Overflow per segment
a technology of overflow and segment, applied in the field of over, can solve problems such as the overflow of the mark stack, the type of memory allocation and de-allocation suffers from a number of drawbacks, and the use of malicious attacks to compromise data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
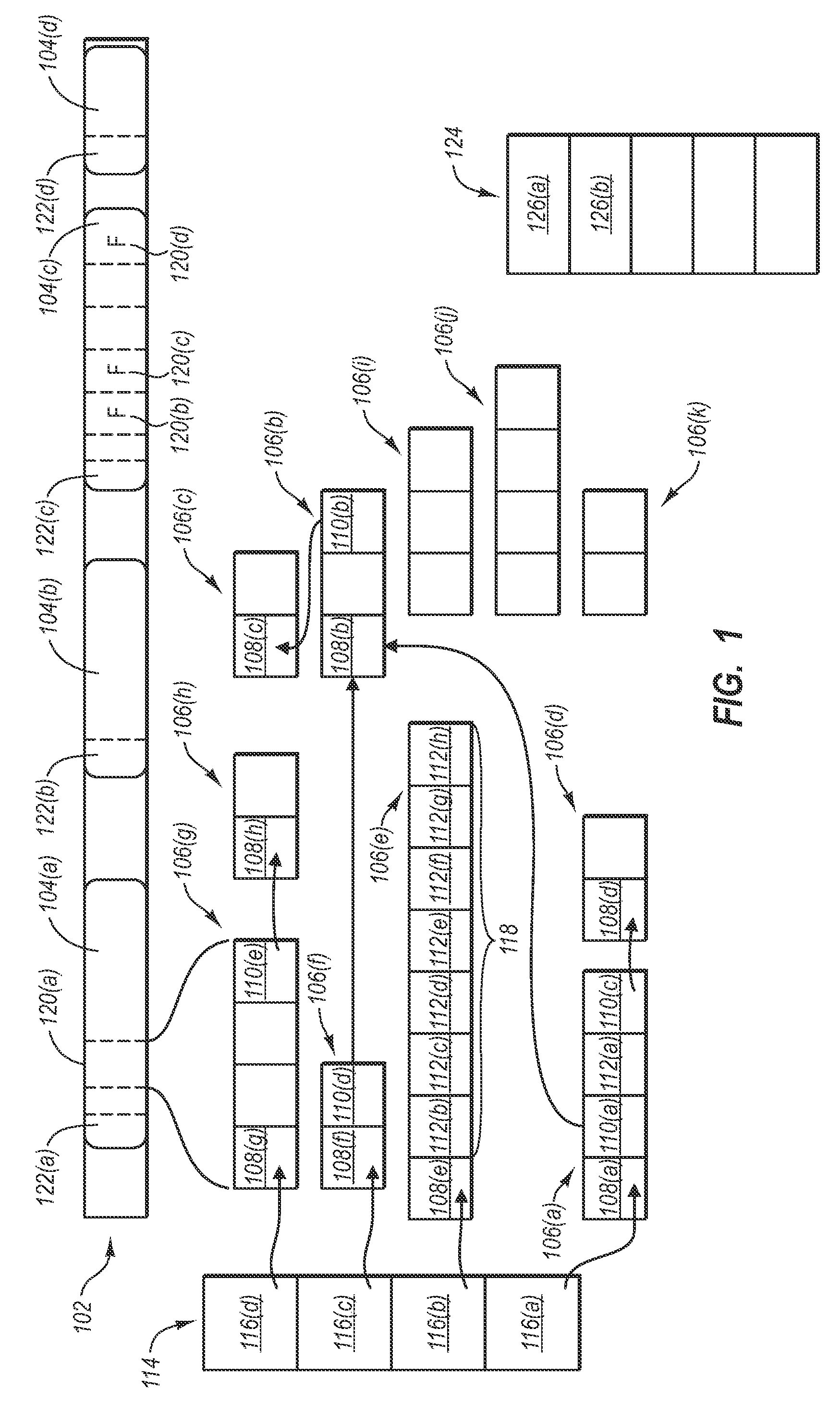
[0017]Referring now to FIG. 1, an example of various garbage collection activities and allocation activities are illustrated. FIG. 1 illustrates an object heap 102. The object heap 102 comprises system memory, such as system RAM or other system memory that can be used to store objects. The object heap 102 includes a number of segments 104. Segments 104 may be assigned by the operating system for in storing managed objects. It should be noted that this point that references to designators in the Figures may be made generically or specifically when the Figures include more than one instance of an item illustrated. For example a generic reference may include a reference to segments 104 generically while a reference to a specific segment may include an additional designators appended to a reference such as is illustrated in FIG. 1 where the specific references to segments 104 include additional designators such that the specific references may be 104(a), 104(b), 104(c), and 104(d).
[0018...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com