Obtaining and assessing objective data relating to network resources
a network resource and objective data technology, applied in the field of obtaining and assessing objective data relating to network resources, can solve the problems of user's inability to determine whether his transmission is done, most users' inability to detect untrustworthy targets, and user's inability to use highly technical information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
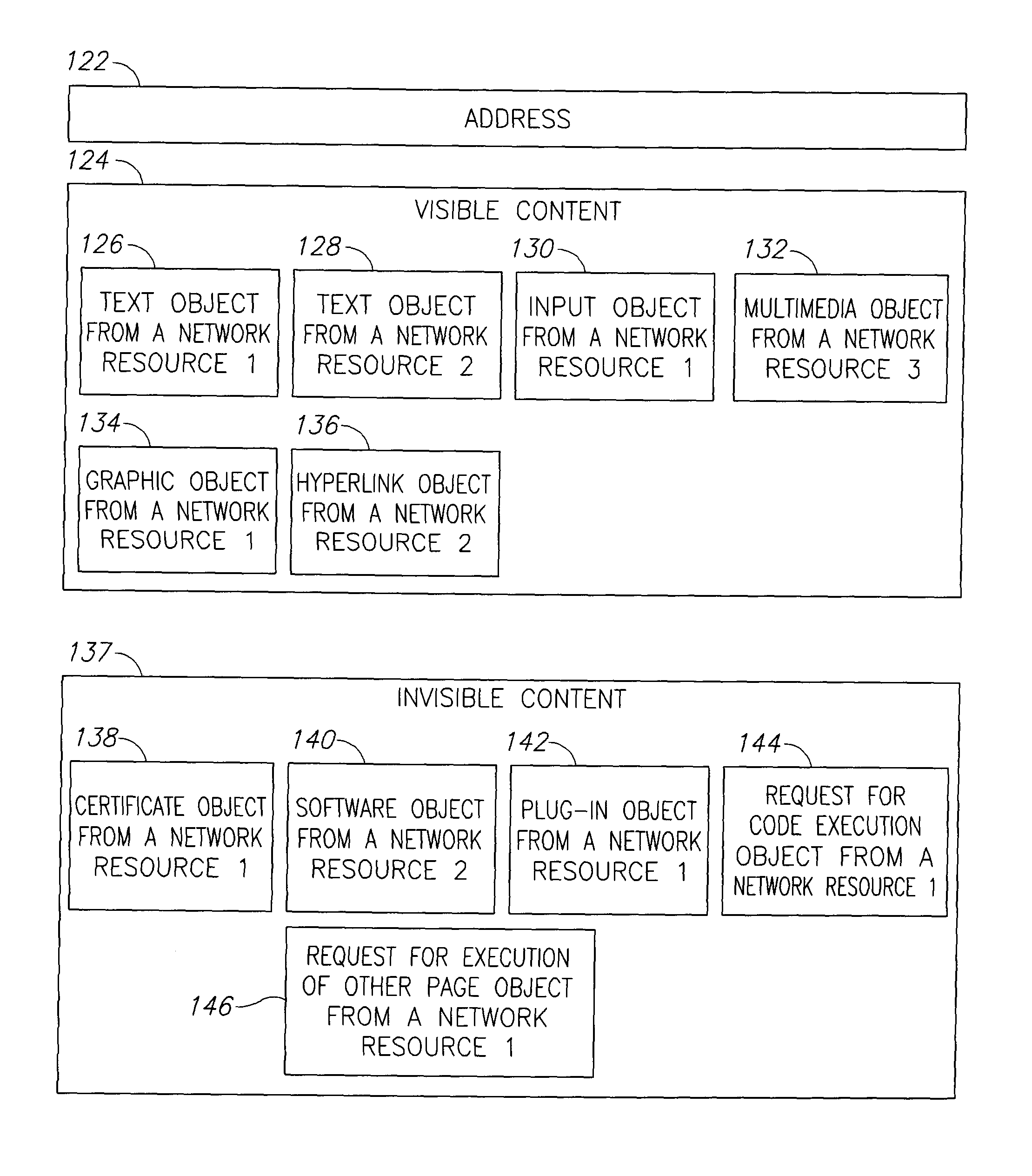
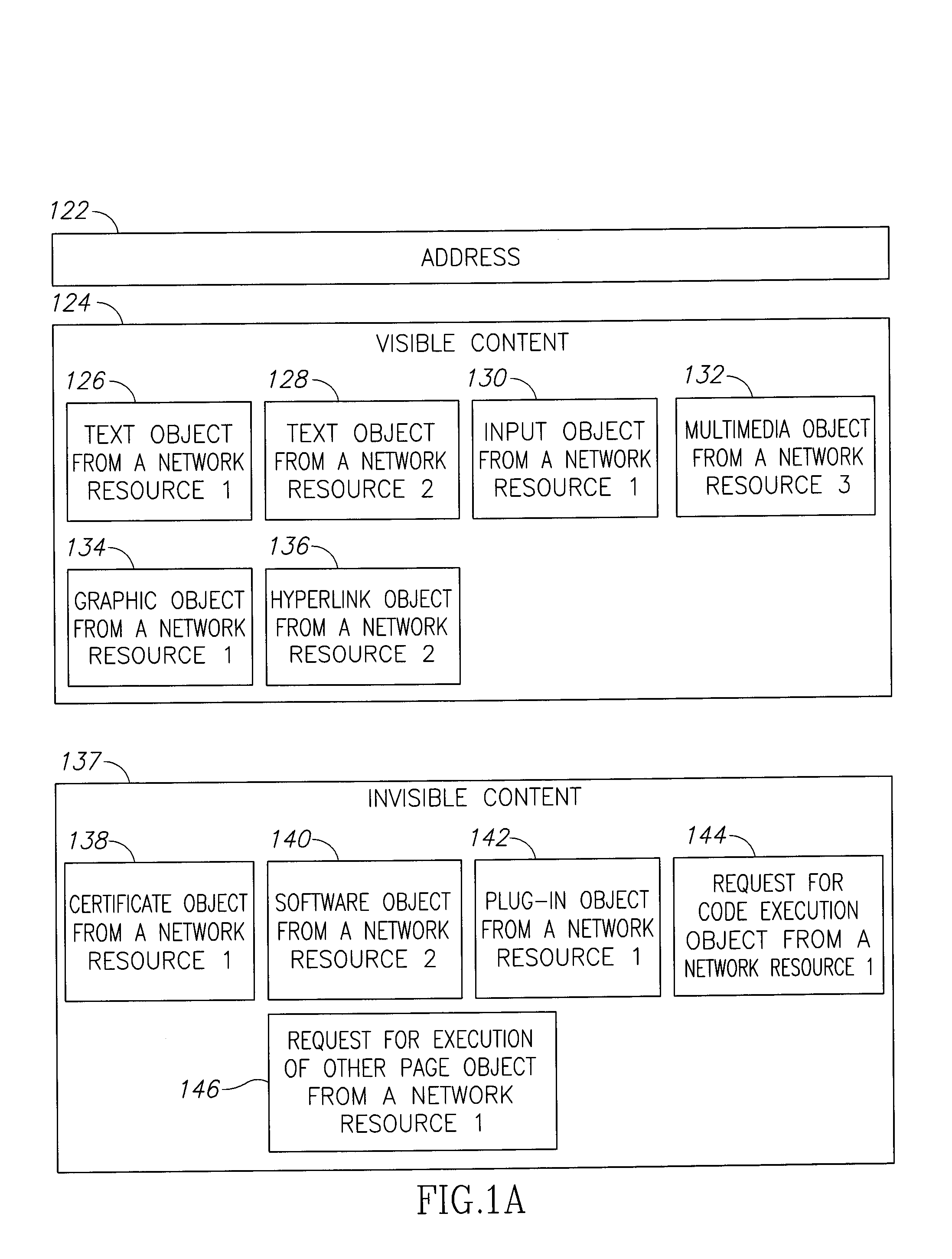
