Credible password module test case creation method and its test system
A test case generation and cryptographic module technology, applied in the computer field, can solve problems such as no method of test case, no system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
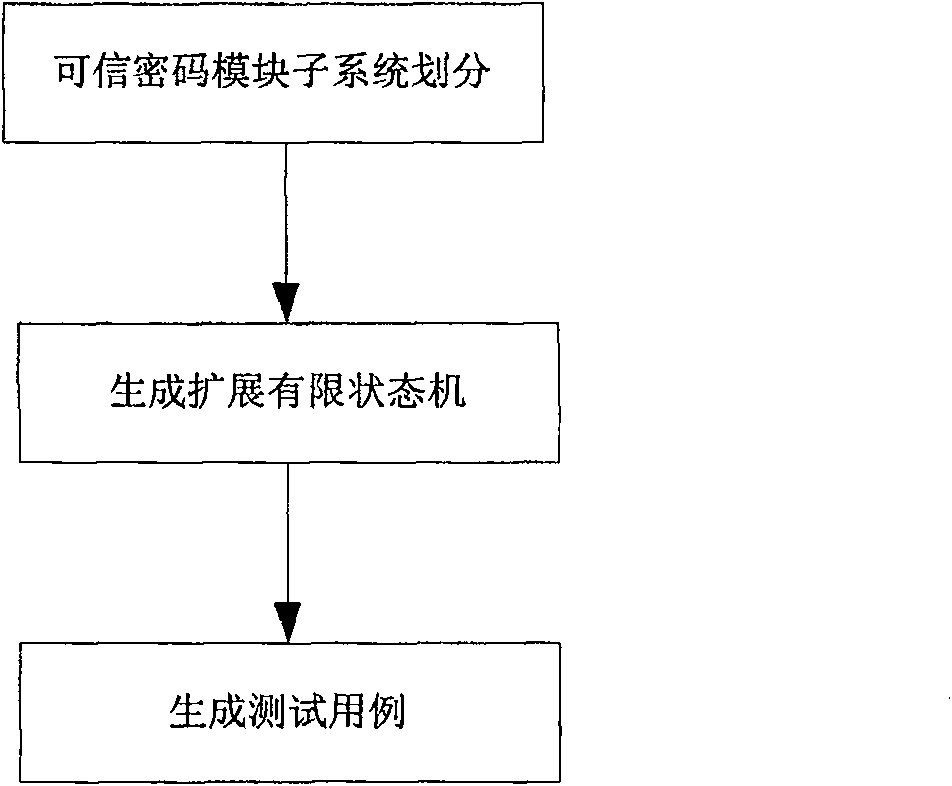
[0074] First, divide the subsystems of the trusted cryptographic module, and strictly divide them according to the functions realized by each subsystem, so that the dependence of each partitioned subsystem is low; here, the trusted cryptographic module can be divided into the following subsystems: cryptographic subsystem , TCM management subsystem, platform identity management subsystem, storage protection subsystem, identification and authentication subsystem, integrity protection subsystem, trusted path subsystem.
[0075] The dependencies between the various subsystems are as follows: Figure 8 As shown in , where the arrow points to indicate the dependency relationship, for example, the cryptosystem points to the integrity protection subsystem, indicating that the cryptosystem depends on the integrity protection subsystem.
[0076] Second...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com