Apparatus and method for implementing interaction between applied system and security chip
An application system and security chip technology, applied in the direction of secure communication devices, transmission systems, digital transmission systems, etc., can solve the problems that the device does not support remote access, does not support drive features, and secret information is no longer safe.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
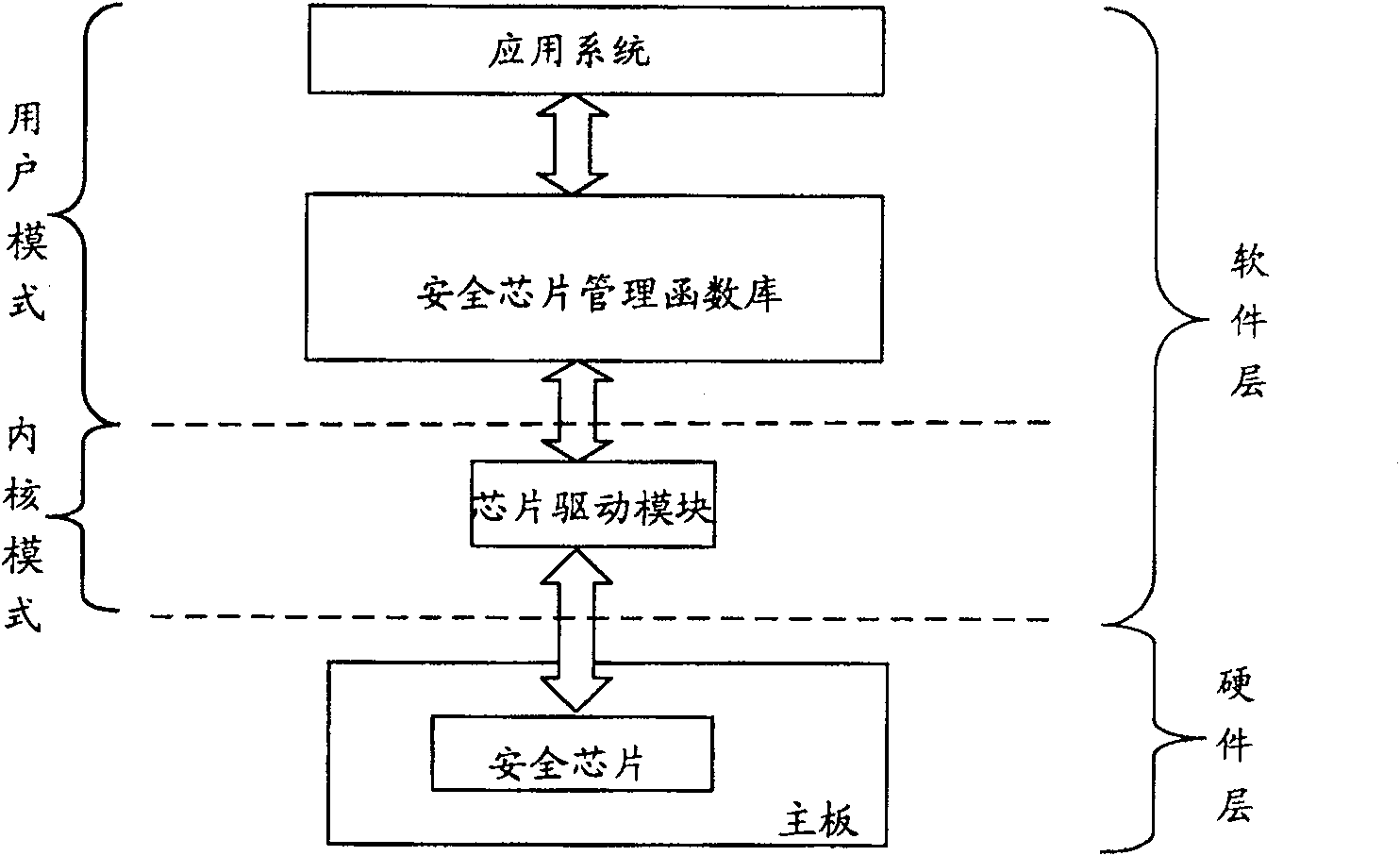
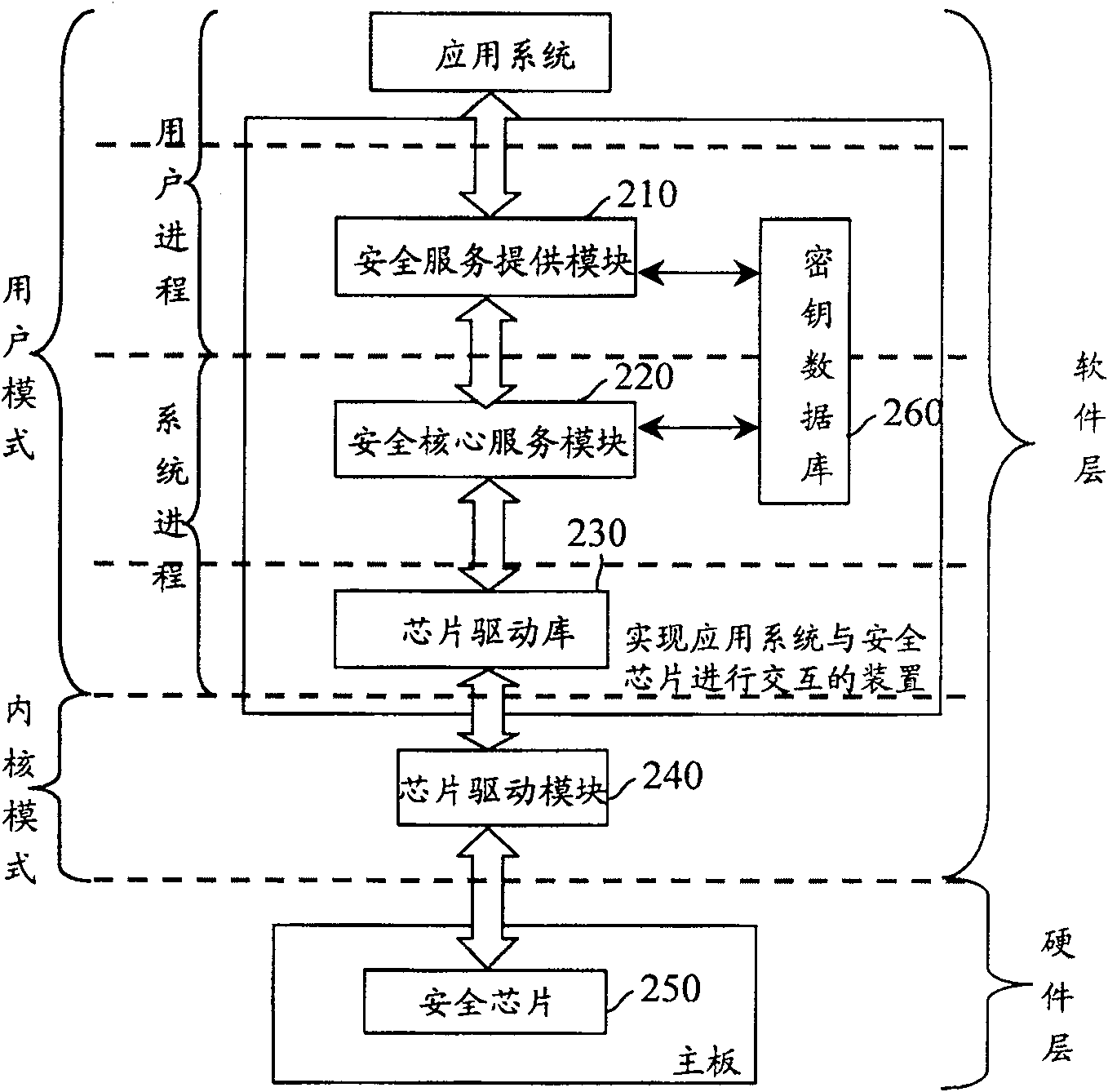
