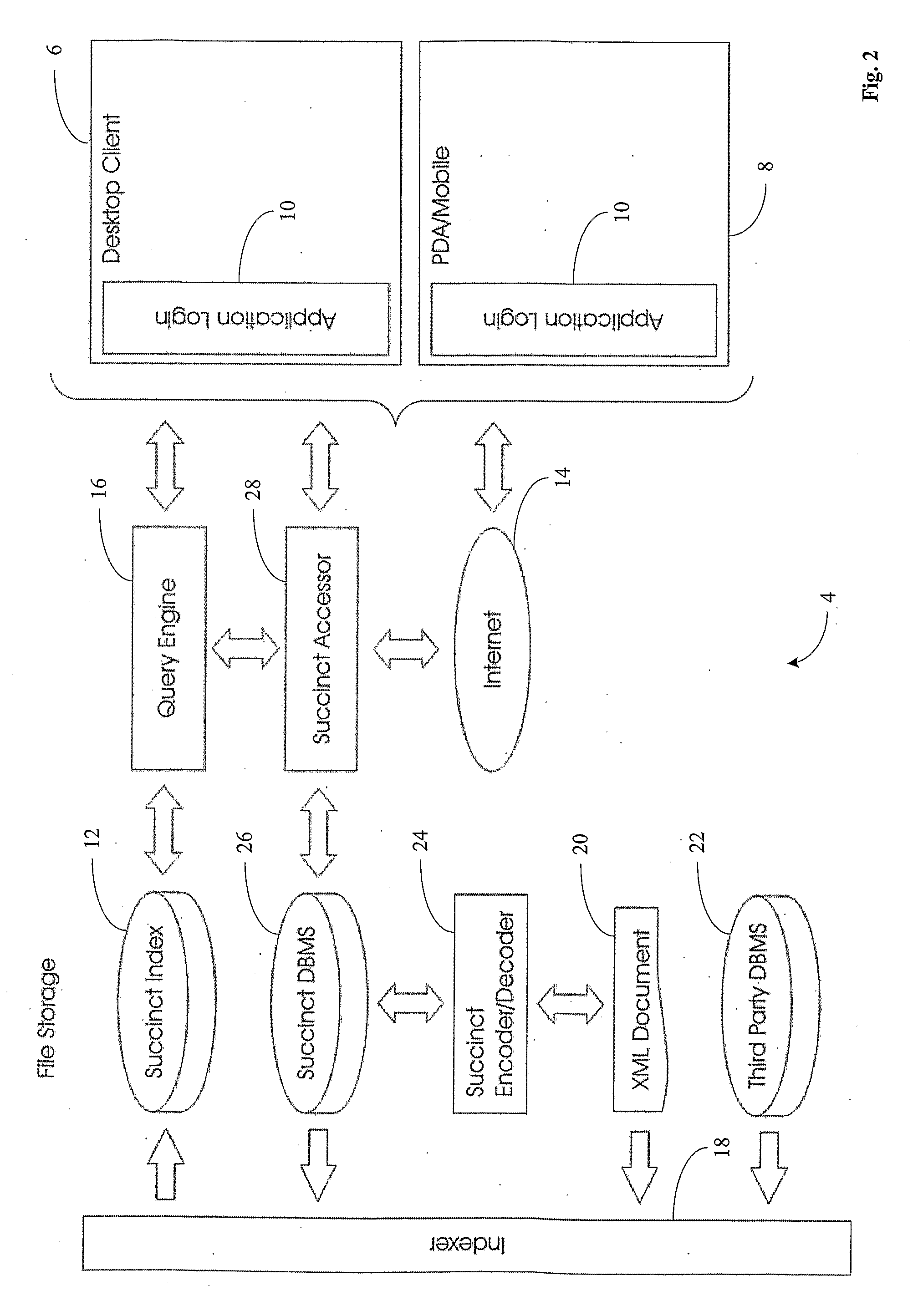
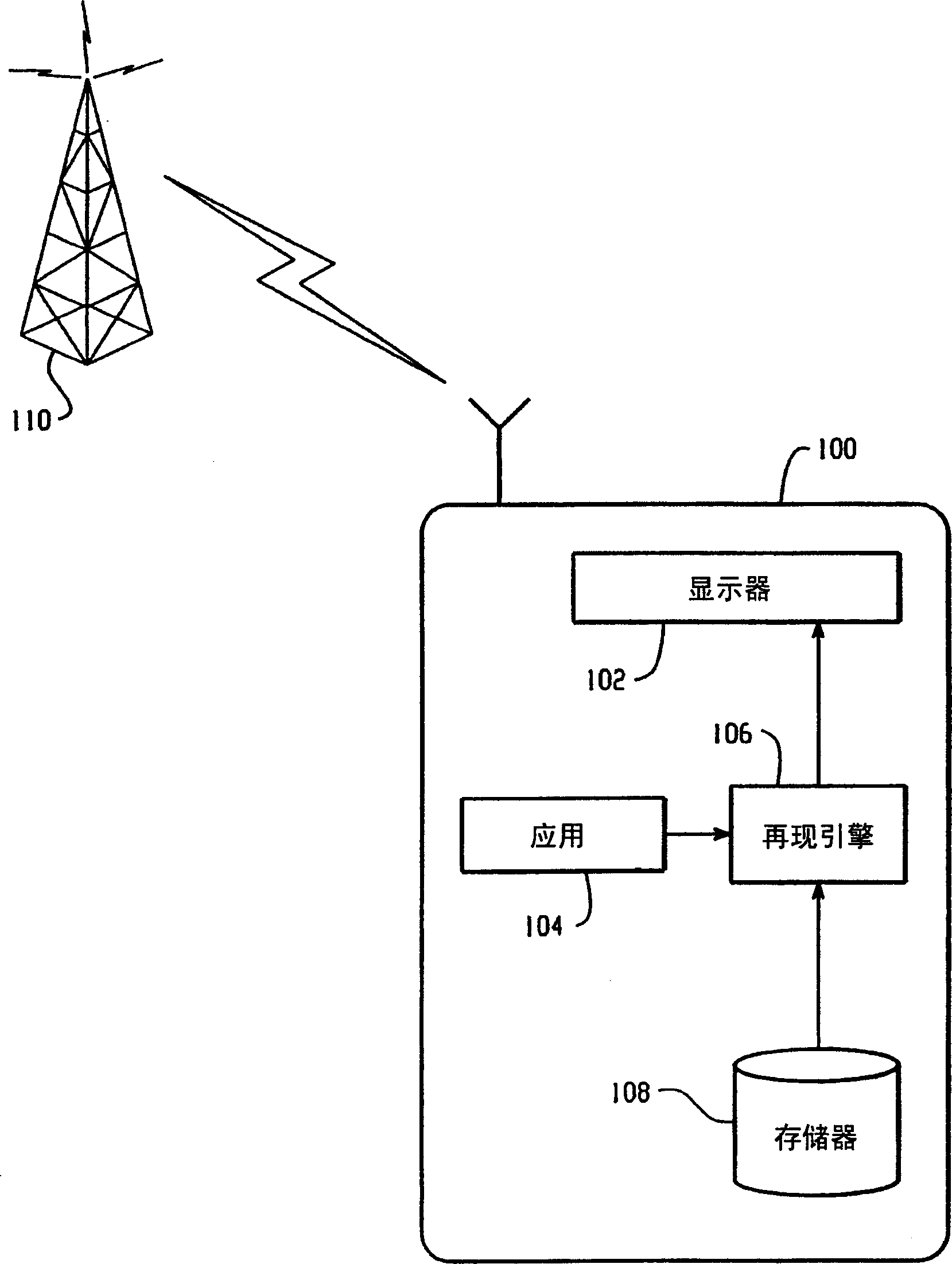
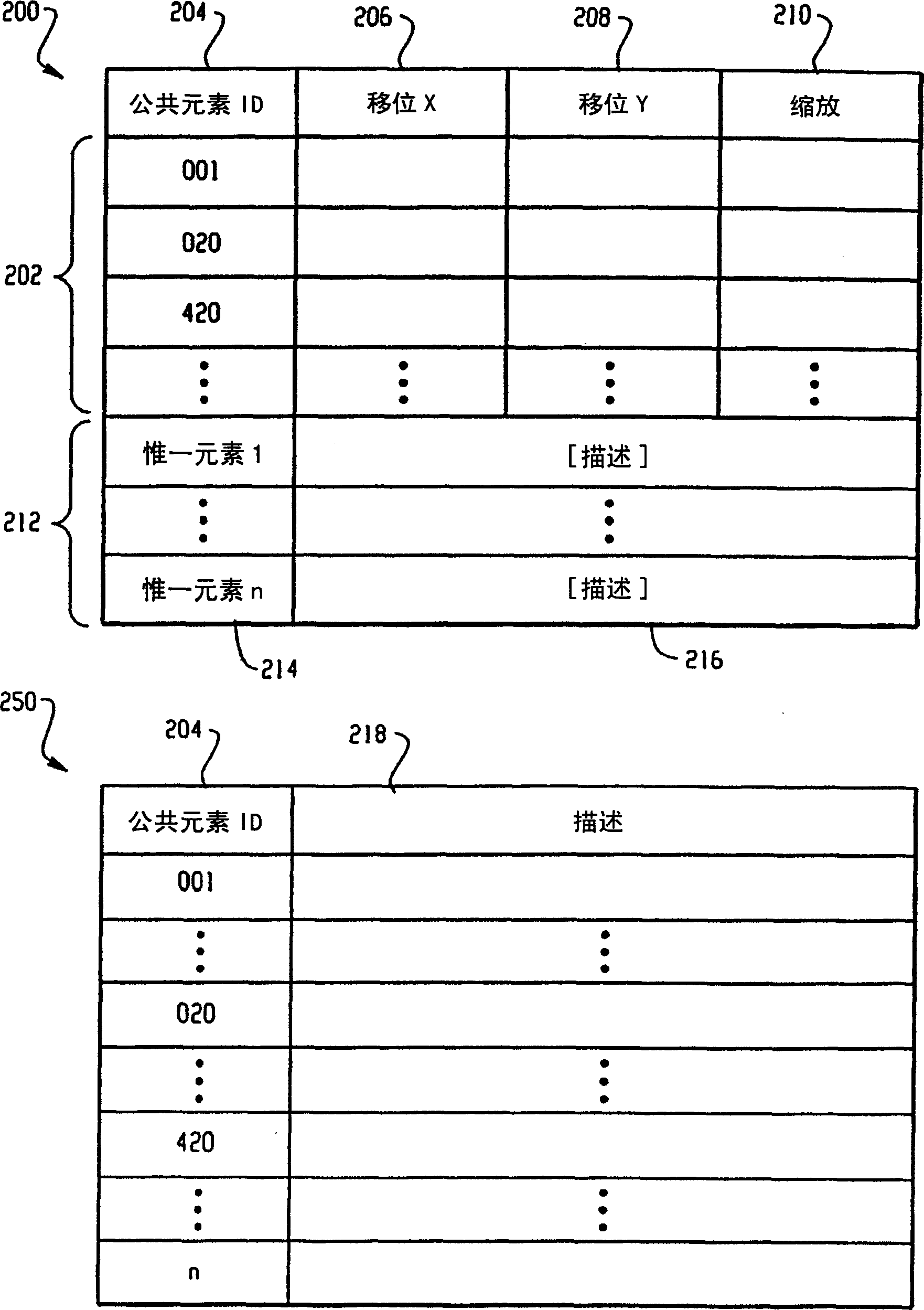
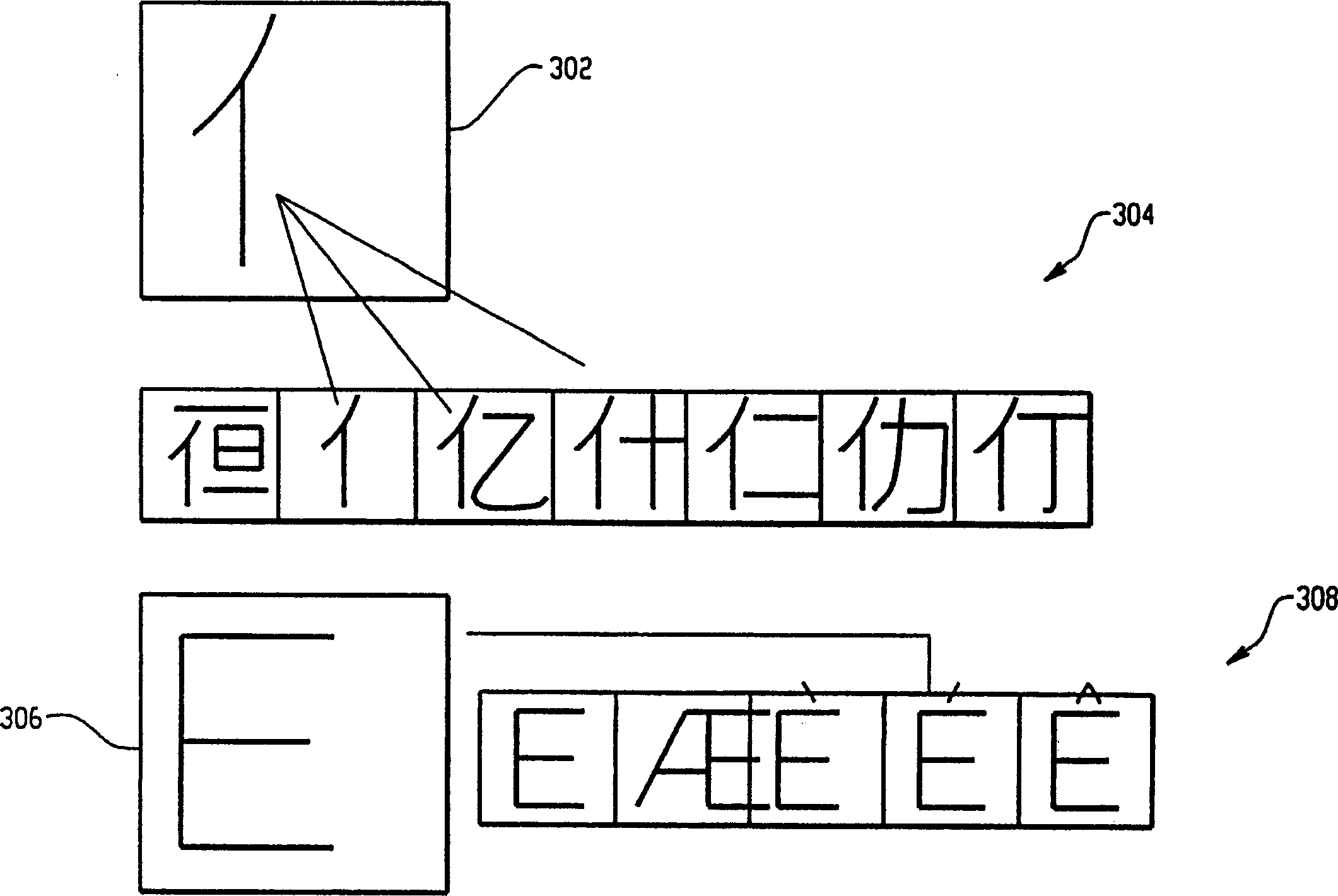
Patents
Literature
58 results about "Unique element" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The unique element defines that an element or an attribute value must be unique within the scope. The unique element MUST contain the following (in order): one and only one selector element (contains an XPath expression that specifies the set of elements across which the values specified by field must be unique)
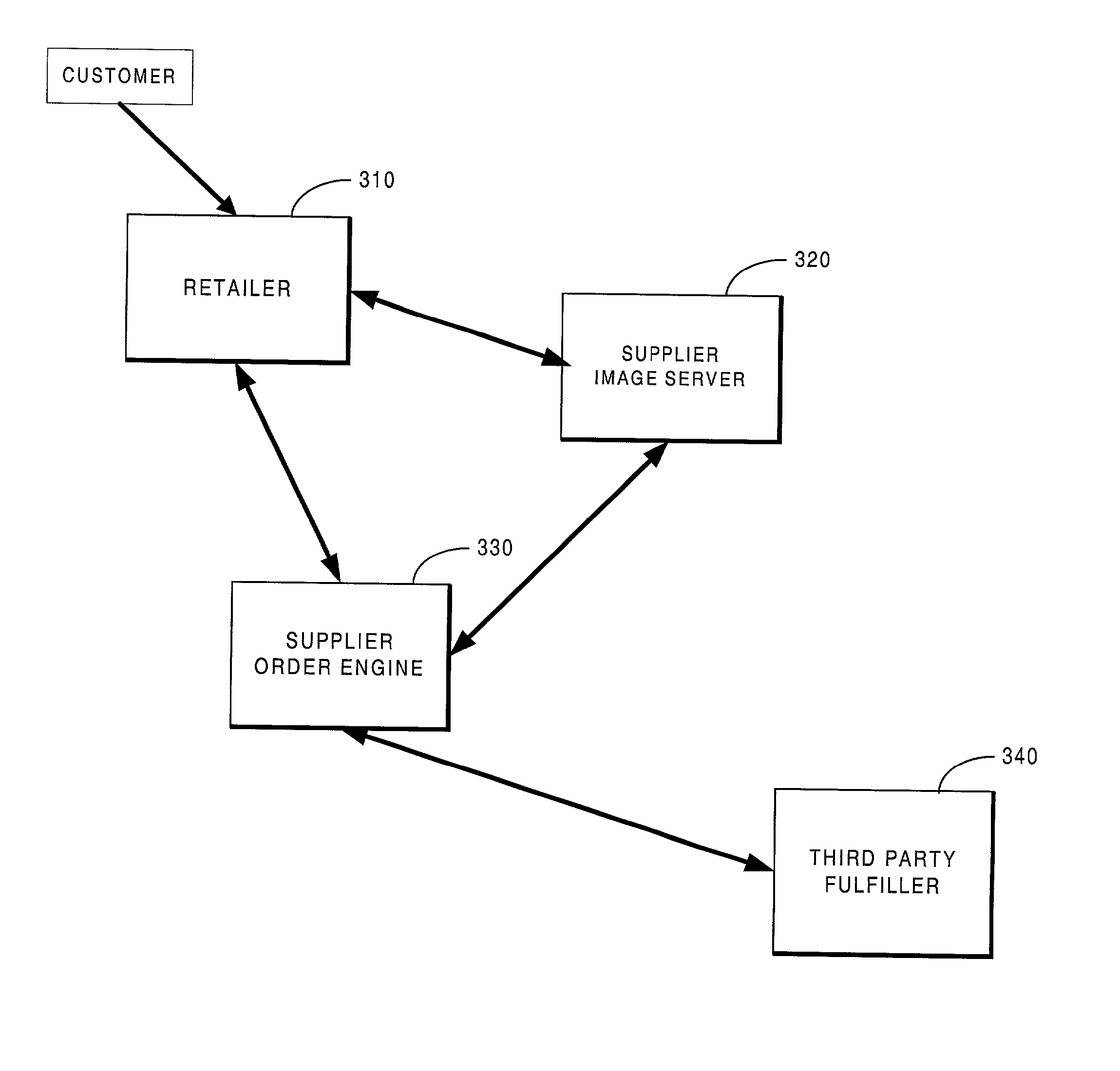
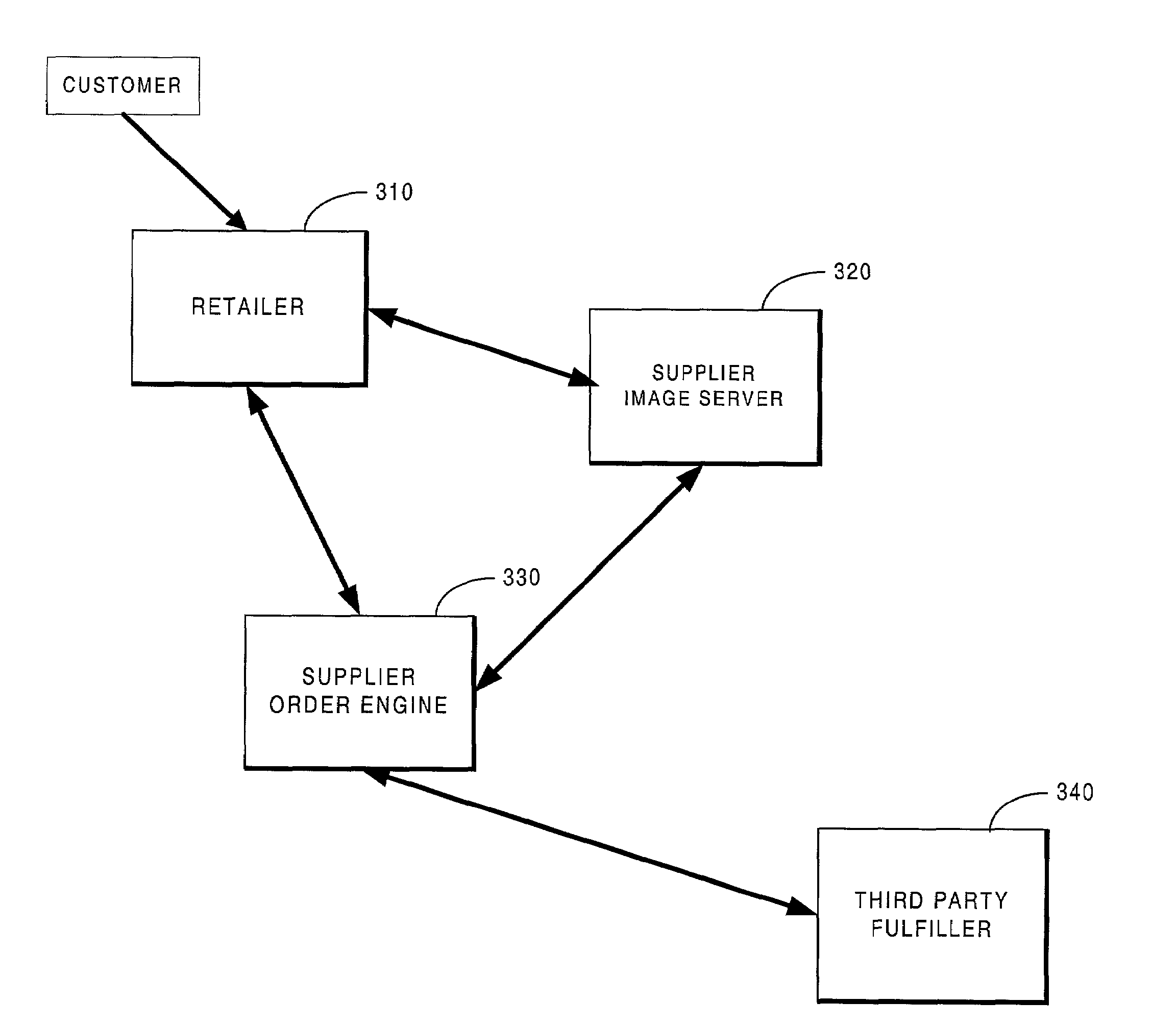
Integrated shopping cart for sale of third party products and services via the internet
ActiveUS20030093321A1Buying/selling/leasing transactionsSpecial data processing applicationsThird partyProduct order
The current invention includes an improved system for an e-commerce vendor to seamlessly incorporate products and services from a third party into its own e-commerce site. This system enables the e-commerce vendor to display the third party products and to accept orders and arrange fulfillment of these products through its own site in a manner that is seamless to the end user. When the e-commerce retailer requests product information from the supplier, the supplier provides the retailer with product information and URLs at which additional information can be located. The retailer uses this information to retrieve product images, descriptions and information and to display this information to its customer on its own site. Each of these items is tagged with a unique element identifier that contains a number of details about the product. This information tagged to the product image or description enables the product to be easily identified by both the retailer and the supplier. When the customer purchases the products from the retailer, the necessary information is tagged to the product information and, thus, is available for placement of the order with the supplier. This enables the product order to be routed to and fulfilled by the third party supplier in a manner that is transparent to the customer.
Owner:SYNIVERSE ICX LLC
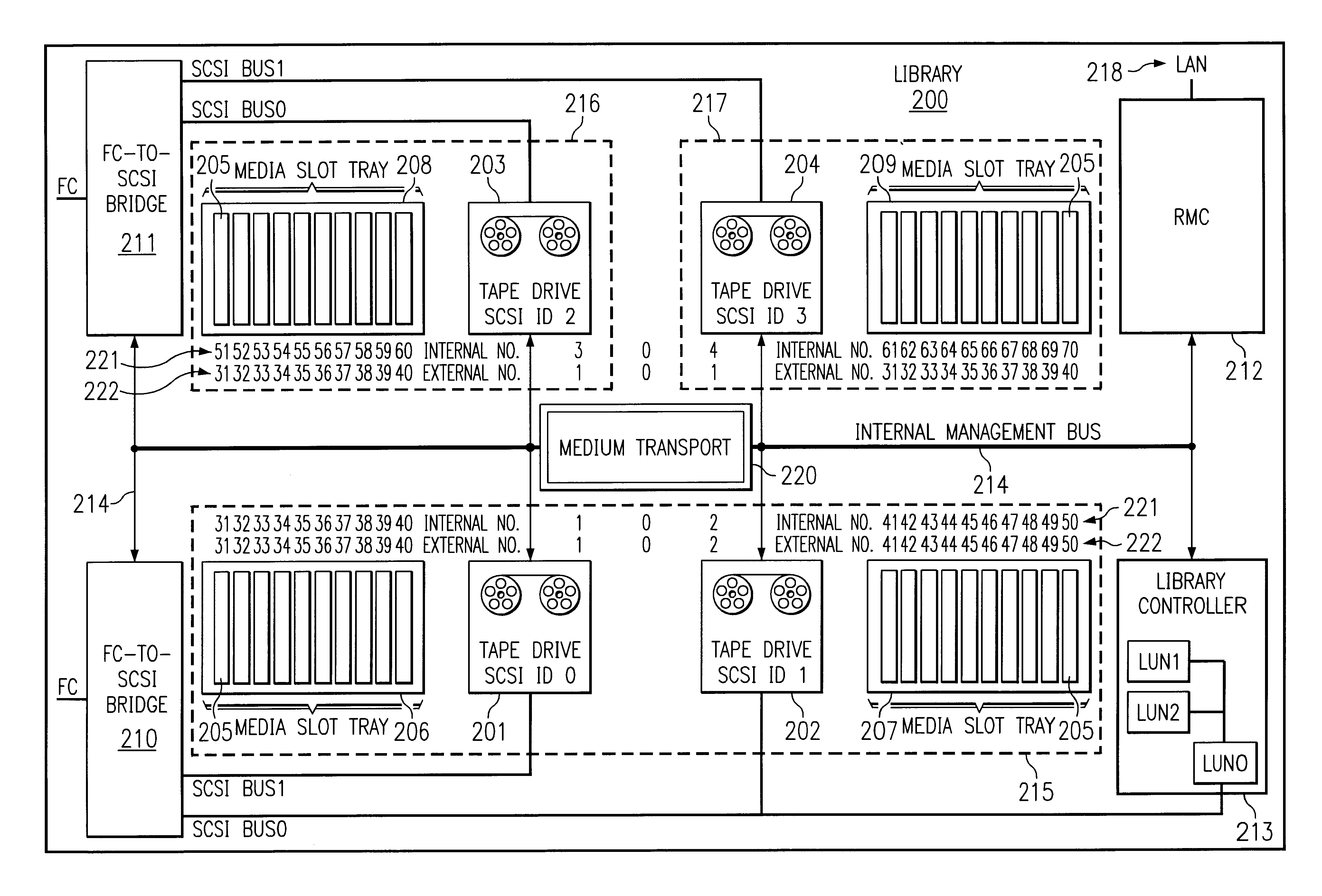
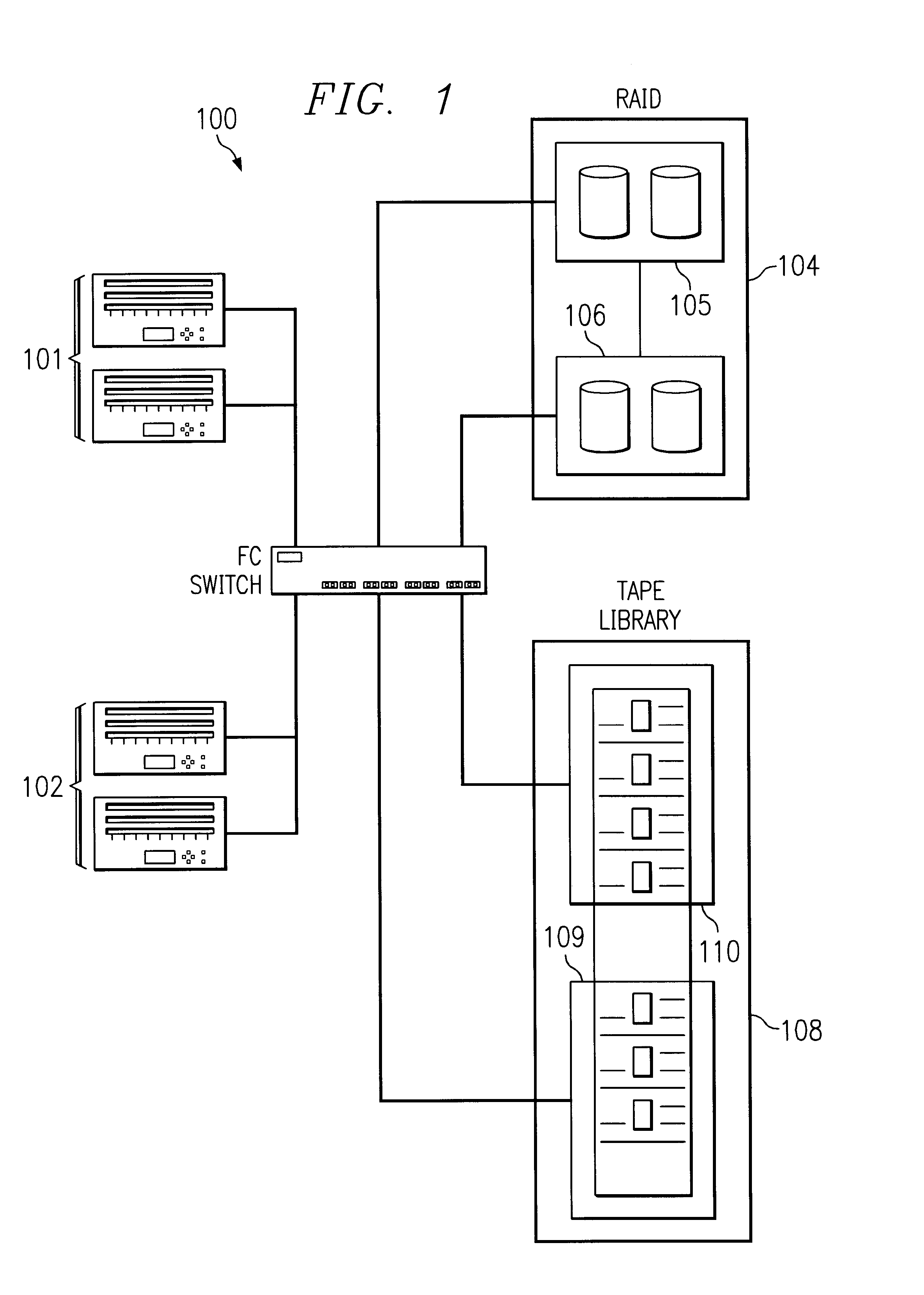
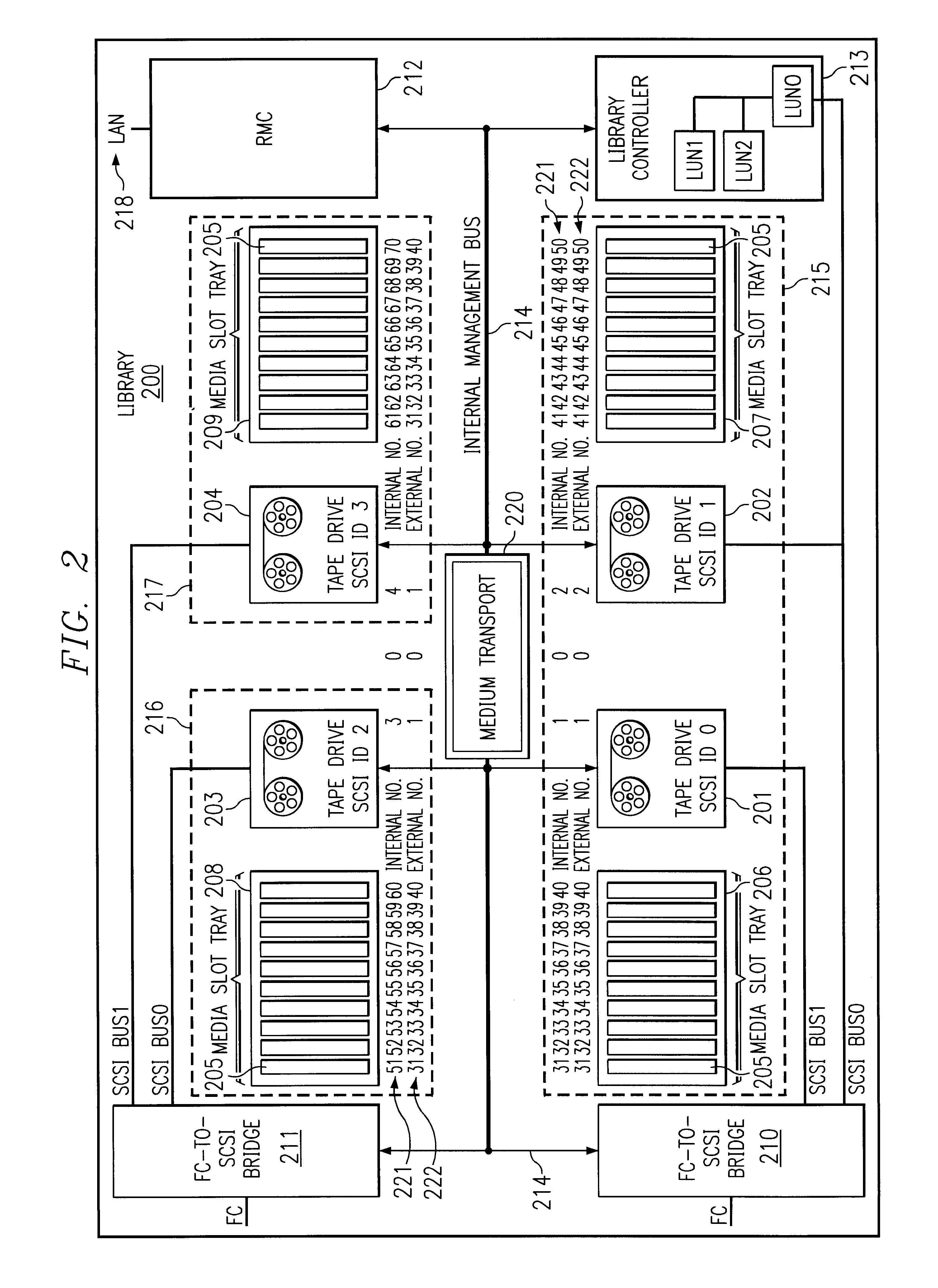
System and method for partitioning a storage area network associated data library employing element addresses
InactiveUS6839824B2Flat record carrier combinationsInput/output to record carriersStorage area networkLogic cell
A data library comprising a plurality of partitions, at least one data transfer element, each of the data transfer elements assigned to one of the partitions and assigned an internally unique element address, a plurality of data storage element slots, each of the slots assigned to a partition and assigned an internally unique element address, at least one media transport element shared by the partitions to move media between the slots and the at least one data transfer elements, the transport assigned an internally unique element address, and a library controller that assigns a different logical unit designation to each of the partitions and that assigns external element addresses to the transport, the data transfer elements, and the slots for each of the partitions and maps the internally unique addresses to the external addresses, the controller restricting movement of media to and from the slots assigned to a same of the partitions.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and apparatus for data center air conditioning
Modular data center containers with modular components suitable for use with rack or shelf mount computing systems currently use cooling methods that do not include economizers due to size constraints of structural steel support infrastructure associated with modular data centers and removable economizers to facilitate portability of modular data centers. The modules allows introduction of outside air to the cooling cycle with the unique elements embodied within airside economizer components. The modules in conjunction with the data center represents a new and useful process to allow the economizer elements to bring outside air into the modular data center cooling cycle.
