Method and device for entering a computer database password
a database and password technology, applied in the computer field, can solve the problems of insufficient security of passwords, small number of password patterns that could be generated, and unauthorized persons' supervision and repeating of processes, so as to improve the number of possible combinations, prevent learning, and protect the user's password.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
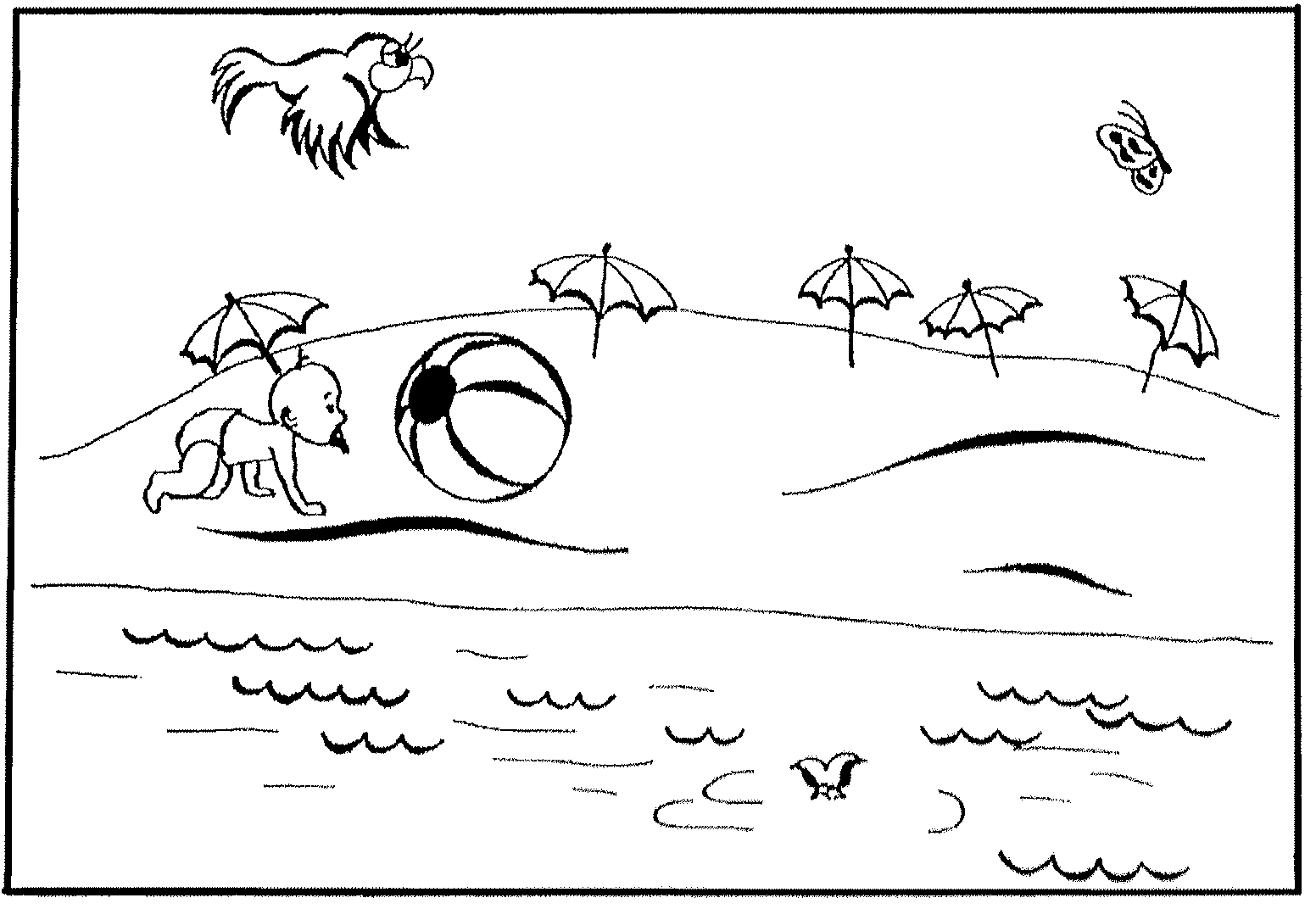
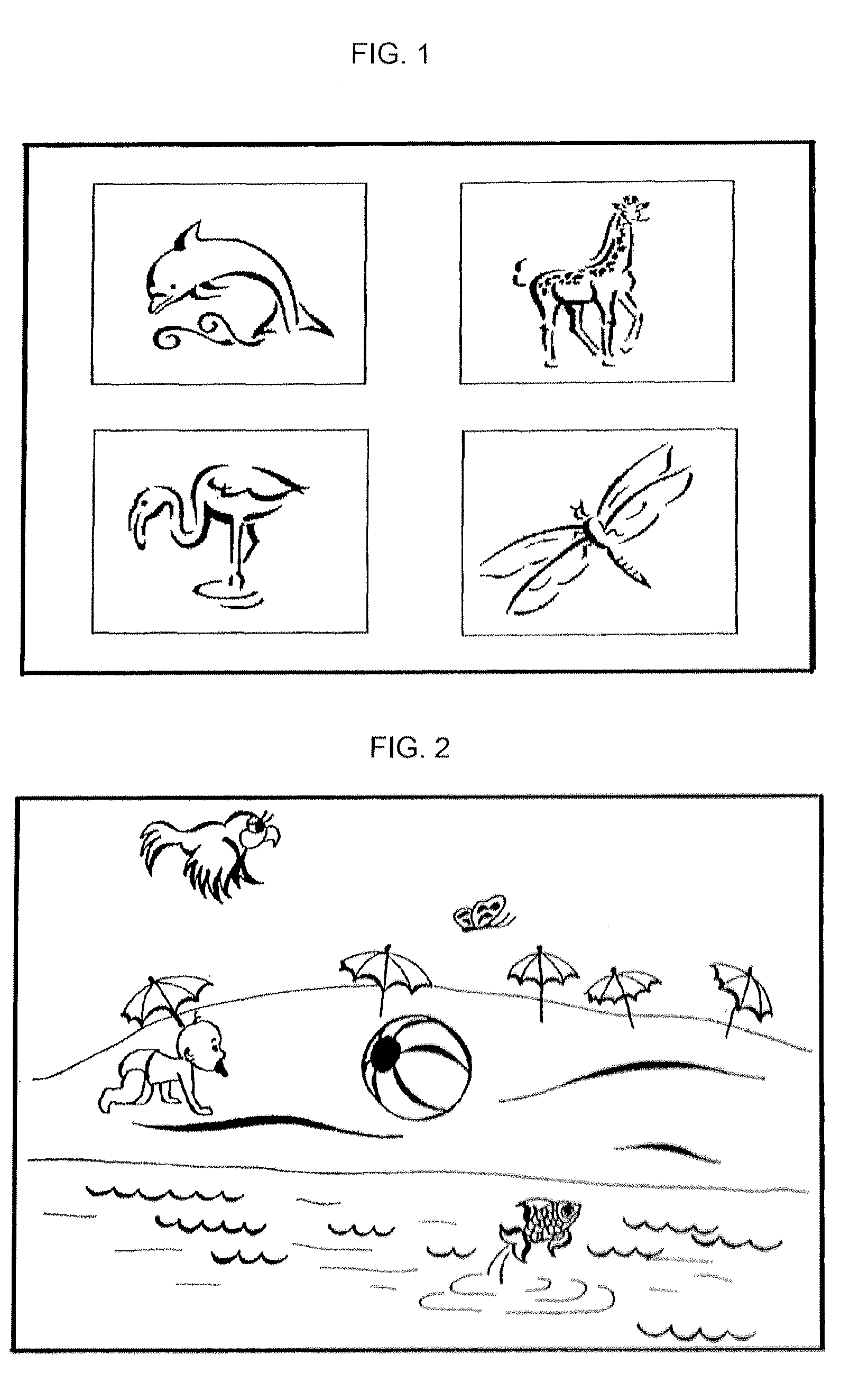
