Device and method for carrying out a cryptographic method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
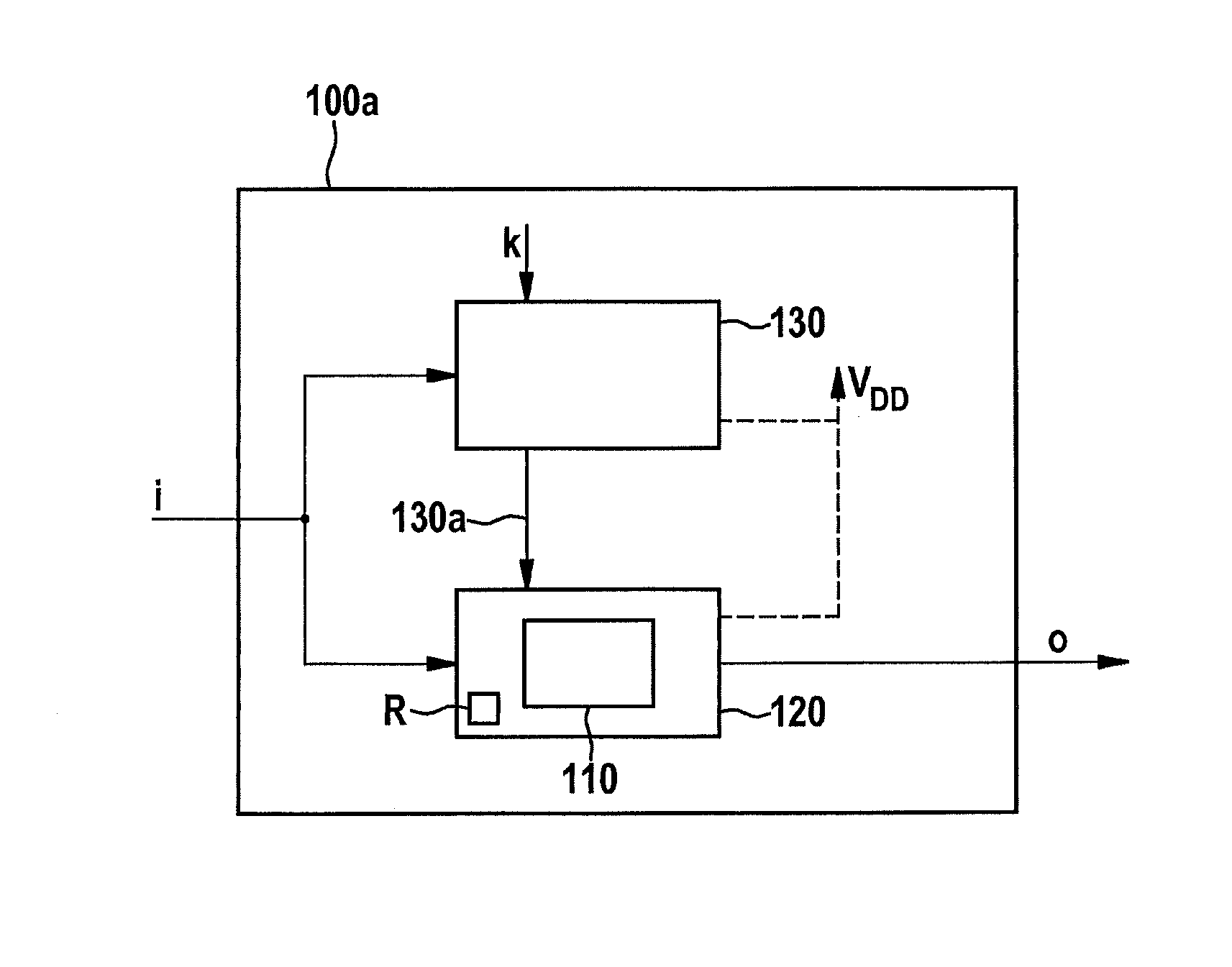
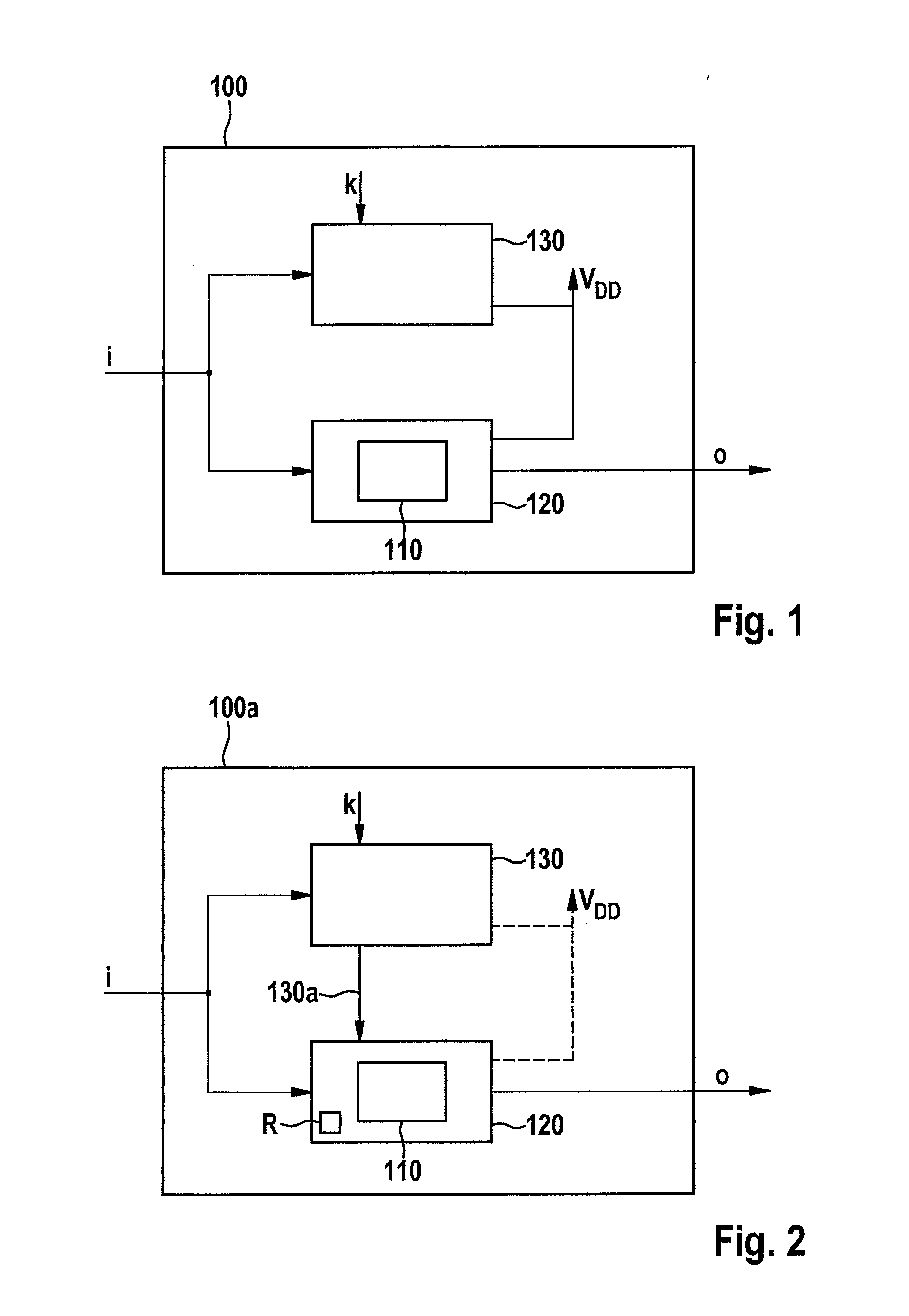
[0035]FIG. 1 schematically shows a block diagram of a first specific embodiment of device 100 according to the present invention. Device 100 has a cryptographic unit 120 that is fashioned to carry out a cryptographic method 110, or at least one step of a cryptographic method 110. An encryption according to the AES (Advanced Encryption Standard) may be taken as an example of a cryptographic method.
[0036]Device 100 is supplied with input data i that can be for example a bit sequence that is to be encrypted by cryptographic unit 120. Correspondingly, encrypted output data o are obtained at an output of cryptographic unit 120.