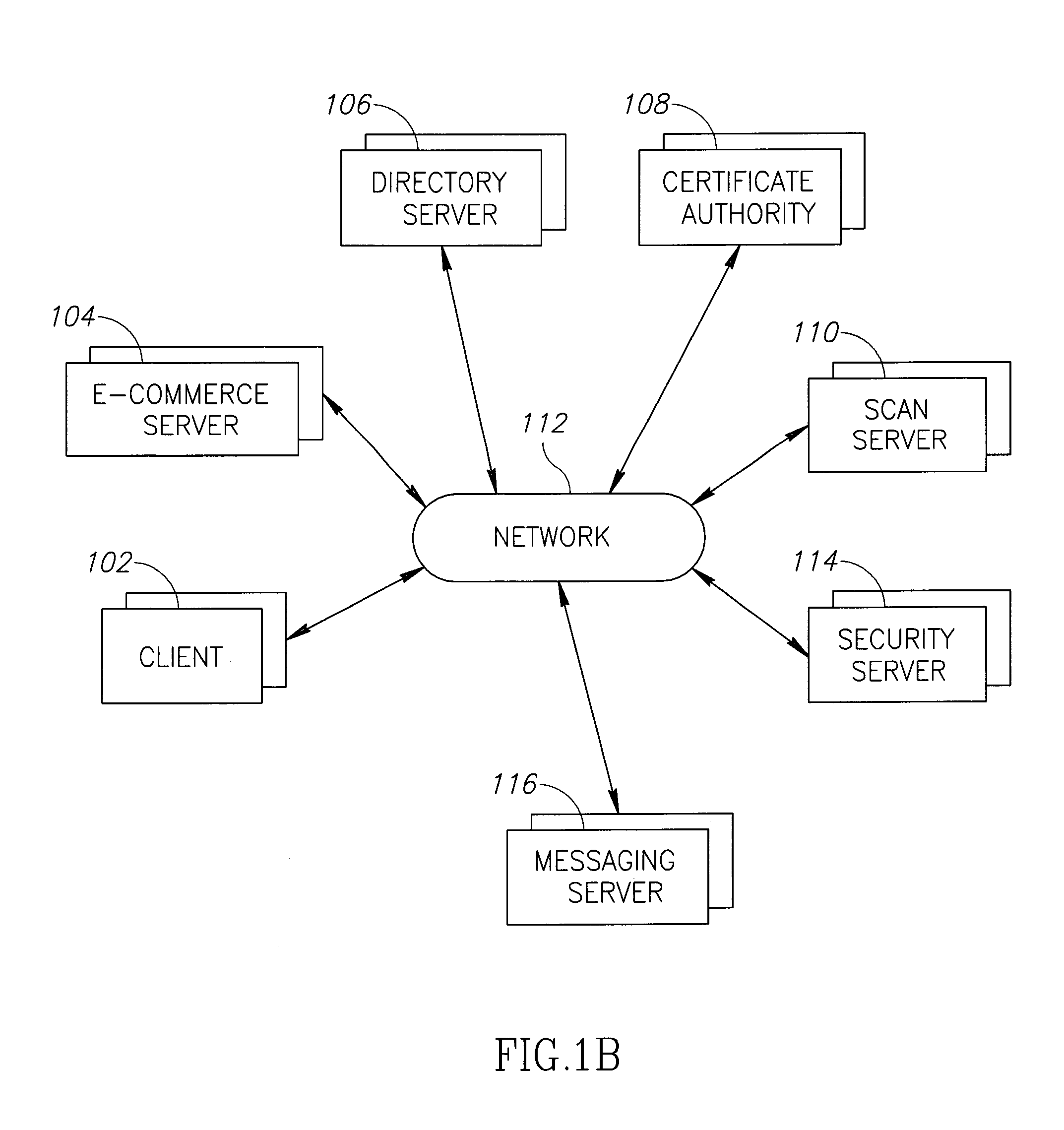
[0112]A network resource in the context of the present invention is a physical or virtual device connected to a network that can receive and / or send data (text, audio, graphic and / or video). Examples of network resources are clients (defined later), E-commerce servers (e.g. web sites, FTP sites), messaging servers, and other similar resources.
[0113]Users connect to a network resource (for example, a web site) through a network (for example, the Internet) using a device such as a personal computer, telephone, mobile phone or other user controlled network-attached device. In the device they use an application such as web browser application, Telnet application, voice conversation or other built-in or programmatic user interface for connecting to a network resource. The device receives output from the application. Typically the output is displayed on the device's display system, although other output like audio, vibration etc. may be used. In most cases the output is a page. In the cas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com