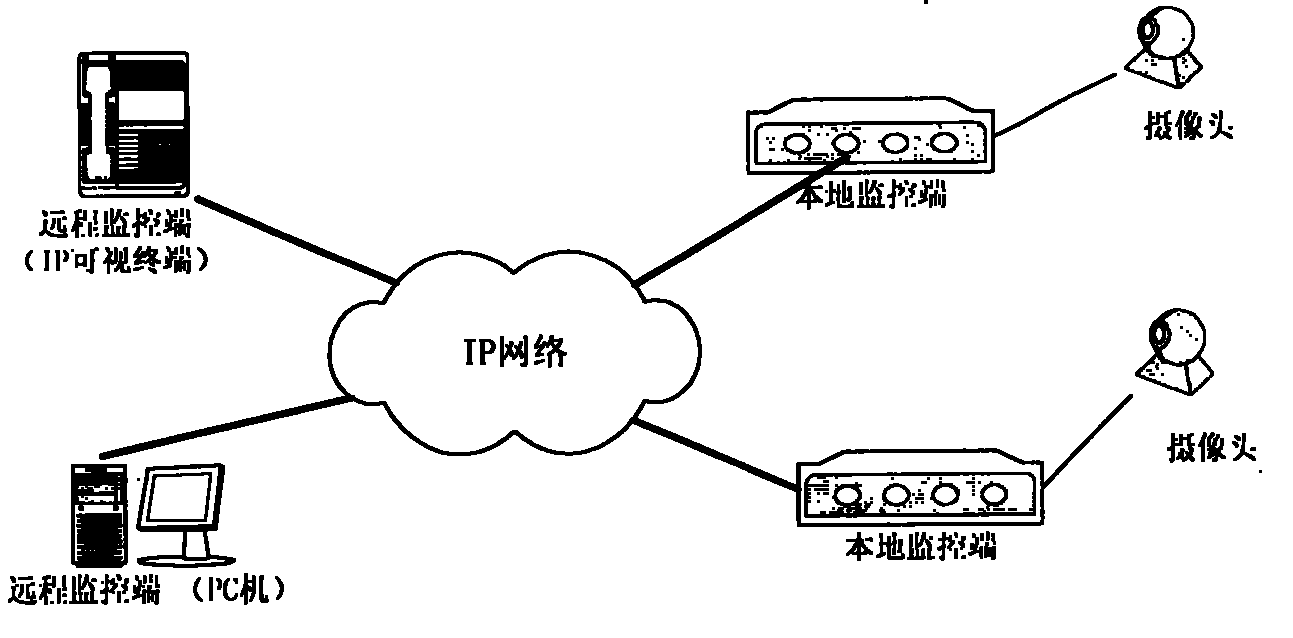
A method for implementing safe remote video monitoring
A technology of remote monitoring and remote video, applied in the field of communication, can solve the problems such as the difficulty of hackers to capture the monitoring password and the difficulty of cracking the monitoring password, so as to improve the process of call control and media control, enhance security, and improve interoperability and scalability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
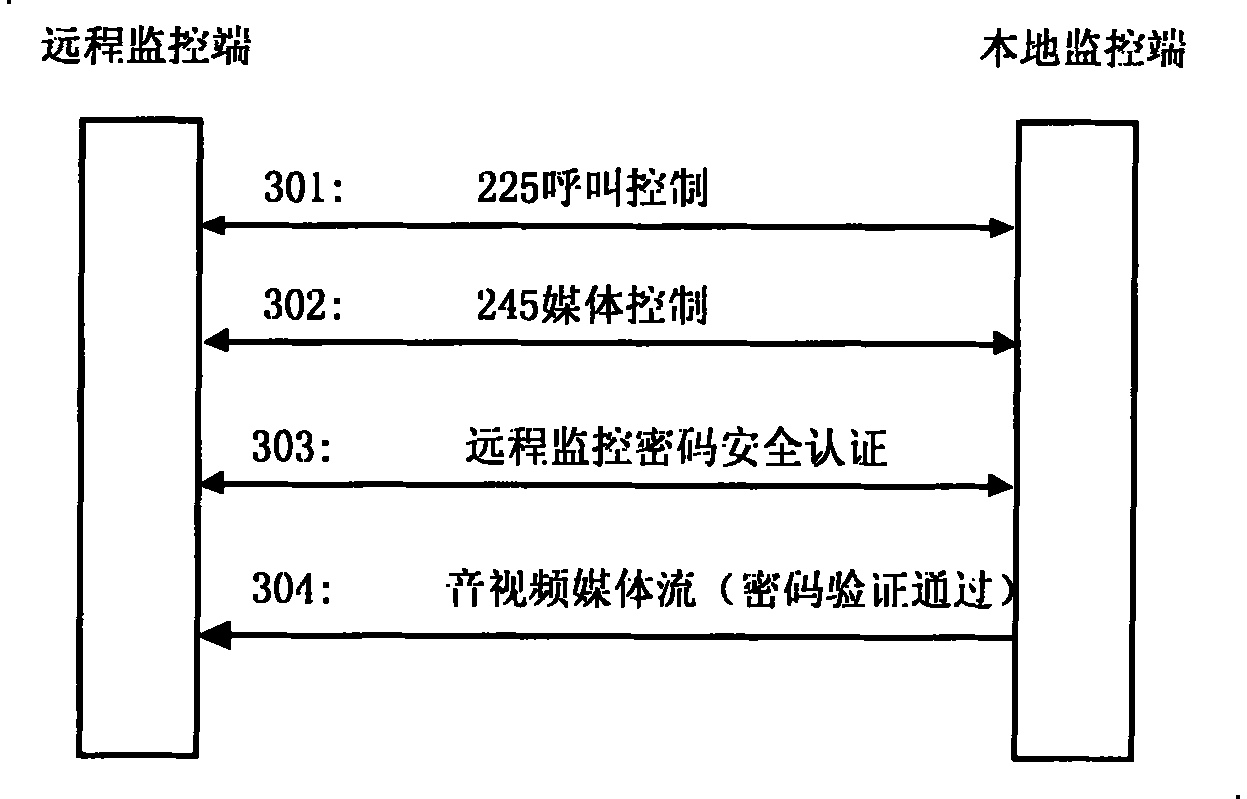
[0059] This embodiment specifies the remote monitoring communication process based on the ITU-T H.323 multimedia communication protocol, which adds security authentication in the call control process, such as Figure 4 shown.