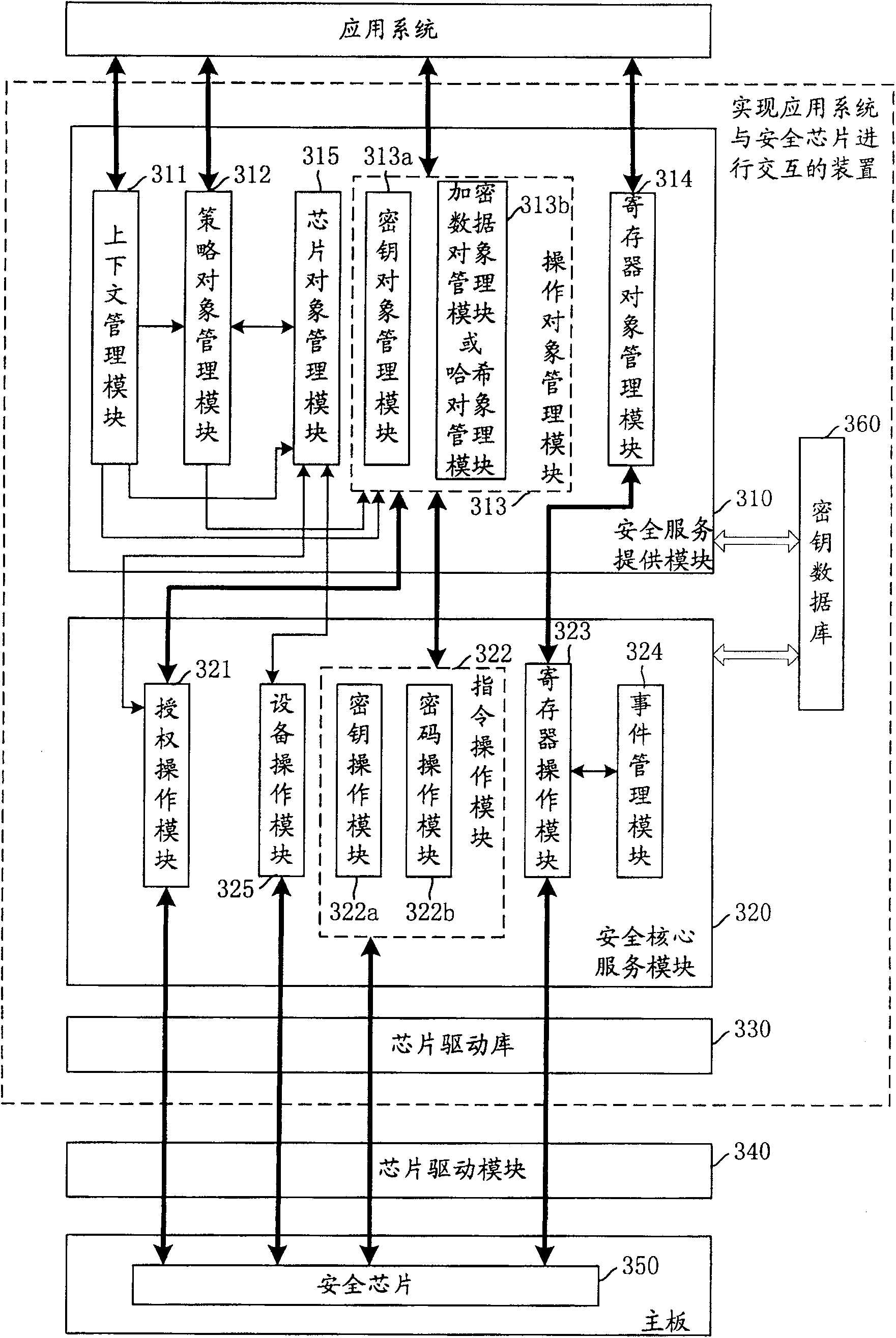
[0068] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0069] Usually, when the application system uses the security chip for the first time, the physical existence switch between the application system and the security chip is set to "on". In this state, the application system directly creates the information of the owner of the security chip and stores the root key. Both the security chip owner information and the storage root key are stored in the security chip, and then the physical presence switch will be set to the "off" state.
[0070] Moreover, when creating the owner of the security chip, it is necessary to further set the authorization information of the owner of the security chip and the authorization information of the root key for storing the root key. When the application system requires the security chip to execute important instructions, such as device management instructions, key management instr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com