Owner:LARSEN ARTHUR E
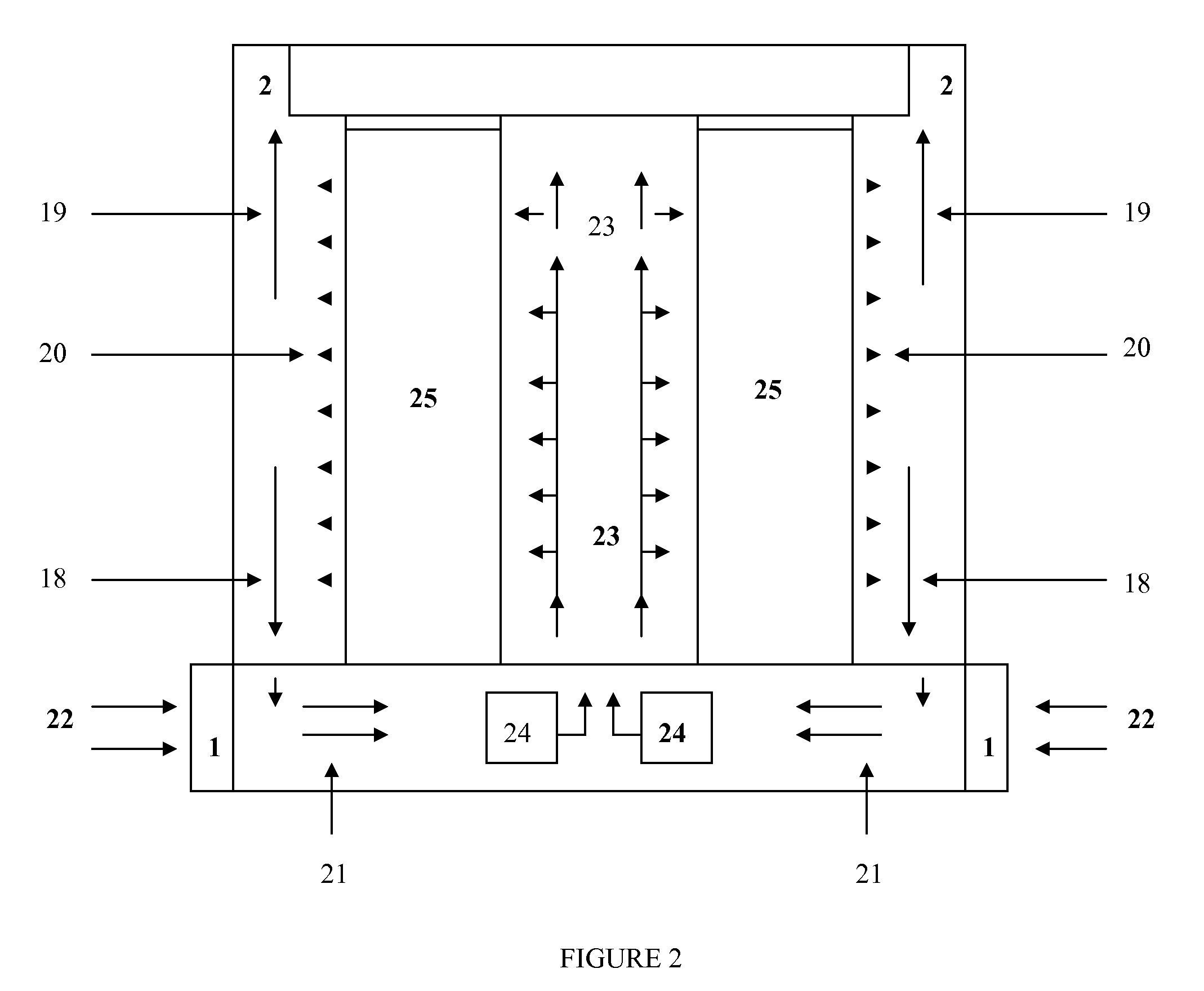
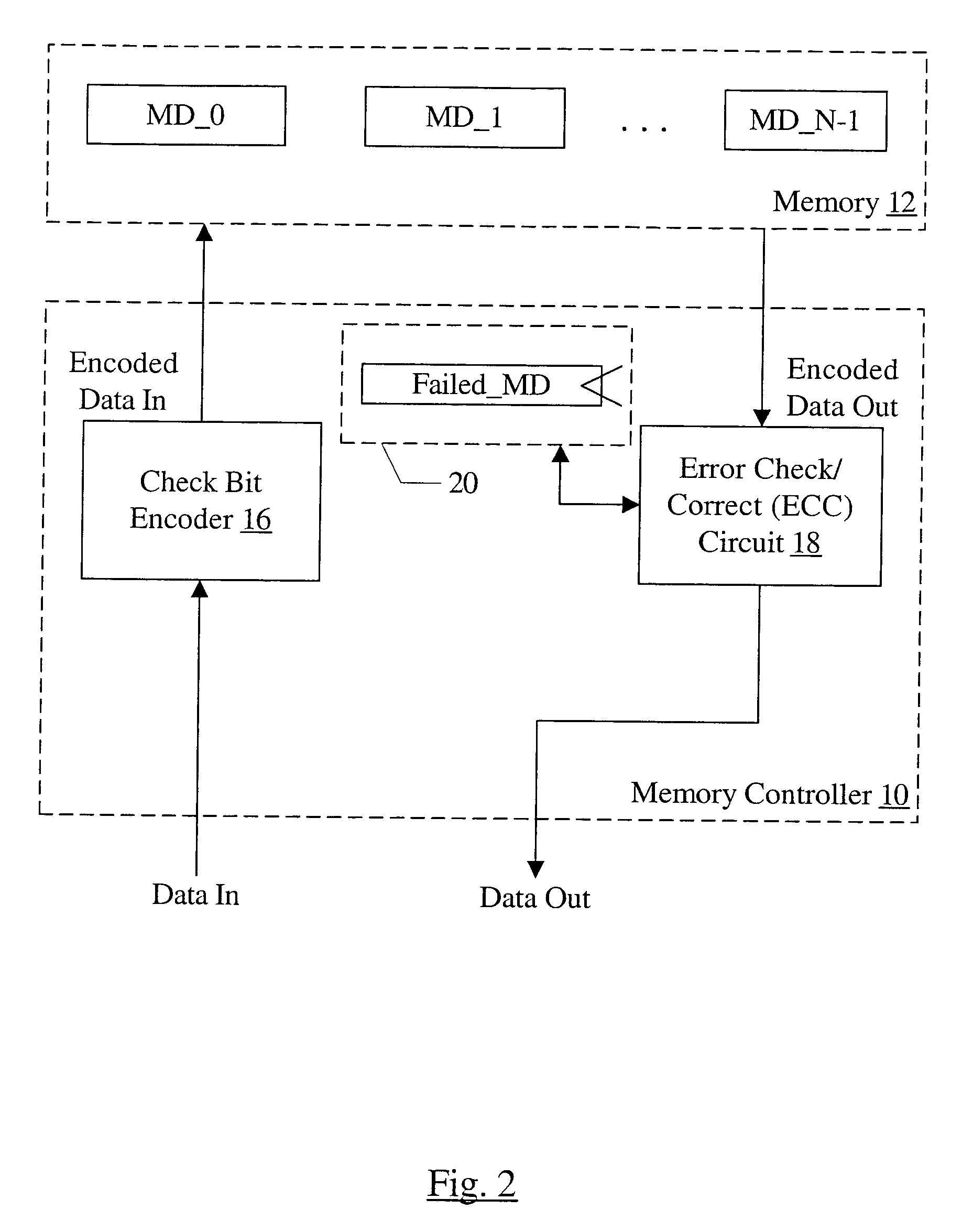
ECC for component failures using Galois fields
An apparatus comprises a check bit encoder circuit and a check / correct circuit. The apparatus operates on encoded data blocks, wherein each encoded data block includes a data block, a first plurality of check bits, and a second plurality of check bits. The encoded data block is logically arranged as an array of R rows and N columns, and each of the N columns comprises data bits from a respective one of the plurality of components. The first check bits form a first column of the array, and each of the first check bits covers a row of the array. The second check bits form a second column of the array and are defined to cover bits in the array according to a plurality of check vectors. Each check vector corresponds to a different bit in the array and is an element of a Galois Field (GF(2R)). The check vectors are derived from a plurality of unique elements of GF(2R), each of which corresponds to a different column of the array. The check vector in row X of the column is the product, in GF(2R), of the unique element for that column and alphaX, wherein alpha is a primitive element of GF(2R).
Owner:ORACLE INT CORP
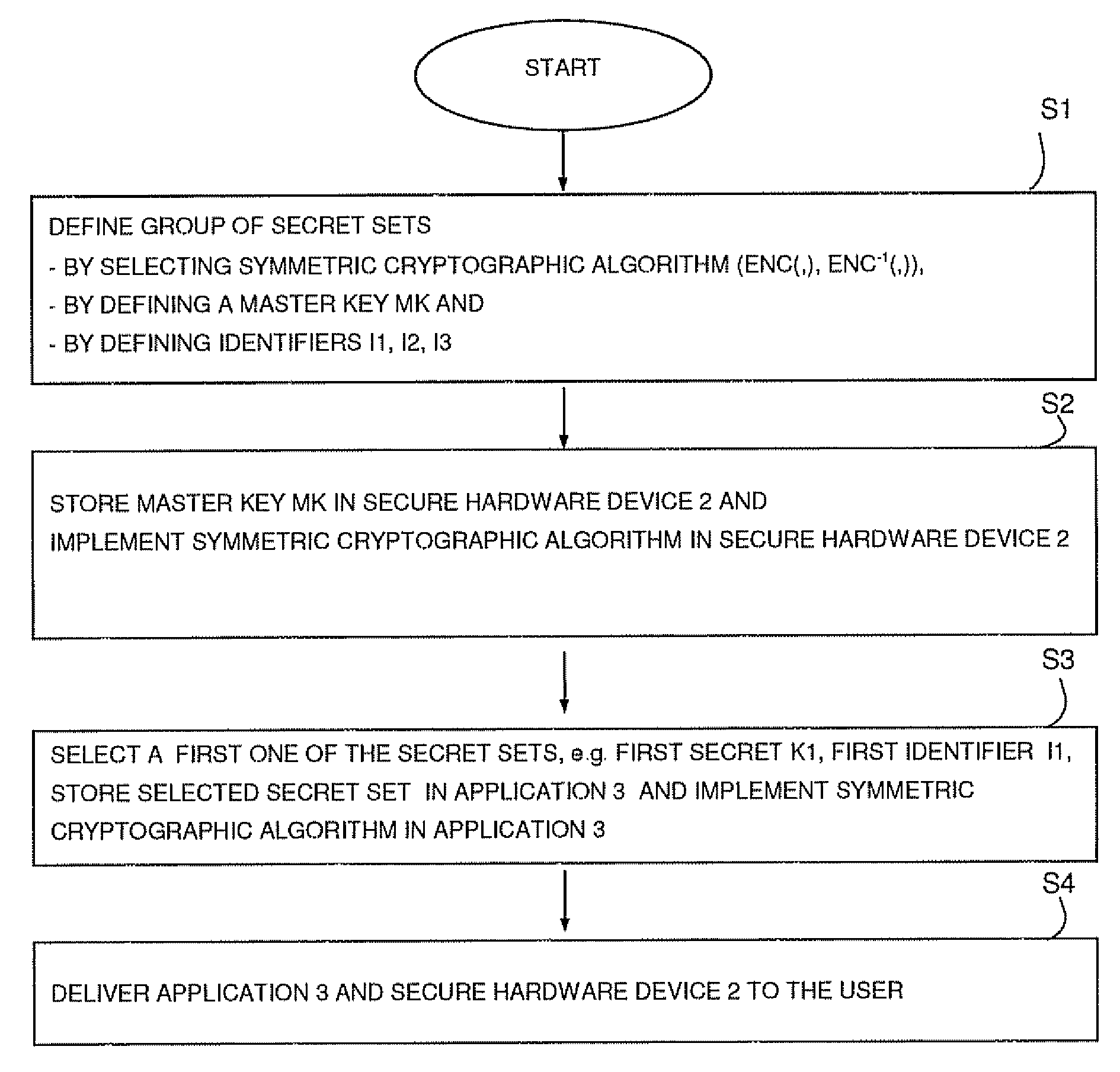
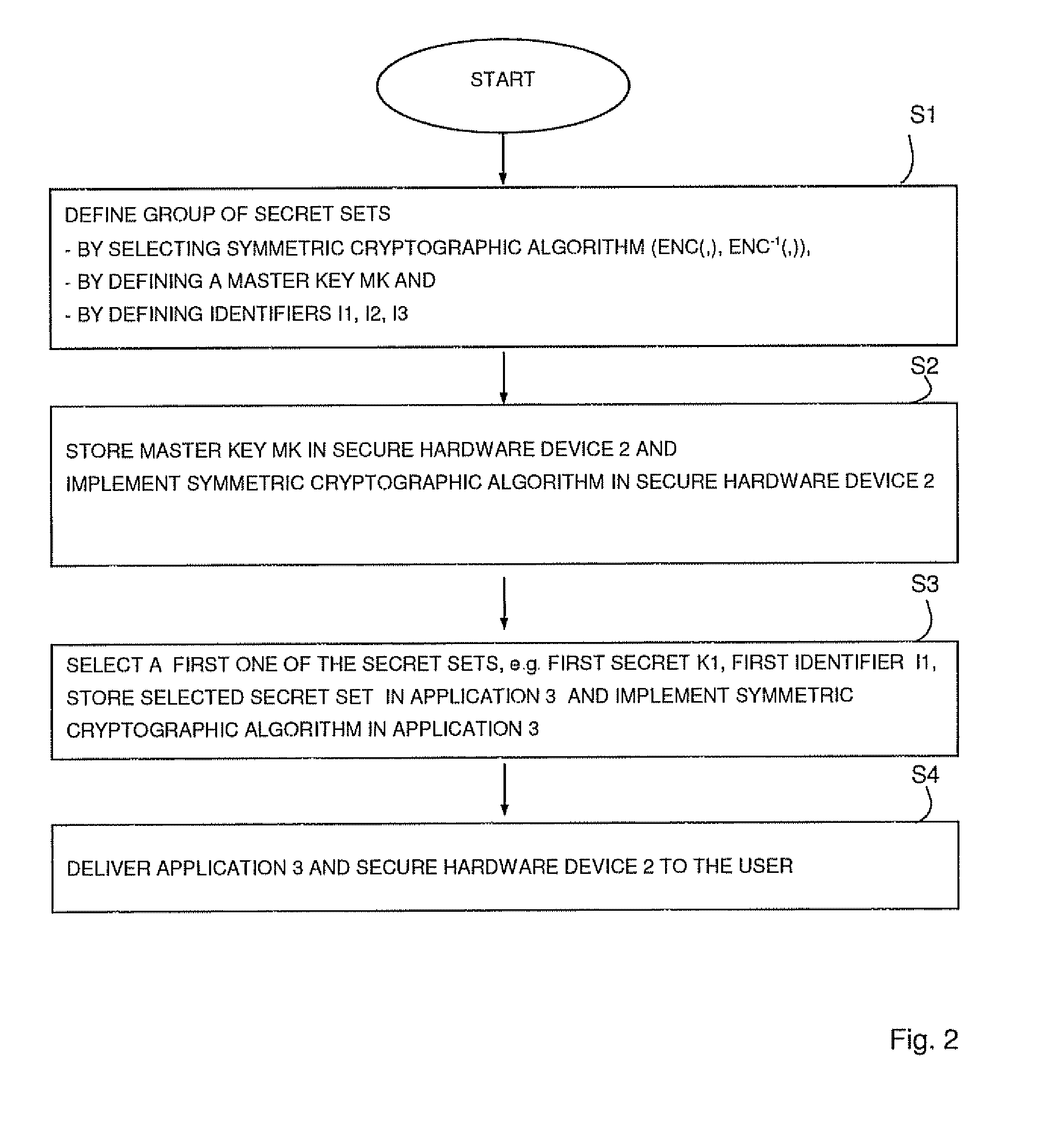
Method for secure communication between a secure hardware device and a computer and apparatus for changing a shared secret for generating a session key for a secure communication between a secure hardware device and a computer
ActiveUS20080226065A1Minimize processing powerRequires minimizationKey distribution for secure communicationPublic key for secure communicationSecure communicationSession key
There is provided a method for secure communication between a secure hardware device connected to a computer and said computer,said method comprising the steps of:a) defining a group of secret sets including at least two secret sets, each of which includes a secret and an assigned identifier,b) storing the group of secret sets in the secure hardware device in such a manner that the secure hardware device can retrieve the secret of any of said secret sets from the assigned identifier,c) selecting a first one of said secret sets and storing said selected first secret set in a first application,d) delivering the first application which includes the first secret set to a user who executes the first application on a computer being connected to the secure hardware device,e) wherein the first application defines a first session key and generates first session key indication data based on the first secret set, said first session key indication data including the identifier of the first secret set as the only element from the first secret set, and transmits said first session key indication data to the secure hardware device, which retrieves, as a first secret, the secret of the first secret set based on the identifier included in said first session key indication data, and further retrieves the first session key from said first session key indication data based on the first secret, so that for secure communication the first session key for encrypting and decrypting of data to be transmitted between the secure hardware device and the computer is shared.
Owner:SFNT GERMANY
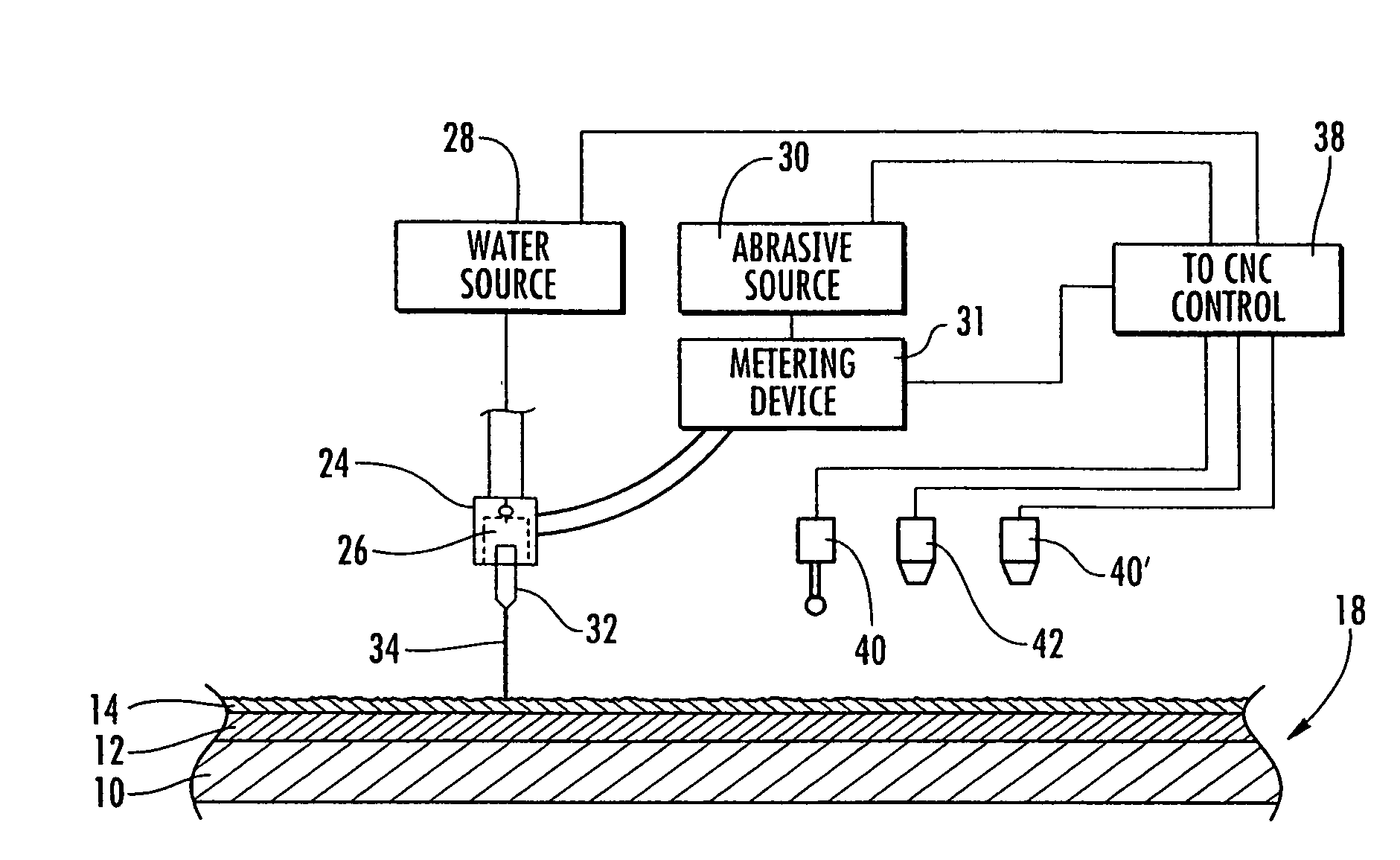
Method and apparatus for removing coatings from a substrate using multiple sequential steps
InactiveUS7896726B1High rateGrinding feed controlAutomatic grinding controlMaterial removalEngineering
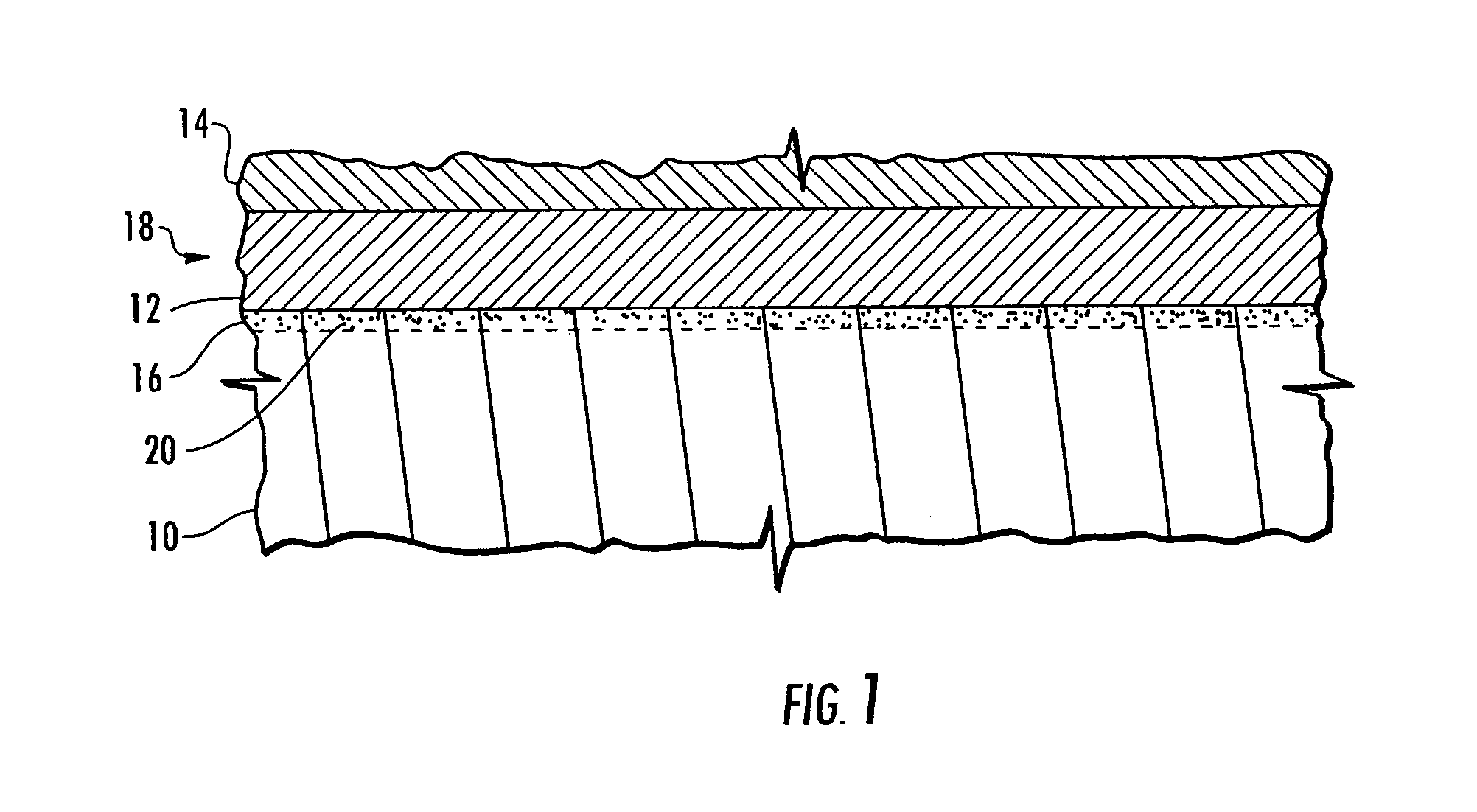
A method and apparatus for removing a coating having an irregular surface configuration that includes mapping the irregular surface configuration, and using the mapping determination in controlling the operation of an abrasive water jet to provide increased material removal rates at the higher points in the irregular surface and decreased material removal rates at the lower points, and thereby even out the surface configuration of the coating. The method and apparatus also includes using a detection device for detecting the presence or absence of an element that is unique to a layer of a coating, and using the detection determination in controlling the operation of the abrasive water jet to stop material removal of the coating when the detection device determines there is an absence of the unique element.
