System for and methods of administration of access control to numerous resources and objects
a technology of access control and system, applied in the field of computer system access control, can solve the problems of cumbersome access control and privilege management, affecting the efficiency of information management, and not allowing for massively scalable or sufficiently granular levels of information management, so as to manage the complexity of a large number of resources, facilitate the complexity of a system, and efficiently create, modify and delete groups
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
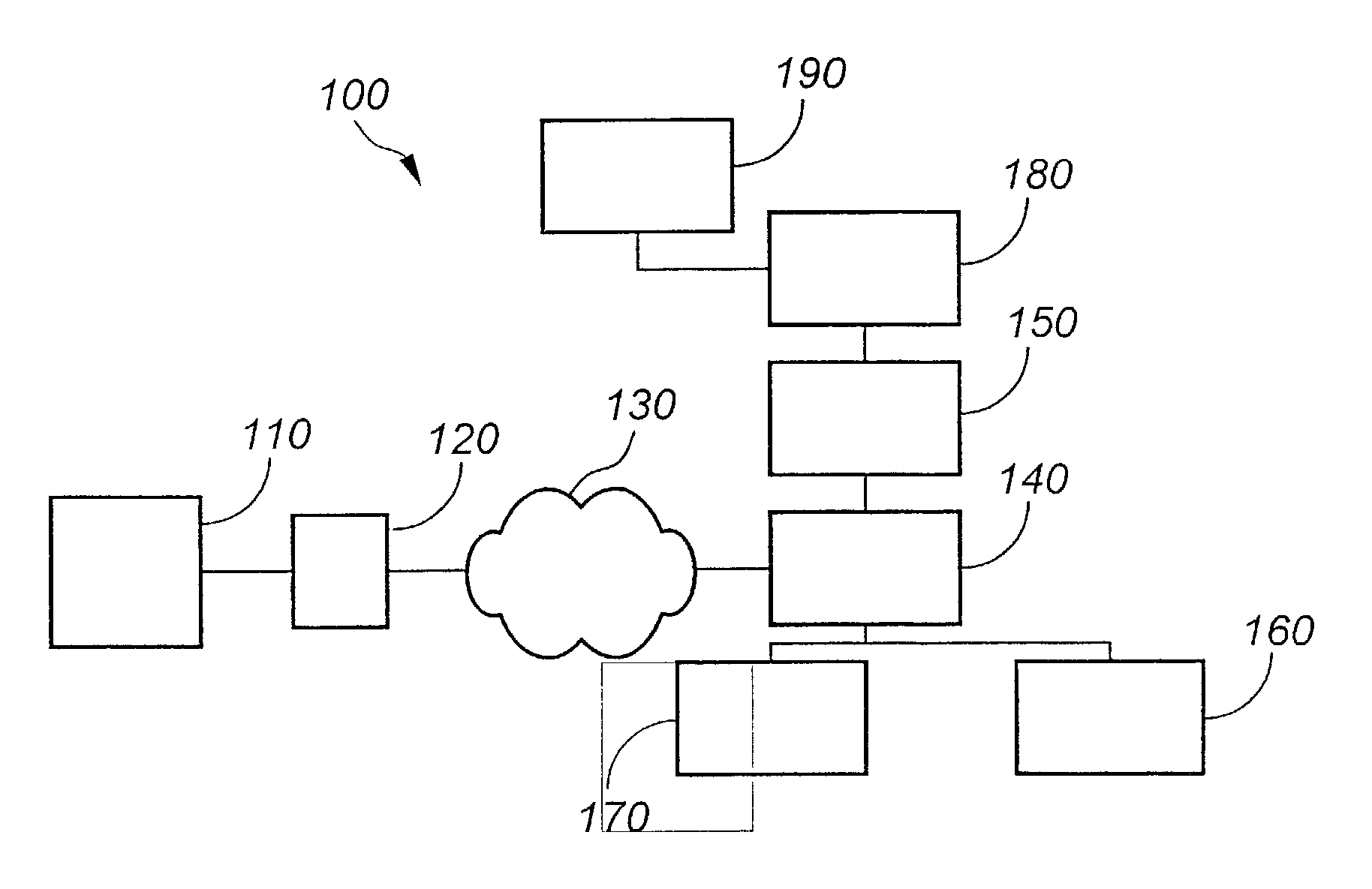
