Multilevel aggregation-based abnormal flow control method and system
A technology for abnormal flow and control system, applied in transmission systems, digital transmission systems, data exchange networks, etc., to improve the utilization rate of network bandwidth, improve utilization efficiency, and reduce bandwidth waste.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
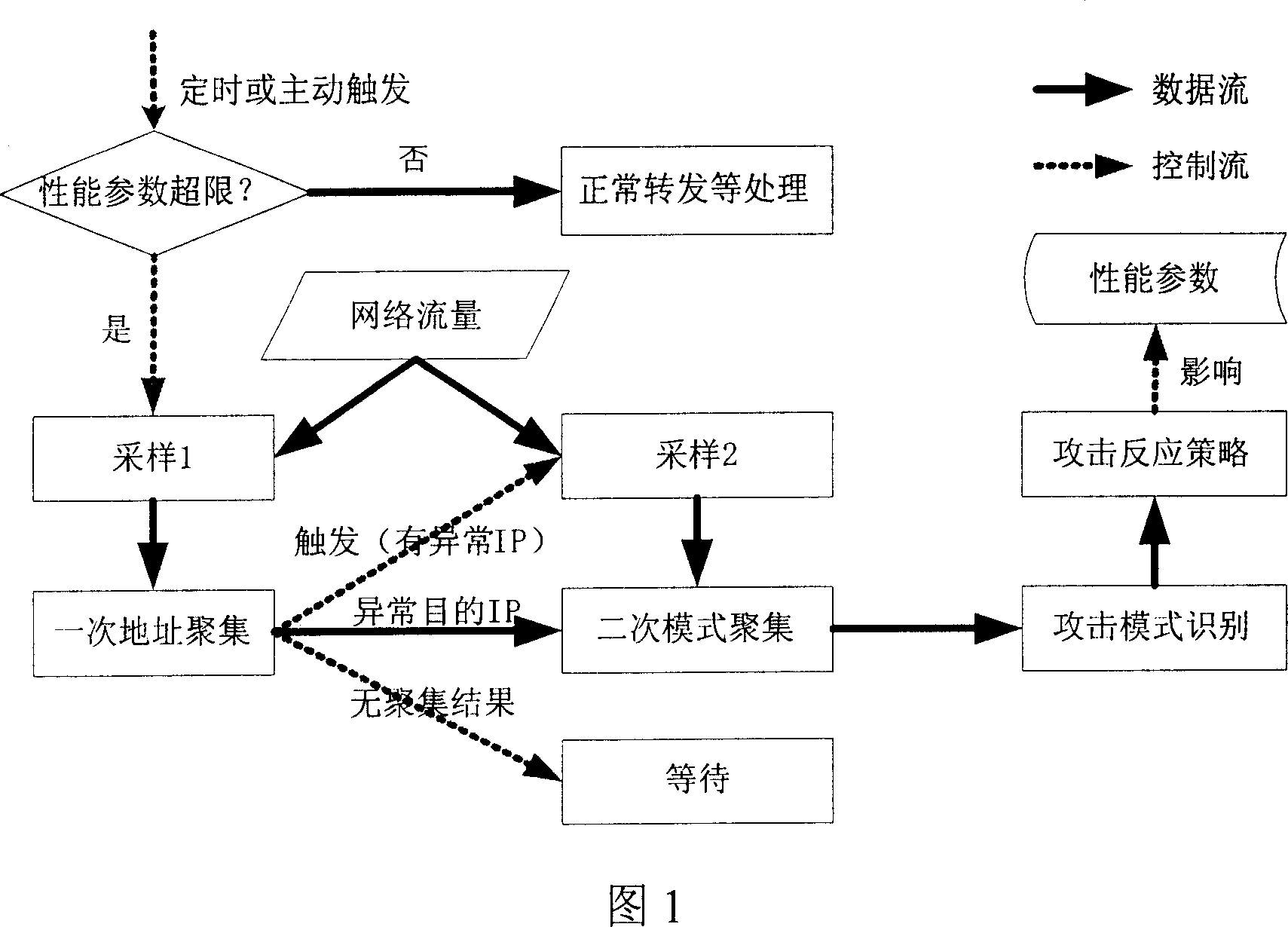
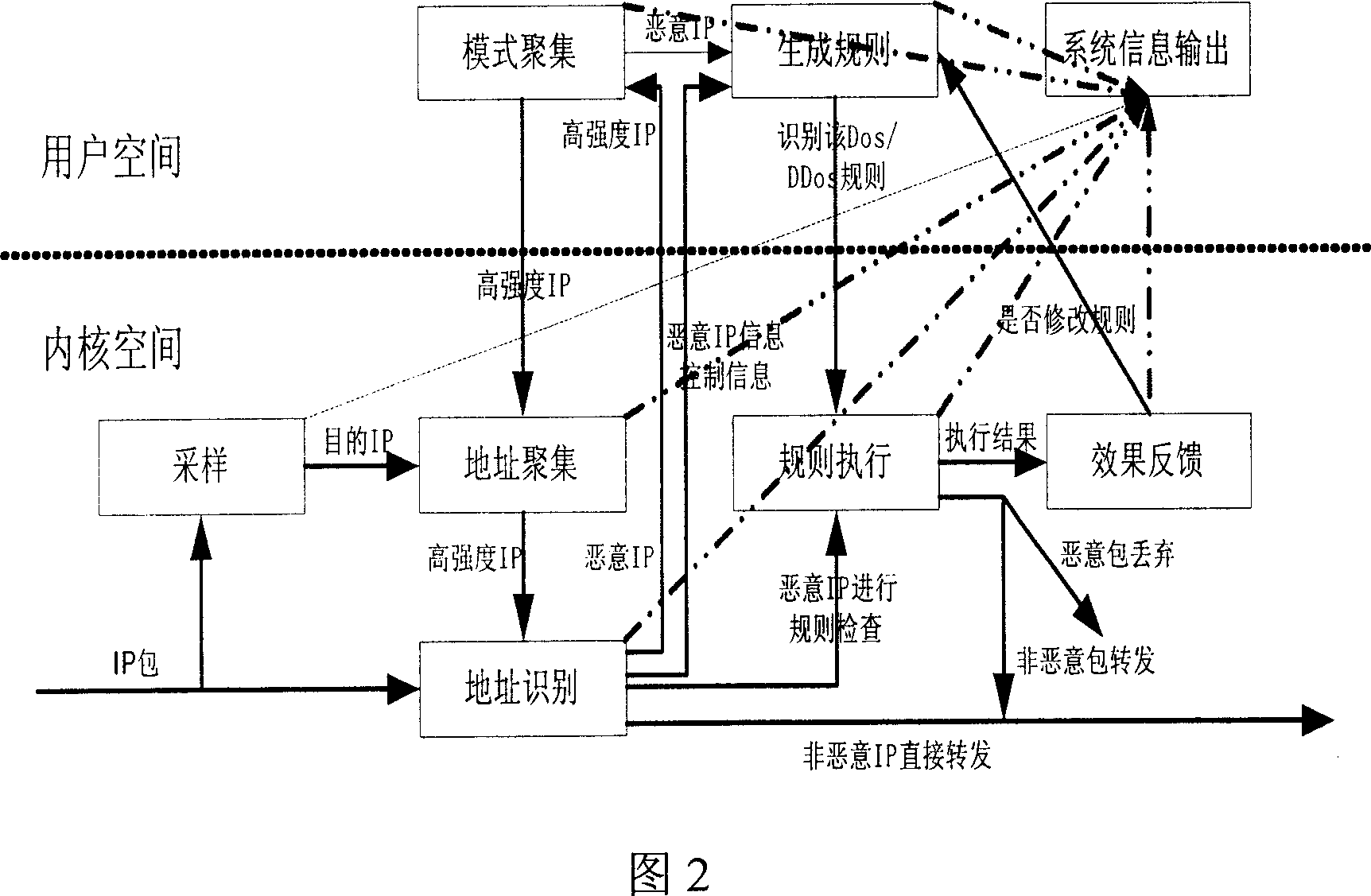
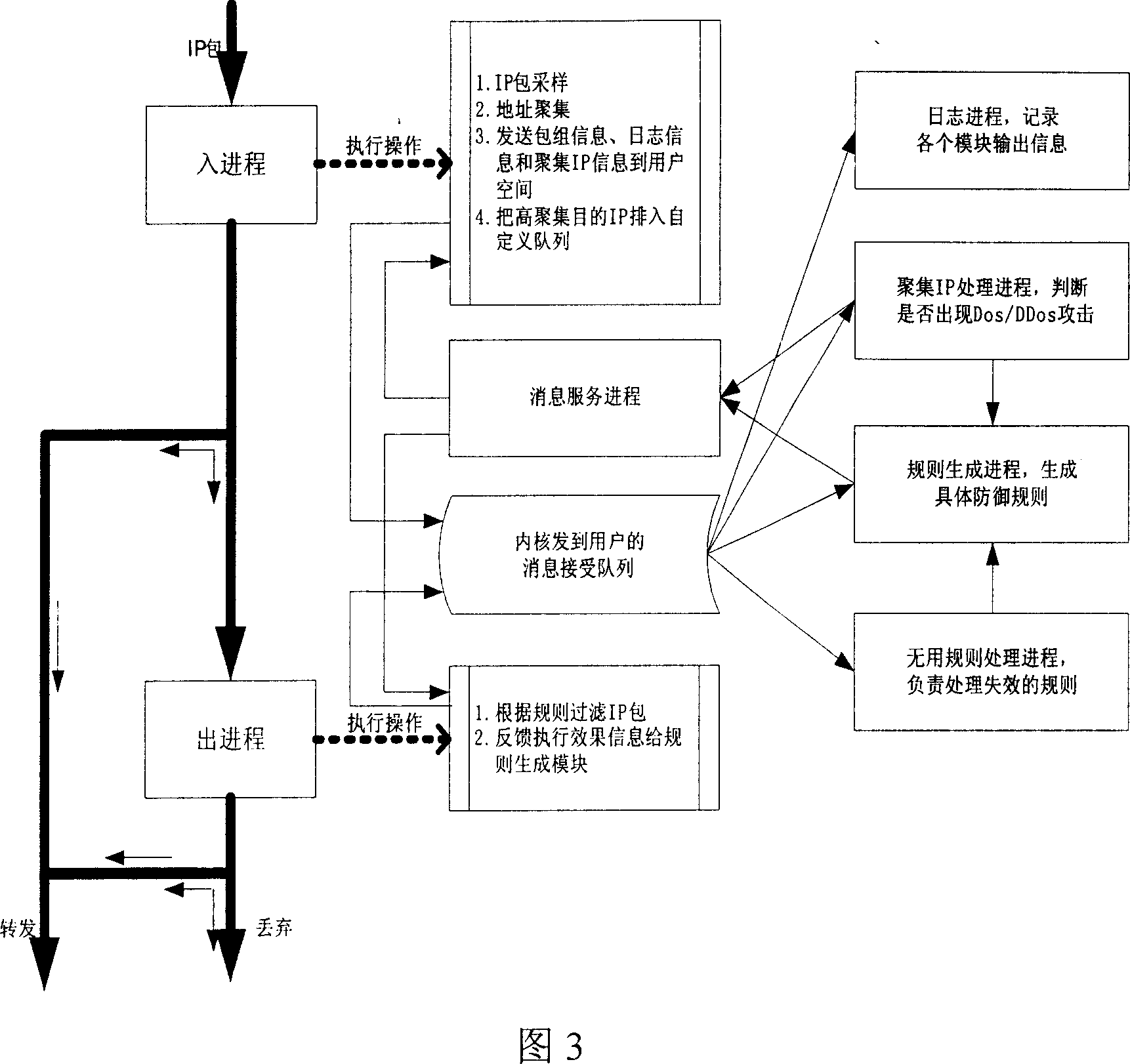
[0045] The present invention provides a brand-new A.M.A.T (Aggregates-Oriented Multi-Levels Anomaly Traffic Control Mechanism in Router) method and system based on multi-level aggregation, which has high detection efficiency and detection accuracy. The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0046] The abnormal flow control system based on multi-level aggregation of the present invention includes the following subsystems:
[0047] Abnormal traffic identification subsystem: It mainly performs data sampling for different occasions, and performs address aggregation through one-time address aggregation and its improved algorithm and cusum algorithm. The subsystem uses advanced identification algorithms and uses historical information tables to increase the accuracy of attack judgments. At the same time, it also uses an anti-shake algorithm in the address aggregation algorithm to jud...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com