Owner:OPTOMEC INC
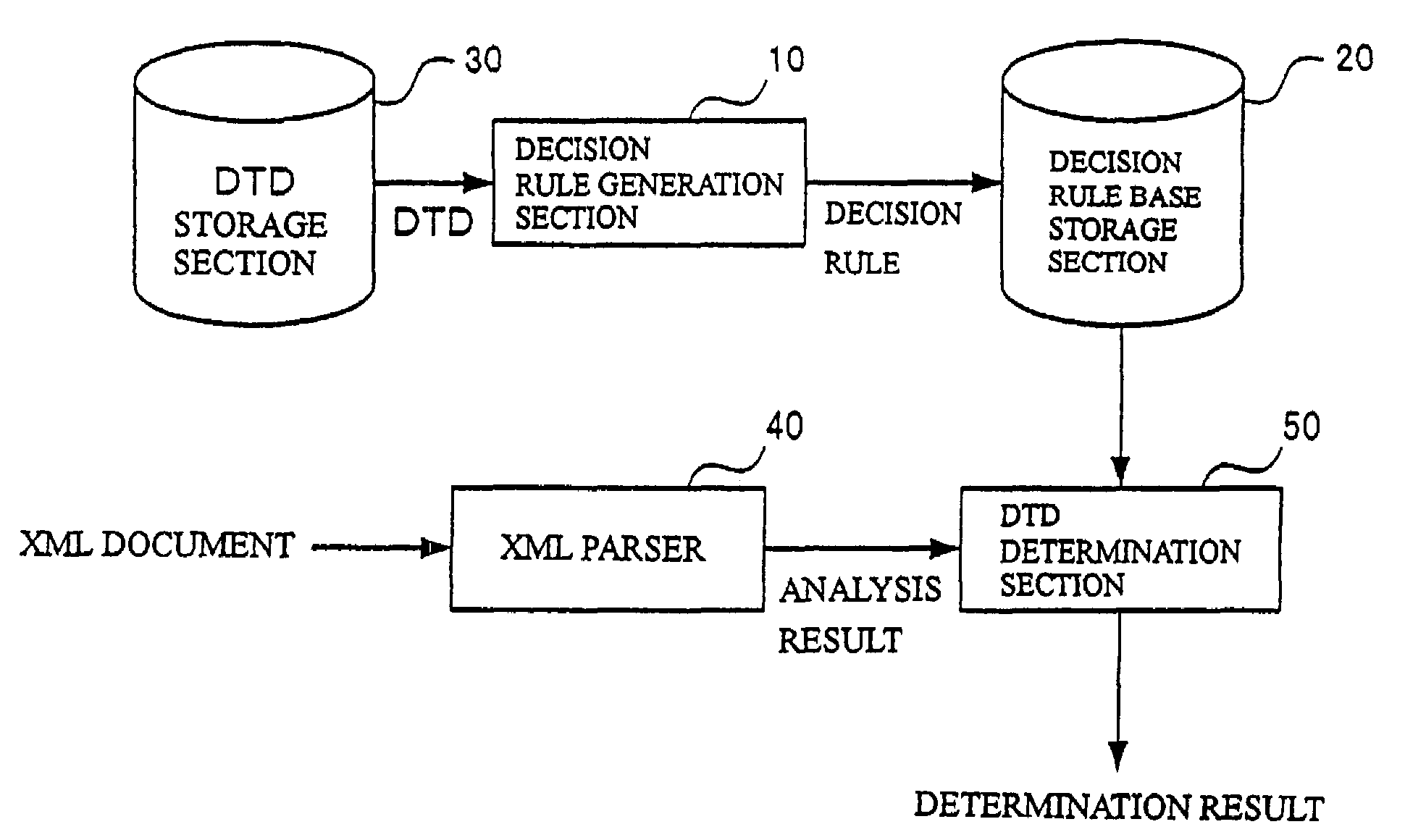
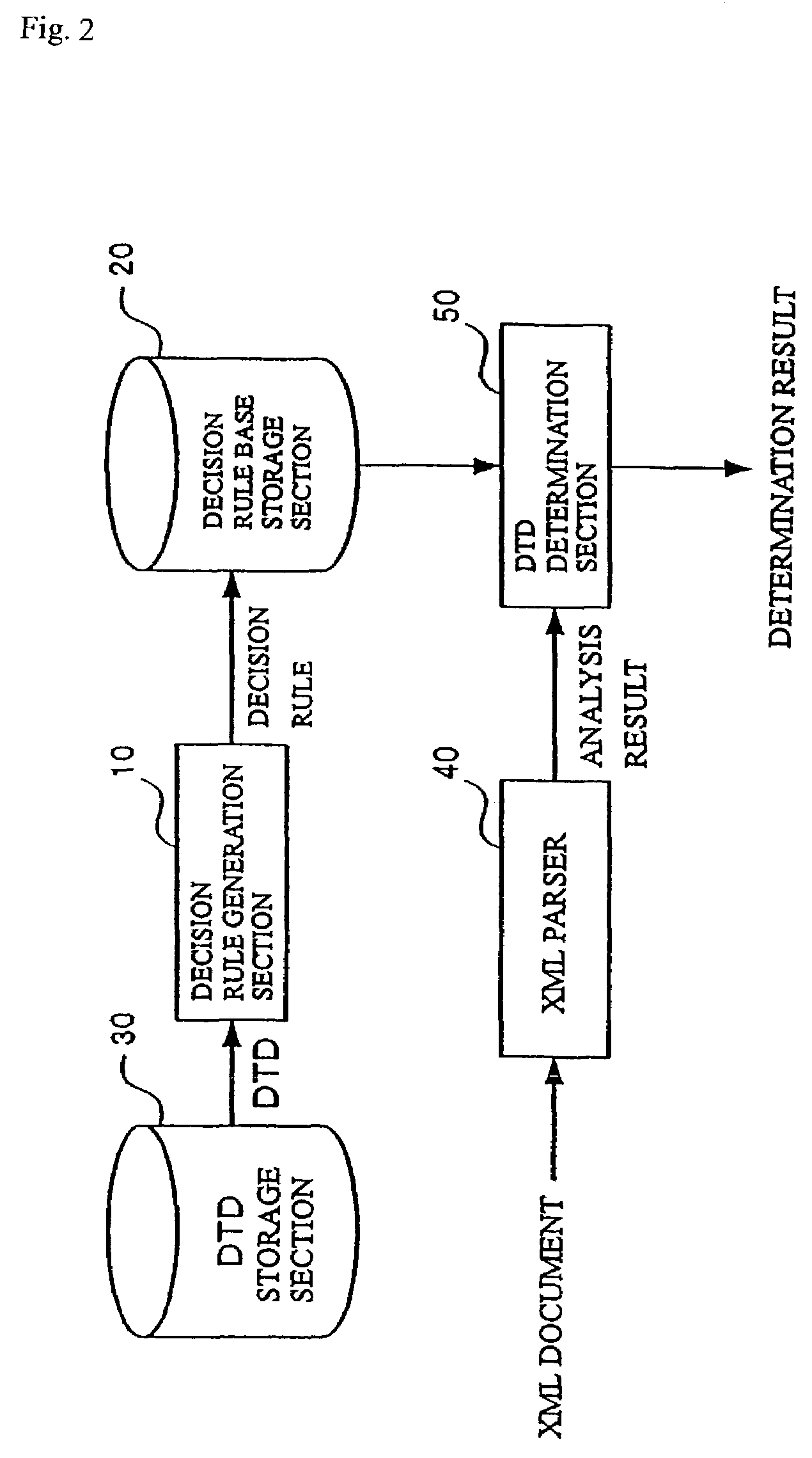
XML document processing for ascertaining match of a structure type definition
ActiveUS7275208B2Digital computer detailsNatural language data processingDocument preparationDocumentation
To perform processing at a high speed to identify some of the structure type definitions in a given definition set to which a received XML document matches. There are provided a decision rule generation section which generates a decision rule for determining to which one of a plurality of DTDs an XML document matches on the basis of unique elements of the DTDs, and a DTD determination section which determines to which one of the plurality of DTDs the XML document to be processed matches on the basis of the decision rule generated by the decision rule generation section.
Owner:GOOGLE LLC
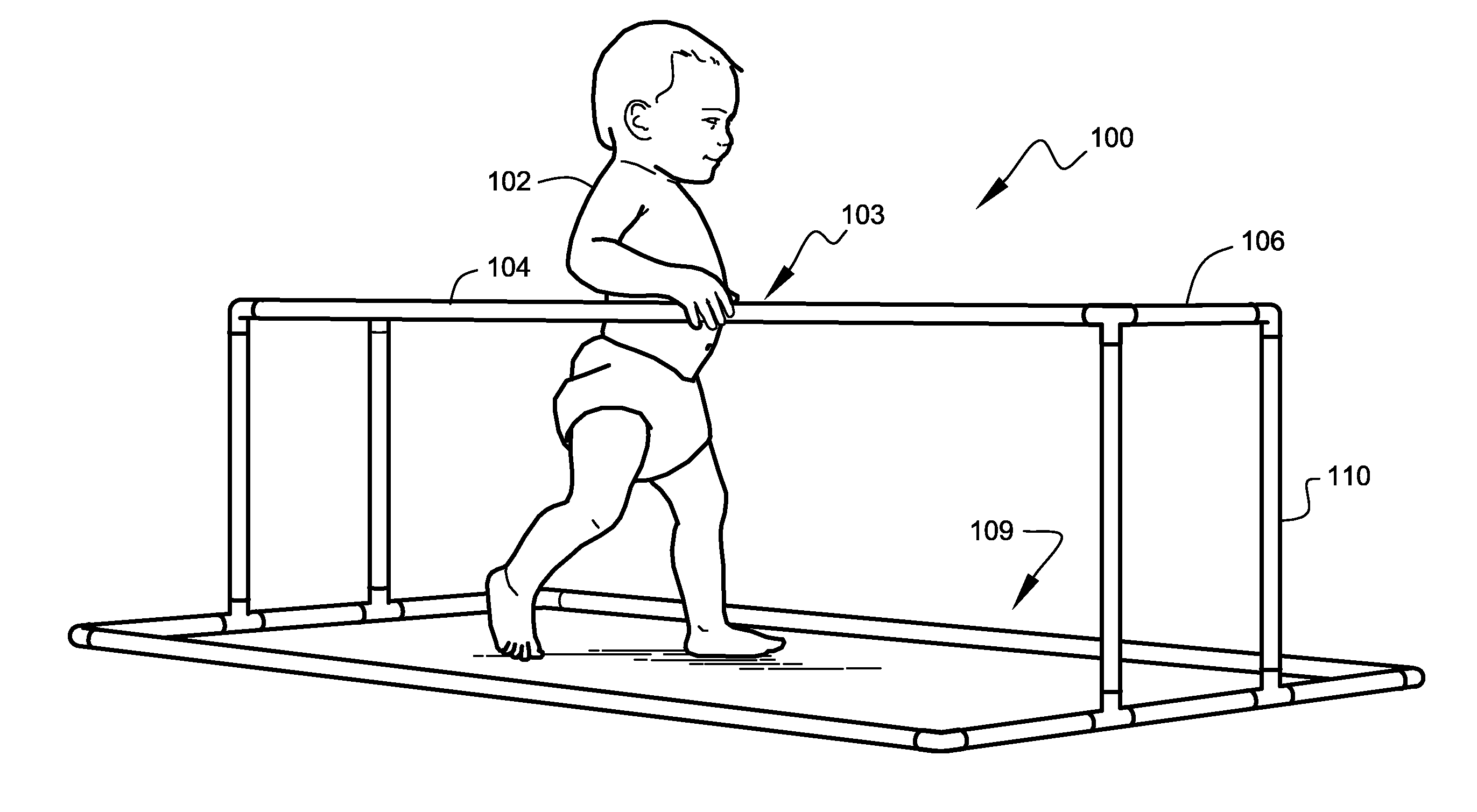
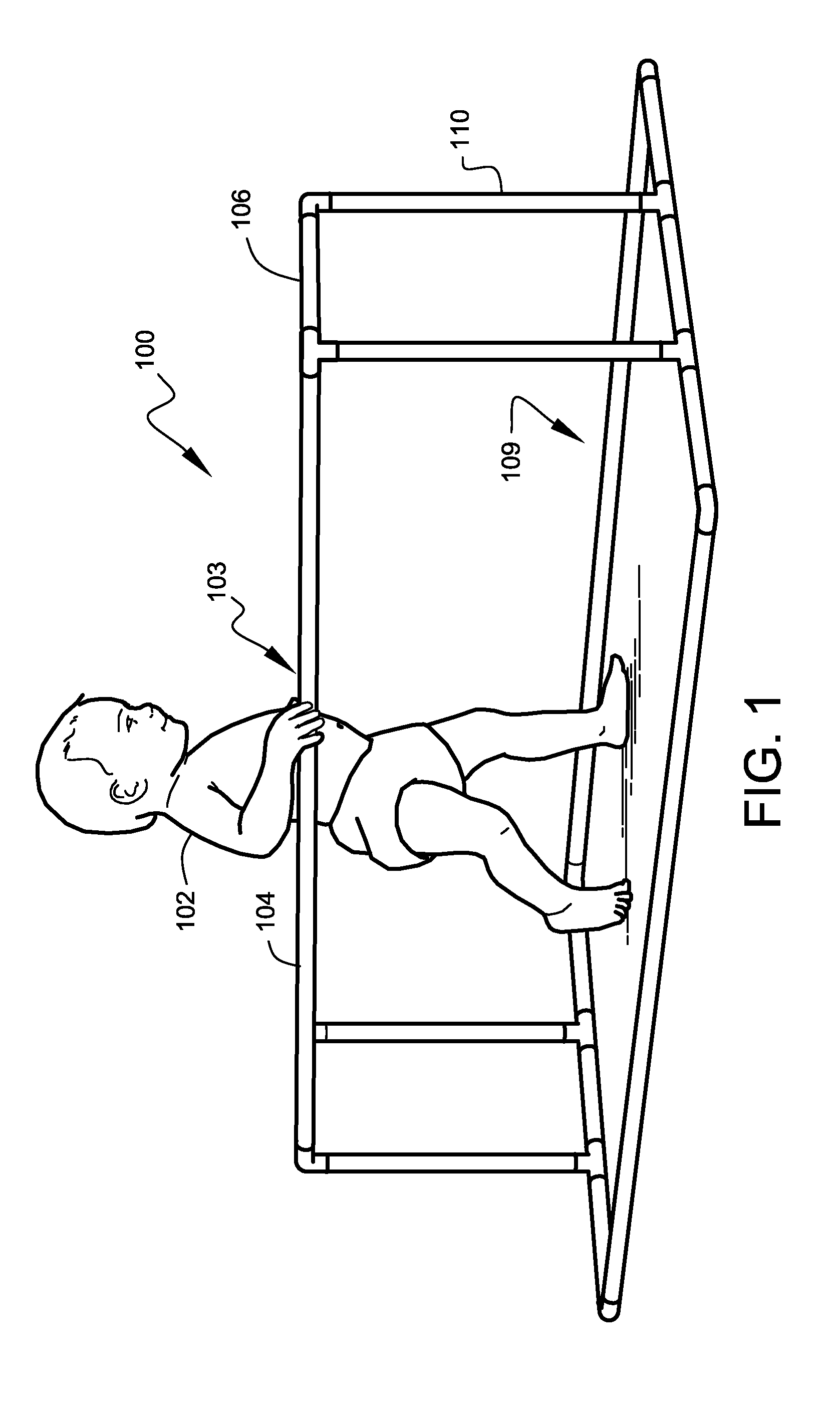
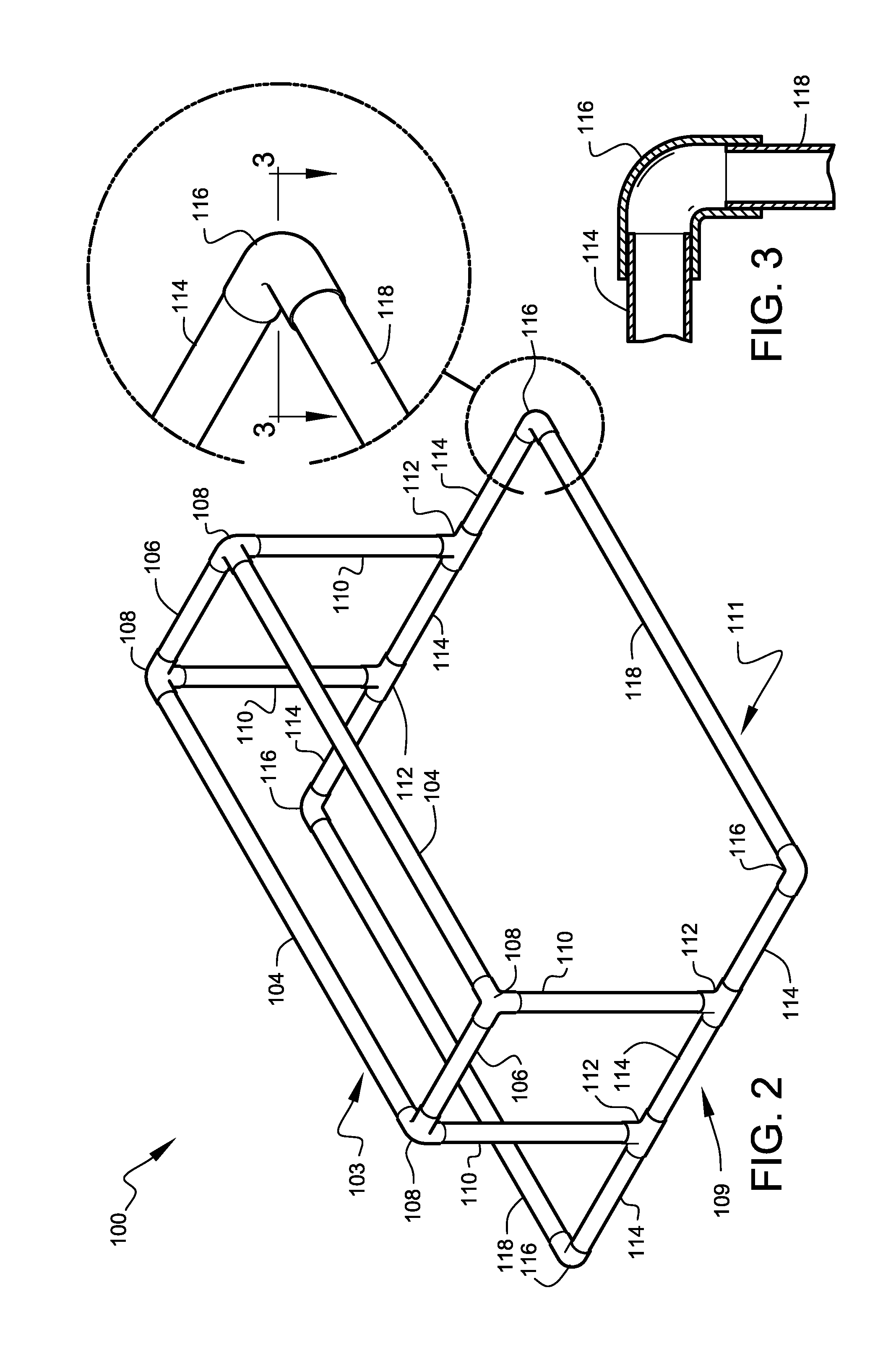
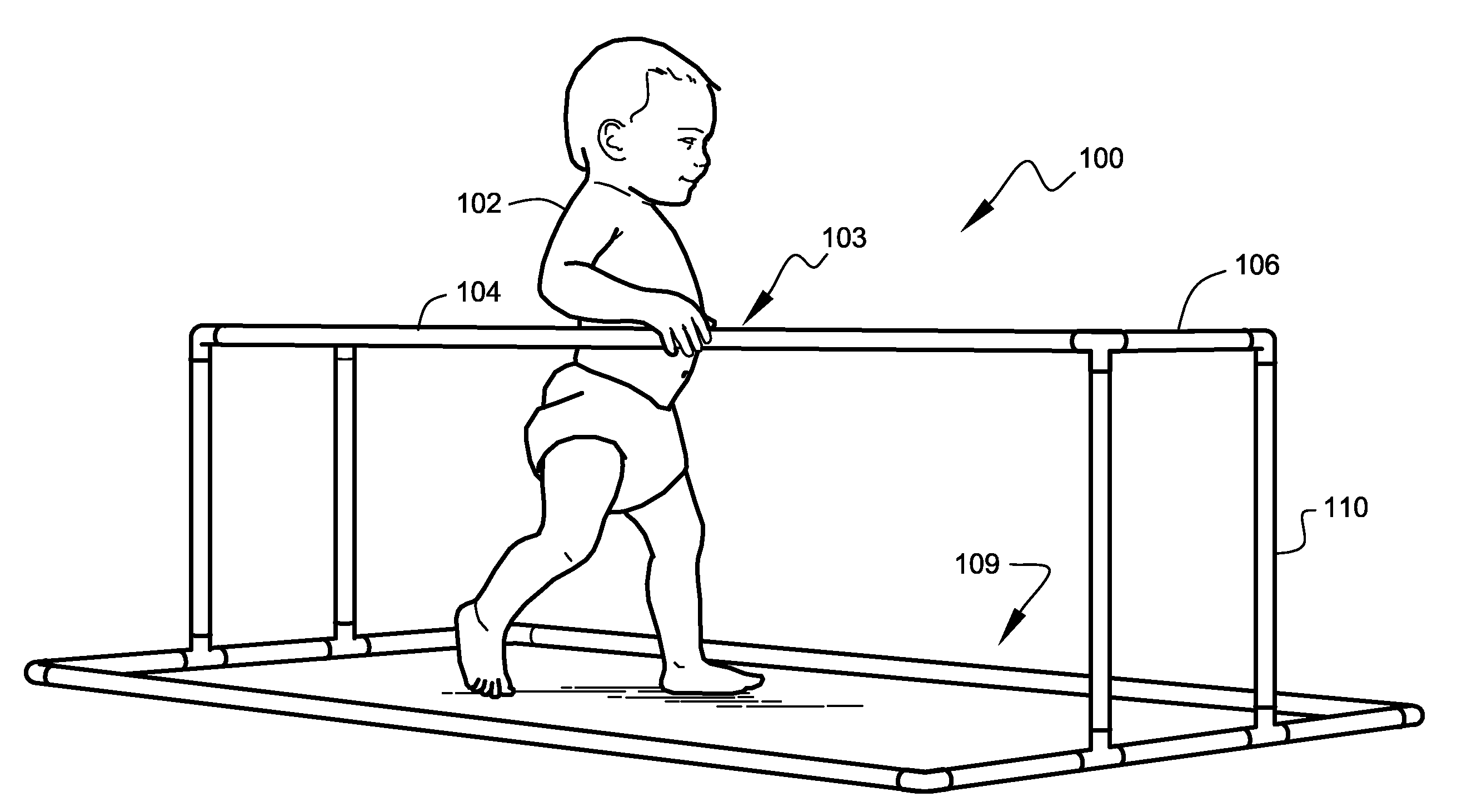
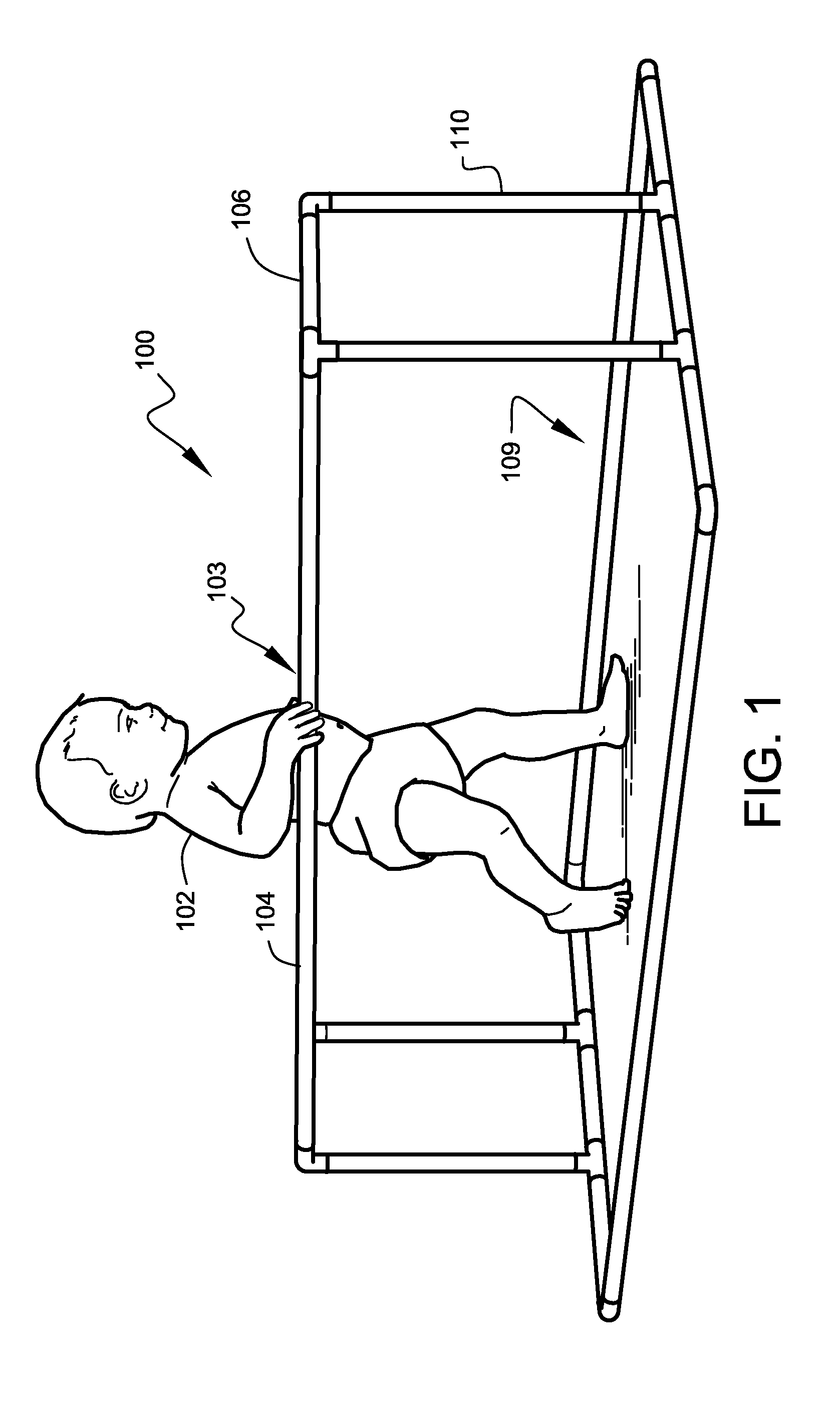
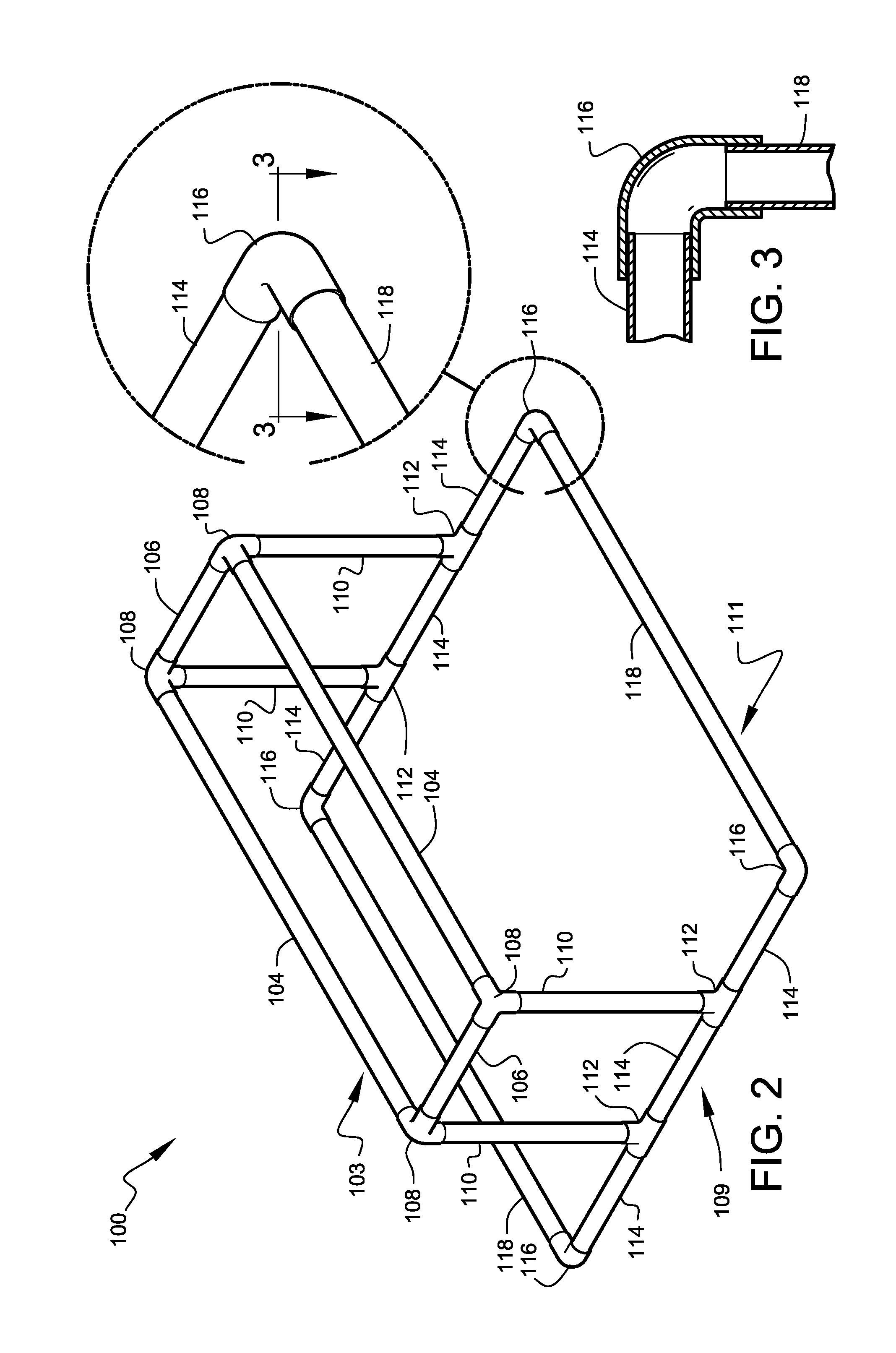
Infant activity systems
InactiveUS7713175B2Easy to trainEasy and inexpensive to manufactureGymnastic climbingKids convertible furnitureTO-18Engineering
A safe and fun exercise and walking-training apparatus and method that is ideal for infants in the approximate age range of 10 months to 18 months is disclosed. The apparatus is lightweight, very sturdy, very simple, consisting of only six unique elements, and may be assembled and disassembled by hand without tools. A system of attachable play features is also disclosed.
