Encryption And Decryption Device In Wireless Portable Internet System,And Method Thereof
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example
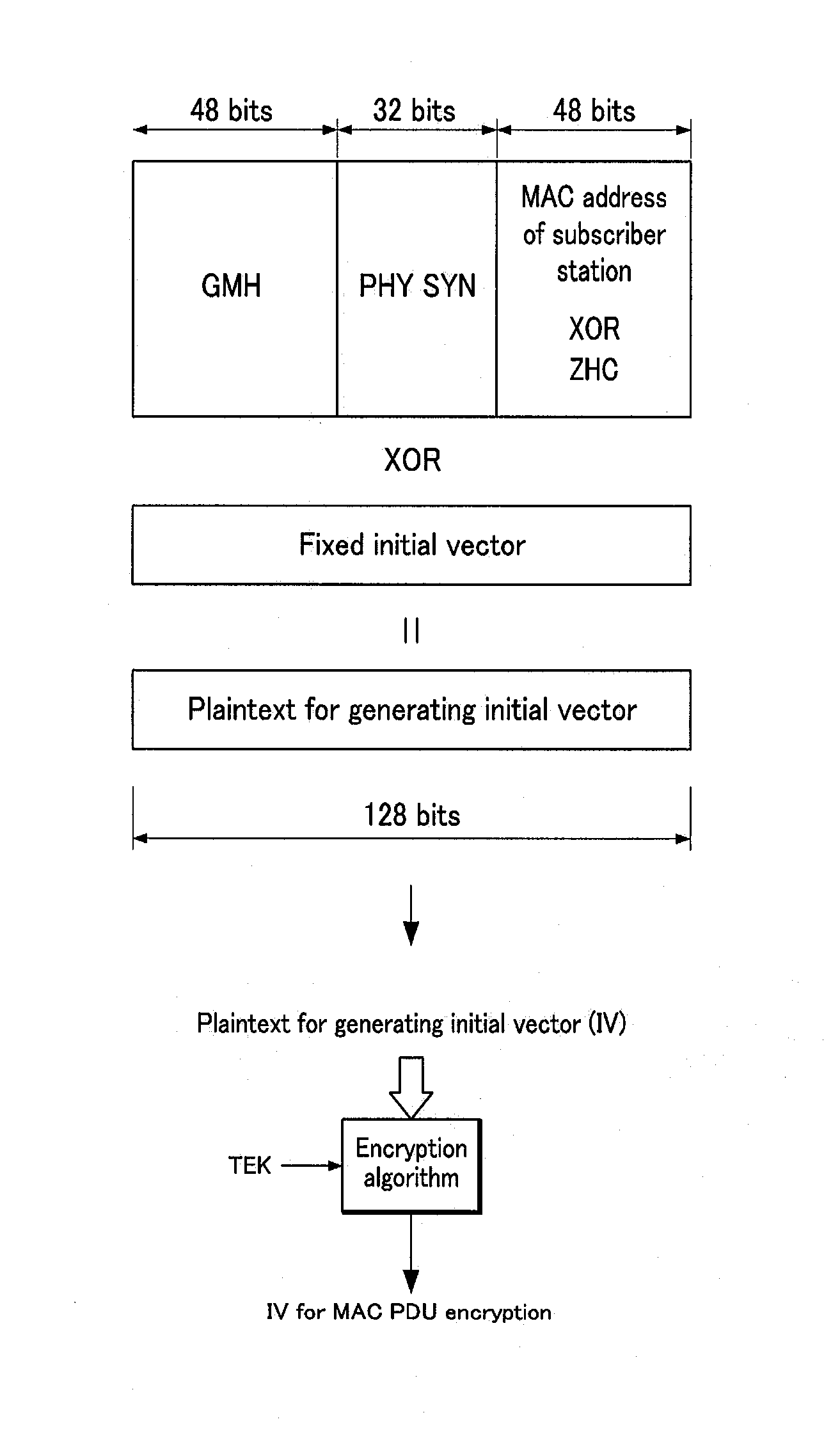
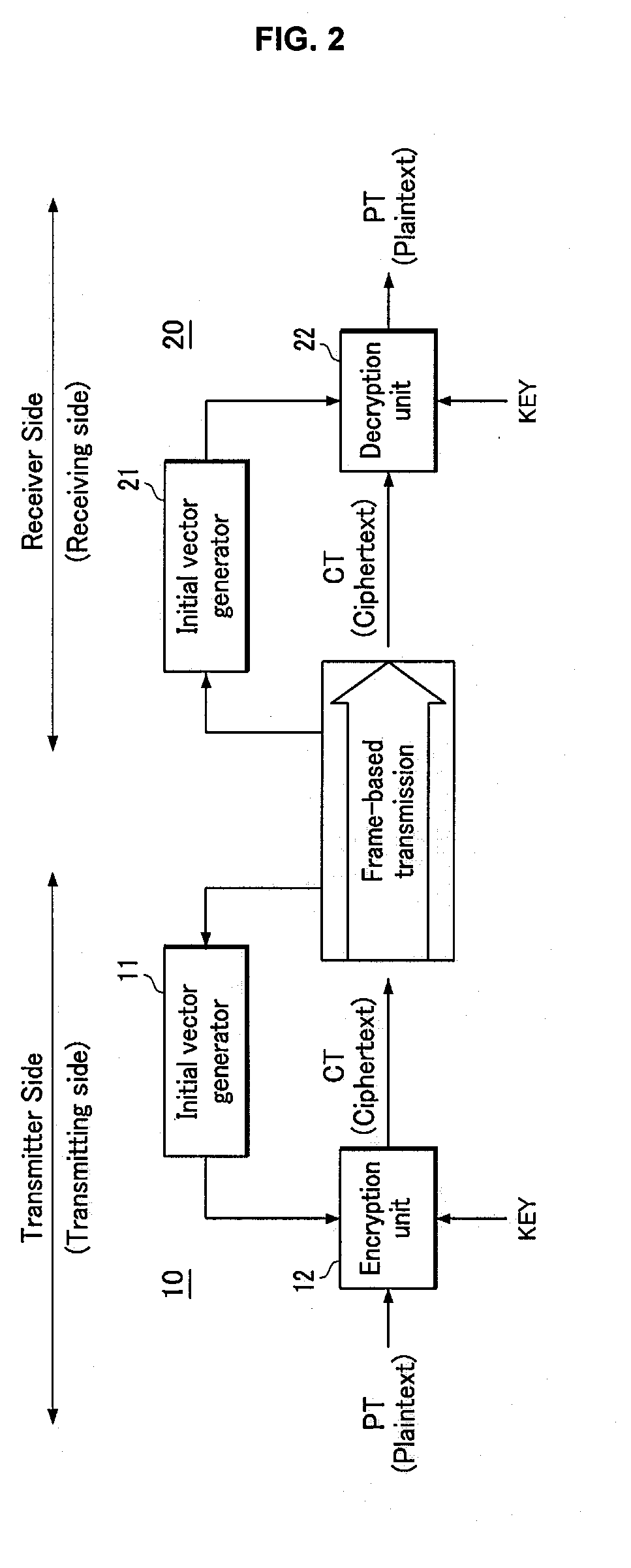
[0107]As shown in FIG. 12, similar to the initial vector generator in the second exemplary embodiment, each initial vector generator 11 and 21 according to the third exemplary embodiment of the present invention includes a frame number determination module 111, a header extract module 112, an identifier determination module 113, a logic operation module 114, a generation module 115, and a ZHC 116, but differing from the second exemplary embodiment, the initial vector generators 11 and 21 according to the third exemplary embodiment of the present invention further include a counter correction unit 117 for correcting a count value.
[0108]A loss of a broadcast frame may occur due to various causes in the wireless channel. Therefore, when counting the number of zero hits of the object field, e.g., the PHY SYN field, a frame that includes the field may be lost, thereby causing malfunction of the zero hit counter so that the zero hit counter may not be able to count the zero hit.
[0109]Ther...
Example
[0127]Such an RN field may be selectively applied to the first to third exemplary embodiments of the present invention. In this case, assume that an RN field is added to each message in addition to a header field, a data field, and a CRC field in the first to the third exemplary embodiments.
[0128]In the case of the first exemplary embodiment, a PHY SYN field may be replaced with an RN field. In this case, the frame number determination module 111 of the initial vector generator 11 determines a random value of the RN field. Therefore, the initial vector generator 11 generates an initial vector for encryption by using GMH field information of the message, a MAC address of a subscriber station which is selectively used, and the random value of the RN field that replaces a frame number of a PHY SYN field, and encrypts and decrypts a message.
[0129]In addition, in the case of applying the RN field, the concept of the zero hit counter may be applied as in the second exemplary embodiment to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com