System and method for verifying delivery and integrity of electronic messages
a technology of electronic messages and verification methods, applied in the field of systems and methods for verifying the delivery and integrity of electronic messages, can solve the problems of cumbersome systems, slow use, and various obstacles to an
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
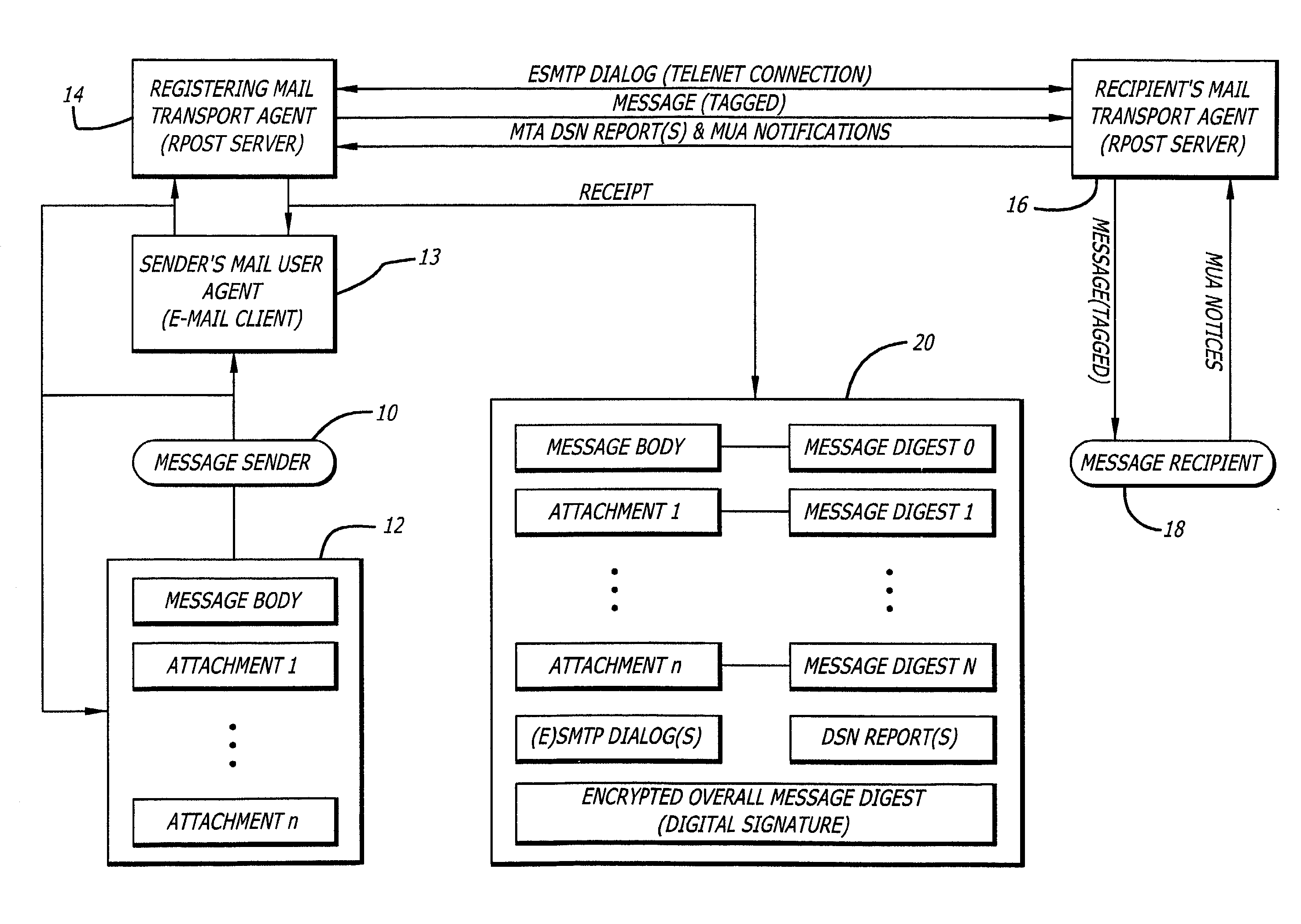
[0032]FIG. 1 is a system diagram of an invention disclosed and claimed in co-pending application Ser. No. 09 / 626,577, in which embodiment outgoing messages are made of record by being transmitted by a special Mail Transport Agent (MTA).