Owner:MONAGHAN MICHAEL J
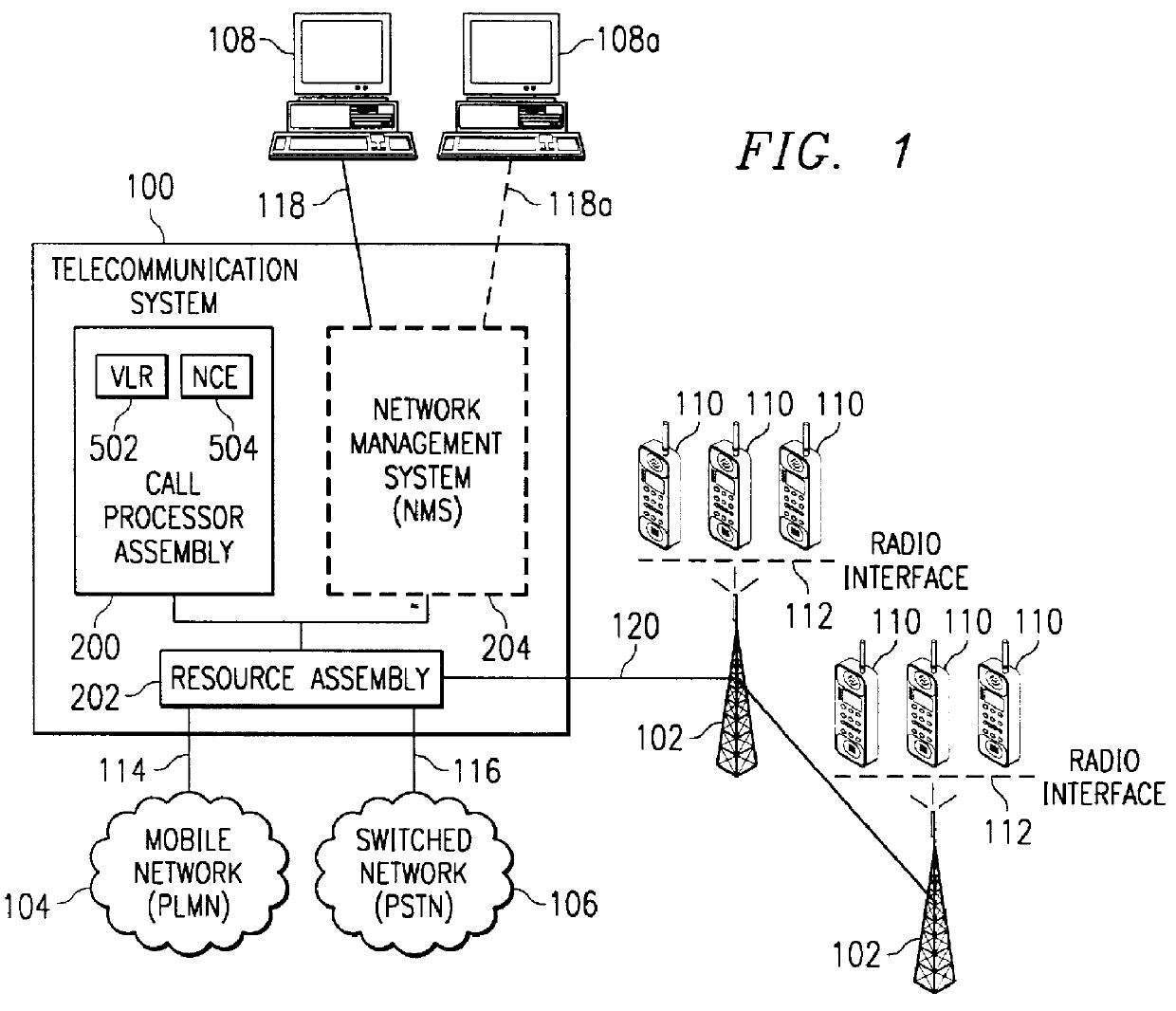
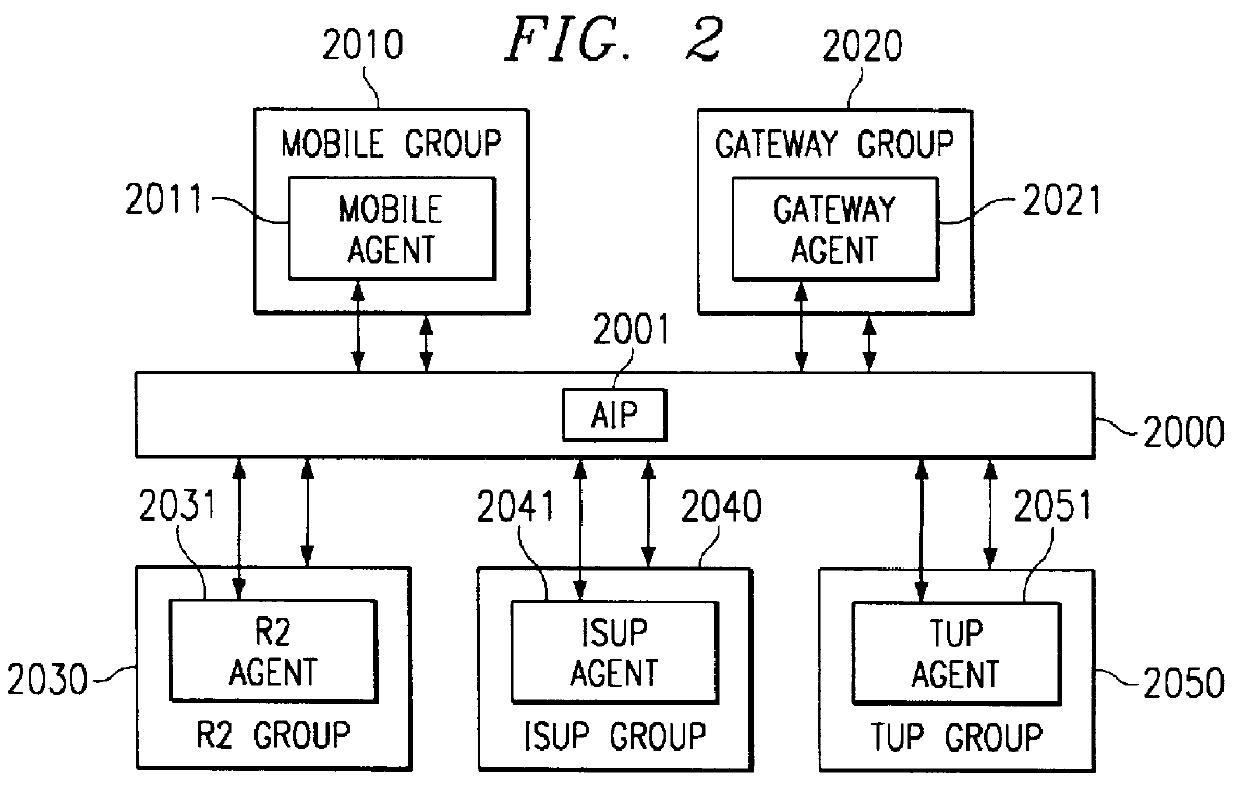
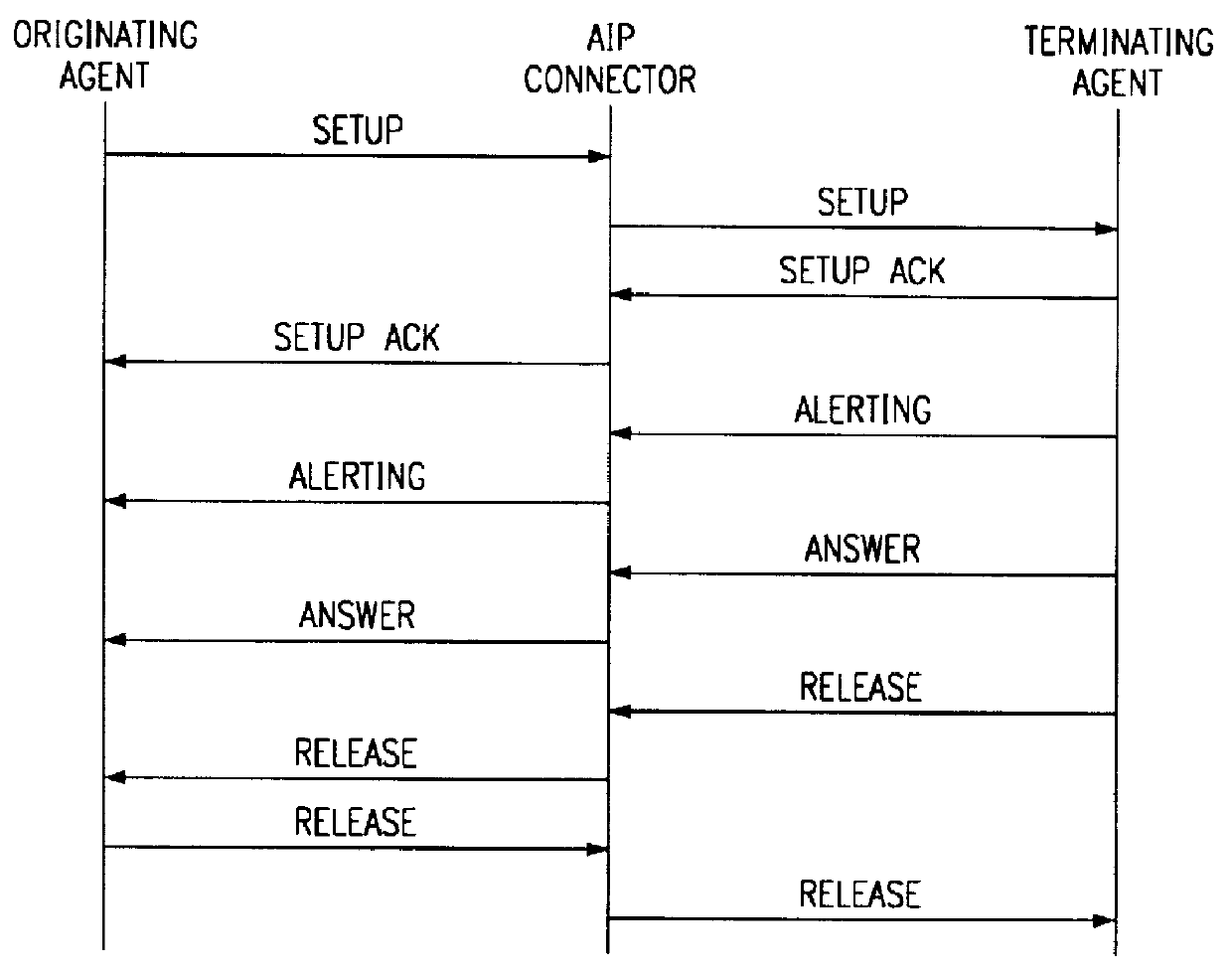
Agent interworking protocol and call processing architecture for a communications system
InactiveUSH1941H1Software engineeringMultiprogramming arrangementsCommunications systemProtocol for Carrying Authentication for Network Access
A call processing architecture treats a call connection as having two halves an originating half and a terminating half. An agent is associated with each call half, the originating agent being assigned by a switching center of a telecommunications system to establish the originating half of a call. The originating agent interacts with a translator and router to process the dated digits for a call to route the call to a terminating agent, the terminating agent establishing the terminating half of the call to complete the call connection. An agent interworking protocol (AIP) provides a generic superset protocol containing the common elements and unique elements for all call types so that an originating agent converts its call messages to the AIP and is connected to a terminating agent via an AIP connector, the terminating agent converting the AIP formatted call messages to the native protocol of the terminating agent. Agents for different call types are each able to convert call messages to or translate call messages from the agents's unique protocol to the AIP format and each type of agent does not need to know the type of agent being connected to as communication with other agents is via the AIP.
Owner:DSCCELCORE
Integrated shopping cart for sale of third party products and services via the internet
ActiveUS7610218B2Simple systemBuying/selling/leasing transactionsSpecial data processing applicationsThird partyProduct order
The current invention includes an improved system for an e-commerce vendor to seamlessly incorporate products and services from a third party into its own e-commerce site. This system enables the e-commerce vendor to display the third party products and to accept orders and arrange fulfillment of these products through its own site in a manner that is seamless to the end user. When the e-commerce retailer requests product information from the supplier, the supplier provides the retailer with product information and URLs at which additional information can be located. The retailer uses this information to retrieve product images, descriptions and information and to display this information to its customer on its own site. Each of these items is tagged with a unique element identifier that contains a number of details about the product. This information tagged to the product image or description enables the product to be easily identified by both the retailer and the supplier. When the customer purchases the products from the retailer, the necessary information is tagged to the product information and, thus, is available for placement of the order with the supplier. This enables the product order to be routed to and fulfilled by the third party supplier in a manner that is transparent to the customer.
Owner:SYNIVERSE ICX LLC
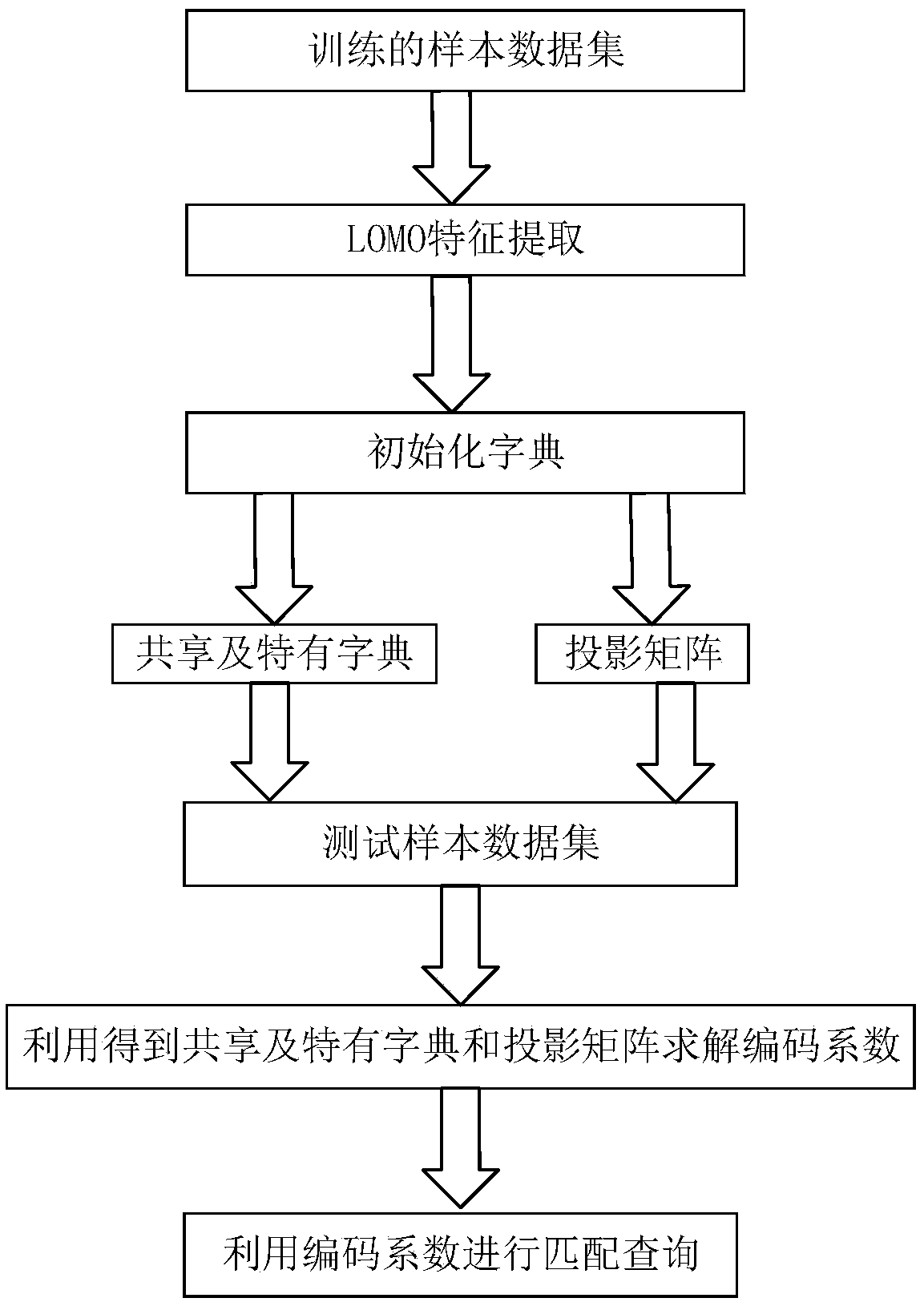
A pedestrian re-identification method based on joint learning of shared and unique dictionary
ActiveCN109409201AReduce ambiguityReduce interferenceCharacter and pattern recognitionSparse constraintAmbiguity
The invention provides a pedestrian re-identification method based on joint learning of a shared and unique dictionary, belonging to the technical field of digital image processing. Because each pedestrian is composed of shared elements reflecting their similarities and unique elements reflecting their identity uniqueness, it is proposed to reduce the ambiguity between pedestrian vision by removing the shared components of features. As that distance and coherence constraint term of the coding coefficient of the same pedestrian special component under the special dictionary are introduced, thesame pedestrian is forced to have similar code coefficients, and different pedestrians have weaker coherence; in addition, low-rank and sparse constraints are introduced to enhance the expressive power and discriminability of shared dictionaries and unique component dictionaries, respectively. The experimental results show that the method proposed by the invention has higher recognition performance than the traditional method.
Owner:KUNMING UNIV OF SCI & TECH
Optical sensing apparatus and method for determining highest intensity of light in an array
InactiveUS7265331B2Photometry using reference valueInstruments for comonautical navigationLight sensingHigh intensity
A plurality of optical sensing elements in an array where each element has a unique element address identifying the element location. Each element senses light and produces an element address signal in proportion to the intensity of the light sensed by the element. The element address signal corresponding to the highest intensity sensed by the array is asserted as an array output signal.
Owner:THE BOEING CO
Succinct index structure for XML
InactiveUS20090222419A1Save spacePerform structural join operations efficientlySemi-structured data indexingSpecial data processing applicationsTheoretical computer scienceComputer software
Succinct data and index structures aim to maximize the efficiency of update and search operations on any data while setting the constraint of storage size to be close to the theoretical optimum. The succinct index structure of the invention indexes data represented in a hierarchical structure. The index is comprised of a symbol table of all distinct root-to-leaf paths as keys or unique element tag names as keys, wherein an entry for a key in the symbol table holds transformed topological information of nodes associated with the key together (FIG. 22) with an indication of the method of transformation used on the topological information (FIG. 17), and wherein the method of transformation used is based on the topological relationship between nodes that are associated with the key. The invention also concerns methods, computer systems and computer software for constructing, using and updating the succinct index structure.
Owner:NAT ICT AUSTRALIA
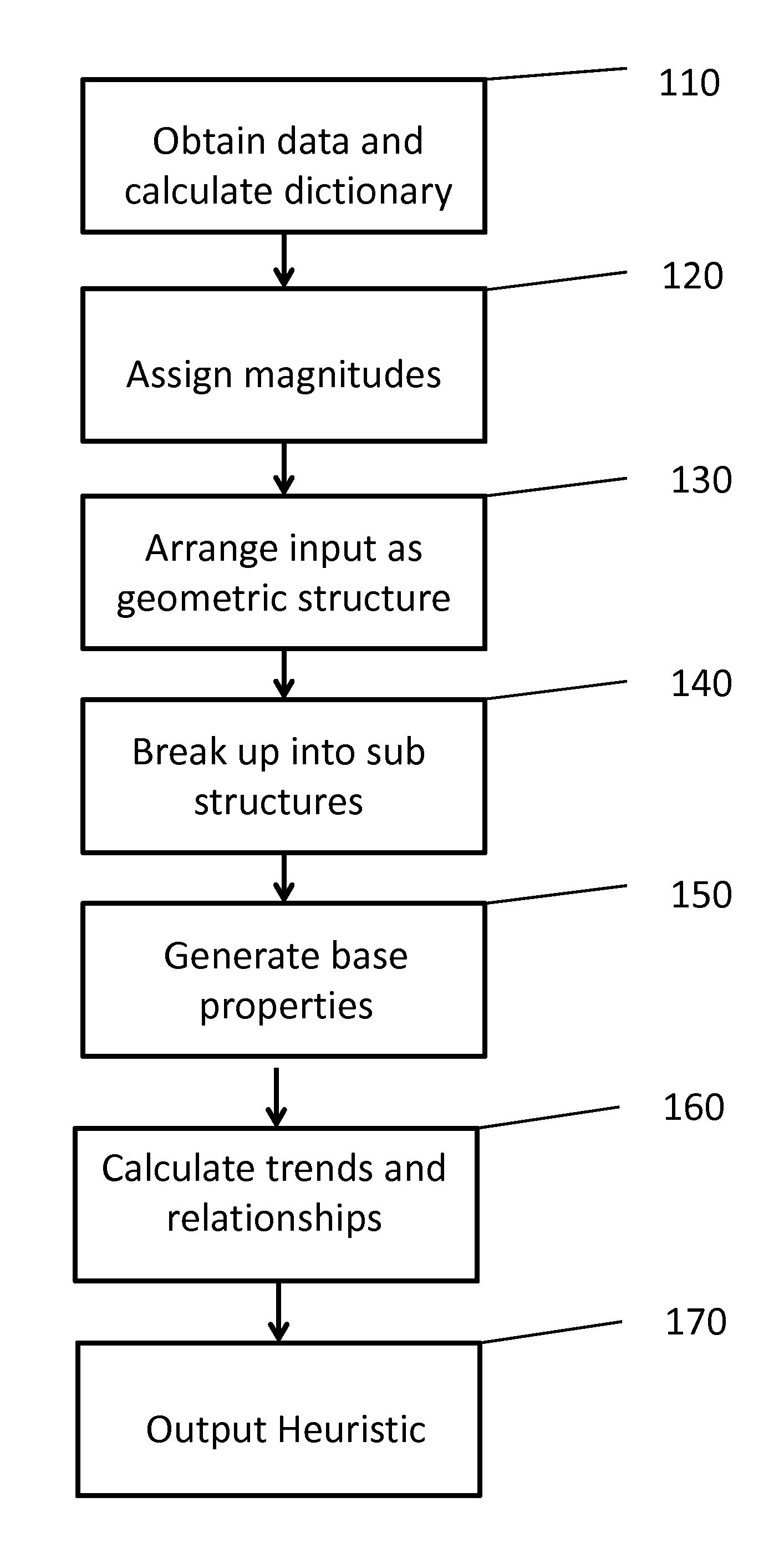
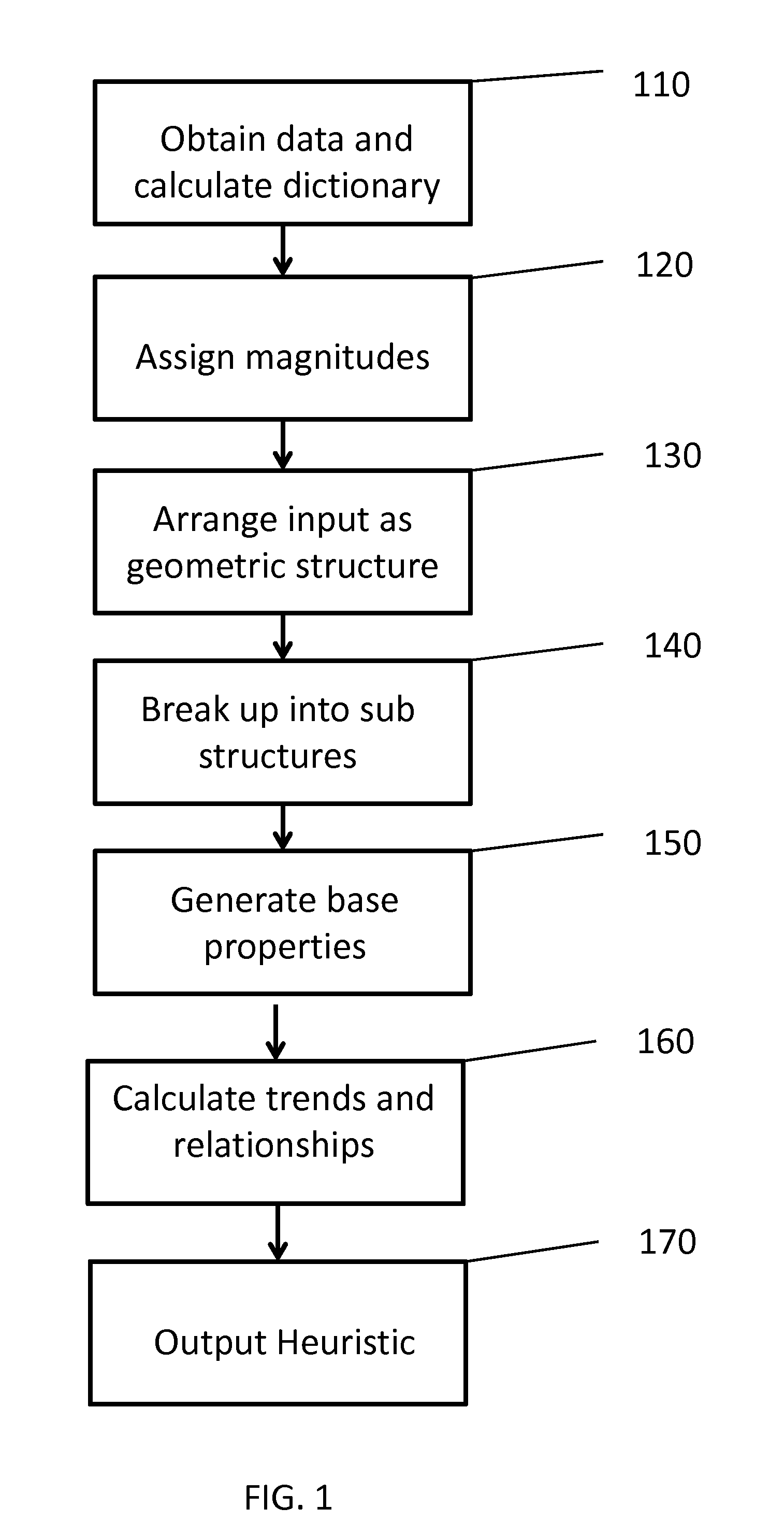
System and Method for Generation of a Heuristic
A system and method for generating a heuristic is provided. A heuristic is capable of identifying data patterns. The method includes: extracting a data set from multiple input sources; creating a set of unique elements used across the data set; organizing the data set into a geometric structure; grouping portions of the data in the geometric structure into a plurality sub geometric structures; determining base attributes for each sub geometric structure using the set of unique elements; identifying trends in the base attributes among the sub geometric structures; and outputting the heuristic as a combination of the base attributes and the trends.
Owner:SPARKCOGNITION INC
Infant Activity Systems
InactiveUS20060226615A1Easy to storeEasy to trainCarriage/perambulator with single axisKids convertible furnitureTO-18Engineering
A safe and fun exercise and walking-training apparatus and method that is ideal for infants in the approximate age range of 10 months to 18 months is disclosed. The apparatus is lightweight, very sturdy, very simple, consisting of only six unique elements, and may be assembled and disassembled by hand without tools. A system of attachable play features is also disclosed.
Owner:MONAGHAN MICHAEL J
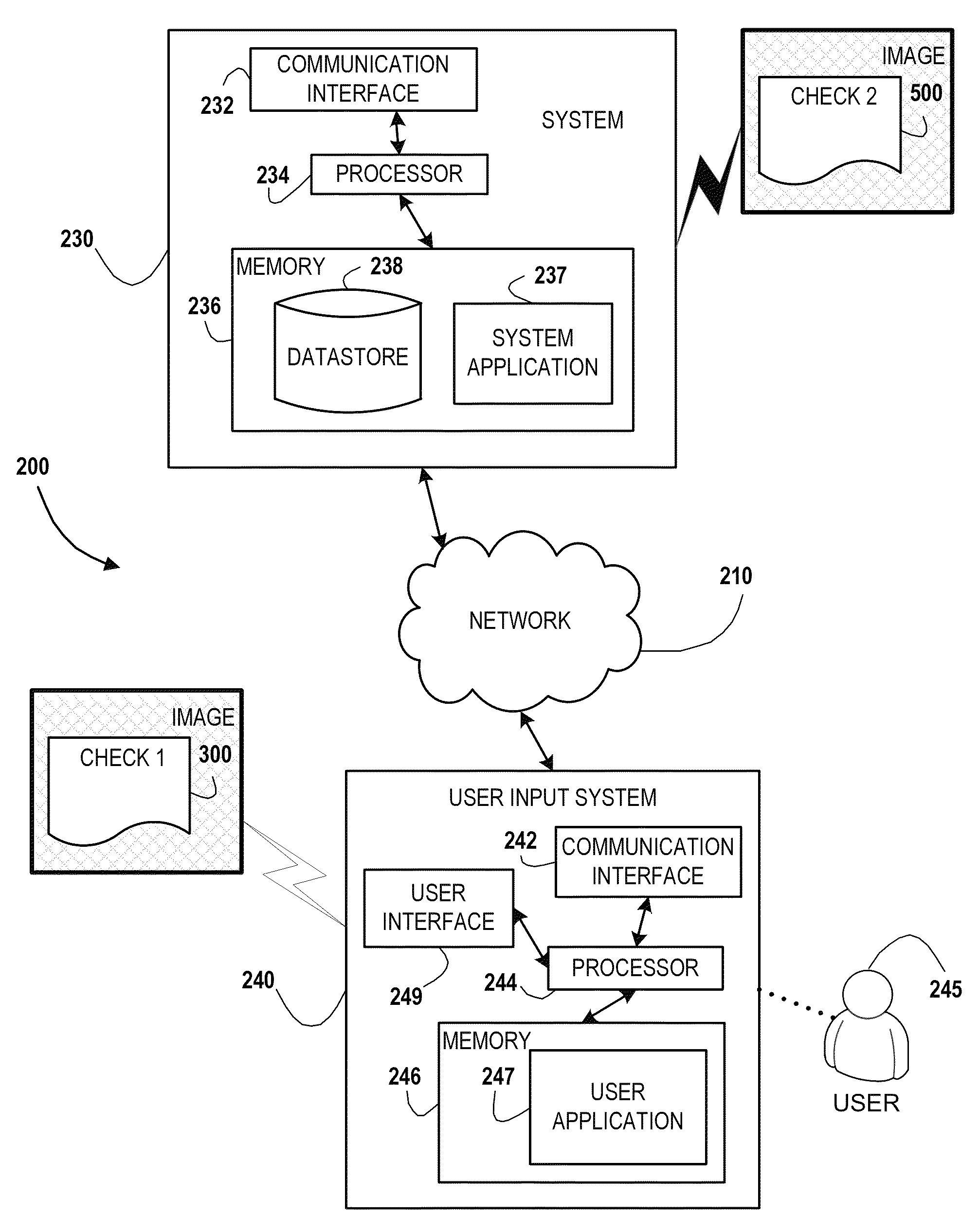
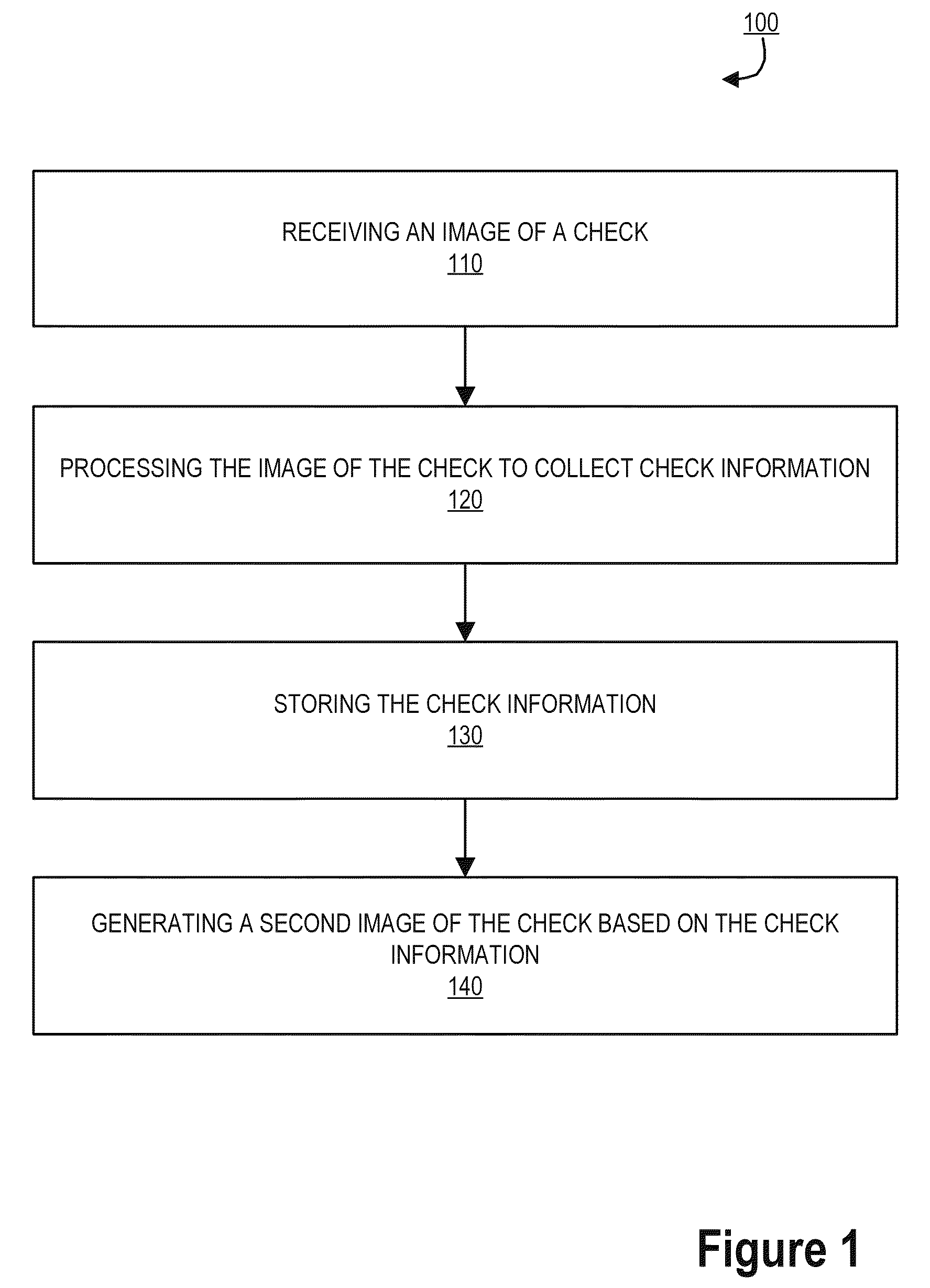
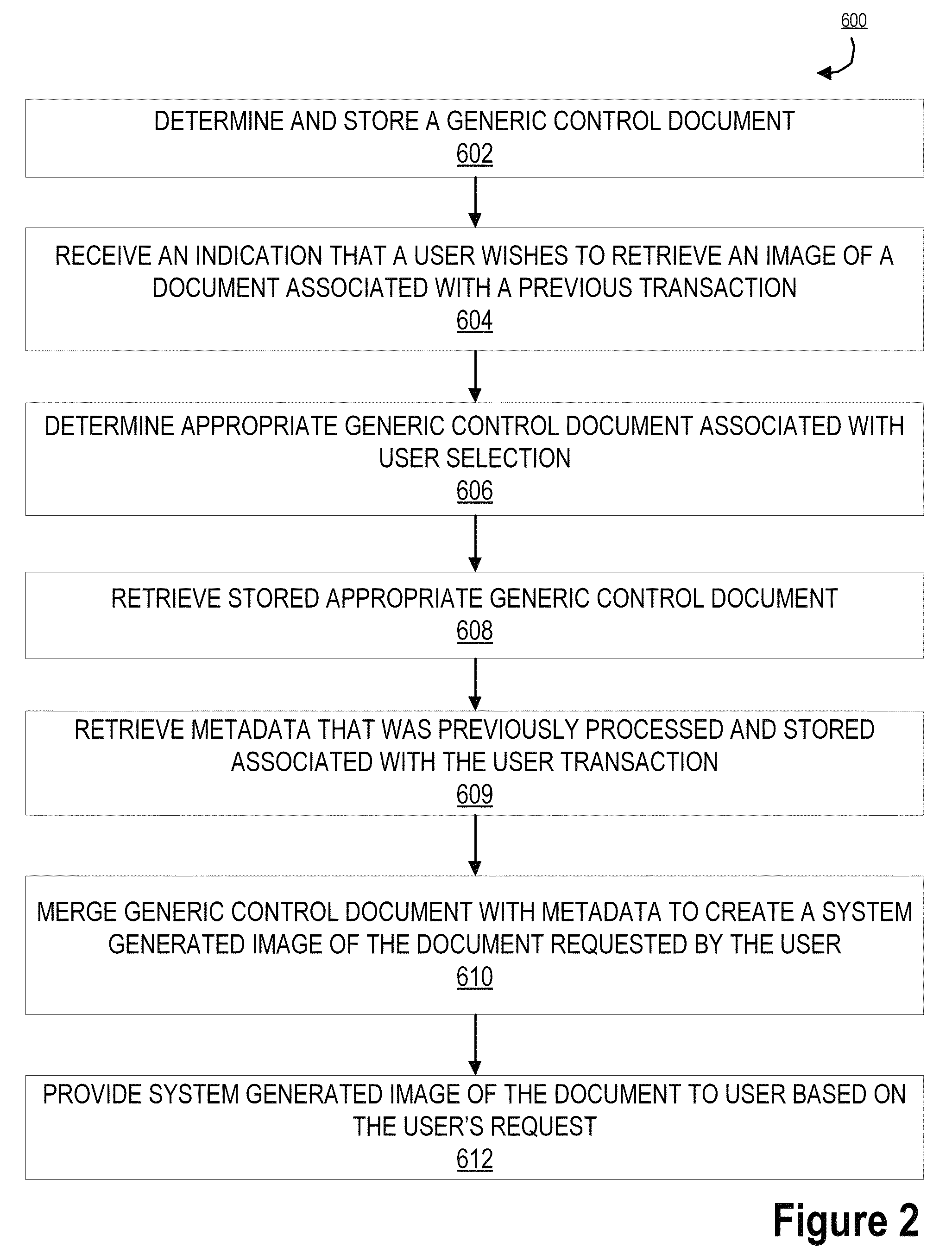
Image recreation using image lift data
ActiveUS9025851B2Reduce storage spaceComplete banking machinesFinanceRecreationComputer graphics (images)
Embodiments of the invention include systems, methods, and computer-program products for providing recreated image documents using image lift data. In this way, an entity may store limited amounts of image data from an original document and subsequently recreate the document image using image lift data. As such, the invention may receive an image document for storage. Upon receiving a document from a transaction for storage, the system may store metadata associated with that document, instead of storing the entire document as a high resolution image file. Furthermore, the system may determine specific unique elements of the document (such as signatures or the like) to capture as an image file. This allows the unique element to be lifted as image data. Using the lifted image data, in combination with the metadata, the system may recreate the image as a system generated image for user recall and reconciliation.
