System and Method for Generation of a Heuristic
a heuristic and system technology, applied in the field of system and method for generating heuristics, can solve the problems of not always enough time for a threat to be found and analyzed, defeated or circumvented, and cost prohibitive to put such defenses in a typical business network at all entry points
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015]The following description is provided to assist in a comprehensive understanding of exemplary embodiments of the invention as defined by the claims and their equivalents. It includes various specific details to assist in that understanding; however these specific details are to be regarded as merely exemplary. Accordingly, those of ordinary skill in the art will recognize that various changes and modifications of the embodiments described herein can be made without departing from the scope and spirit of the invention.
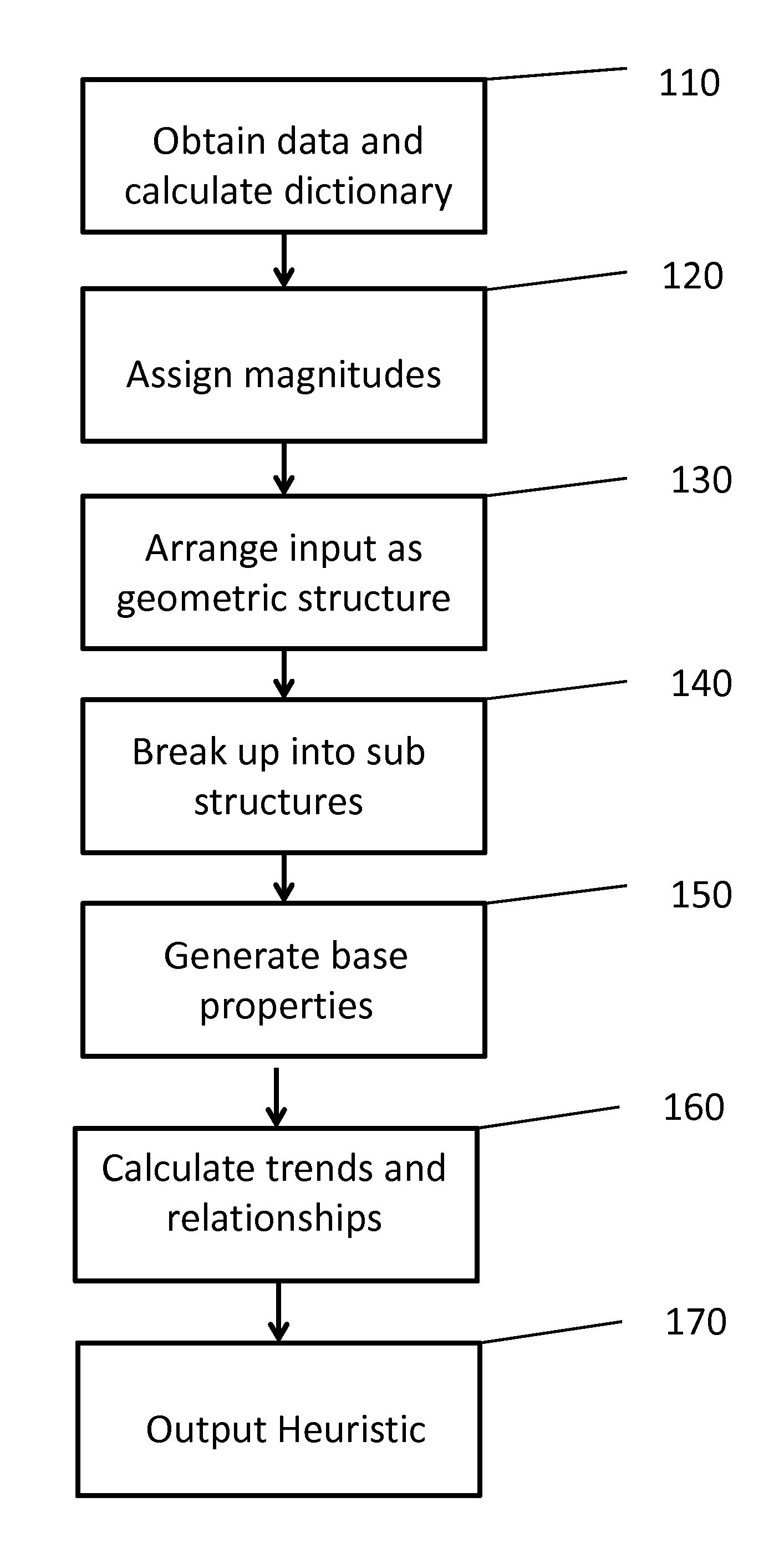
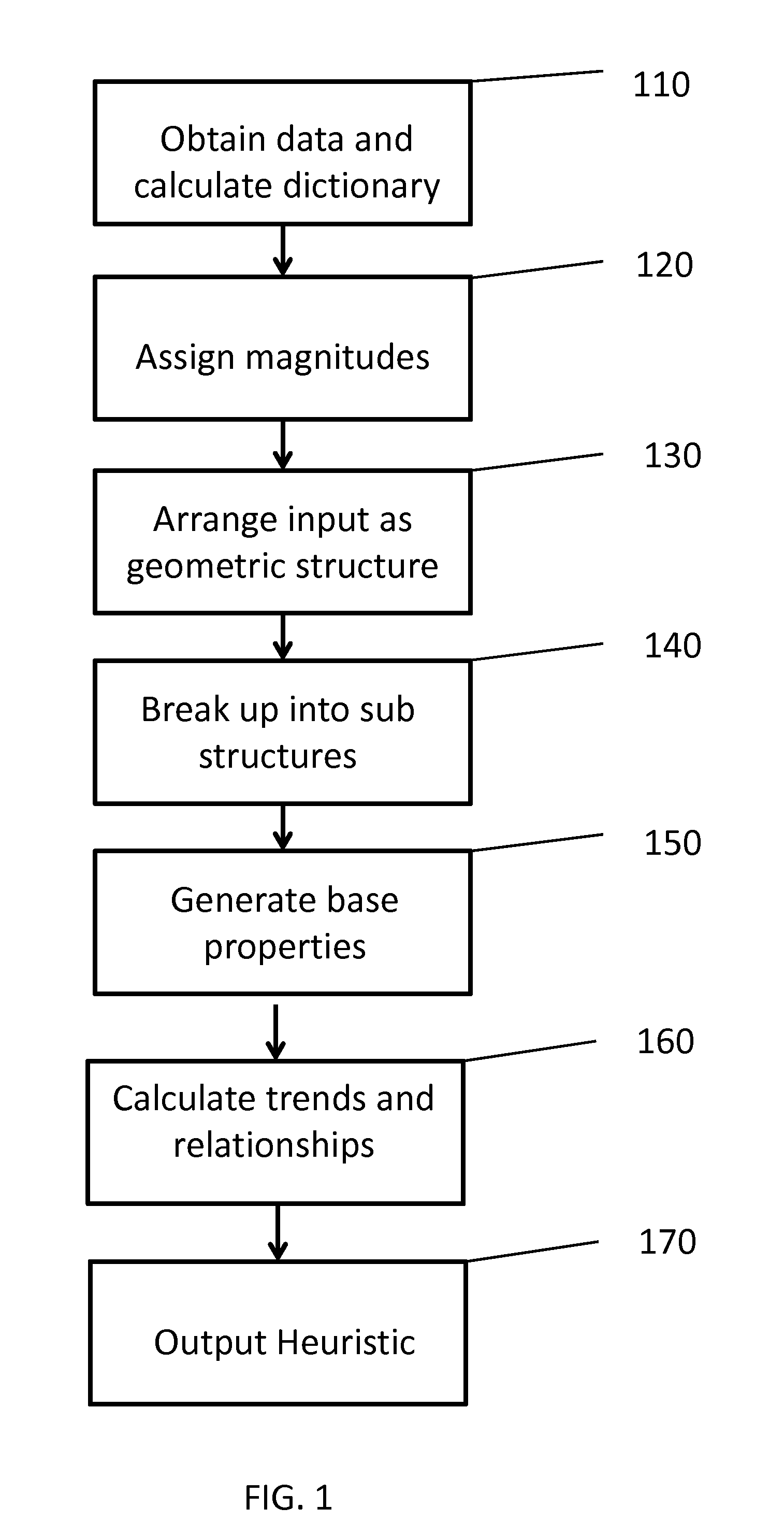
[0016]FIG. 1 is a block diagram of a heuristic generation process according to an exemplary embodiment of the present invention. Referring now to FIG. 1, data from which a heuristic will be generated is obtained at step 110. Data can be obtained from a user computer system, a wireless phone, a network server, and can arrive or be extracted from multiple data sources, implementing multiple formats, etc. The data is assessed for unique elements associated therewith ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com