Unauthorized Device Detection Device And Unauthorized Device Detection System
a detection device and unauthorized technology, applied in the field of unauthorized device detection devices and unauthorized device detection systems, can solve the problems of high labor and cost, the decryption key may be revealed,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
1. Unauthorized Device Detection System 1
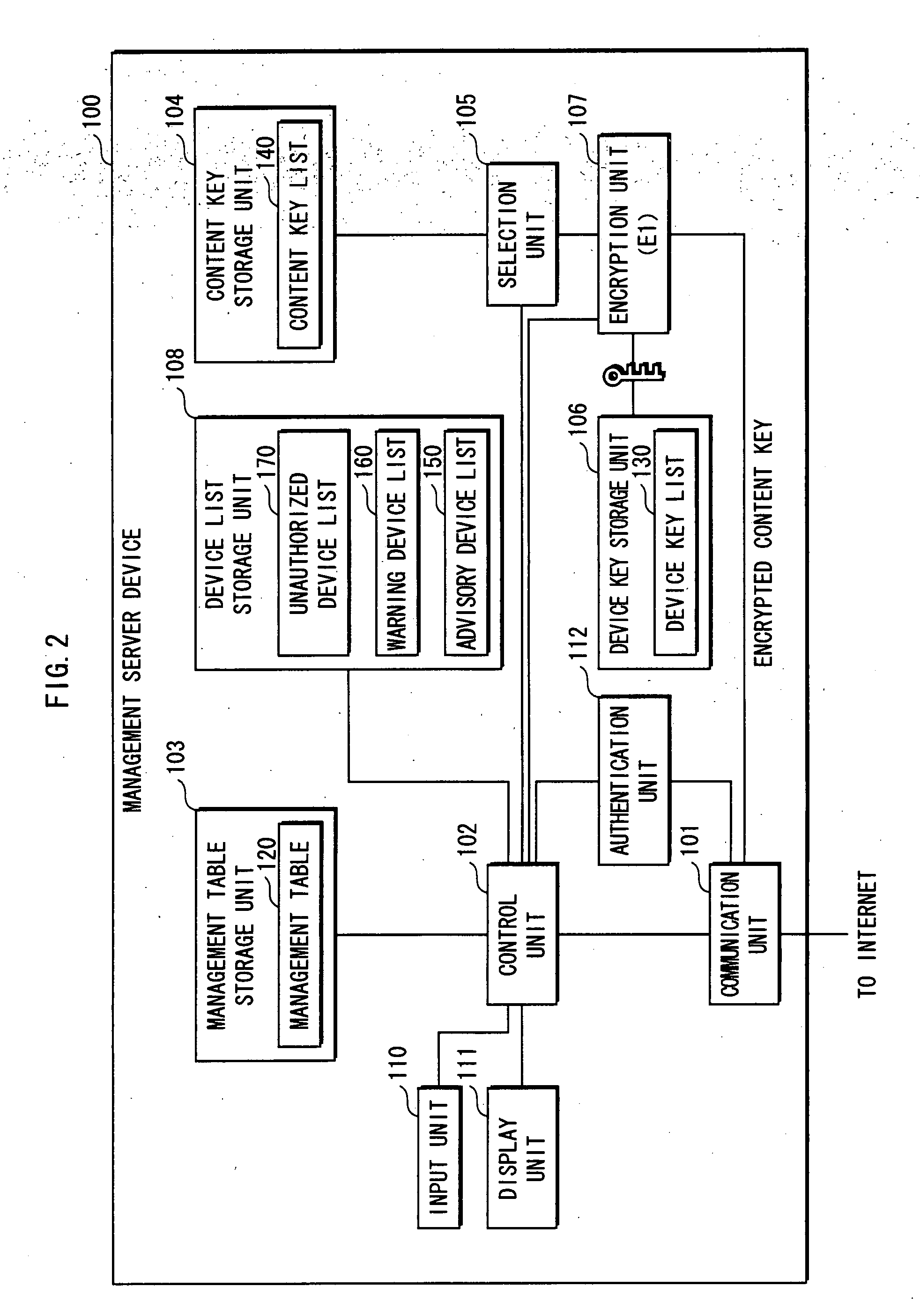
[0064] The following describes an unauthorized device detection system 1 as one embodiment of the present invention.