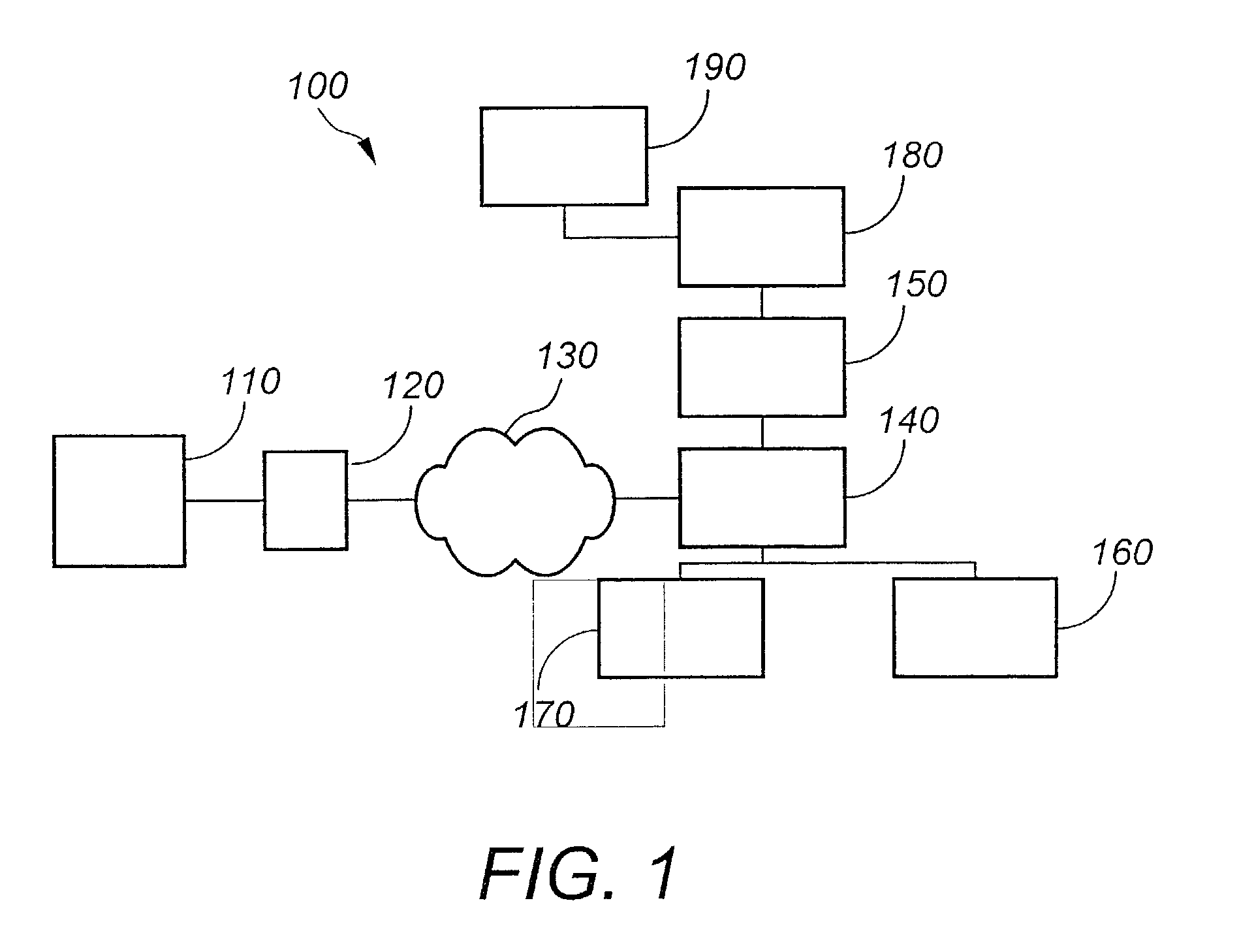
[0040]The present invention provides a system for and associated methods of administration of access control to numerous resources and objects. The present invention operates from an “object-centric” view, in contrast with that of the conventional “user-centric” system of access control administration. The system described optimally employs the “Entitlement engine” referred to and incorporated by reference above as an authorization mechanism, however, the present invention may be used by any access management system and also incorporate a wide array of database administration protocols, such as Lightweight Directory Access Protocol (LDAP).
