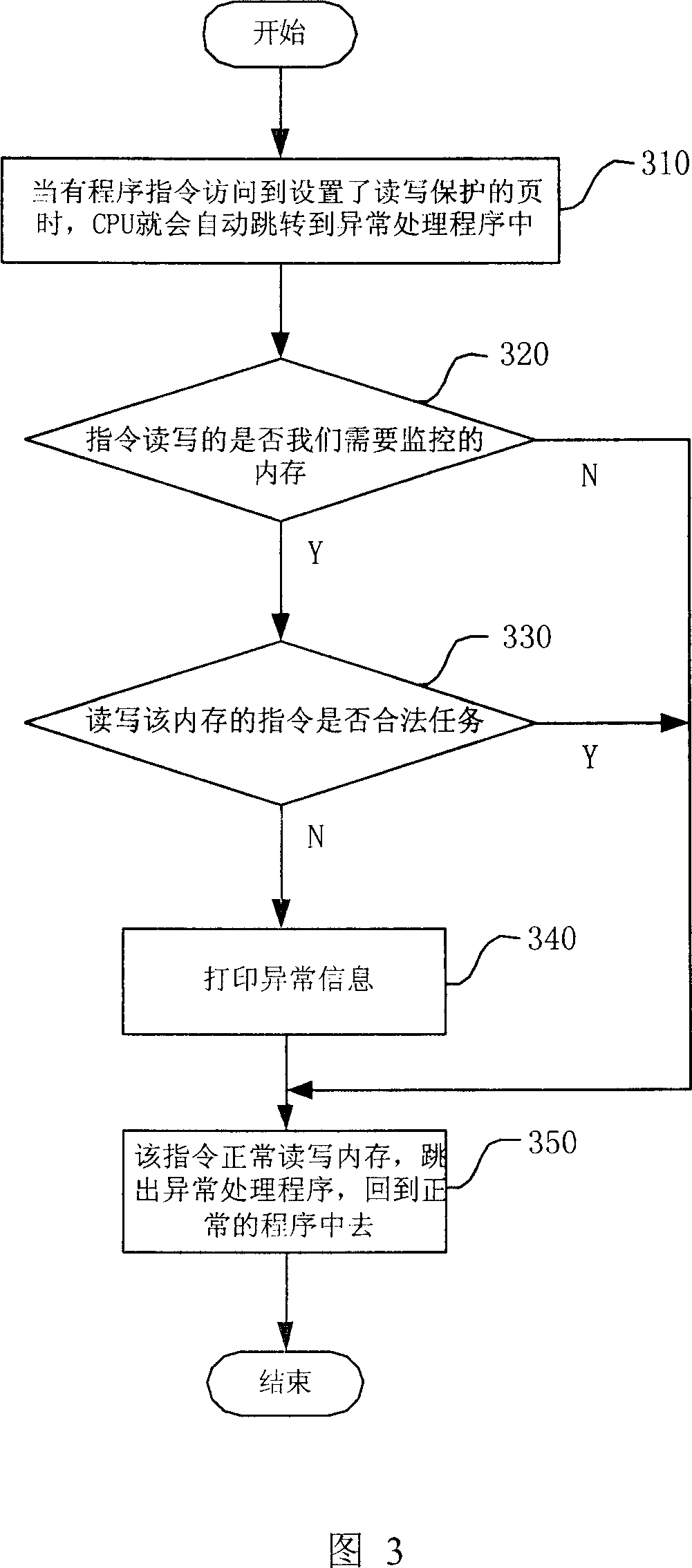
[0023] The invention is applicable to all embedded system platforms with MMU in the CPU. Below in conjunction with accompanying drawing, the inventive method is described in detail by specific examples:
[0024] First, describe the application environment of this example. The CPU used in this example is MPC8245, which has an MMU, and the page size is 4K bytes. The exception vector of data access violation is 0x300. When the authority is abnormal, the CPU will automatically jump to 0x300 to execute the exception handling program. After executing the abnormal program, the CPU will jump back to the normal program for execution. The operating system used is vxWorks (embedded real-time operating system). This operating system provides the interface functions vmStateSet and vmStateGet for setting and reading the read and write attributes of the MMU block. All this example directly uses these two functions to set the read and write properties of the MMU block. Write properties.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com