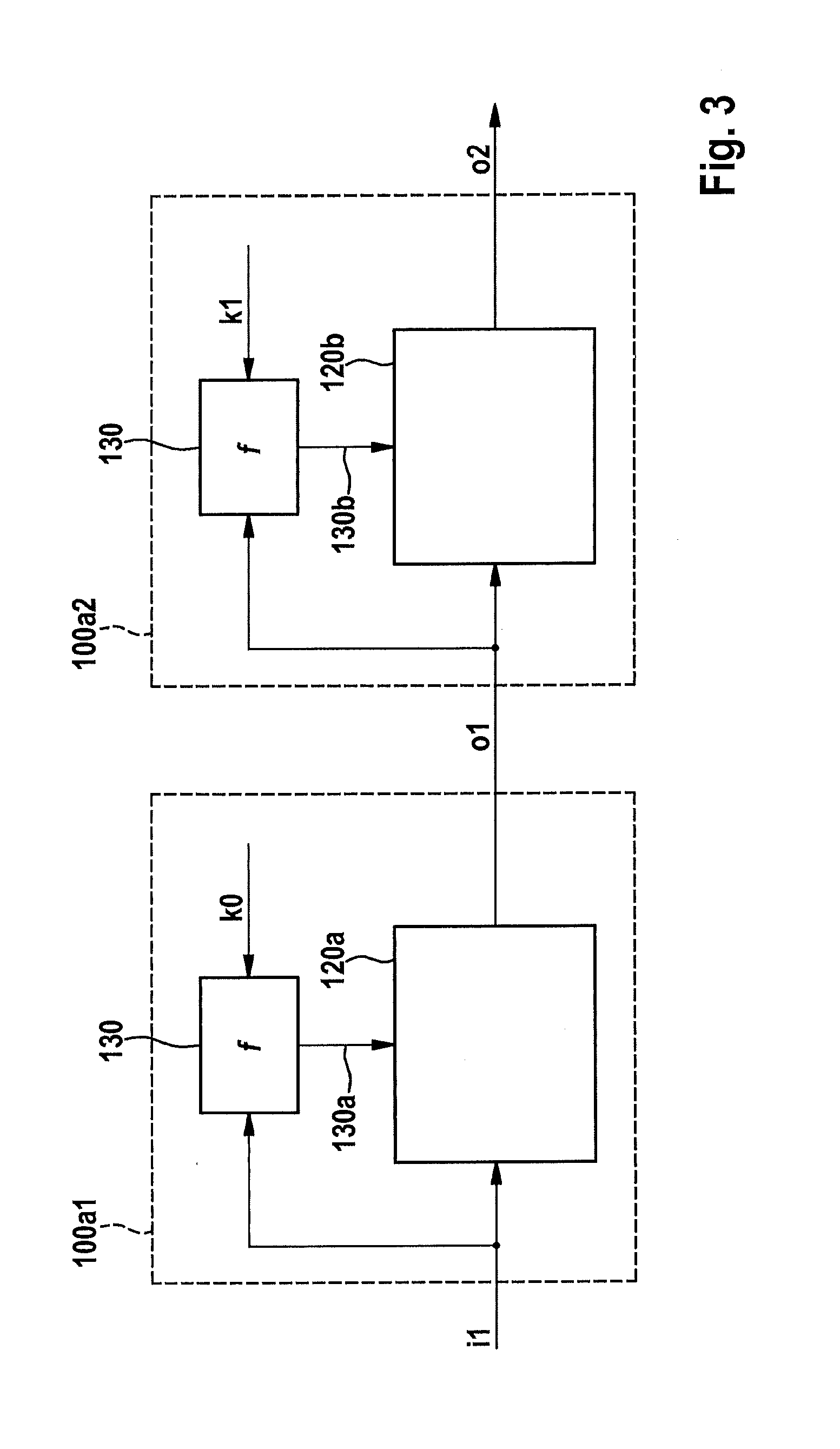
[0037]According to the present invention, device 100 has, in addition to cryptographic unit 120, a functional unit 130 that is fashioned to carry out a deterministic function as a function of the input data and of at least one secret key k.
[0038]The operation of functional unit 130 in parallel, at least at times, to the operation of cryptographic unit 120 makes dif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com