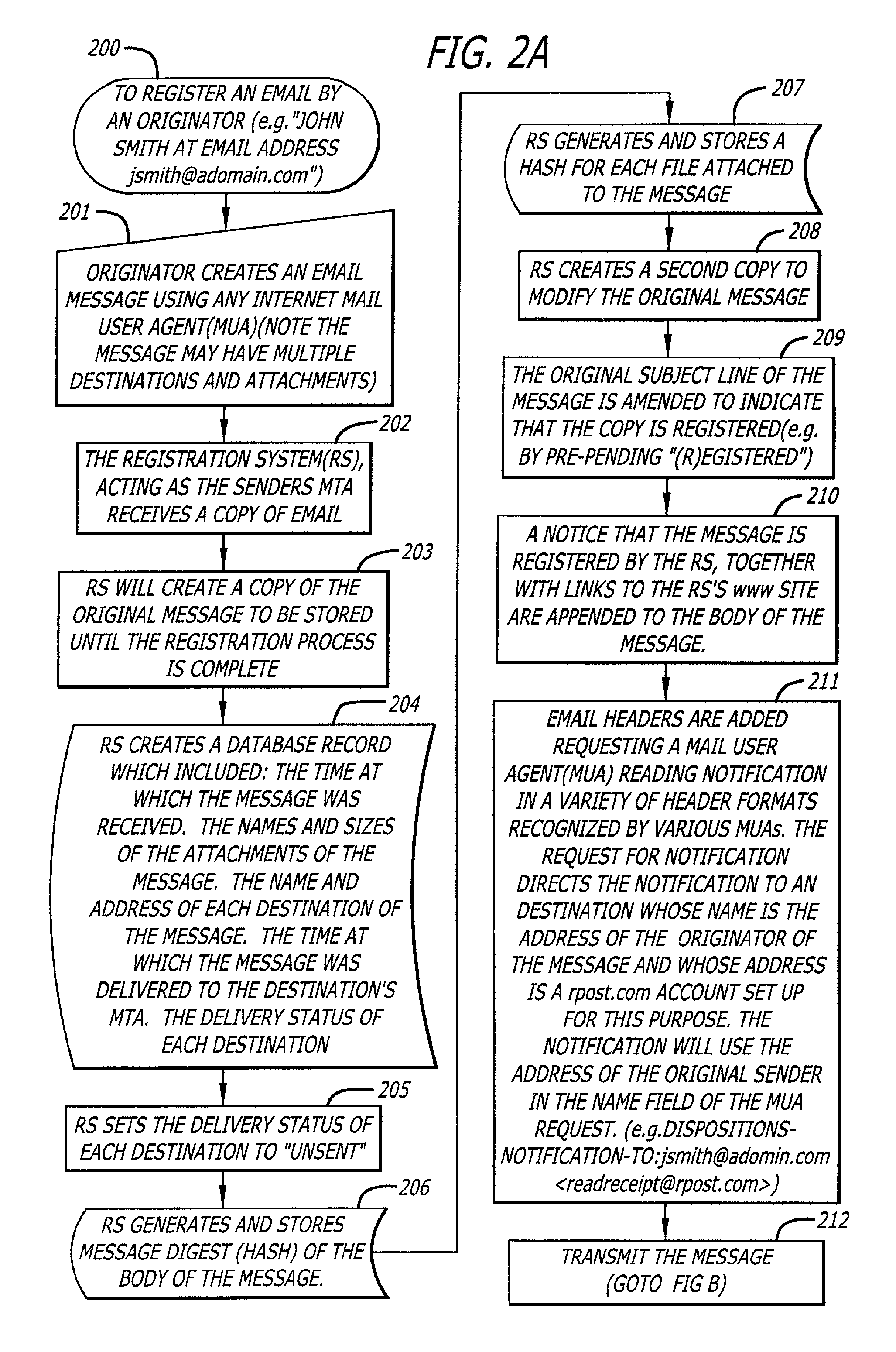
[0033]FIGS. 2-2F constitute a representative flow diagram for making an outgoing e-mail of record according to the embodiment of FIG. 1.
