Method and system to provide security implementation for storage devices
a storage device and security technology, applied in the field of security in portable digital devices, can solve problems such as avoiding data loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example implementation
[0039]The product would be shipped as CD+Public, meaning the storage device, when connected to a PC, would provide a CD icon and a storage icon in the My Computer window, by pretending to the operating system of the host to be or to contain a CD drive. In the CD portion, there would be an application resident to make the device “Secured”. When launched, the program prompts the user for a password and then encrypts the secure partition with the master key and IV, as described above.
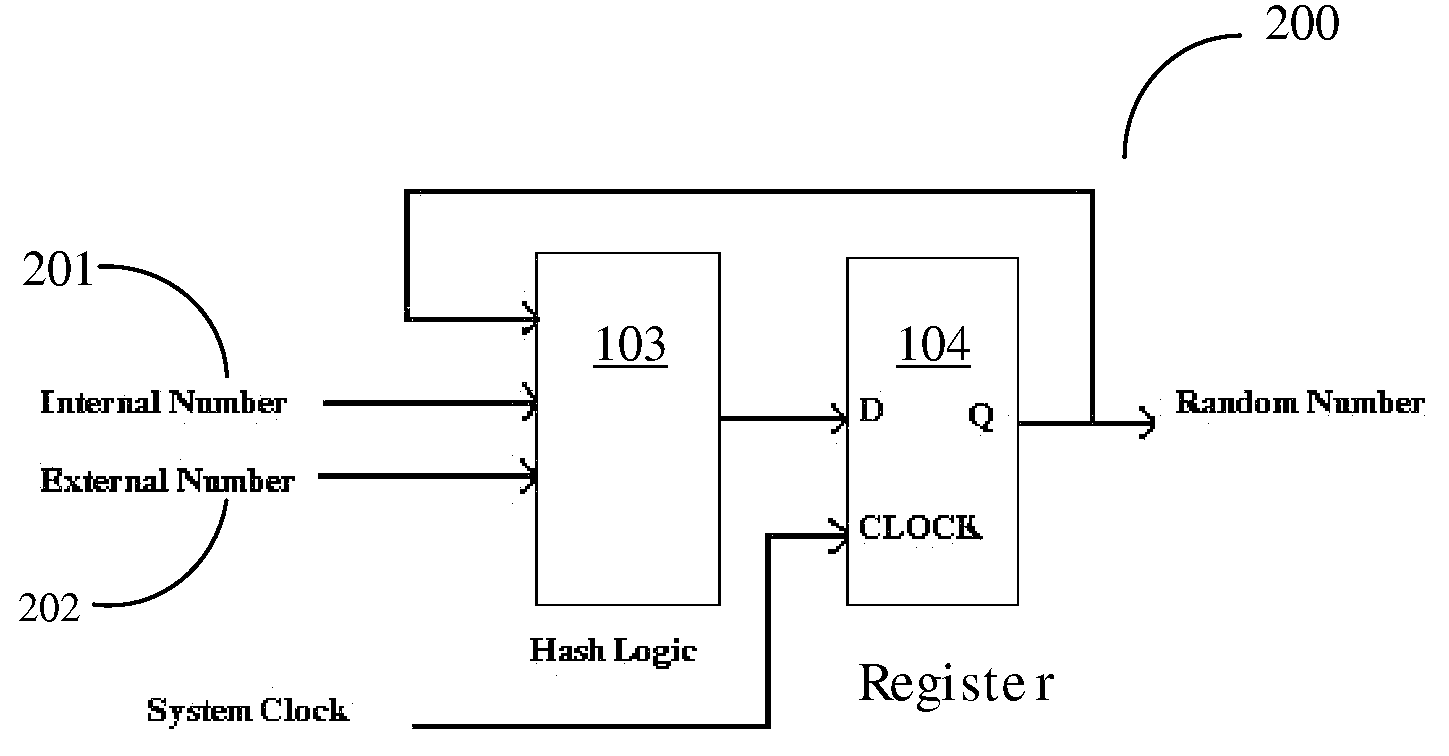
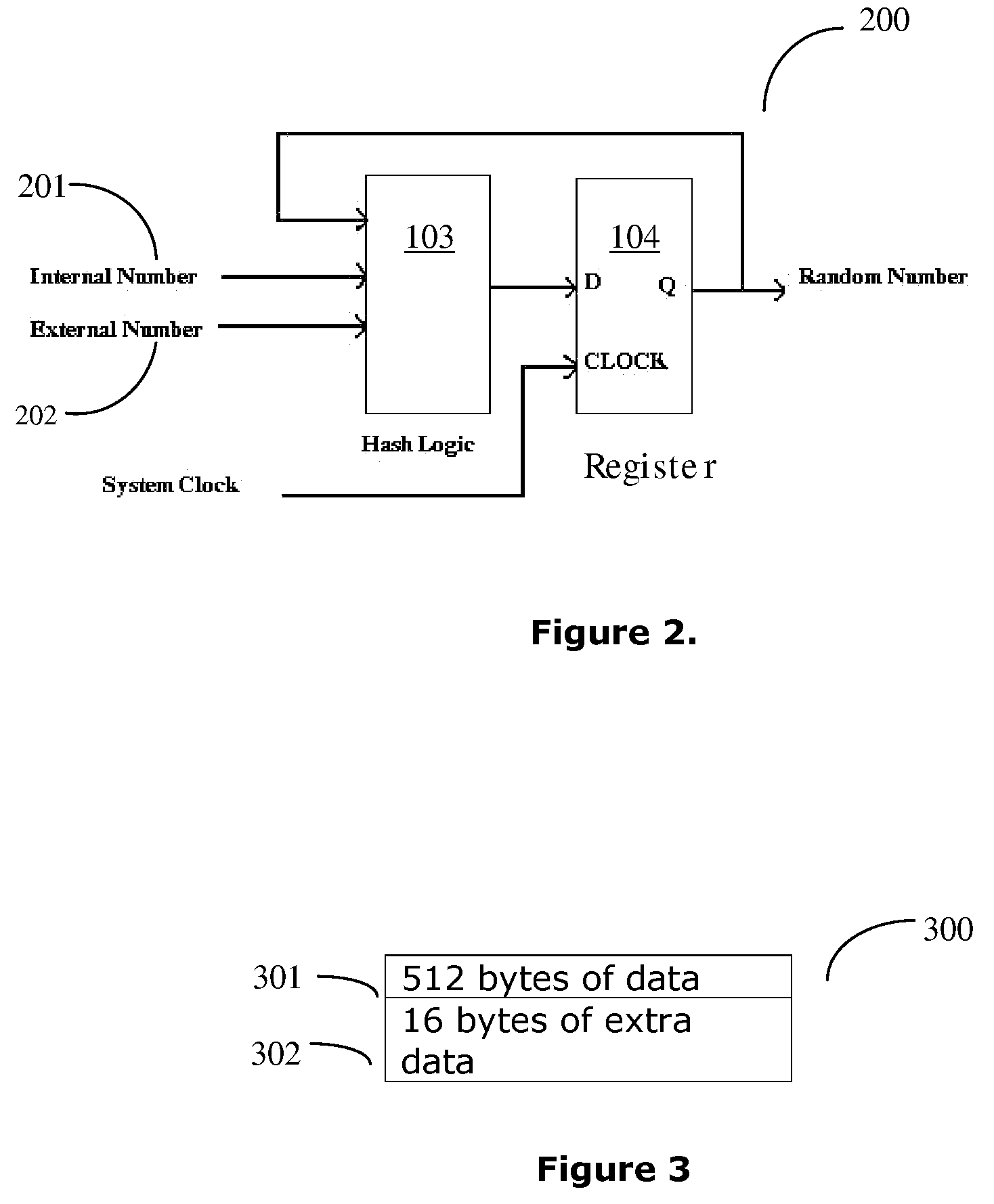
[0040]One method to generate a 32-bit random number in a USB storage system is to use the USB frame number (a random number that is generated by the USB host, such as a PC, every millisecond) and an internal counter in the controller that is incremented every system clock and that has a random starting value that cannot be predicted, as previously discussed in the description of FIG. 1.
[0041]FIG. 7 shows a block diagram of such an exemplary asynchronous random generator 700, using both a frame number 701 a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com