Network user identification authentication method and system
An identity authentication and network user technology, applied in the network field, can solve problems such as interfering with user operations, reducing user information security, network application hazards, etc., to achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
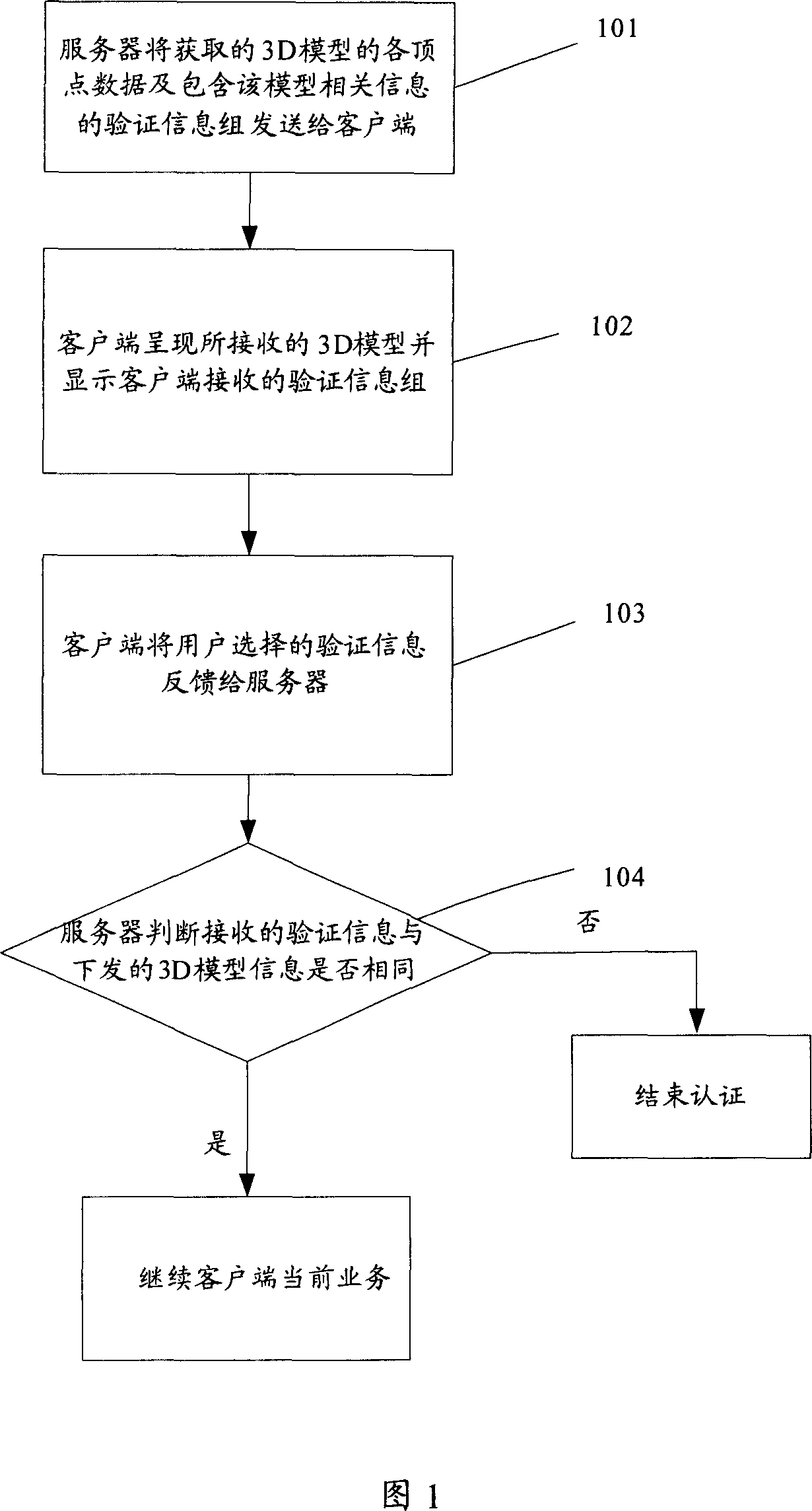
[0034] Embodiment 1, referring to accompanying drawing 1, in order to realize the purpose of the invention, the specific flow of the method provided by the present invention includes the following steps:
[0035] Step 101: the server sends the obtained vertex data of the 3D model and a verification information group including the corresponding information of the model to the client;
[0036] Among them, the 3D model library is preset on the server side, and each 3D model corresponds to a unique identifier. After the authentication procedure starts, the server randomly selects a 3D model from the 3D model library, and sends the vertex data of this model to the client. In addition, the server randomly selects more than two preset 3D models, and sends the relevant information of all the selected 3D models as a verification information group to the client;
[0037] Wherein, the verification information group includes relevant information of the selected 3D model, and the relevant ...
