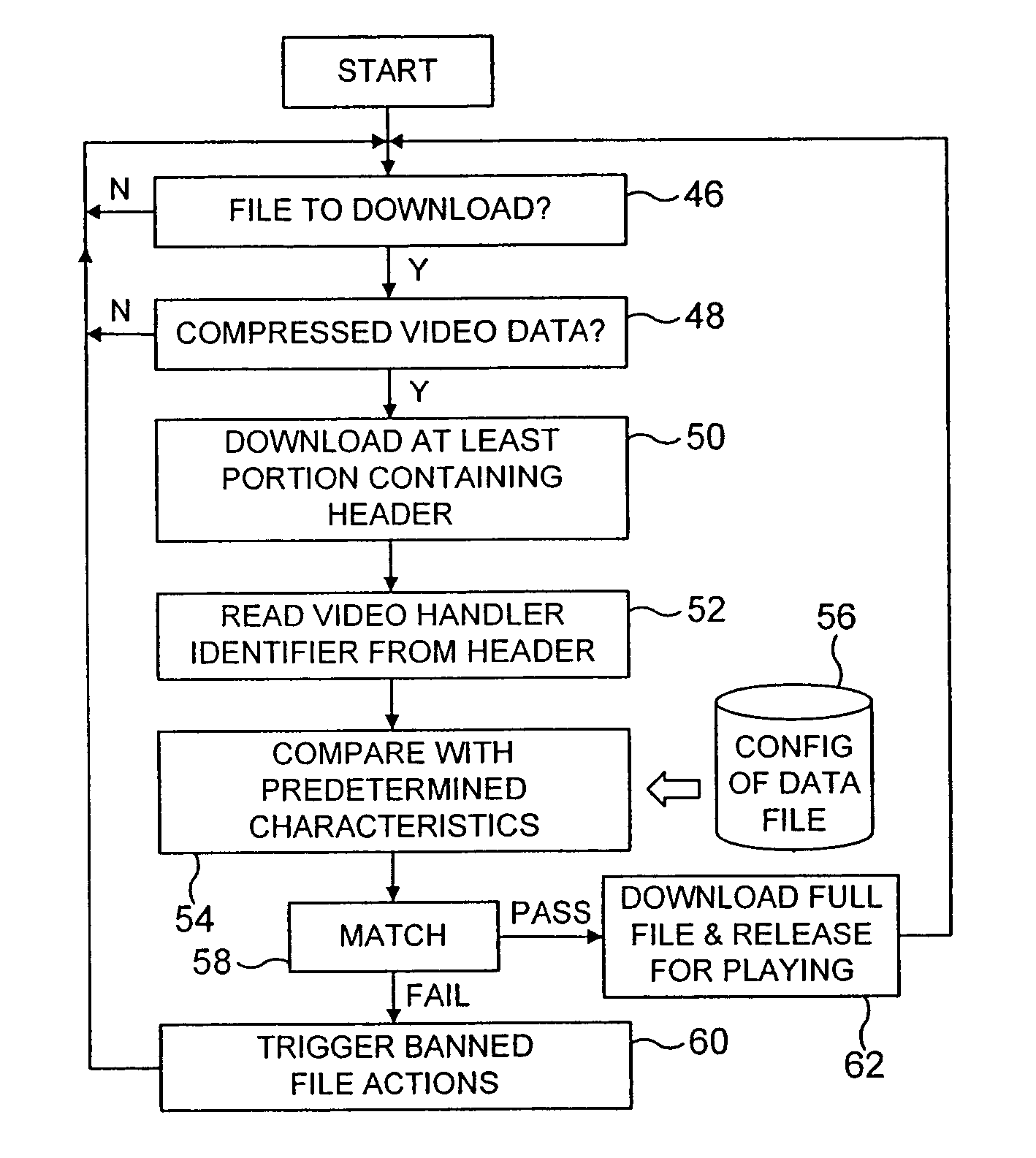
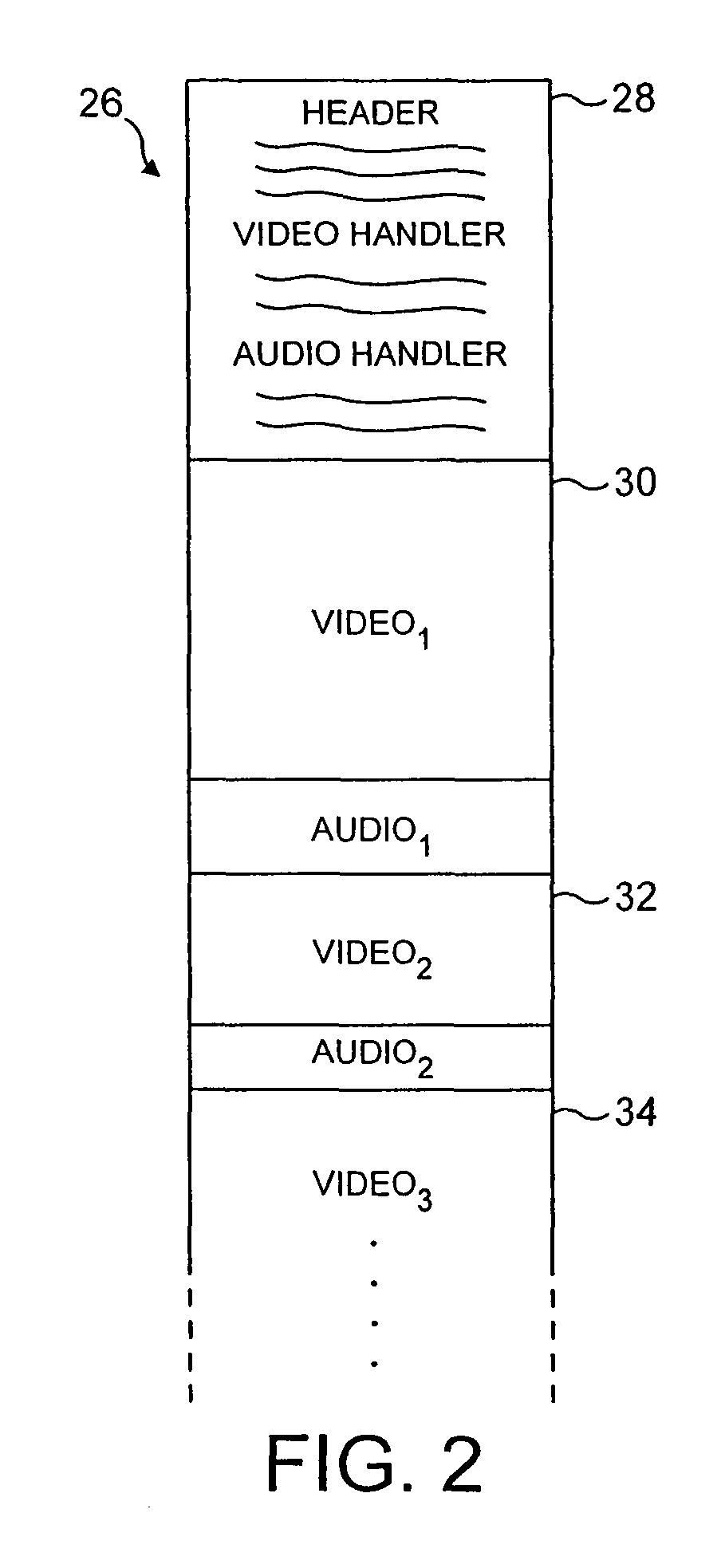
Detecting computer data containing compressed video data as banned computer data
a technology of computer data and compressed video, applied in the field of data processing systems, can solve the problems of copyright infringing or otherwise unauthorised, unauthorised and/or copyright infringing video data being distributed via the internet and other mechanisms, and achieve the effect of increasing false alarms and a higher degree of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