Owner:BANK OF AMERICA CORP
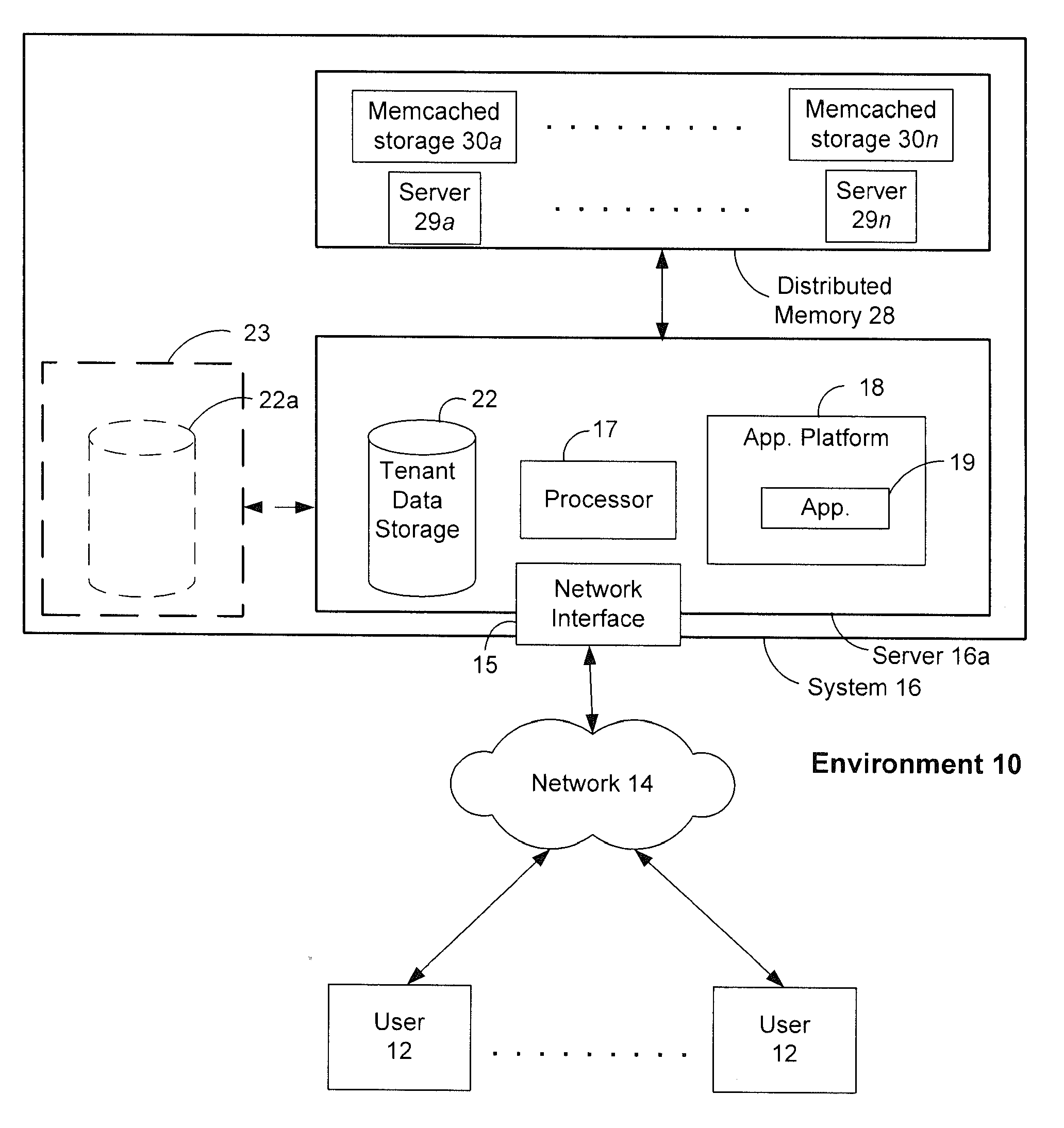
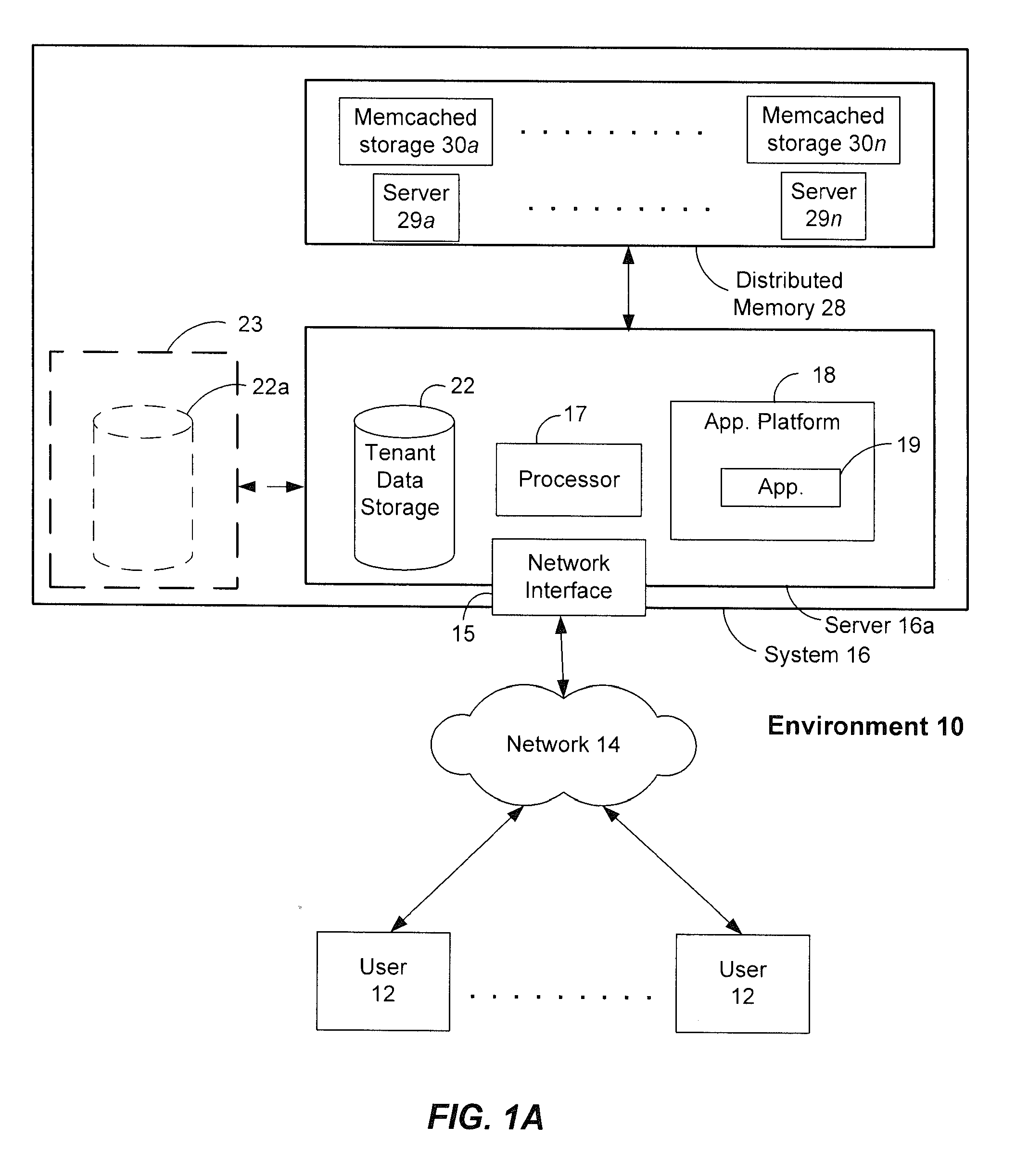
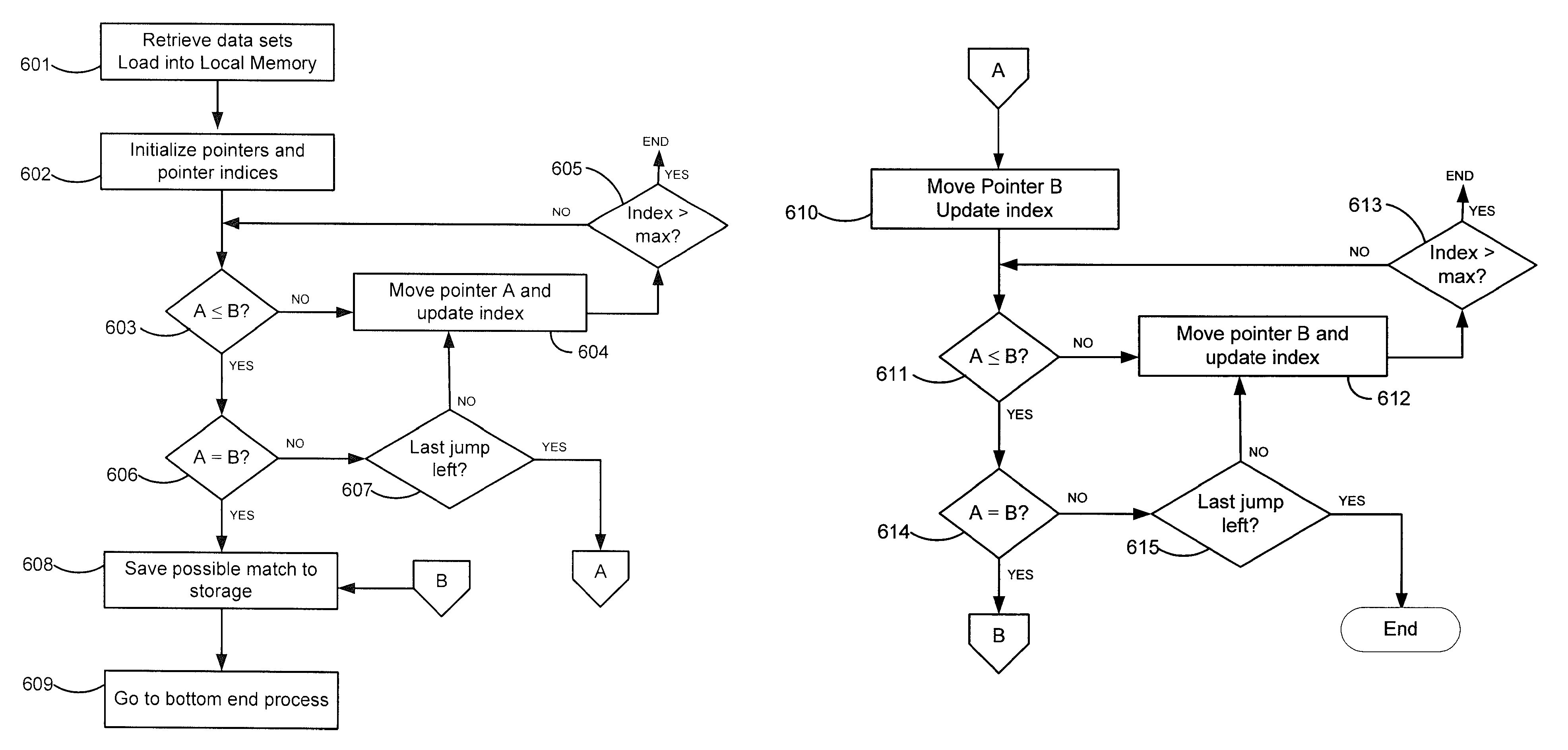
Methods and systems for latency-free database queries
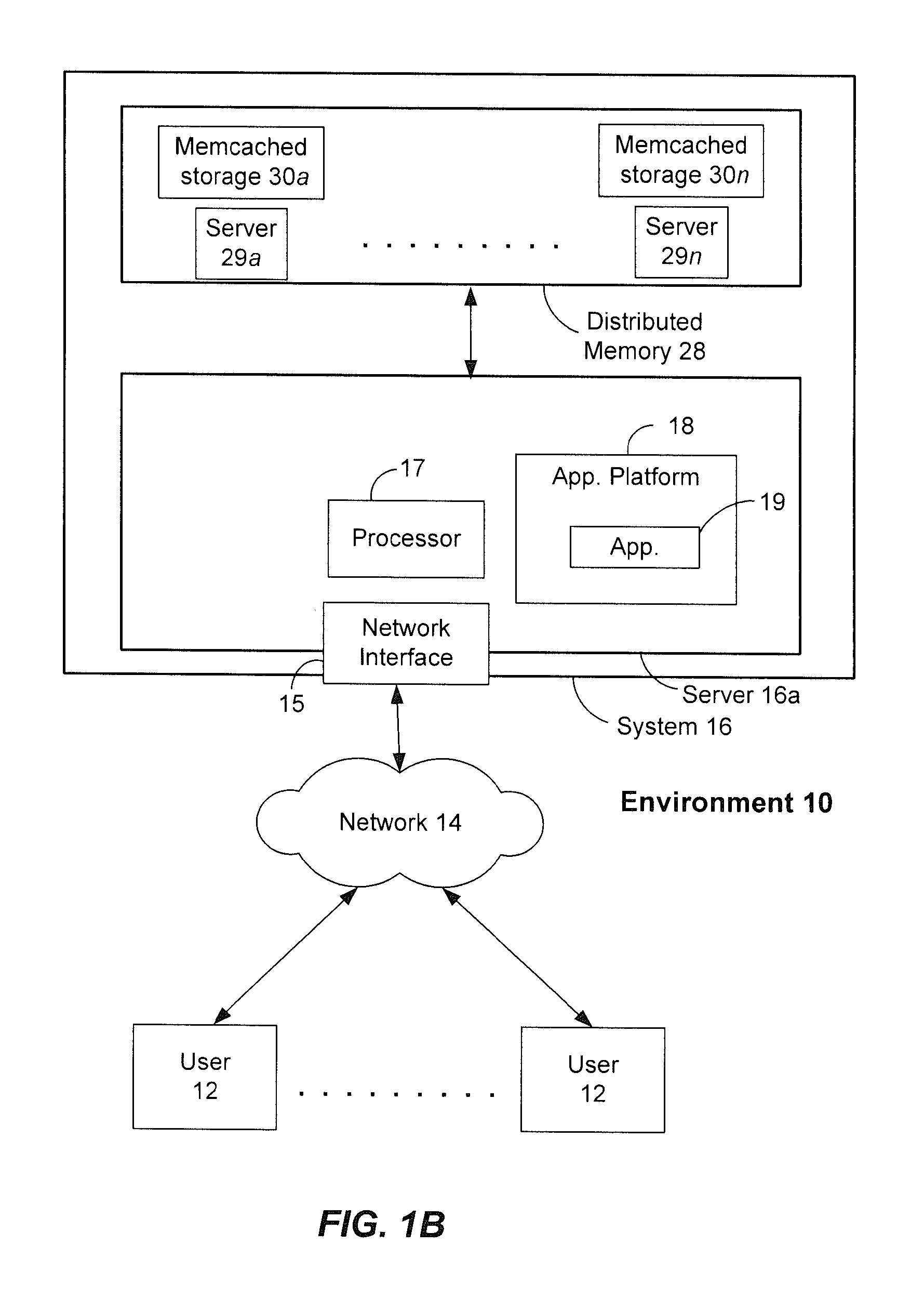
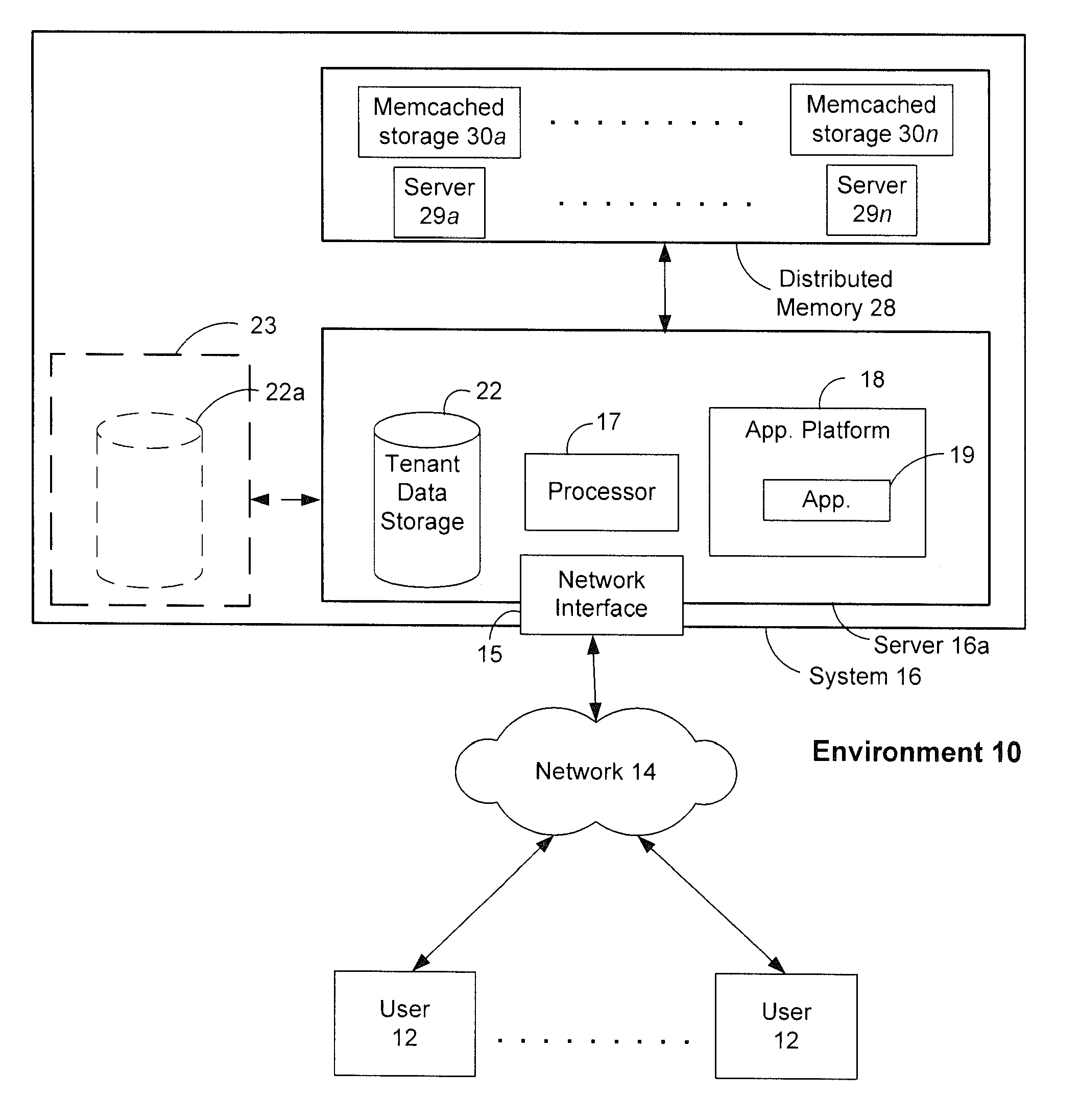
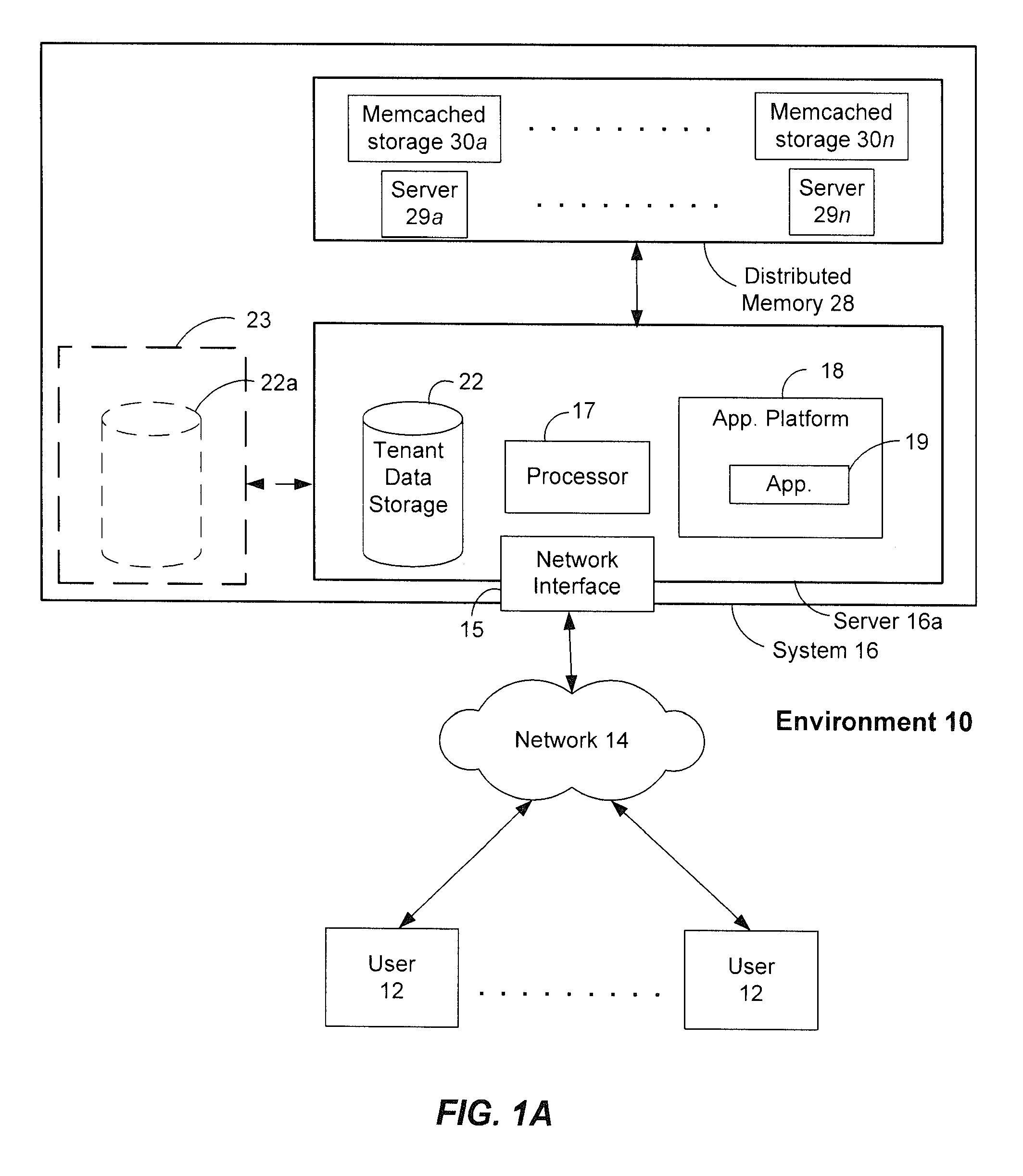
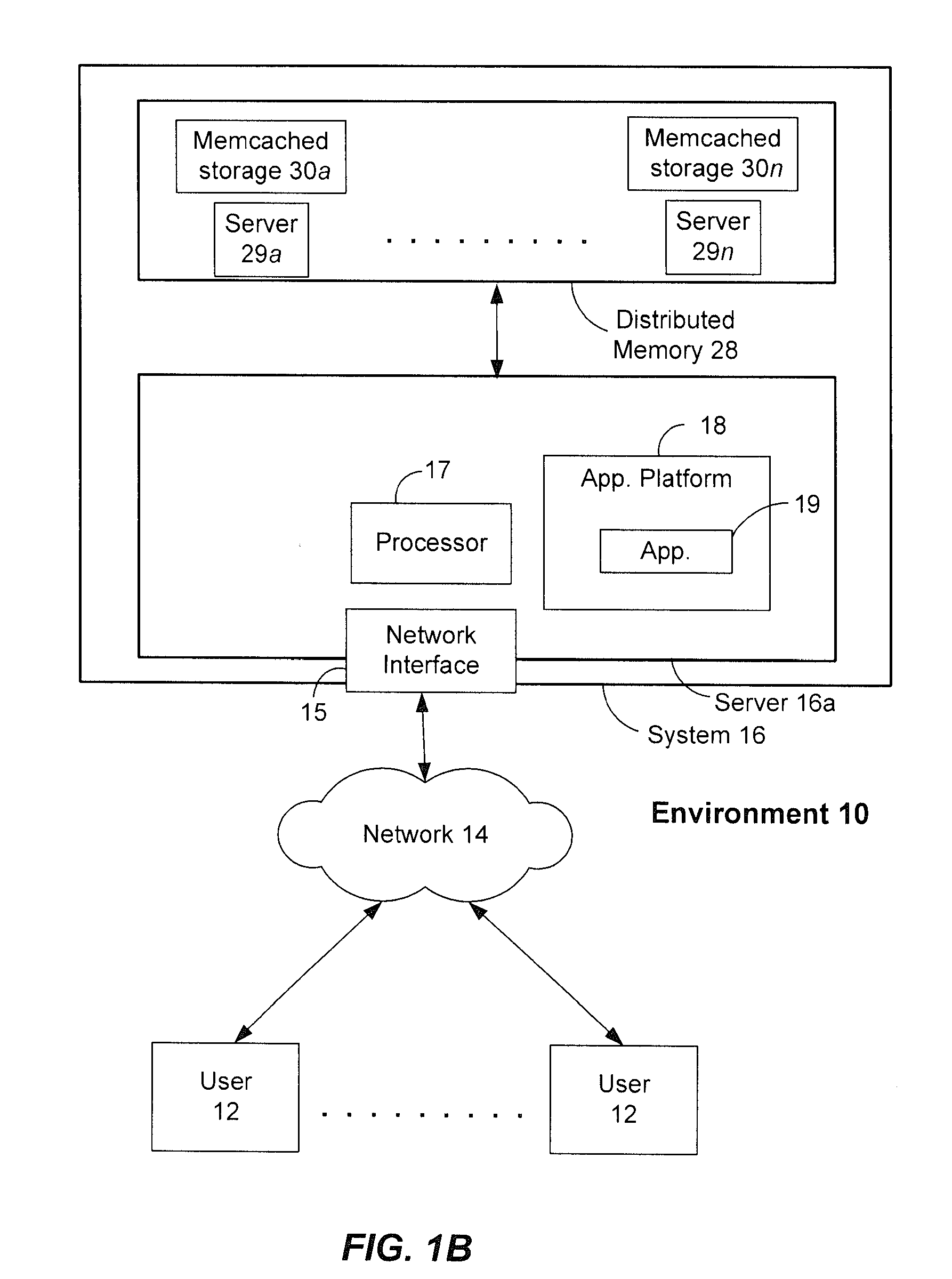
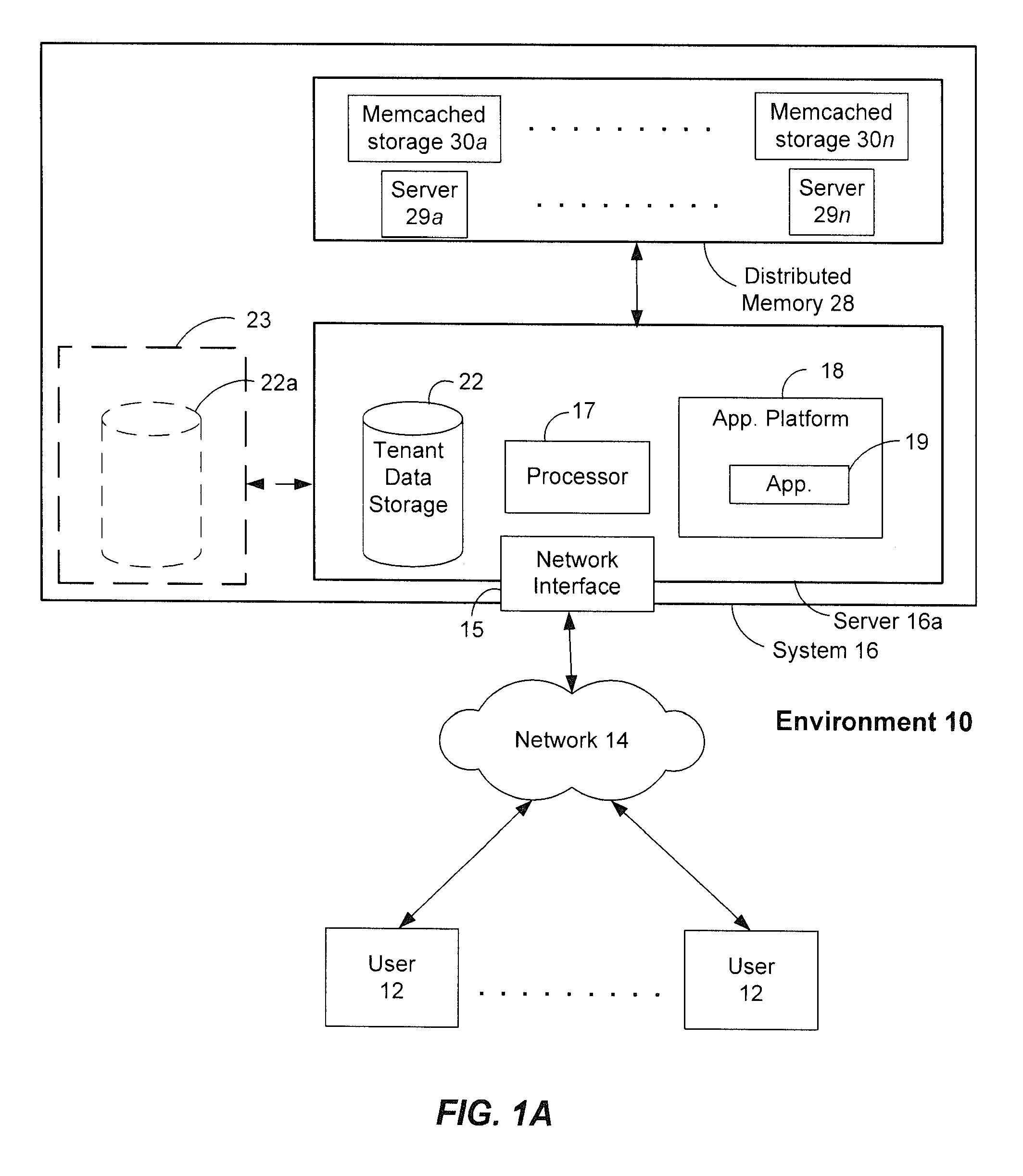
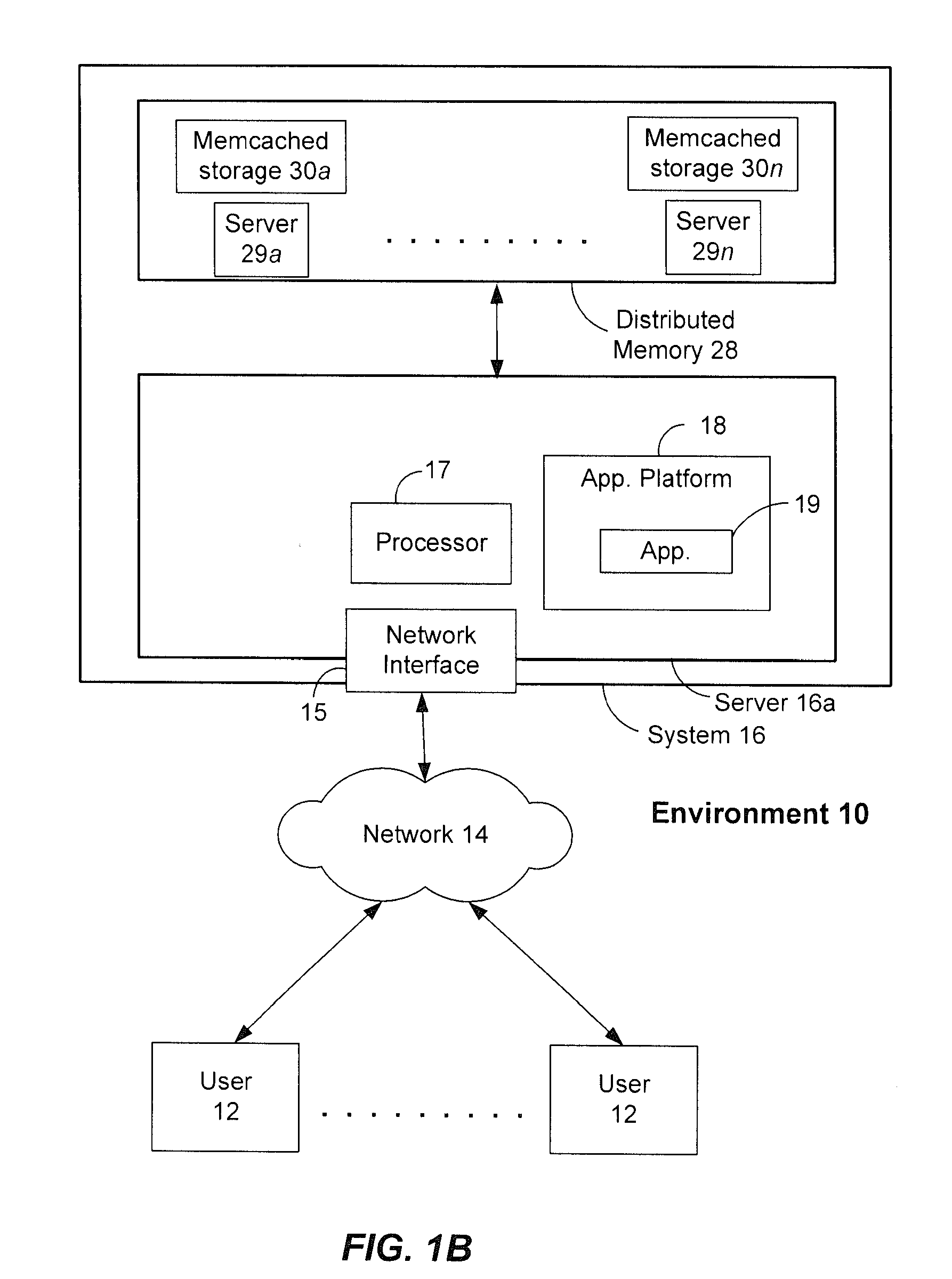
ActiveUS20120089647A1Not addressDigital data information retrievalDigital data processing detailsDatabase queryDistributed memory
Systems and methods for performing latency-free database searches using two-level indexed data structures having decreasing integer sets as identifiers to represent actual data. The indexed data structures are stored in distributed memory. Data operations such as intersection and union are performed using the indexed data structures. A binary interval reduction technique is used to quickly move through the data sets looking for common elements for the intersection set, or unique elements to add to the union set.
