Method for performing a transaction over a network
a network and transaction technology, applied in the field of network transaction methods, can solve the problems of inconvenient and expensive implementation of solutions, and the connection between the use of these cards and a certain risk of fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0007]The objective of the described invention is to eliminate the before mentioned risk of fraud, and to develop a simple, easy and cheap solution to the security problem of identification and verification used for international interchange transactions over an electronic communication channel. The verification could be implemented as a part of a payment transaction, e.g. between the customer, a bank and a shop.
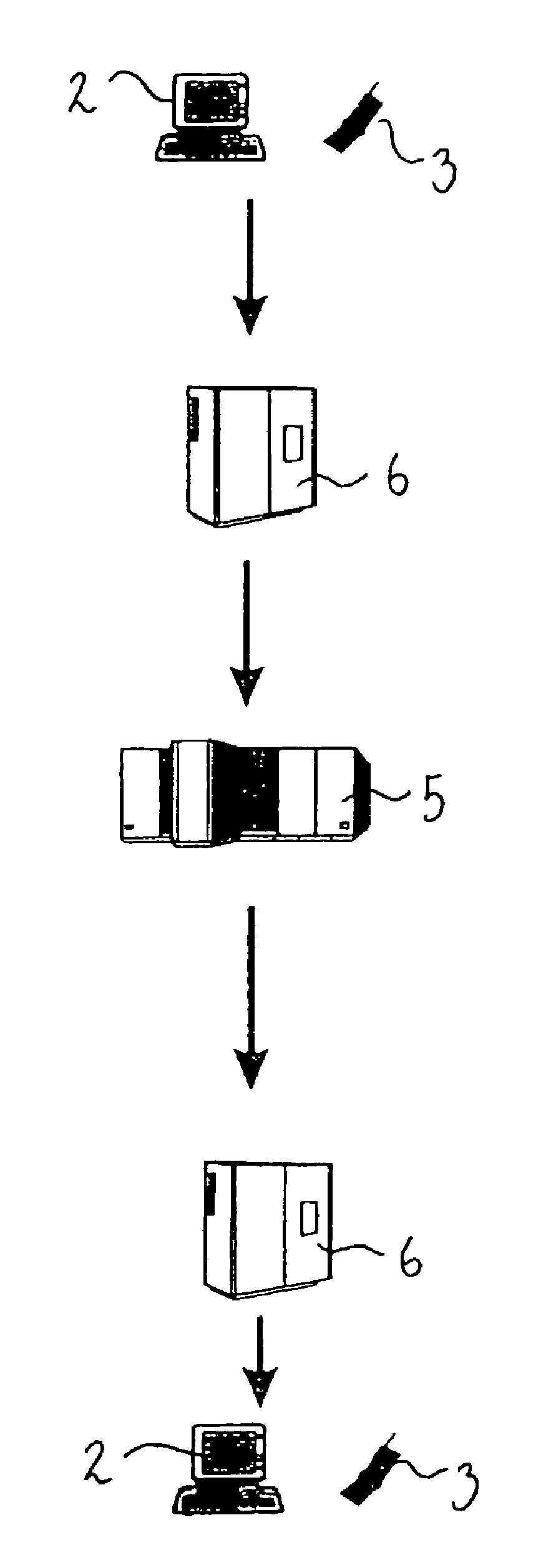
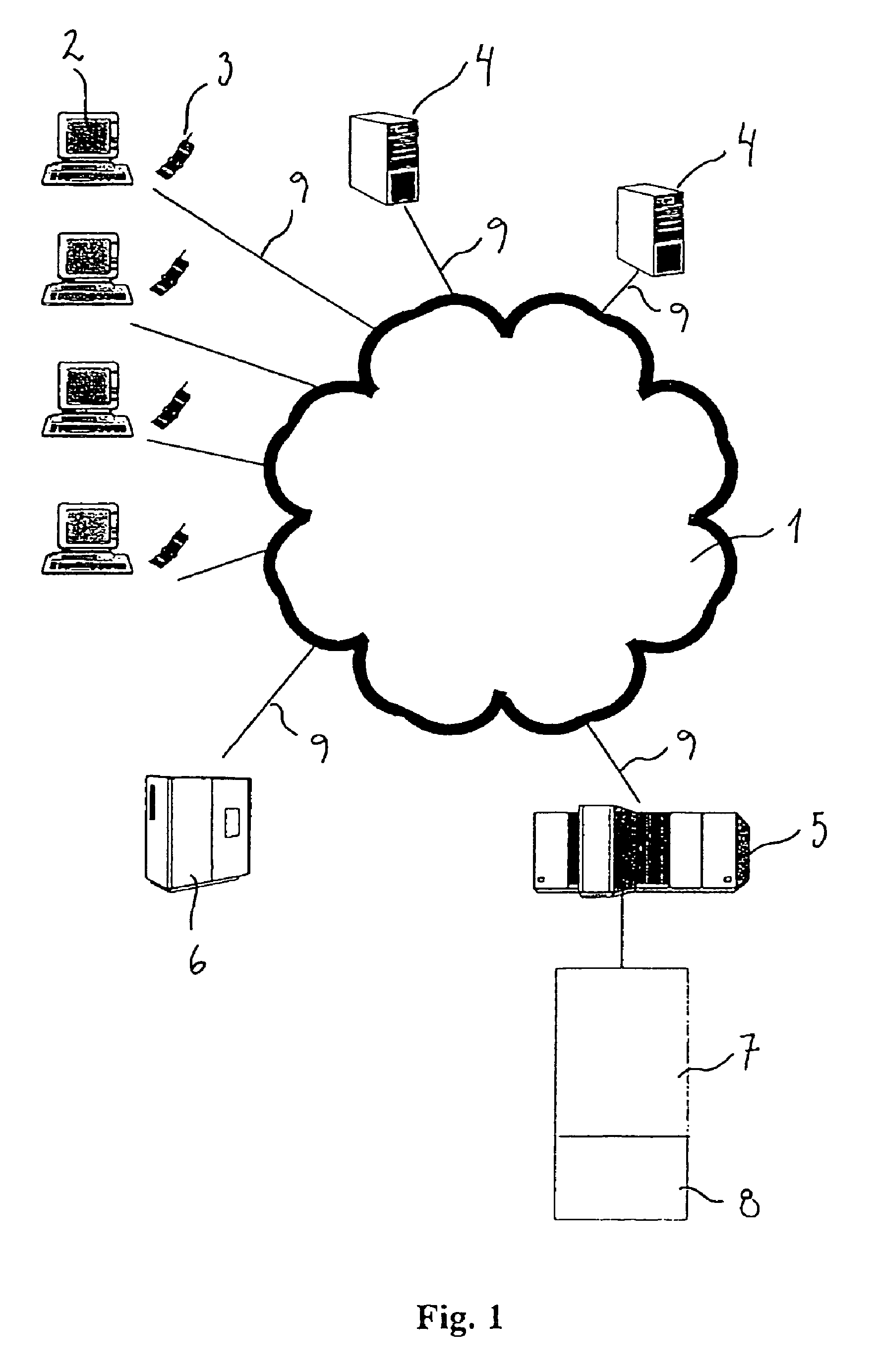
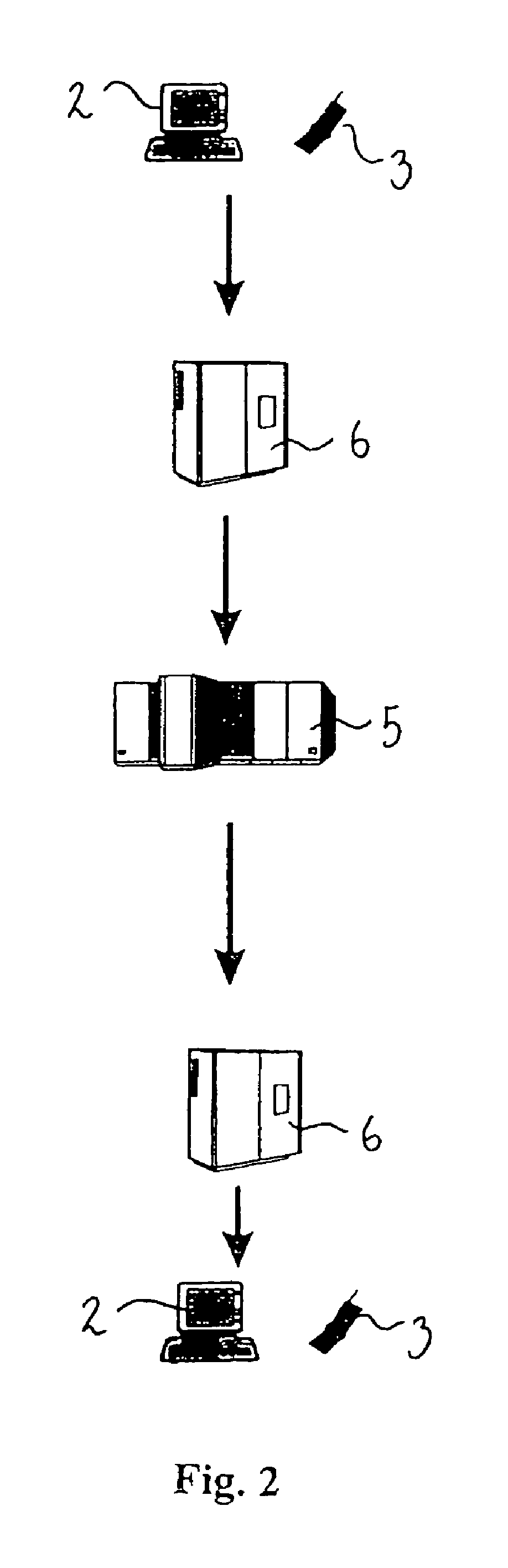
[0008]Accordingly the present invention relates to a method for performing a transaction between a legal entity A who has an approval to perform such a transaction, and a legal entity B over a network, the transaction being initiated by the legal entity A,
wherein
the legal entity A, to verify the approval to the legal entity B, associates the transaction with a verification insignia,
the verification insignia being a unique transitory insignia provided to the legal entity A by a legal entity C who thereby guarantees that the legal entity A has the approval,
[0009]the provision ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com