second embodiment
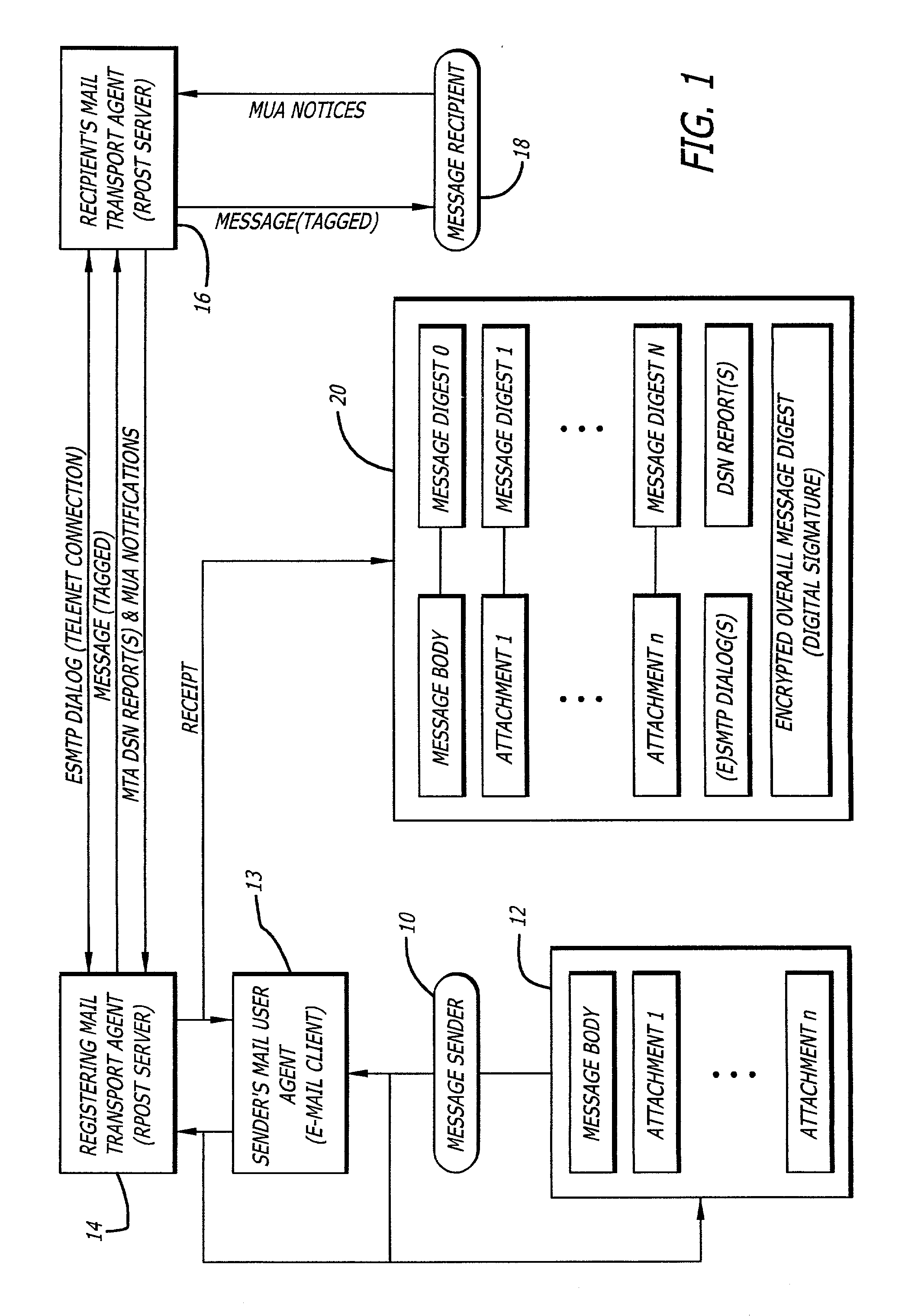
[0034]FIG. 3 is a system diagram of the invention disclosed and claimed in co-pending application Ser. No. 09 / 626,577, in which embodiment senders may direct a Mail Transport Agent to transmit selected messages through a separate Mail Transport Agent constructed to make the selected messages of record.
third embodiment
[0035]FIG. 4 is a system diagram of the invention disclosed and claimed in co-pending application Ser. No. 09 / 626,577, in which carbon copies (cc's) of outgoing messages are sent to a special server to be made of record.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com