Owner:SALESFORCE COM INC
Methods and systems for latency-free contacts search
ActiveUS20120089638A1Not addressDigital data information retrievalDigital data processing detailsData setDistributed memory
Systems and methods for performing latency-free contact searches using two-level indexed data structures having decreasing integer sets as identifiers to represent actual contact data. The indexed data structures are stored in distributed memory. Data operations such as intersection and union are performed using the indexed data structures. A binary interval reduction technique is used to quickly move through the data sets looking for common elements for the intersection set, or unique elements to add to the union set.
Owner:SALESFORCE COM INC
Strong authentication method
ActiveUS20160149893A1Improve security levelMultiple keys/algorithms usageDigital data processing detailsAction CodeUnique identifier
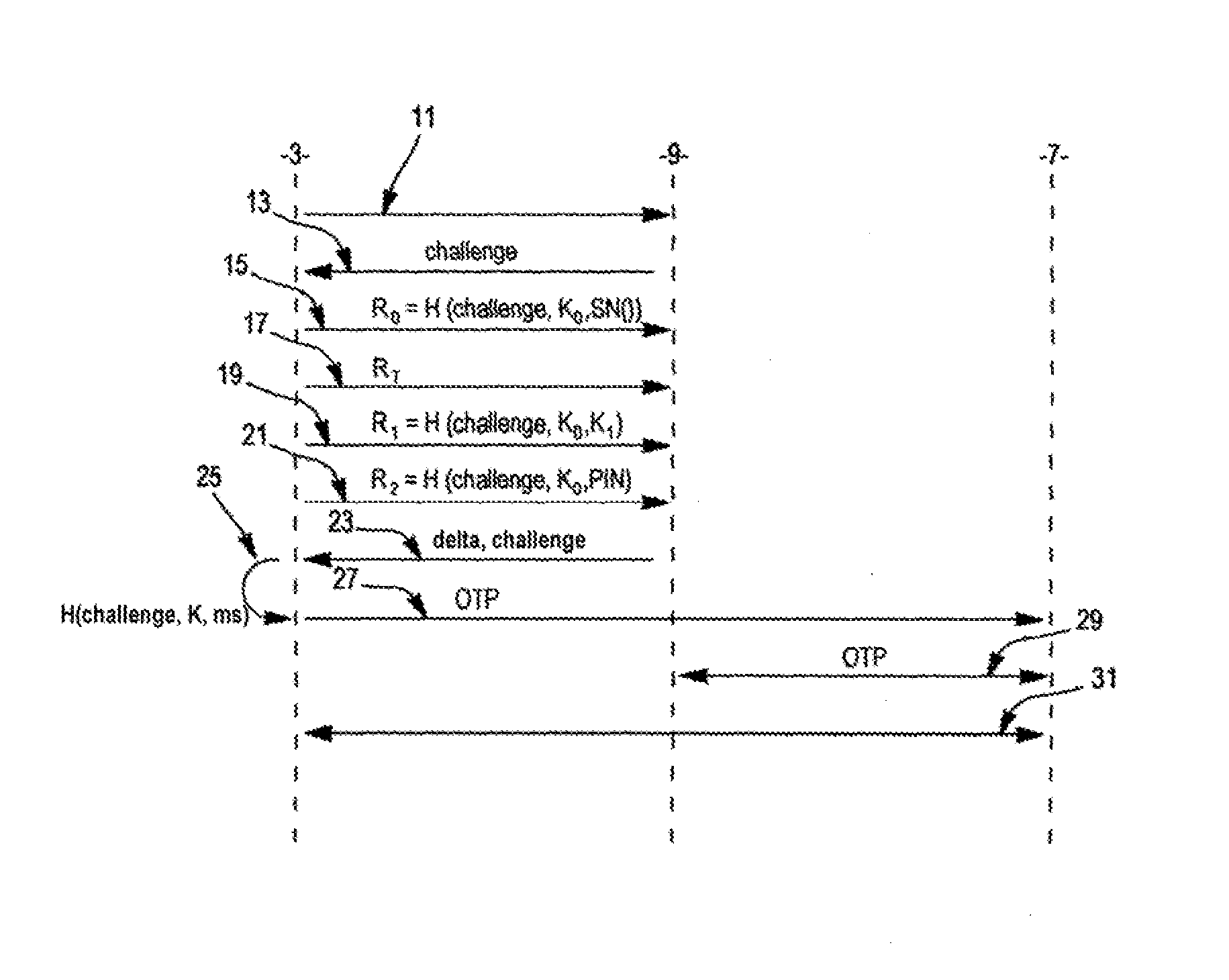
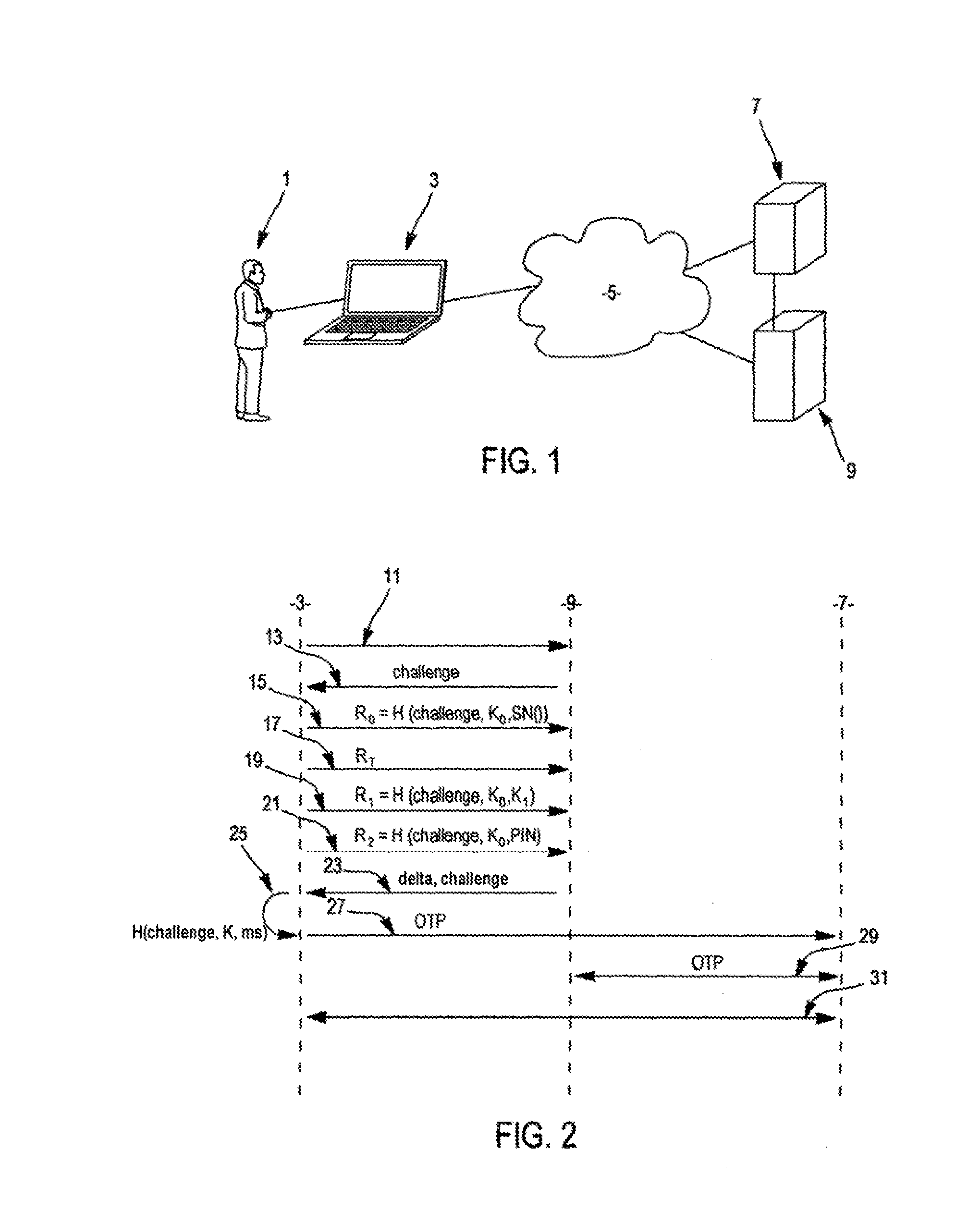
The present invention relates to a method of authenticating, with an authentication server, a user having at his disposal a calculator storing at least one unique identifier specific to the calculator and one first secret key (KO) and calculating a non-invertible function (H); the method comprising: • reception of the unique identifier by the authentication server, which sends an item of information (challenge) and an action code; • reception by the authentication server of three results of the non-invertible function, • the first result (R0) depending on at least one item of data specific to a unique or quasi-unique element of the calculator (SN); • the second result (RT) depending on a Turing test, conditioned to the action code, carried out by the user; and • the third result (R1) depending on a second secret key (K1); • authentication of the user if all four of the unique identifier and the first, second and third results are valid.
Owner:IN WEBO TECH
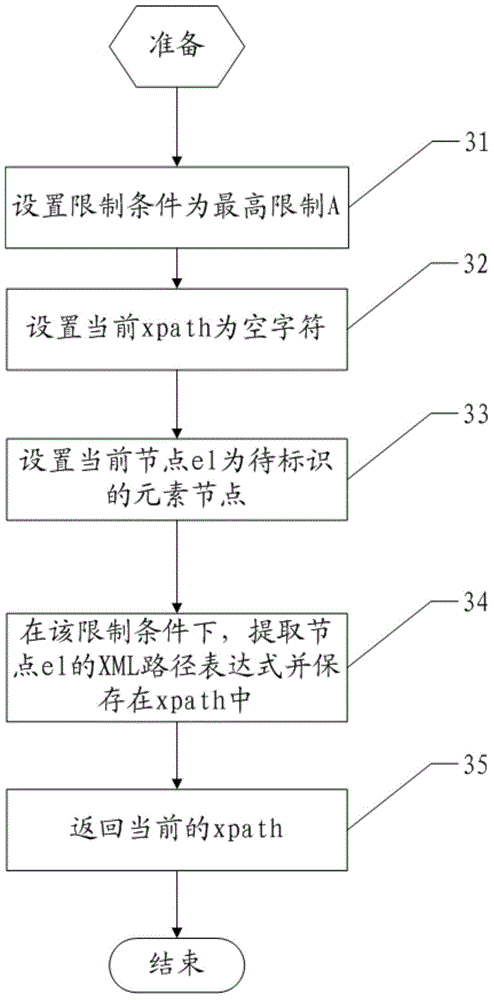
XML (extensive markup language) path expression extracting method and device
ActiveCN103605675AReduce the possibility of failureMultiprogramming arrangementsSpecial data processing applicationsNODALPath expression
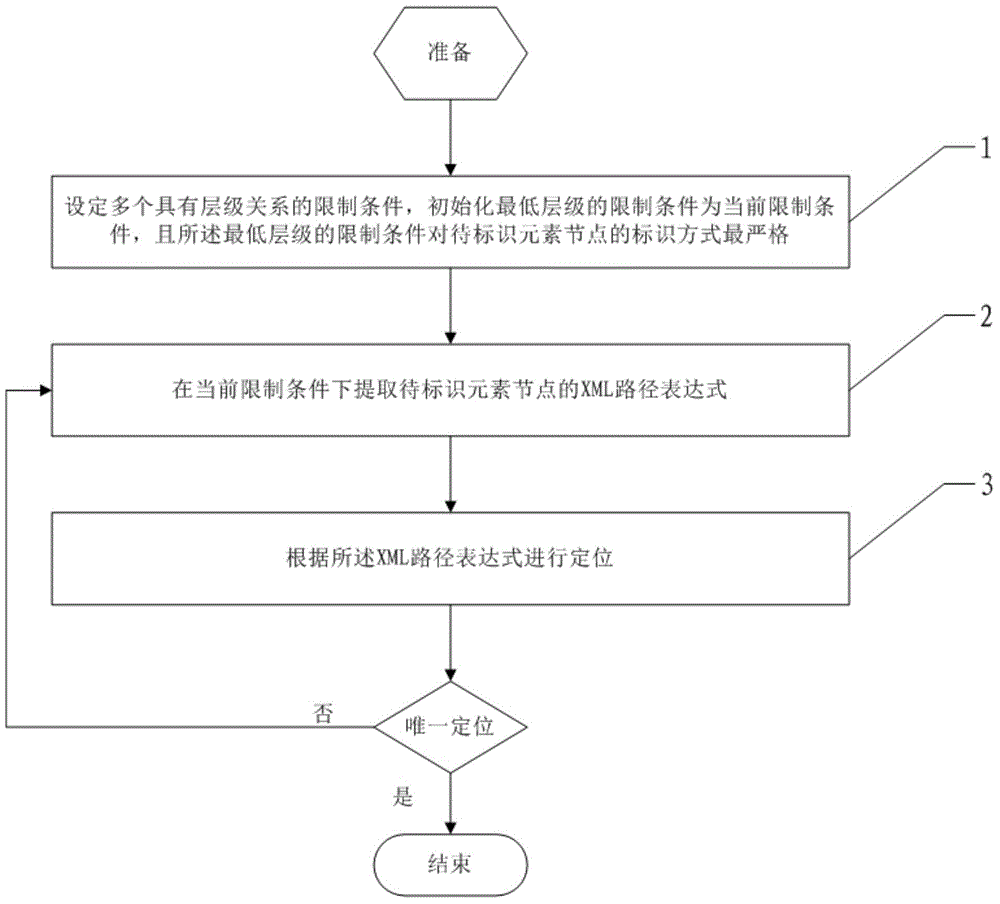
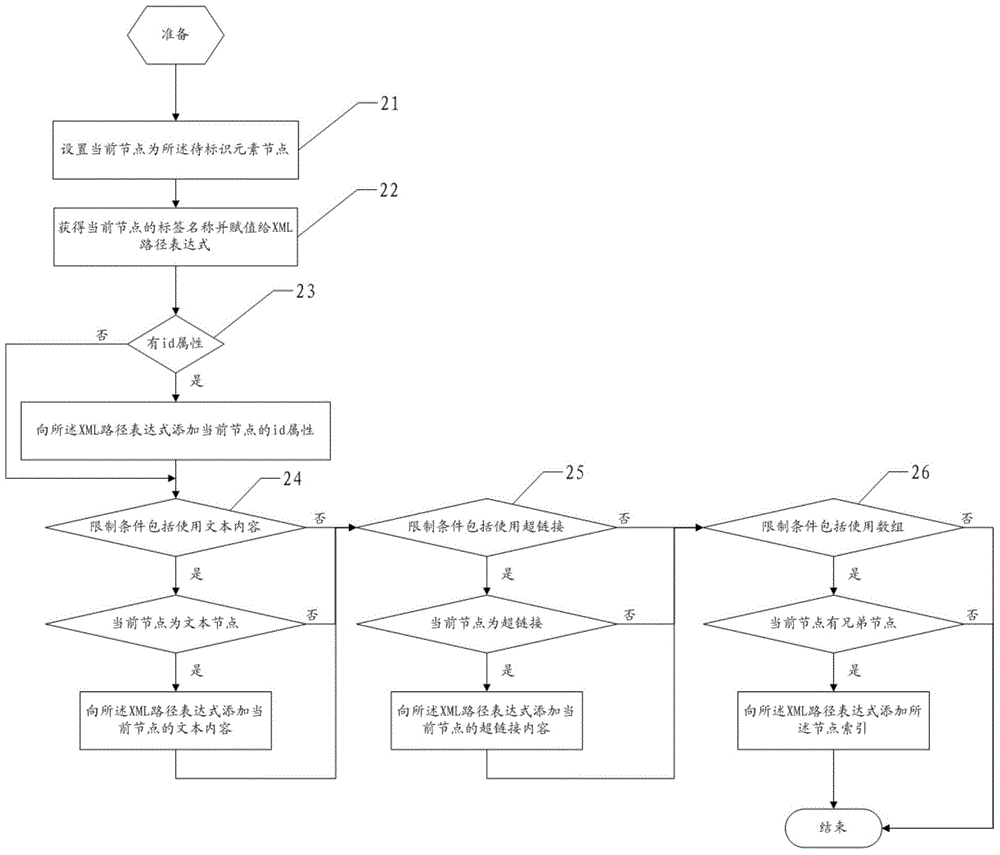
The invention discloses an XML path expression extracting method and device. The method comprises, step (1), setting limit conditions with a plurality of hierarchical relations and initializing the limit conditions of the lowest layer as current limit conditions; step (2), extracting the XML path expression of an element node to be identified under the current limit conditions; step (3), performing location according to the XML path expression, and if the XML path expression locates a unique element node, ending the XML path expression extraction; if not, namely, if the XML path expression locates more than one element nodes, selecting the limit conditions one layer above the current limit conditions as current limit conditions and re-executing the step (2). By means of the XML path expression which is as strict as possible, the XML path expression extracting method and device can reduce the possibility of XML path expression failures when web pages have small changes.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
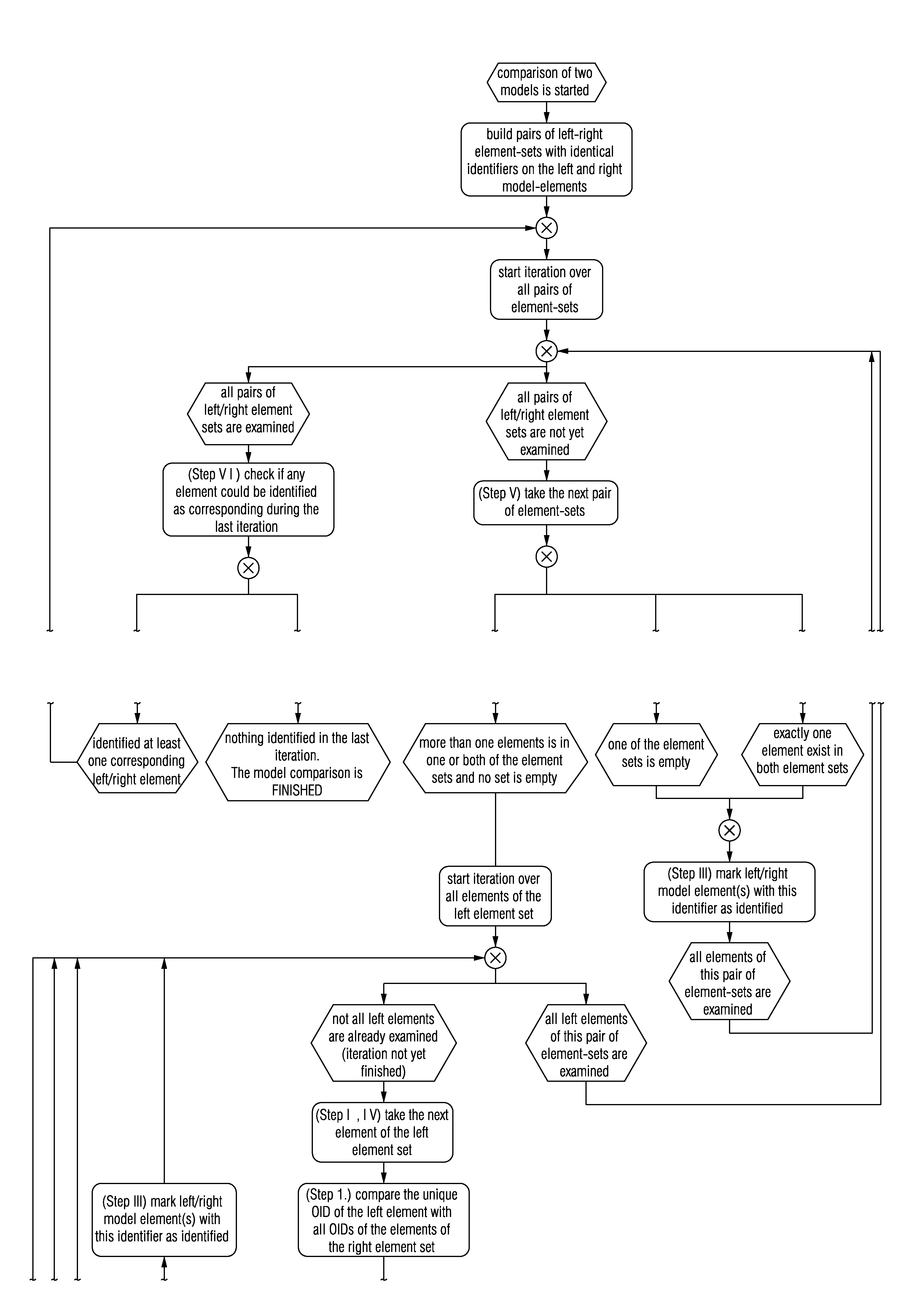
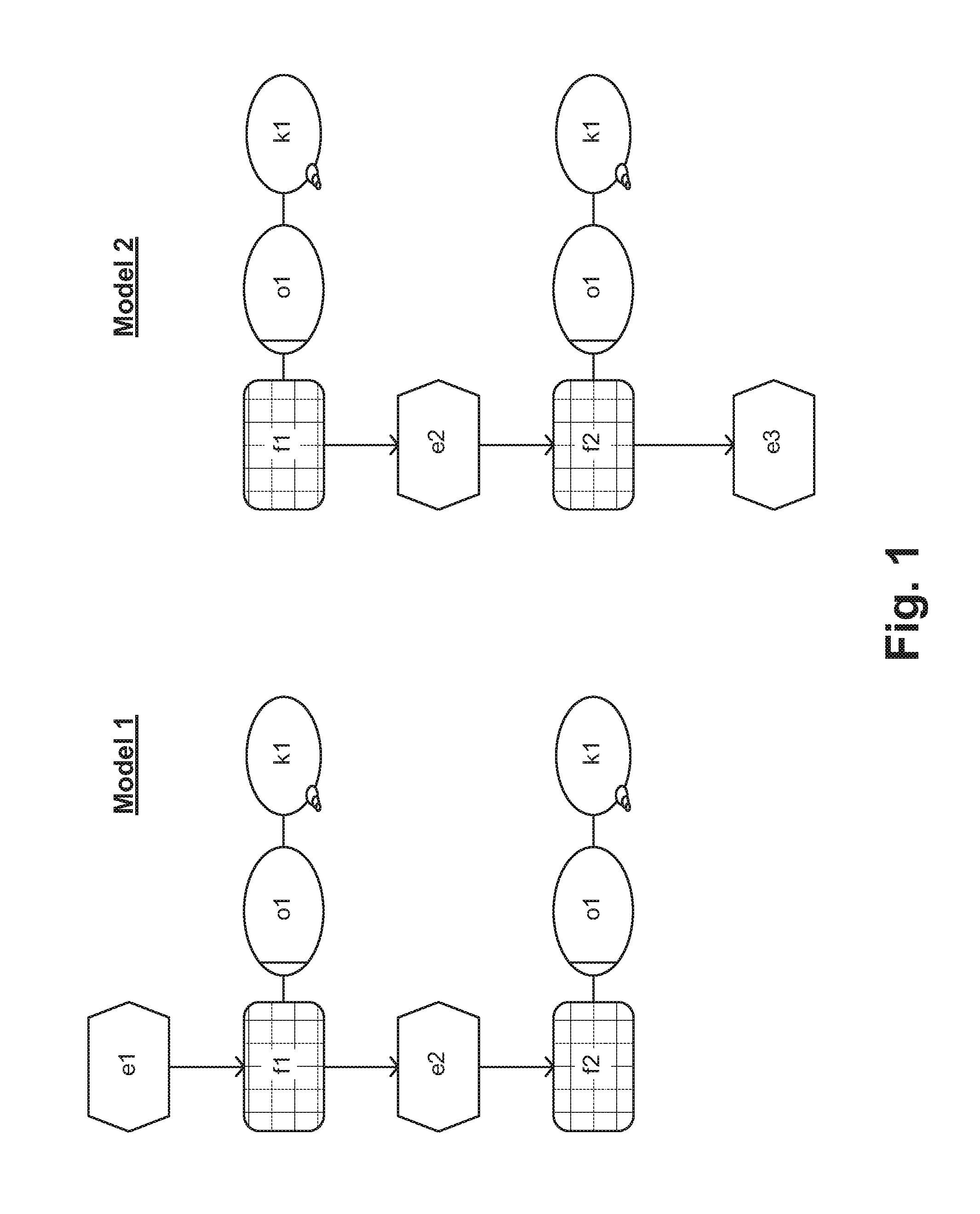
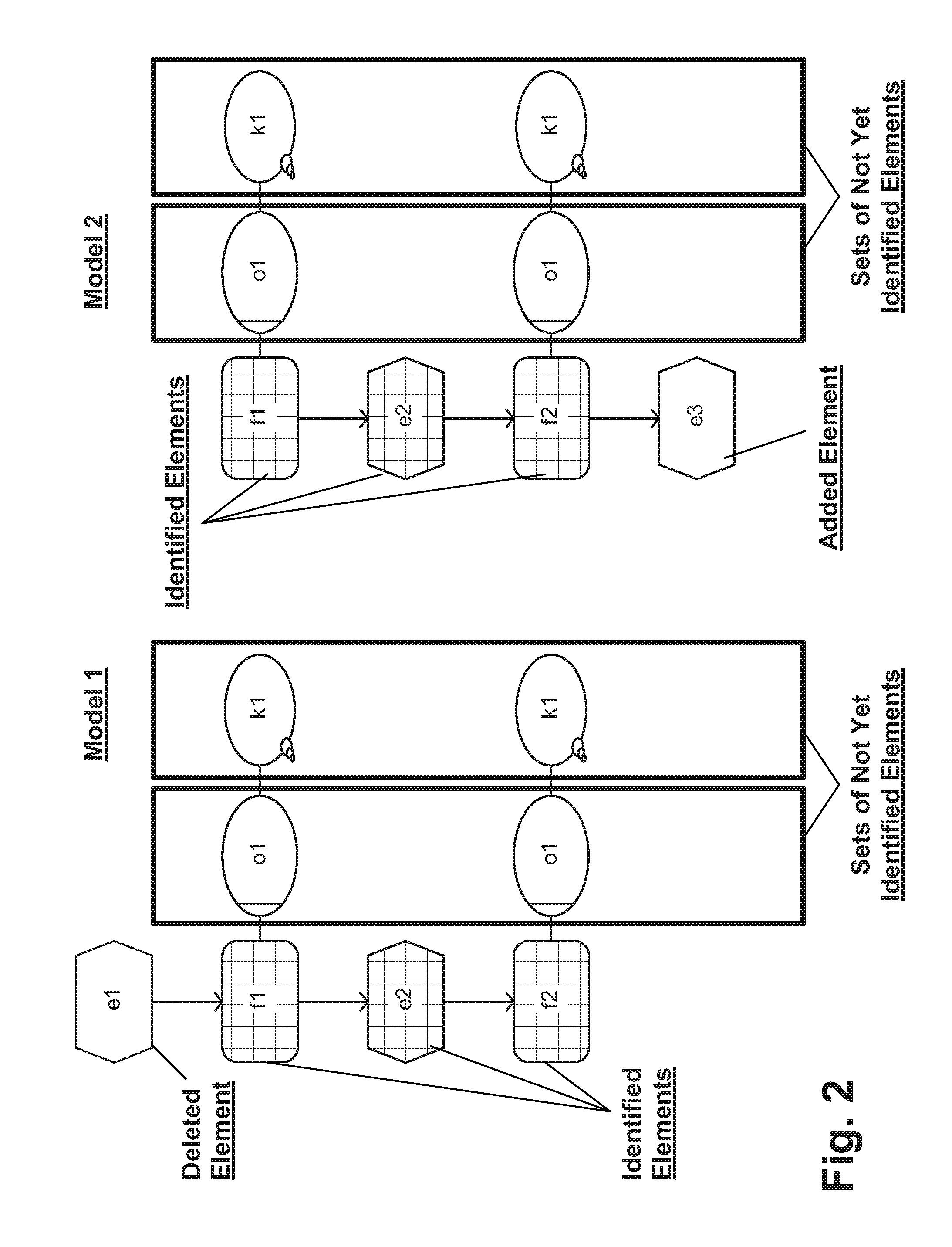
Systems and/or methods for identifying corresponding elements in different models
Certain example embodiments relate to systems and / or methods for identifying corresponding elements in different models (e.g., two or more different models), where multiple non-unique elements are connected with one another. The techniques of certain example embodiments are suitable for comparing the different models and identifying corresponding elements, regardless of whether the different models are different versions of one another, represent transformed and / or merged models, and / or were copied and subsequently modified from a source model. The techniques also advantageously leverage a more deterministic approach that is more consistent across different comparisons and when the source and target models are swapped.