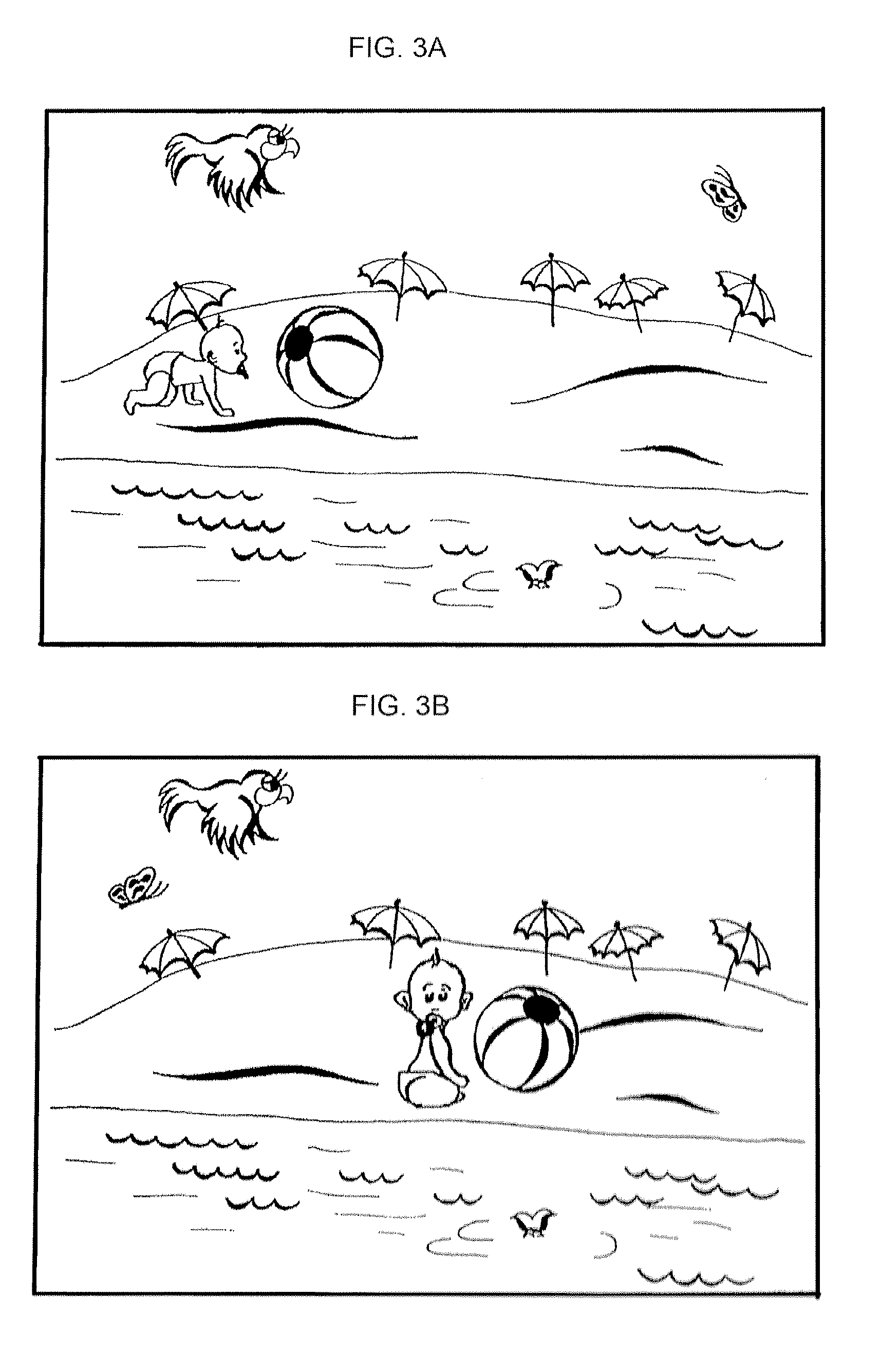
[0027]In a first embodiment of a method is accordance with the present invention (FIG. 1), a user predetermines a number of screens, type of images to be displayed of each of the screens, a number of objects to be displayed on each of the screens, and an order and screen on which the objects of the dynamic image are to be selected. The user further determines which contact means (e.g. left or right button of a mouse or a certain key on a keyboard, etc.) will be used to point the time of appearance of a predetermined object on a screen. The predetermined object of the dynamic image is an object that has taken a user-conceived position in space and / or state in time.
[0028]The user can further determine which of the screens are significant for entering a password and which are not, i.e. which of the screens will be used to enhance security of the password entry. Respective user's settings are registered in software.
[0029]According to FIG. 1, a user is suggested to monitor appearance of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com