1.1. Overview of the Unauthorized Device Detection System 1
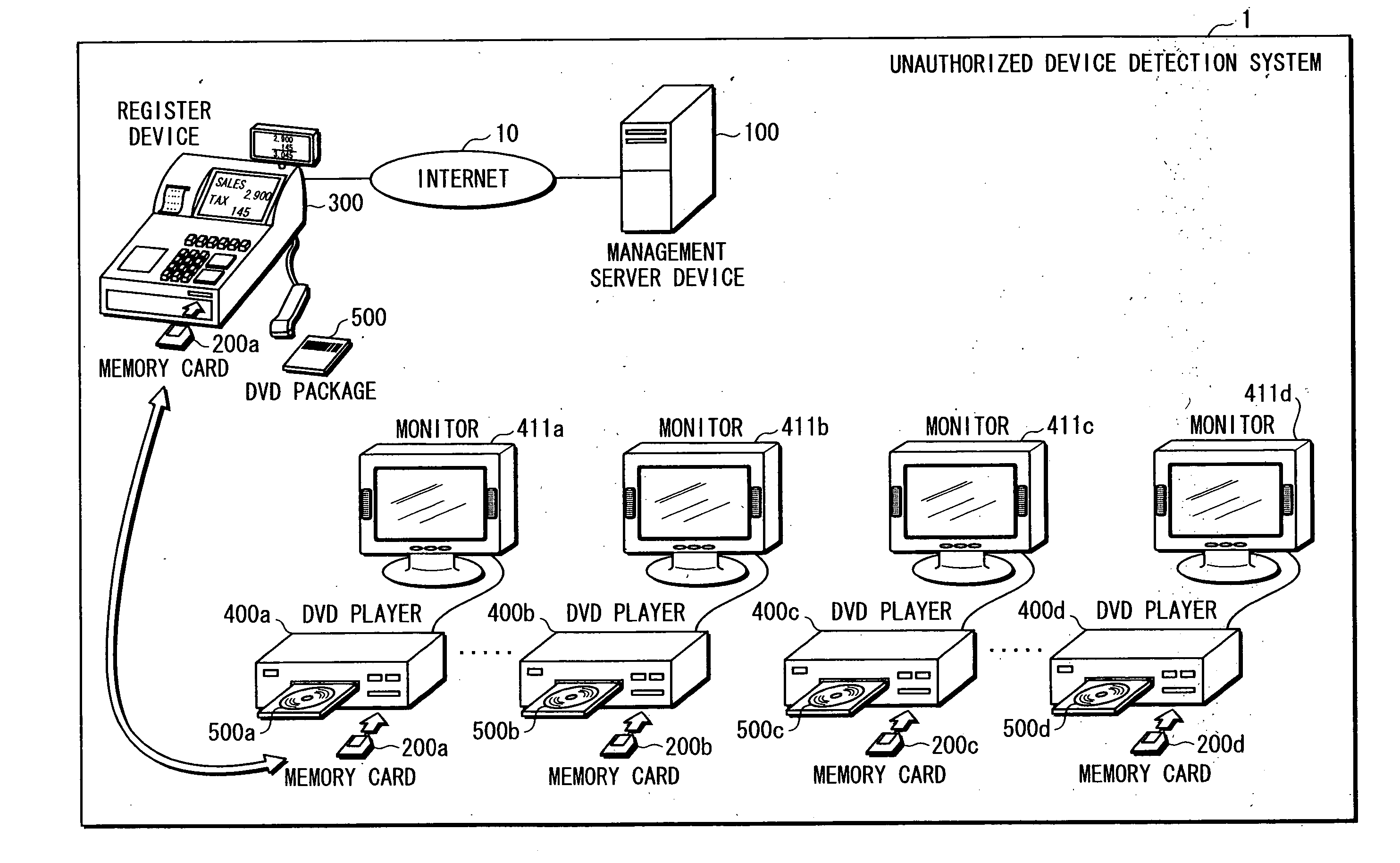
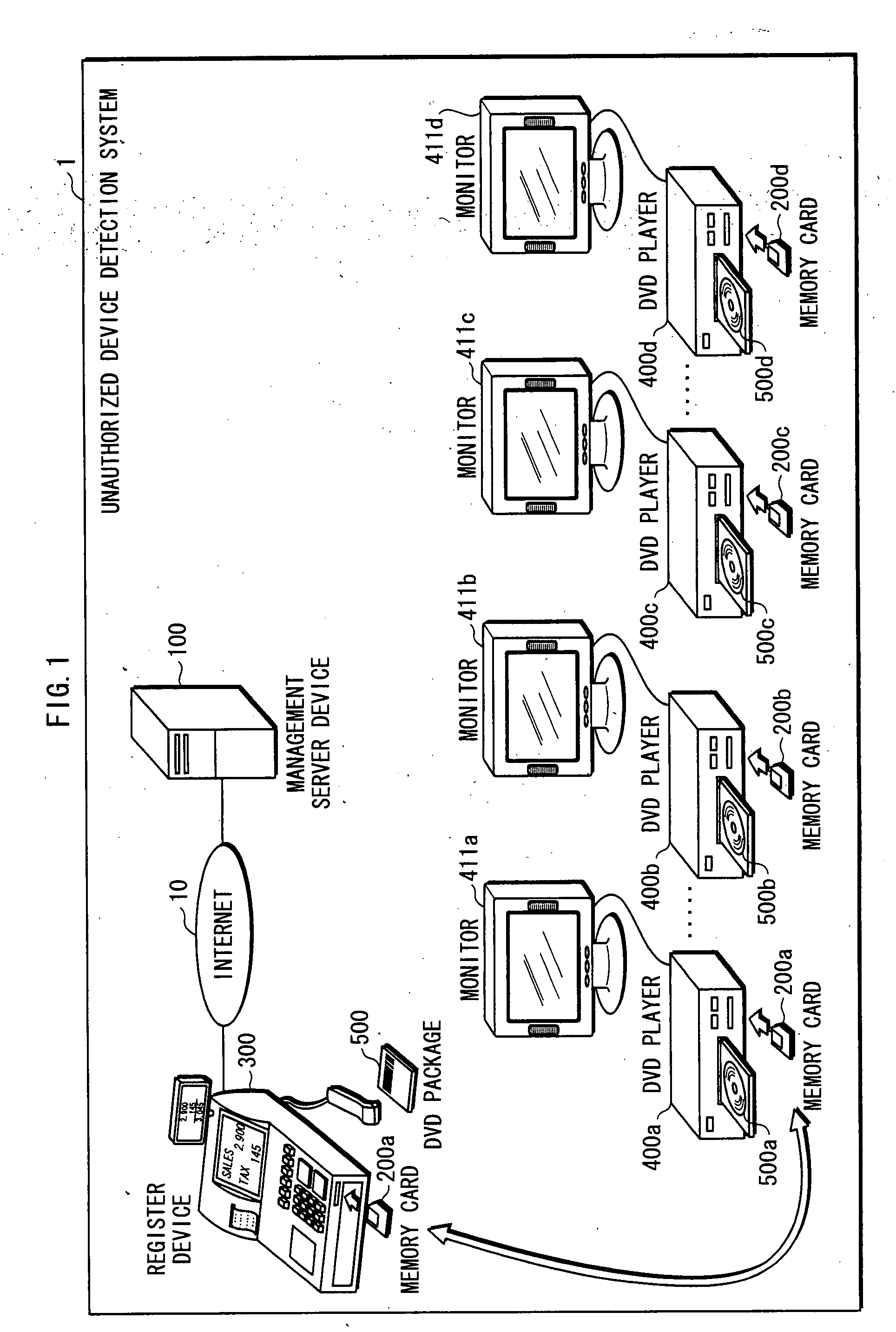
[0065] The unauthorized device detection system 1 includes a management server device 100, a register device 300, and DVD players 400a, . . . , 400b, 400c, . . . , 400d, as shown in FIG. 1. The management server device 100 and the register device 300 are connected to each other via an internet 10.
[0066] The DVD players 400a, . . . , 400b are authorized players manufactured by an authorized manufacturer, and each hold a device ID for uniquely identifying the DVD player itself. For example, a total number of the DVD players 400a, . . . , 400b is 10,000.
[0067] Meanwhile, the DVD players 400c, . . . , 400d are players manufactured by an unauthorized manufacturer copying the DVD player 400b, and each hold a same device ID as the one for uniquely identifying the DVD playe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com