[0060] Step 401: the user of the remote monitoring terminal calls the local monitoring terminal, and the user interface module of the remote monitoring terminal pops up a password input window, requiring the user to input the monitoring password;
[0061] Step 402: the H.323 module of the remote monitoring terminal encrypts the monitoring password;
[0062] Steps 403-404: the H.323 module of the remote monitoring terminal sends an access permission request (ARQ) to the gatekeeper as the calling terminal, and after receiving the confirmation response (ACF) from the gatekeeper, proceed to step 405;
[0063] Step 405: Fill in the remote monitoring password of the encrypted text in the nonStandardData extension field of the Setup message, and send the Setu...
Embodiment 2
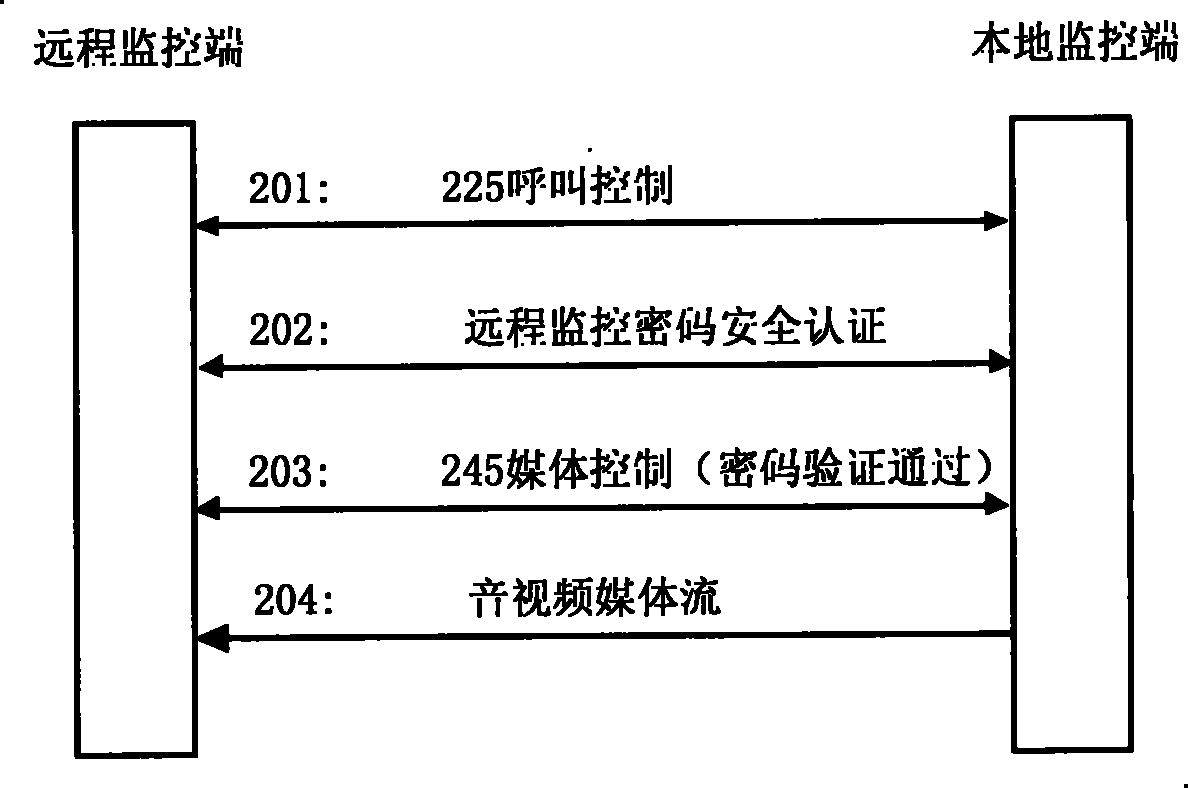
[0071] The present embodiment specifies based on the ITU-T H.323 multimedia communication protocol, after the H.225 call control process and the H.245 media control process are completed, before entering the audio and video media data transmission, the remote monitoring communication flow of security authentication is added, Such as Figure 5 shown.
[0072] Step 501: the remote monitoring terminal user calls the local monitoring terminal;
[0073] Steps 502-503: The H.323 module of the remote monitoring terminal sends an access permission request (ARQ) to the gatekeeper (GK1) as the calling terminal, and after receiving the confirmation response (ACF) from the gatekeeper (GK1), continue to step 504;
[0074] Step 504: the remote monitoring terminal sends the H.225 Setup message to the local monitoring terminal;
[0075] Step 505: After receiving the Setup message, the local monitoring terminal sends a CallProceeding message to the remote monitoring terminal;
[0076] Steps...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com