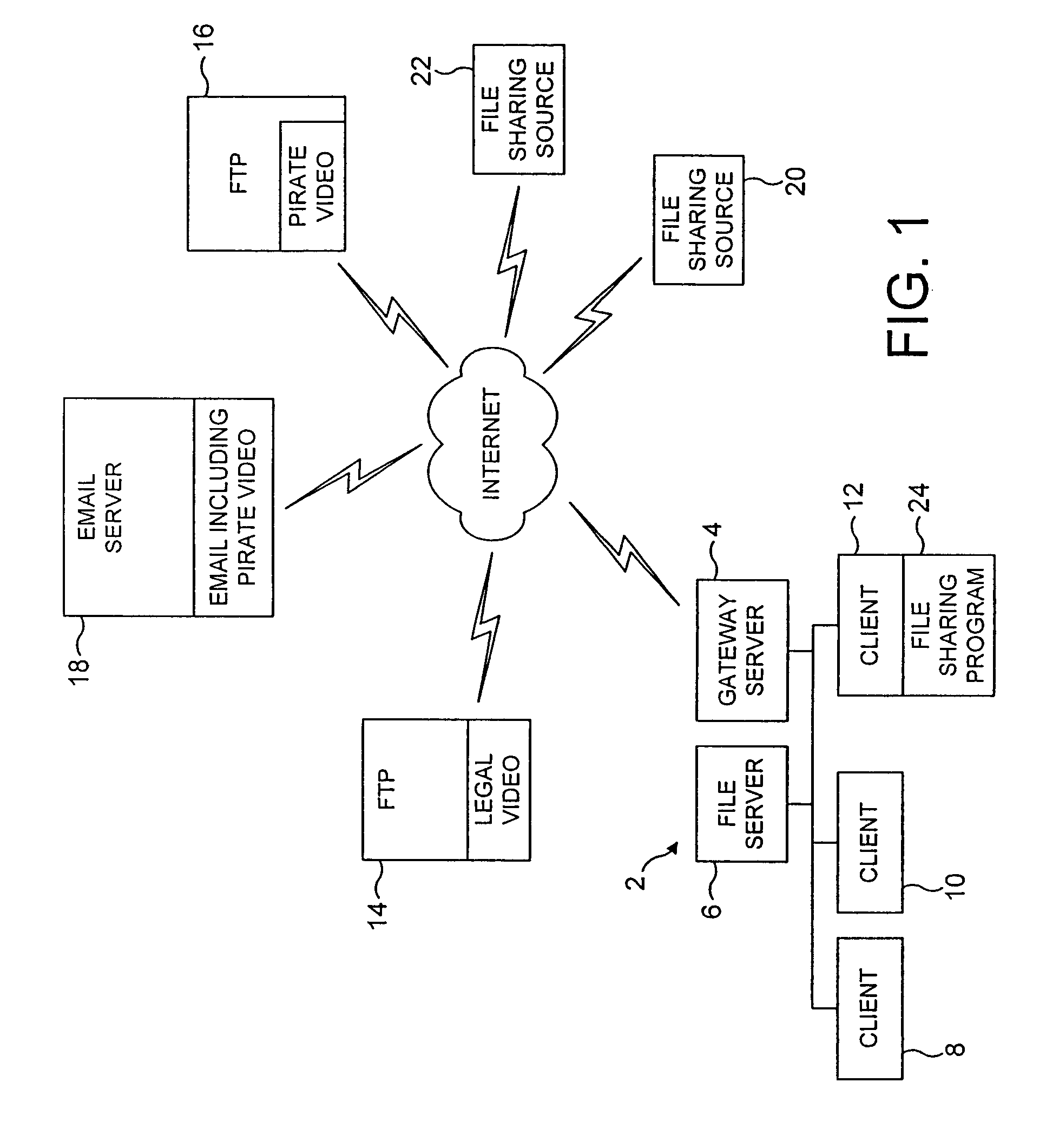
[0037]FIG. 1 illustrates a computer network 2, such as a corporate computer network, comprising a gateway server 4, a file server 6 and a plurality of client computers 8, 10, 12. The network 2 is connected via the Internet to provide a plurality of sources of data. Some of these sources of data may be sources of legitimate data, such as an FTP server 14 containing a legal copy of a video file that can be downloaded and used by appropriately authorised persons connected by the Internet. Conversely, another FTP server 16 may store a copy which is a pirate, copyright-infringing version of the video concerned and which it is desired to prevent from being manipulated within the network 2. An email server 18 may serve as a source for the banned material, such as email messages containing the banned material as an email attachment. There are also known number of file sharing schemes whereby banned computer files, such as pirate, copyright-infringing versions of computer files are stored on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com