Method for realizing information encryption transmission in wireless communication system
A wireless communication system and information encryption technology, which is applied in the field of information encryption transmission in wireless communication systems, can solve the problems of difficulty in prohibiting illegal access, no solution, hidden dangers, etc., and achieves low processing capacity requirements and small changes. , the effect of confidentiality performance guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
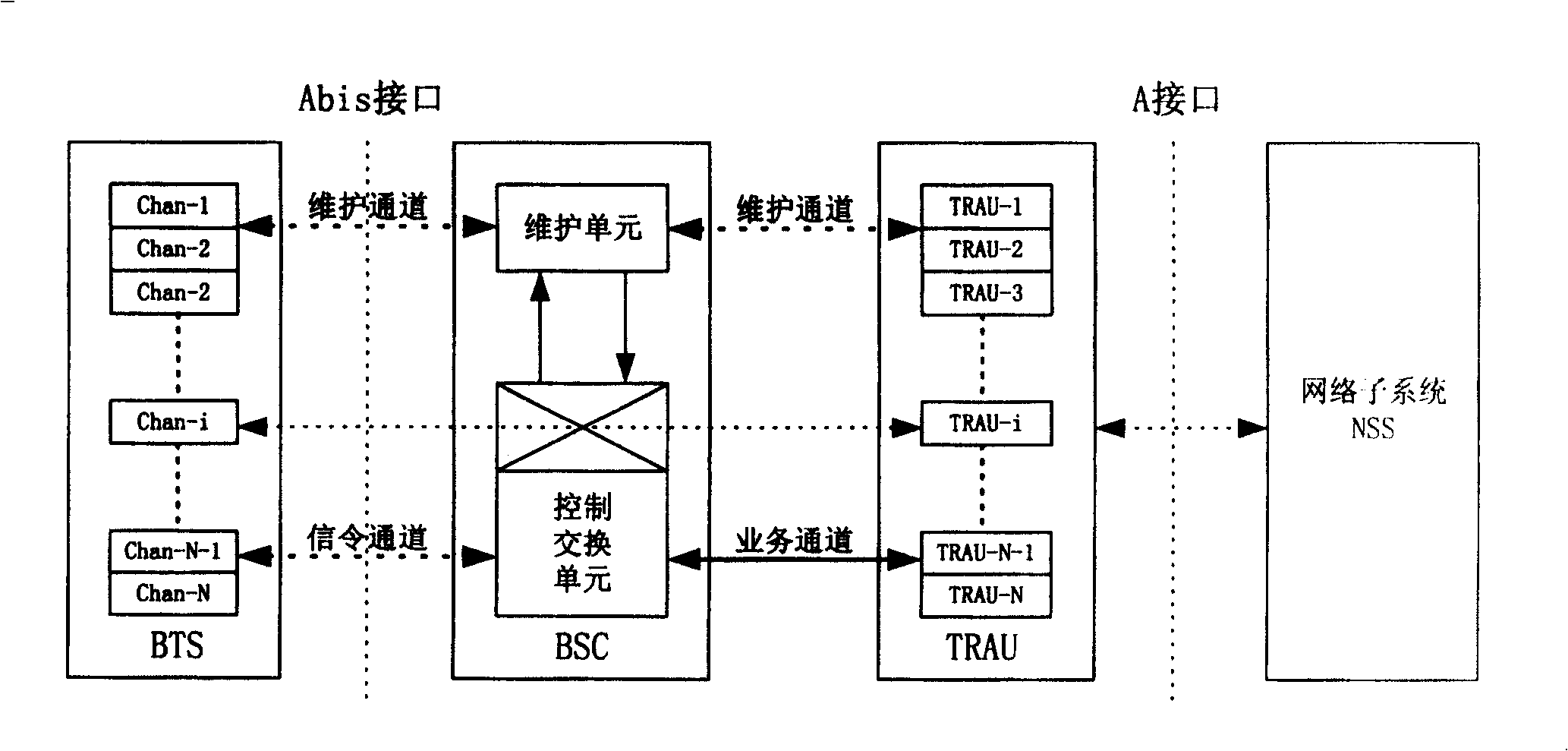