Owner:SOFTWARE AG
Scalable stroke font system and method
A method of creating font format data from source font data includes analyzing the source font data to obtain glyph data for a plurality of glyphs, dissecting the glyph data, extracting midline data from the dissected glyph data, classifying the midline data as unique element data and common element data, associating unique element data and common element data to each glyph of the plurality of glyphs.
Owner:BLACKBERRY LTD
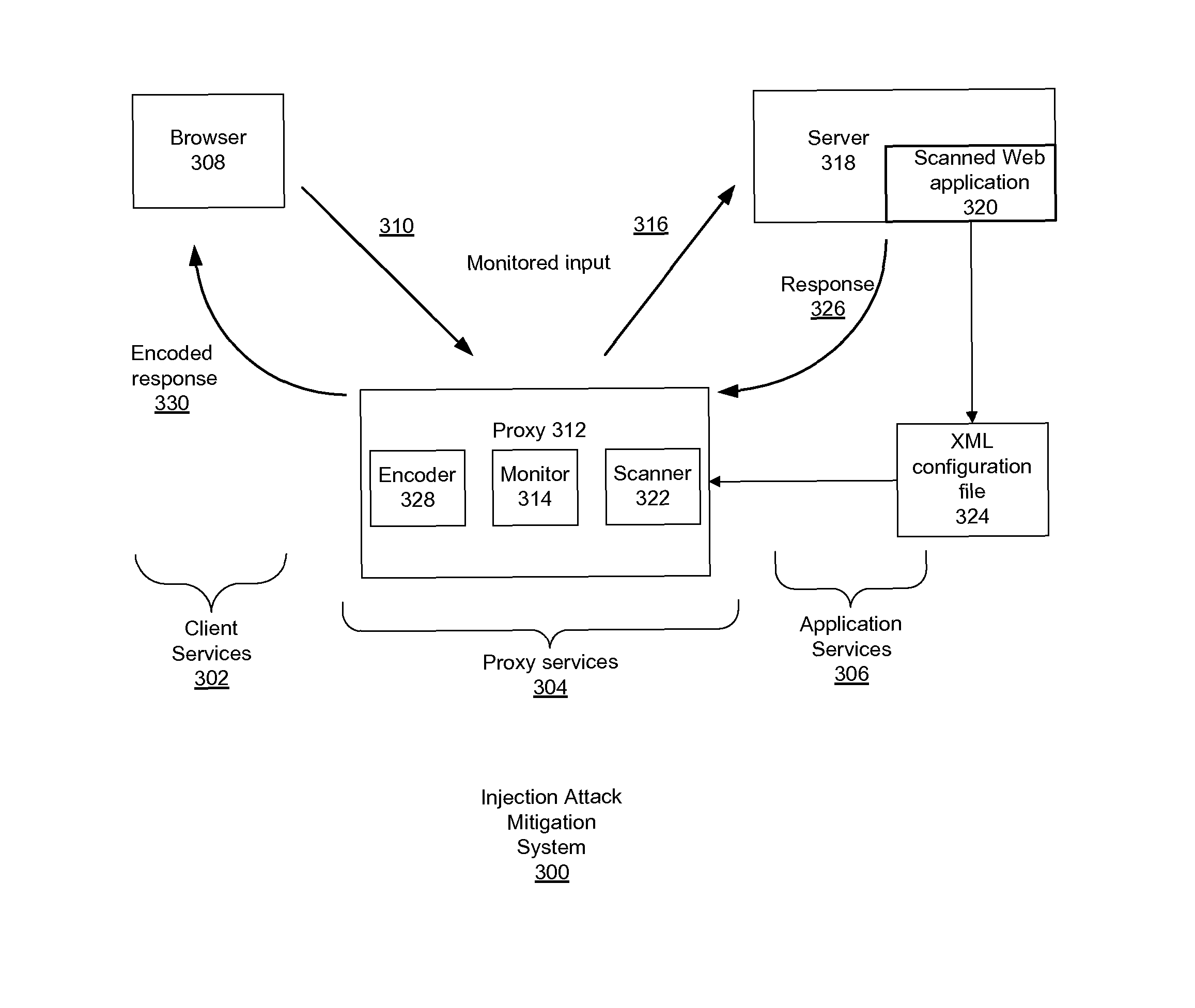
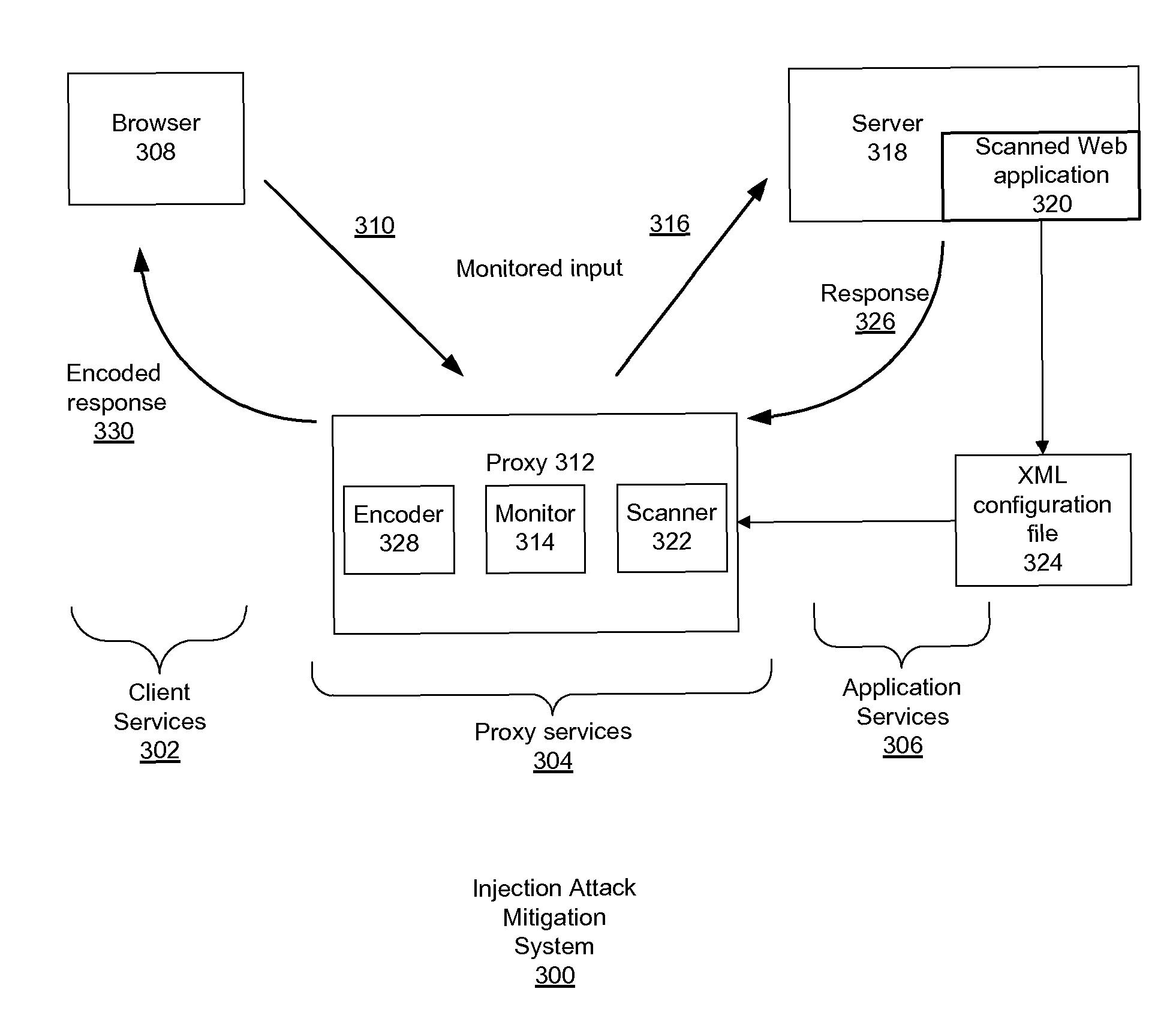
Injection attack mitigation using context sensitive encoding of injected input
ActiveUS20130081135A1Reduce attackPreventing malicious code being embeddedMemory loss protectionError detection/correctionScripting languageWeb application
A method for preventing malicious code being embedded within a scripting language of a web application accessed by a web browser (308), the method comprising: monitoring all incoming traffic (310), generated by the web browser, and outgoing traffic (326) generated by a server (318) to form monitored traffic; determining whether a unique element, defined in a configuration file, is matched with an input value of the monitored traffic to form a matched input value; responsive to a determination that the unique element is matched with an input value of the monitored traffic, saving the matched input value, determining whether an output contains the matched input value in an expected location; responsive to a determination that the output contains the matched input value in an expected location, encoding the matched input value using a respective definition from the configuration file; and returning the output (330) to the requester.
Owner:IBM CORP
Systems and methods for managing global warming
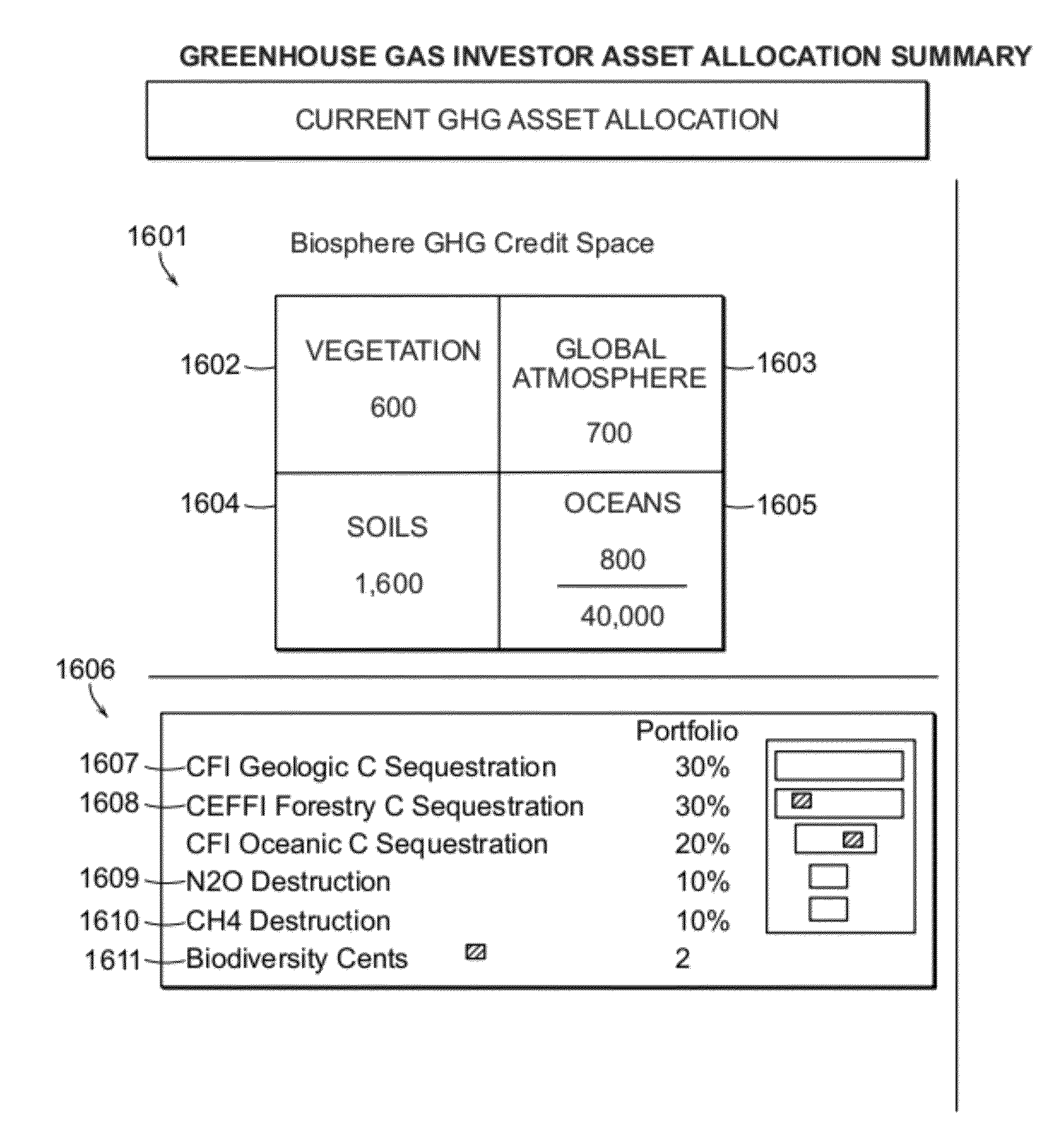
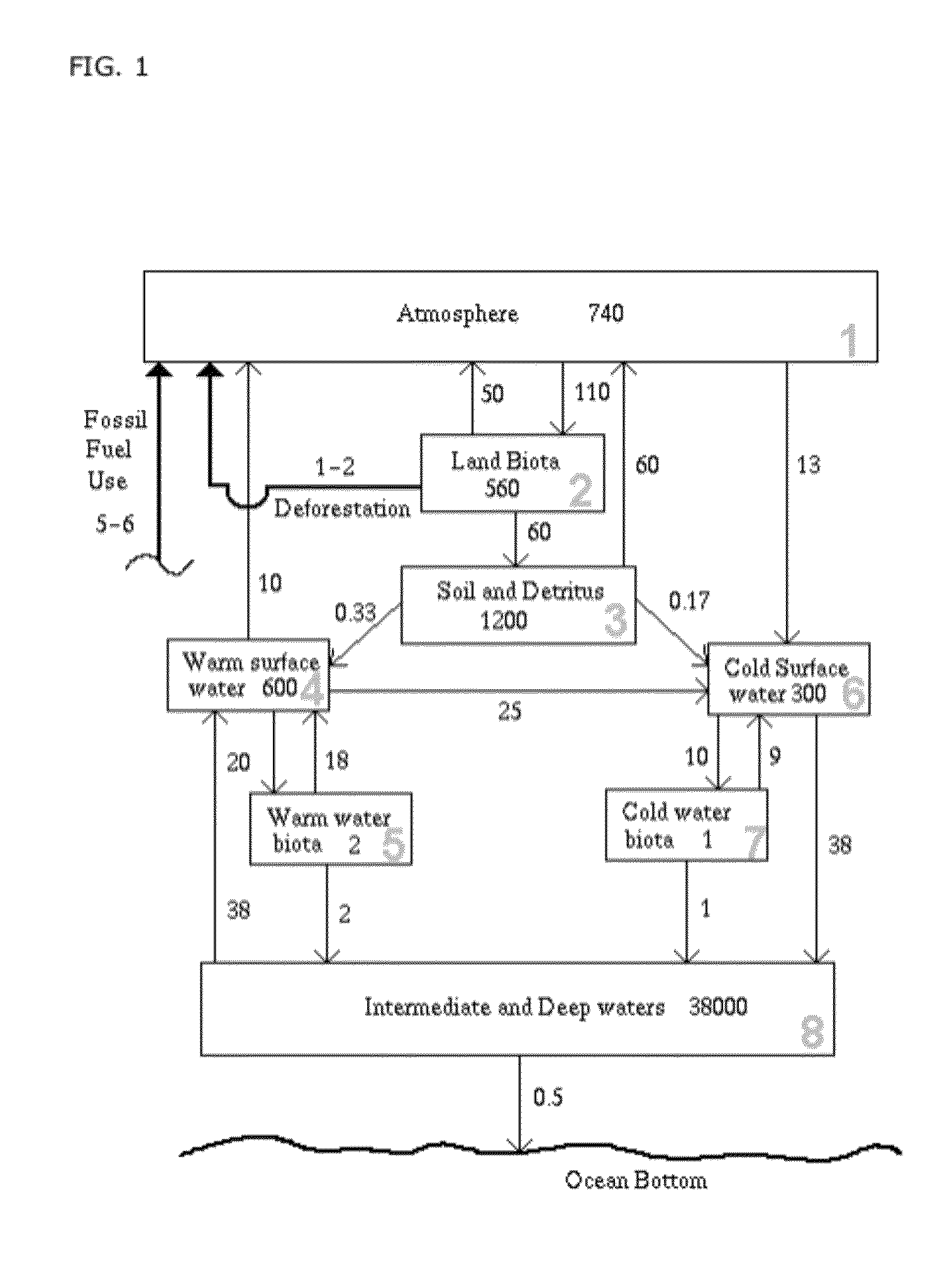
A closed end financial instrument for the monetization of greenhouse gases is disclosed. The closed end security has unique features providing for the securitization of greenhouse gas reductions (e.g., avoidance, sequestration, transformation) on global and sub-global scales. A universal carbon index based on the computed value for metric tons fossil fuel derived CO2 from measurements of the carbon 14 isotope, directly linked to fossil fuel emissions, is also disclosed. The 14C based universal index provides a unique and novel market mechanism to value and track fossil fuel carbon across all reduction genres and measurement platforms. Sub-global indexes for 14C and other GHGs representing partial carbon budgets for specific regions are accounted for within the global budget. The global and sub-global GHG indexes may operate in real time across all GHG currency transactions constituting a live GHG trading regime. An asset allocation system, based on trace gas emissions over small to large scales is also disclosed providing a means to manage and reduce GHG emissions with market-based risk assessment versus return and modern portfolio theory paradigms. Features such as small, mid and large, growth and value are applied to GHG reduction efforts by trace gas type. The unique elements of financial mechanism, global and sub-global carbon indexes and asset allocation options provide a means to manage, reduce and monetize the burden of GHGs to the atmosphere and resultant global warming.
Owner:PLANETARY EMISSIONS MANAGEMENT
Method for coding XBRL (extensible business reporting language) elements
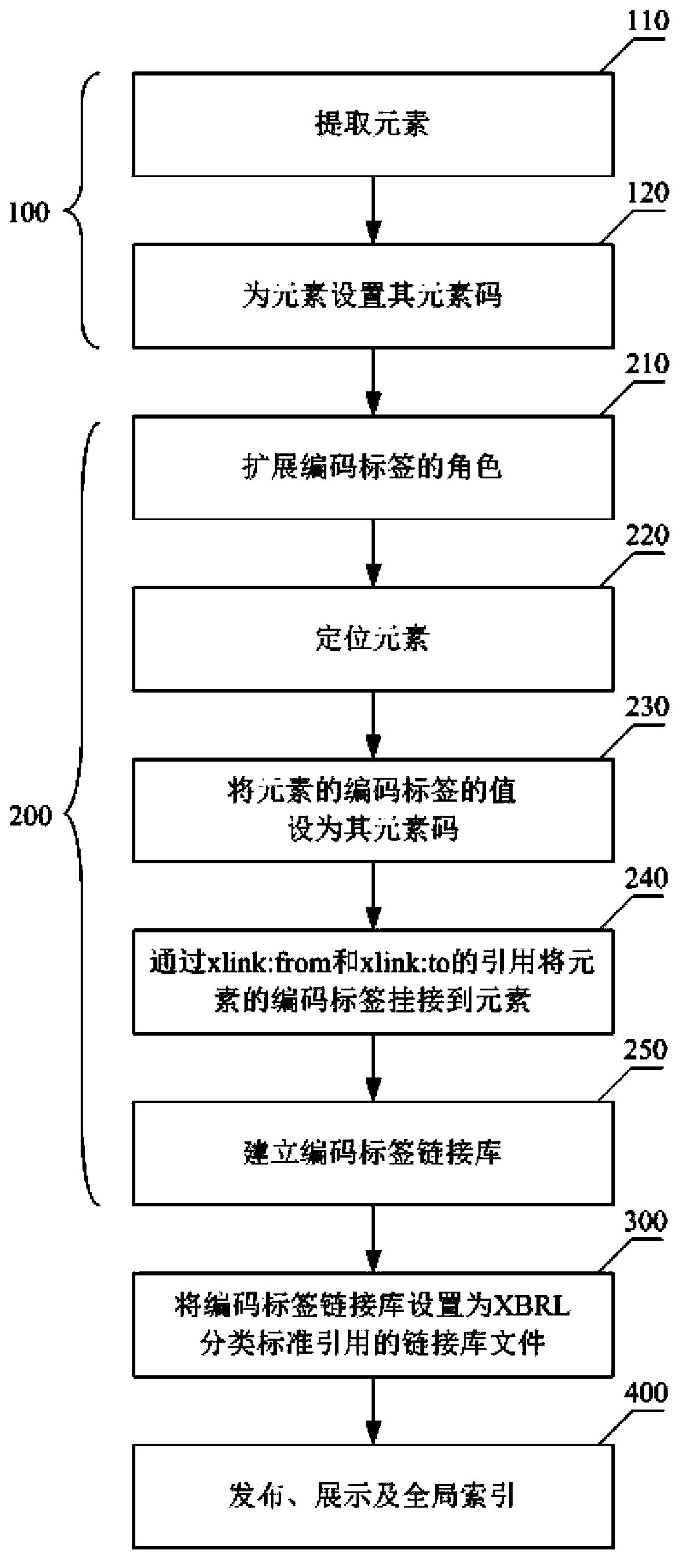
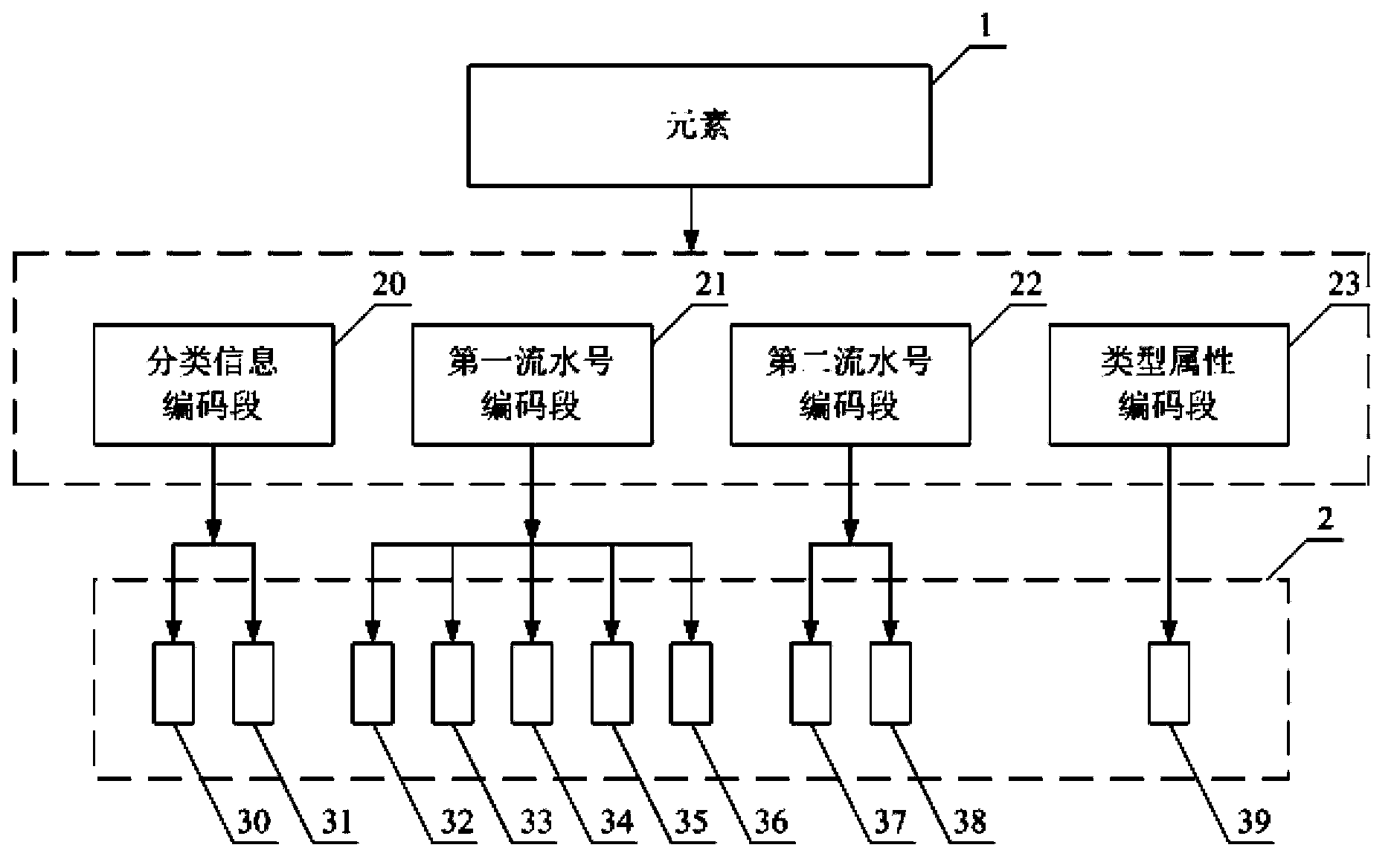
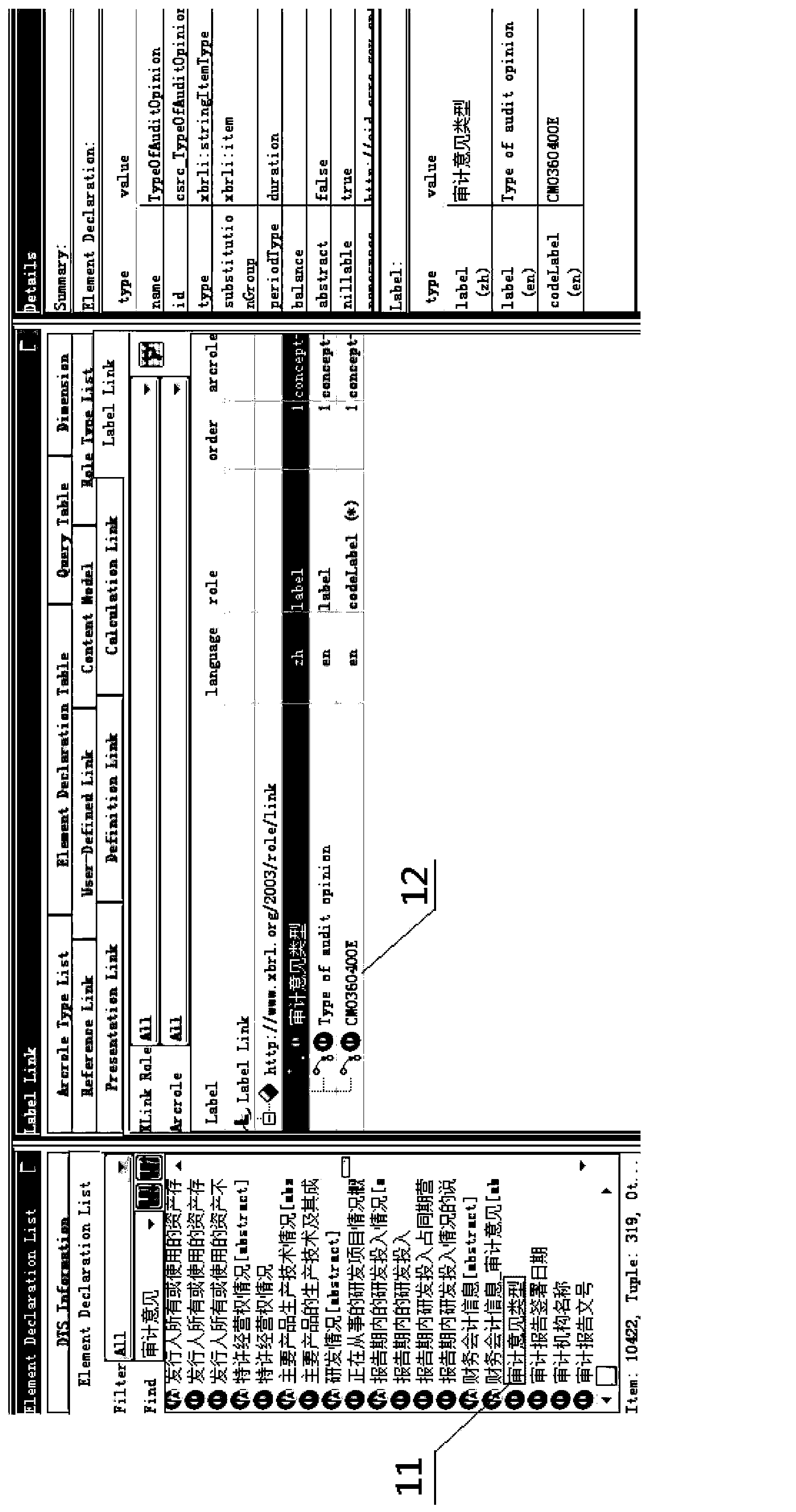
InactiveCN103885765APromote exchangeImprove management efficiencySpecial data processing applicationsSpecific program execution arrangementsTechnical standardManagement efficiency
The invention discloses a method for coding XBRL (extensible business reporting language) elements. The method includes setting element codes for the elements; creating coding label link libraries; setting the coding label link libraries as link library files which can be cited by XBRL taxonomy schema files. The coding label link libraries contain coding labels of the various elements, and values of the coding labels are the element codes of the elements. The method has the advantages that the unique element codes which contain taxonomy information, serial numbers and technological type information are provided for the various elements in XBRL taxonomy and are published and demonstrated along with the elements, so that information disclosure persons and information disclosure organizations can manage the elements by the aid of computers in a unified manner, and data exchange can be facilitated; global indexes are created, so that the element service and management efficiency can be improved, and social resources can be saved; users can acquire additional information from the element codes so as to easily understand and identify the elements.