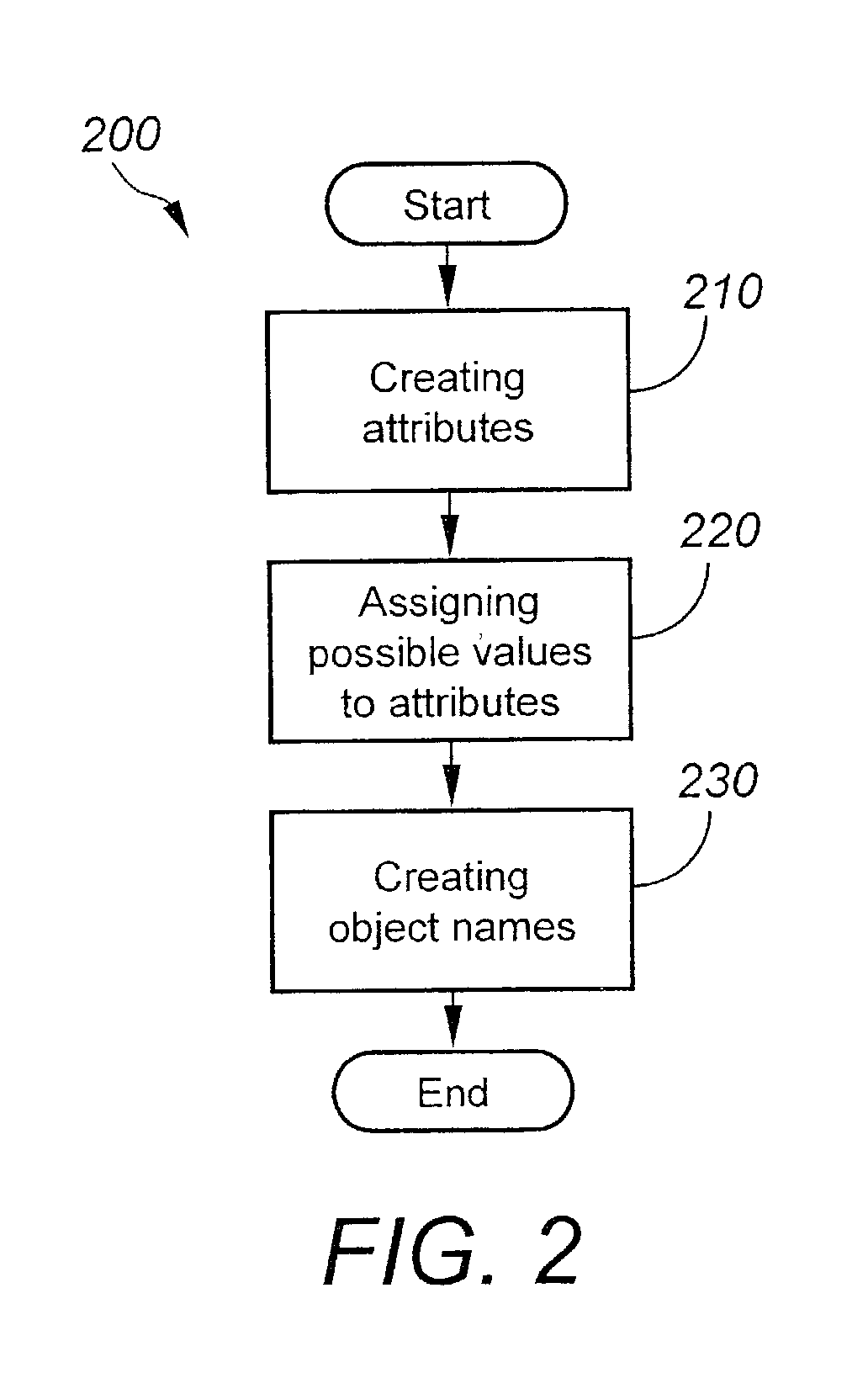
[0041]In certain embodiments, the system includes a special parameter called {super} that is useful in establishing access privilege inheritances. Through the use of {super} and DefaultAccessPrivileges, it is shown that an administrator can control access to resources and objects with great specificity or detail in some parts of the system and more...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com