Embodiment 2
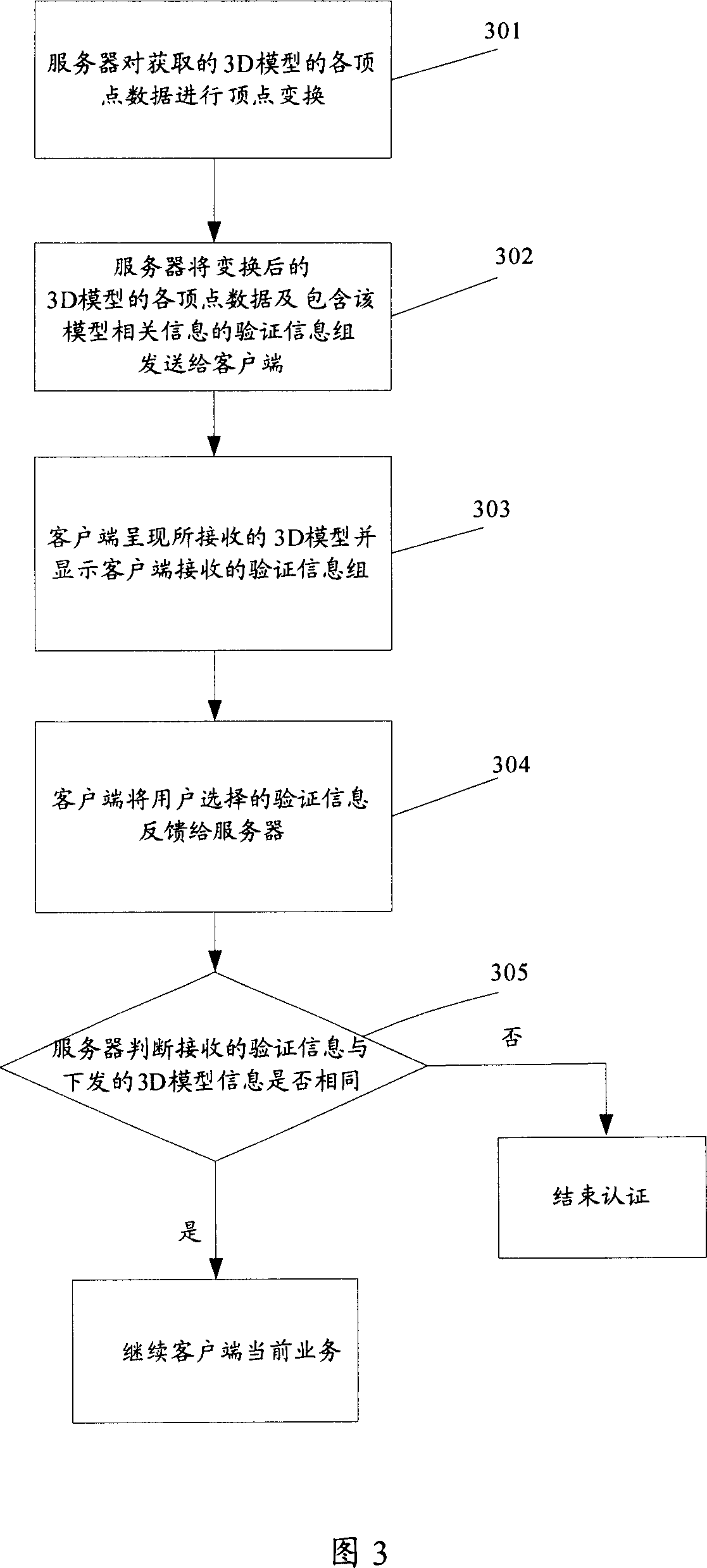
[0058] Embodiment 2. The present invention also provides an optimization method for network user identity authentication. Before the server sends the obtained vertex data of the 3D model to the client, the 3D model to be sent is subjected to interference processing, and the model is transformed. The 3D model data sent to the client is the vertex data of the model after the vertex transformation, avoiding specific external programs to save the 3D model sent by the server each time, and find out the rules of the sent model through analysis and calculation to achieve the purpose of identification.
[0059] Referring to Figure 3, the specific process of the method includes:
[0060] Step 301: the server performs vertex transformation on each vertex data of the acquired 3D model;
[0061] Among them, the 3D model library is preset on the server side, and each 3D model corresponds to a unique identifier. After the authentication procedure starts, the server randomly selects a 3D mod...
Embodiment 3
[0079] Embodiment 3, in the above two specific embodiments, in the process of network user identity authentication, in order to prevent the external program from forcibly suspending the client service every time the server authenticates the user identity, and then reconnecting to the service, In order to evade identity authentication, on the basis of the methods provided in the above two embodiments, the server sends the 3D model data and starts the preset timer at the same time. When the client does not feed back the verification information within the preset time When the user is offline, the server saves the authentication state of the client user identity, and when the user connects again, the previous identity authentication state is restored, and the user's identity authentication process continues.
[0080] Referring to Fig. 5, on the basis of the method provided in the first embodiment, the specific flow of the optimization scheme provided in this embodiment includes: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com