Owner:INFORMATION CENT OF CHINA SECURITIES REGULATORY COMMISSION +1
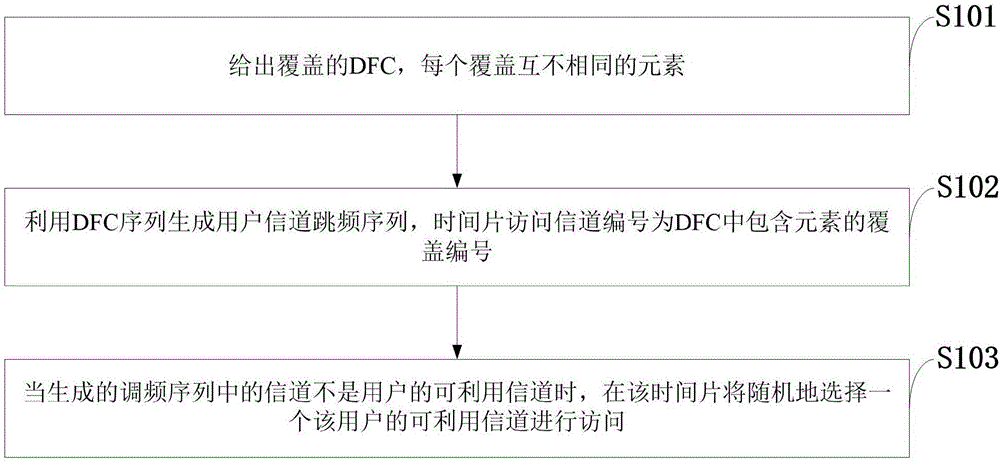
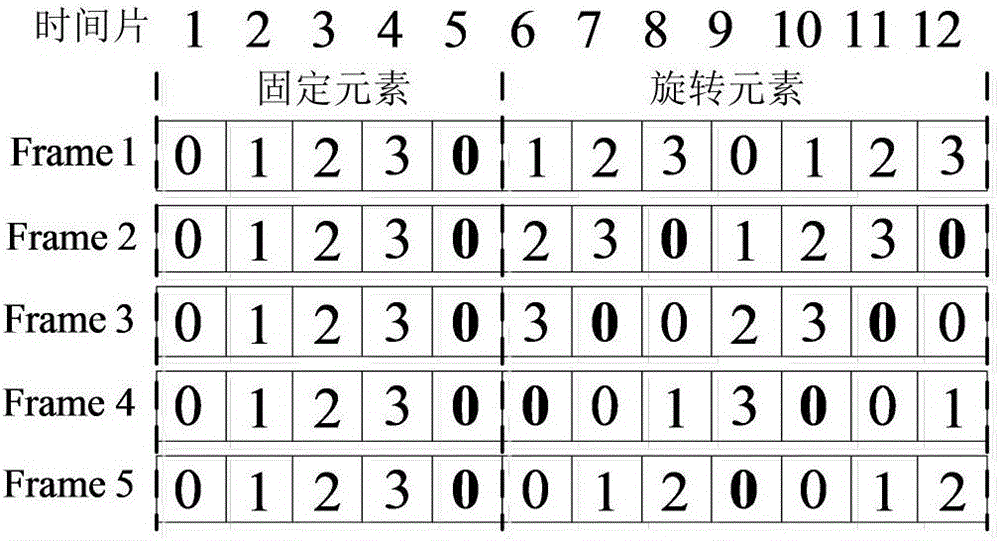
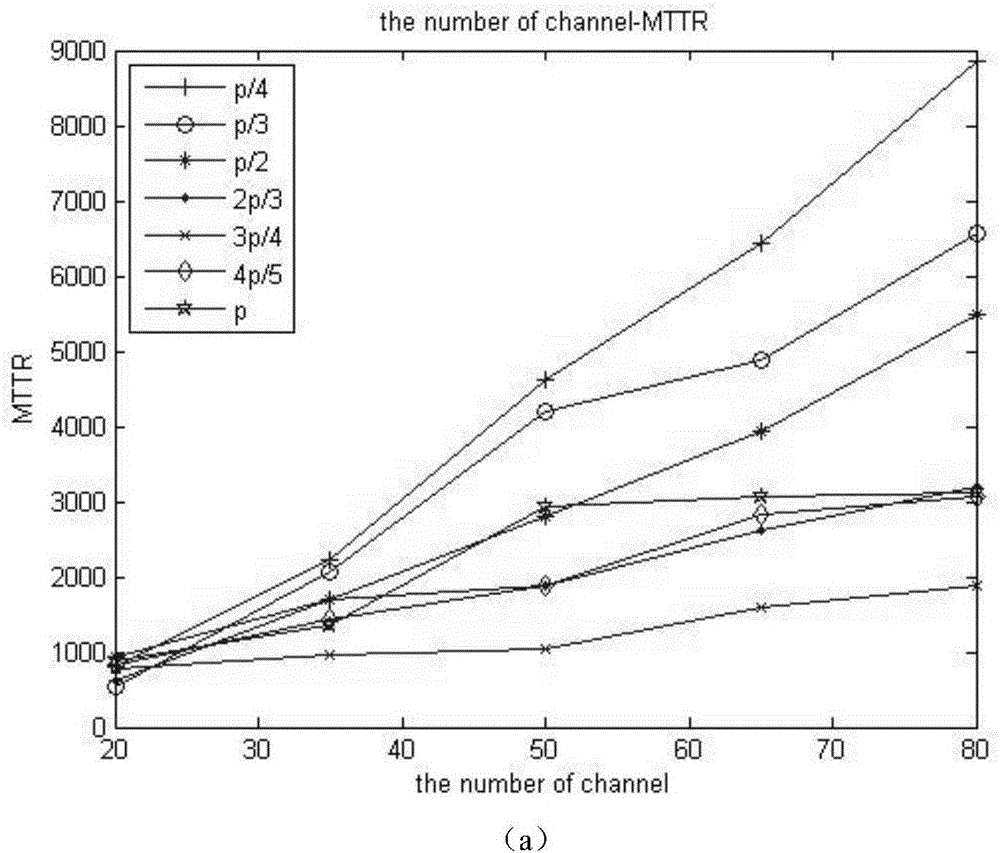
Adjustable channel intersection method based on finite cover in cognitive wireless network
ActiveCN106604321AAdapt to diverse needsImprove performanceNetwork traffic/resource managementTransmission monitoringAlgorithmAnonymity
The invention discloses an adjustable channel intersection method based on finite cover in a cognitive wireless network (CRN). An adjustable non-crossing finite cover channel intersection algorithm for time asynchronization, model heterogeneity, role symmetry and user information anonymity is acquired by use of non-crossing finite cover. A relationship is established between the channel intersection process of the CRN and non-crossing finite cover, wherein each cover in DFC represents one channel, each element in the cover represents a time slice in a CH frequency-modulated sequence, and the unique element in each cover represents the channel represented by the cover searched in the time slice represented by the element. The generated DFC is a function LOCK of network scale. The diverse requirements of the network can be satisfied by changing the size of LOCK. Simulation results show that ADFC-CH has better performance than other algorithms (SSB, L-DDP and DSCR).
Owner:XIDIAN UNIV
Apparatus and method for a court ball game
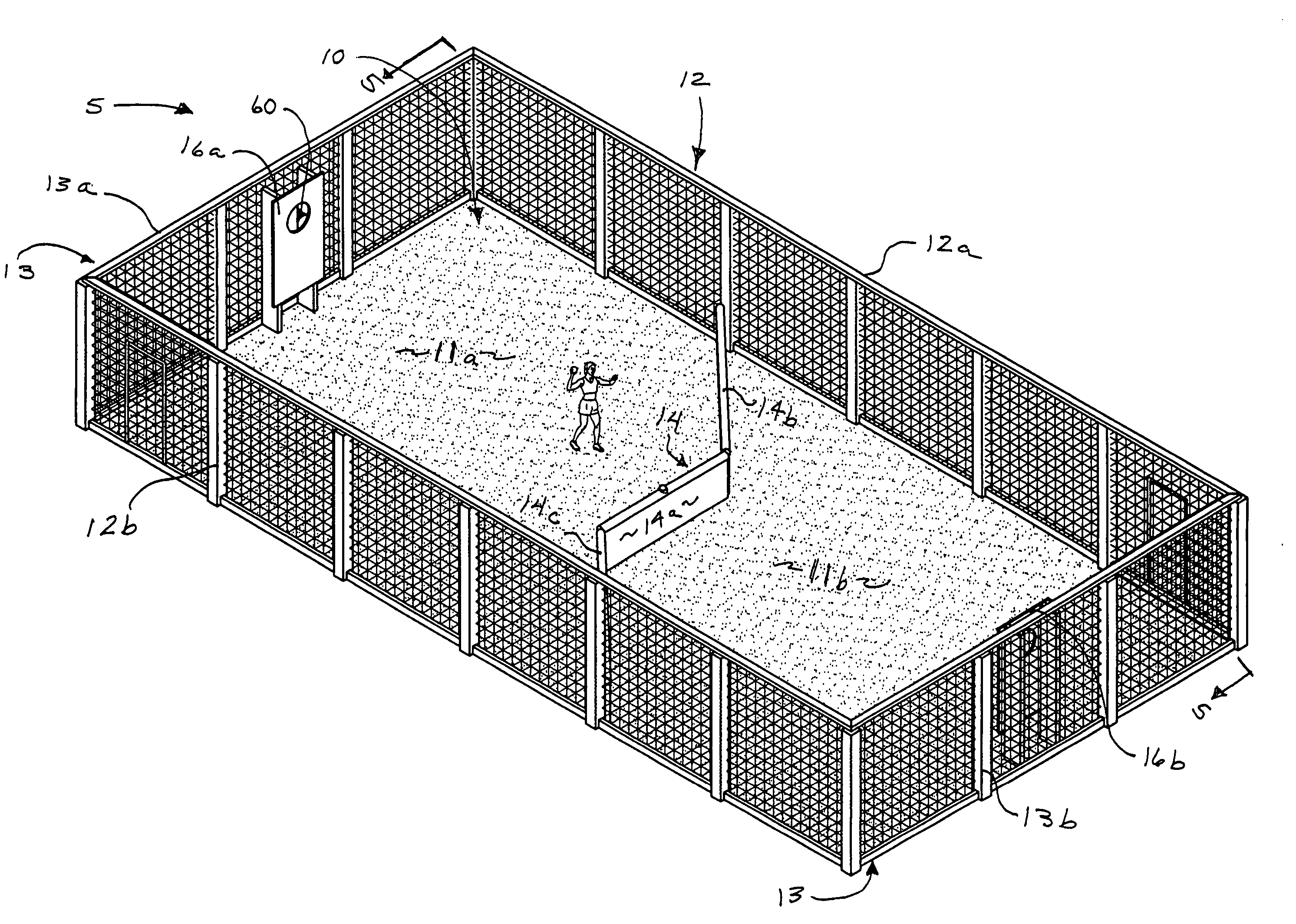
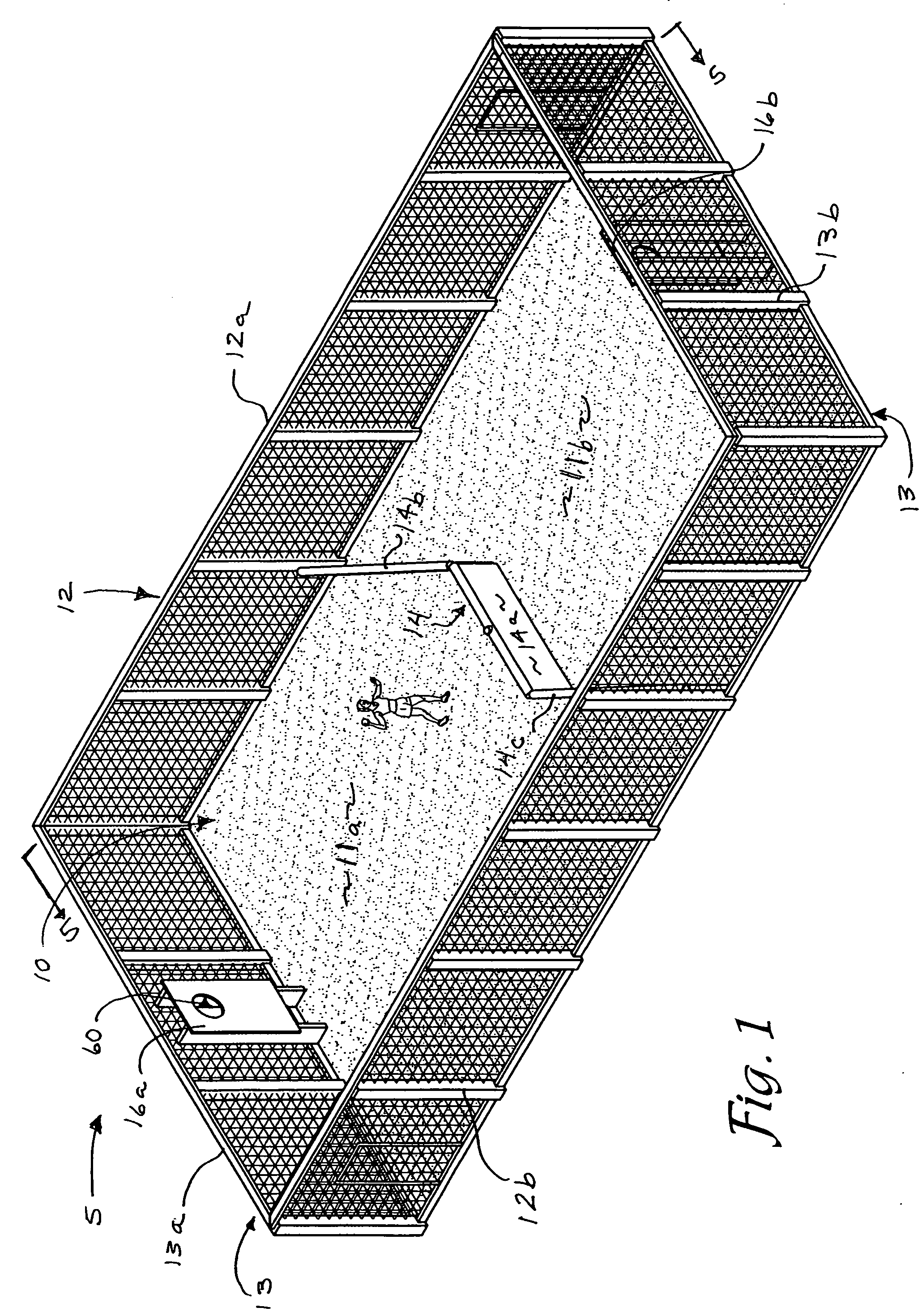
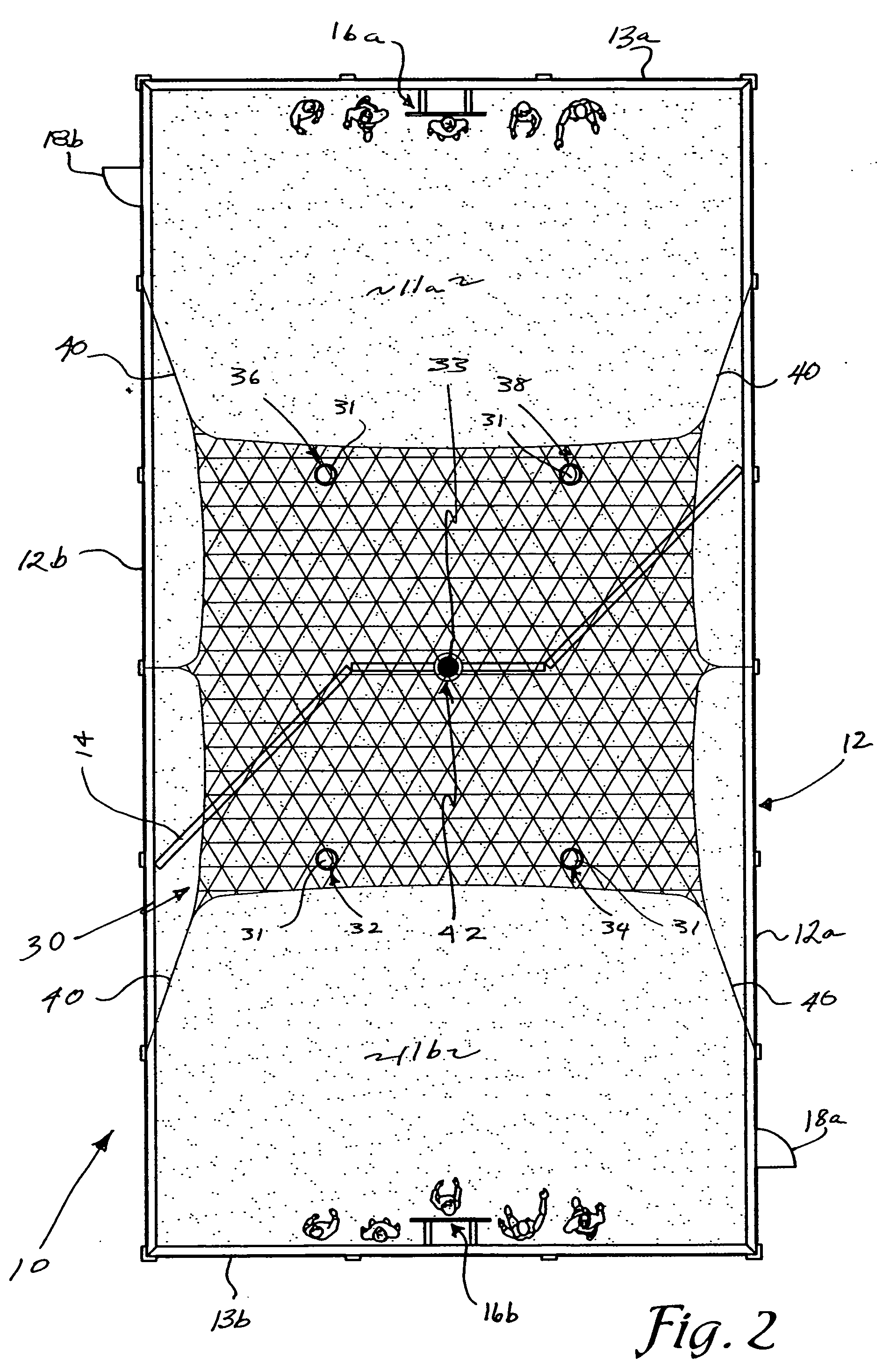
InactiveUS20070213146A1Alters possibilityEnhance strategic advantageBall sportsWater-skiingEngineeringBall game
A game court and method of play are provided which allow players to compete and score points by throwing a ball through their opponent's goal or throwing the ball and hitting their opponent. The game provides a court bound on all sides to facilitate retention of balls during game play and features an opaque dividing fence which splits the court into two halves each occupied by a different team. The fence is oriented such that each team has on its side of the fence an area of the court protruding past the midpoint of the court. The configuration and orientation of the dividing fence creates unique elements of strategy including the possibility that players from one team may attempt to score points from a position behind players of the opposing team.
Owner:RAGEBALL 5 LLC
Injection attack mitigation using context sensitive encoding of injected input
ActiveUS9009821B2Preventing malicious code being embeddedMemory loss protectionError detection/correctionScripting languageWeb application
A method for preventing malicious code being embedded within a scripting language of a web application accessed by a web browser (308), the method comprising: monitoring all incoming traffic (310), generated by the web browser, and outgoing traffic (326) generated by a server (318) to form monitored traffic; determining whether a unique element, defined in a configuration file, is matched with an input value of the monitored traffic to form a matched input value; responsive to a determination that the unique element is matched with an input value of the monitored traffic, saving the matched input value, determining whether an output contains the matched input value in an expected location; responsive to a determination that the output contains the matched input value in an expected location, encoding the matched input value using a respective definition from the configuration file; and returning the output (330) to the requester.
Owner:IBM CORP
Surface covering with an irregular undulating edge
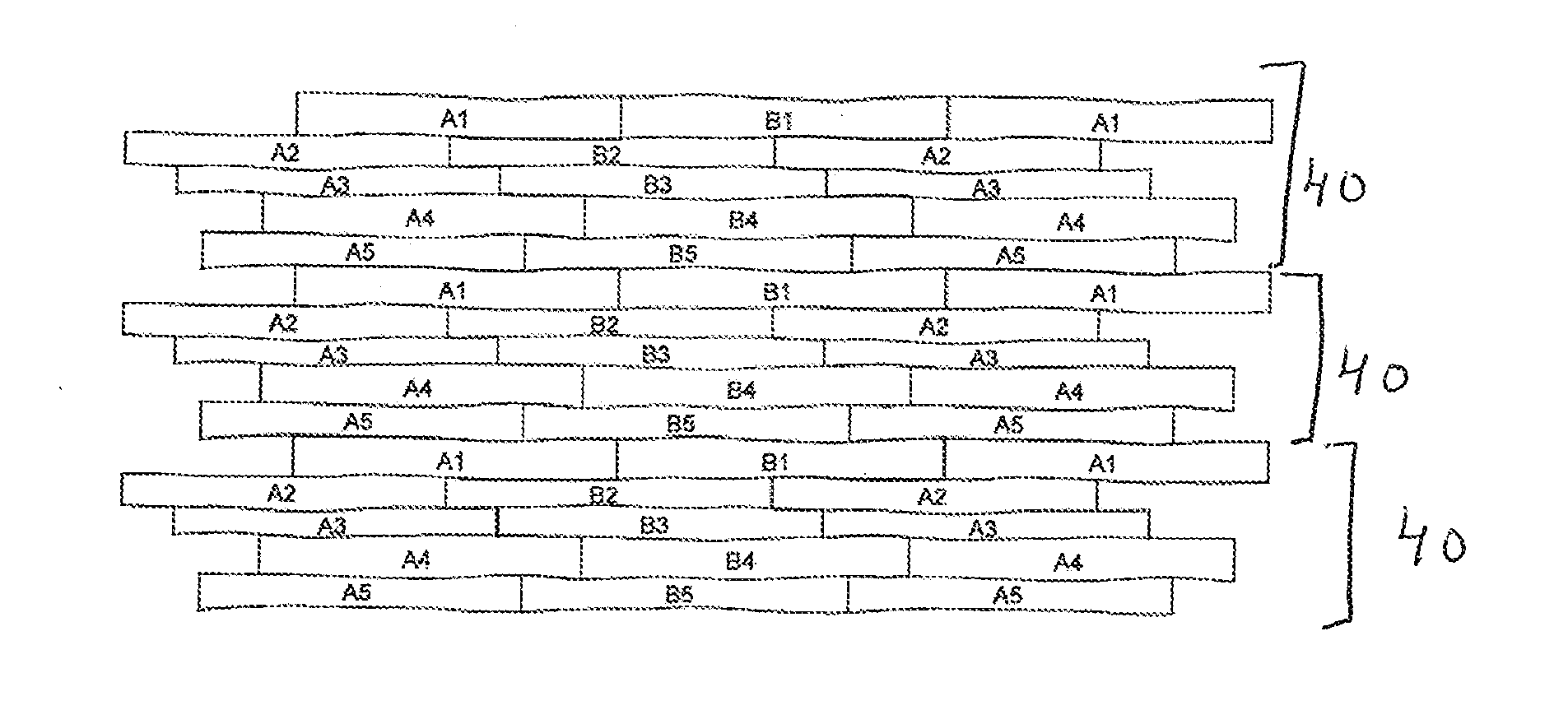
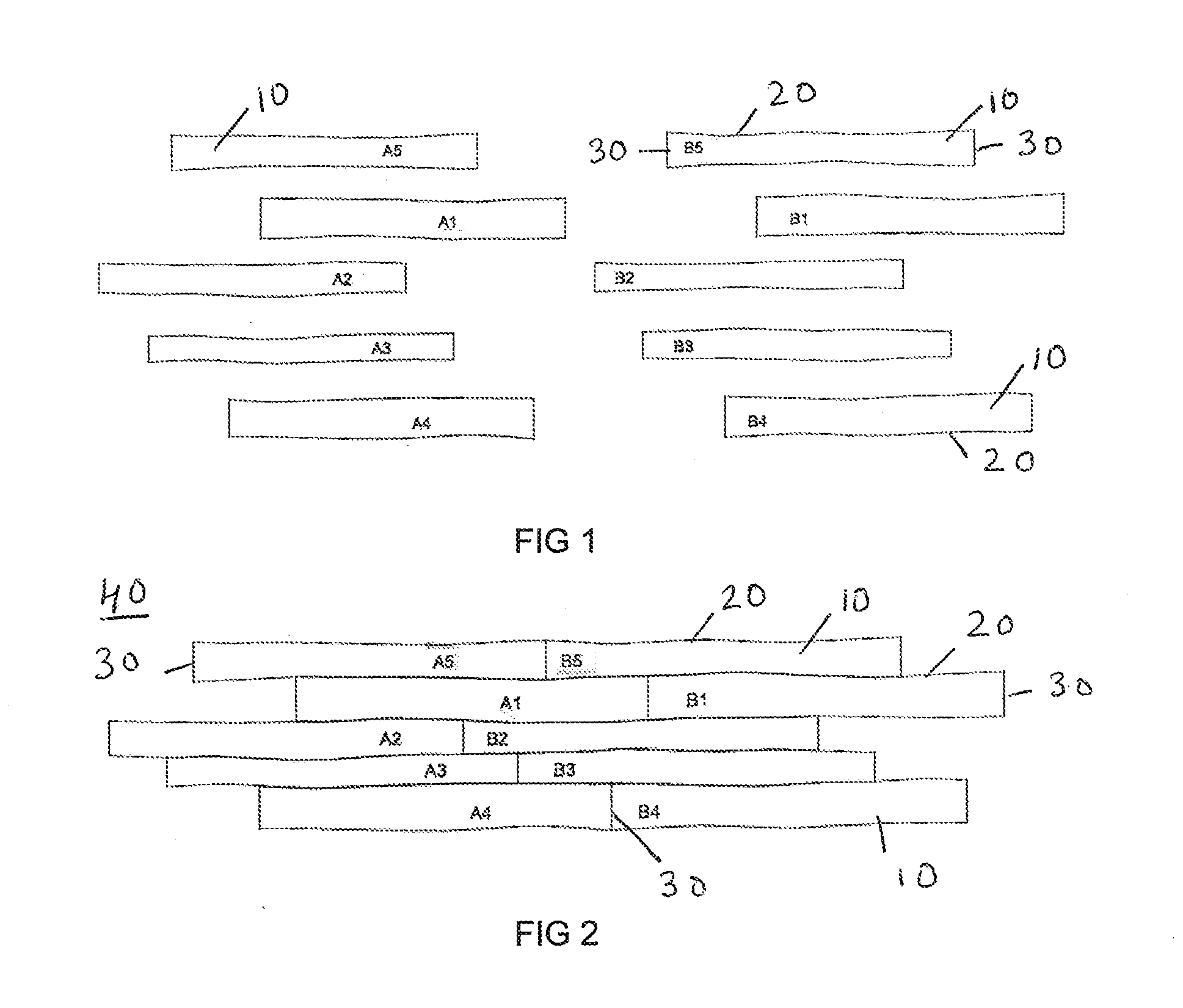
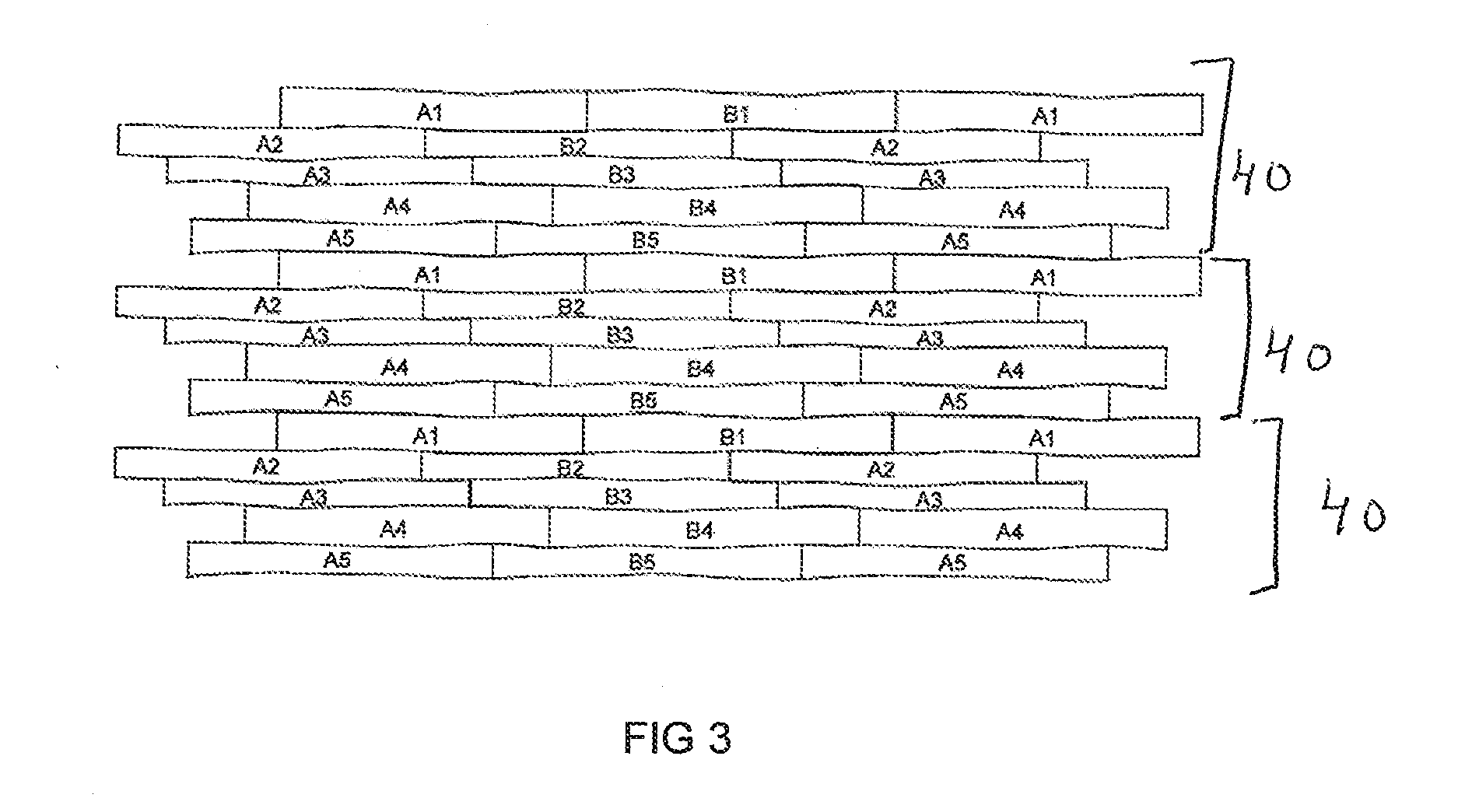
InactiveUS20140363591A1Economic and easyDead plant preservationNatural patternsEngineeringSurface cover
The invention describes a surface covering that comprises modules, made up of elements with irregular undulating edge, imitating natural warping of wood. At least one element with irregular undulating edge of a module is unique and an element with at least one irregular undulating edge can be matched, according to the predefined specification, side to side, with at least one adjacent element with irregular undulating edge. Unique element of each module, featuring at least one irregular undulating edge, will be interchangeable with the unique element with an equivalent irregular undulating edge that forms a part of another module. Modules can be matched mutually, at horizontal plane, to the shape of irregular undulating edge of the outmost element of module, at least in part, according to the predefined specification, given above; the modules can be also matched to each other at ends, according to the predefined specification, thus forming a repeating pattern.
Owner:LCF HLDG OU
Methods and systems for latency-free contacts search
ActiveUS8898186B2Digital data information retrievalDigital data processing detailsDistributed memoryData set
Systems and methods for performing latency-free contact searches using two-level indexed data structures having decreasing integer sets as identifiers to represent actual contact data. The indexed data structures are stored in distributed memory. Data operations such as intersection and union are performed using the indexed data structures. A binary interval reduction technique is used to quickly move through the data sets looking for common elements for the intersection set, or unique elements to add to the union set.
Owner:SALESFORCE COM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com