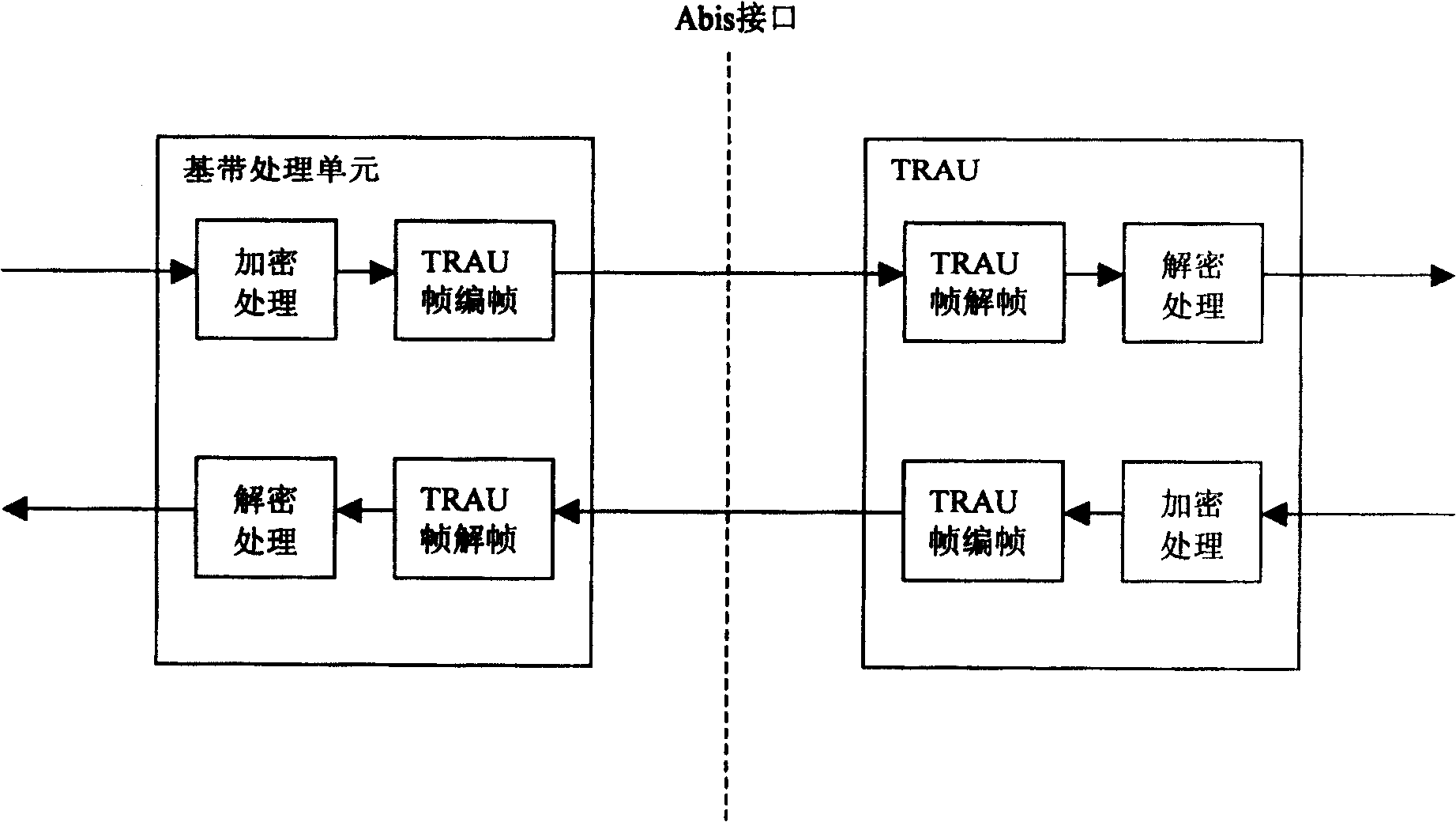
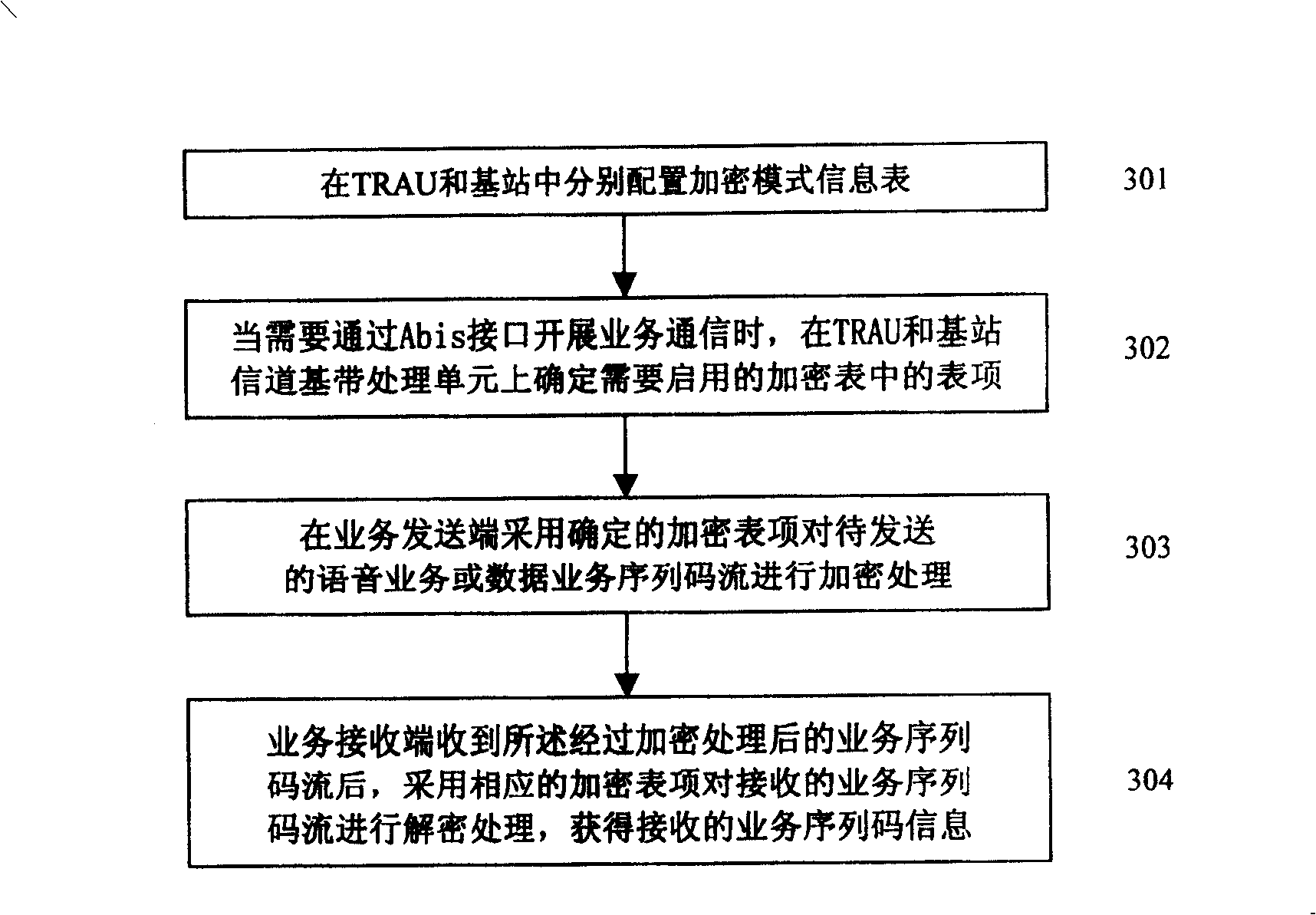
[0050] The core of the method of the present invention is to use a predetermined encryption mode on the TRAU and the base station channel baseband processing unit to encrypt the service flow to be transmitted, and to decrypt the received service flow to obtain the restored service flow . In this way, the voice or service data of the Abis interface of the digital trunking system based on the GSM system is encrypted, so as to effectively prevent the calls between trunking users in the trunking system from being monitored at the Abis interface
[0051] That is, in the present invention, when it is necessary to carry out voice or data service communication on the Abis interface, the corresponding encryption process is enabled, and the data carried by the TRAU frame transmitted between the specific TRAU and the specific base station channel baseband processing unit Encrypt so that the code stream of the voice service and data service transmitted on the Abis interface is an encrypte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com