Implementing authentication method and system
An authentication system and authentication information technology, applied in the direction of user identity/authority verification, etc., can solve the problems of user legitimacy verification, lack of user-to-network authentication capability, and inability to achieve two-way authentication between network and user.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
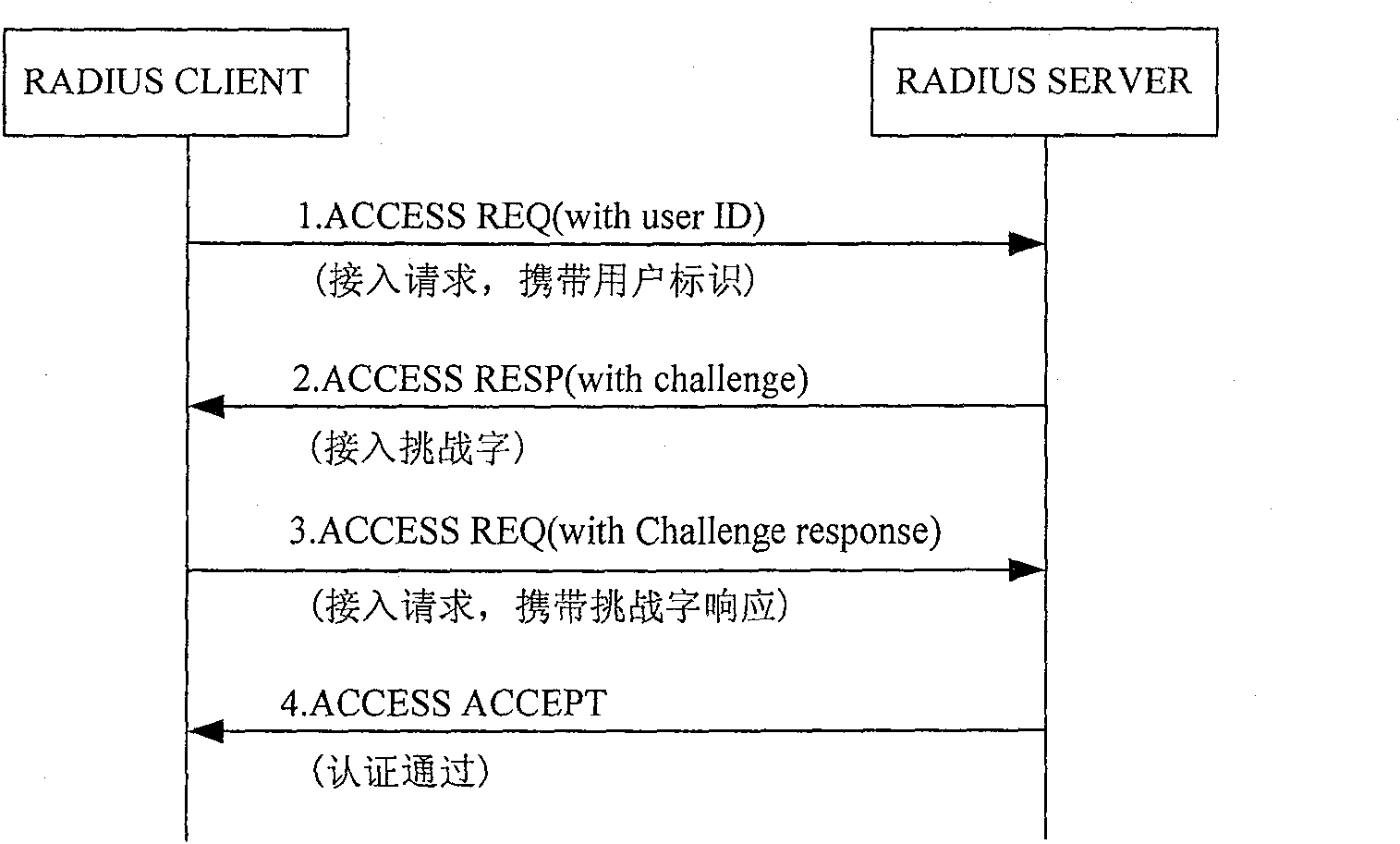
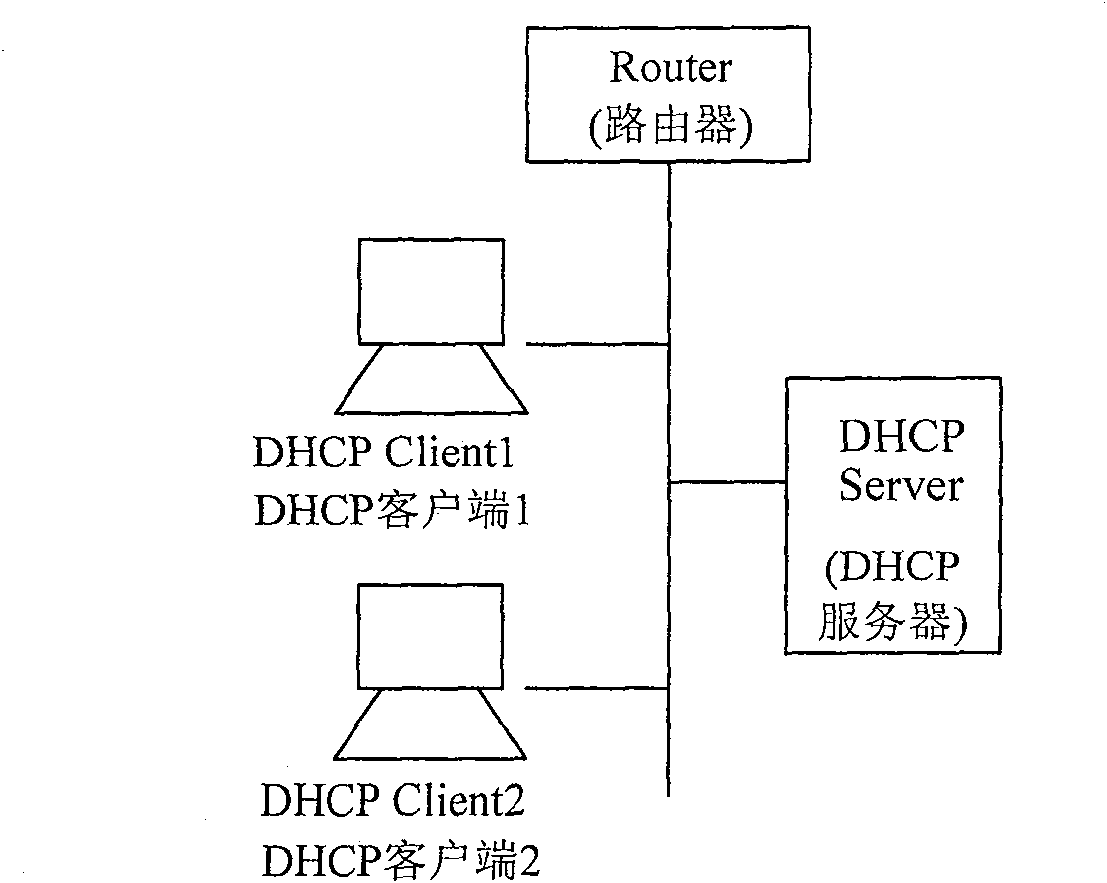
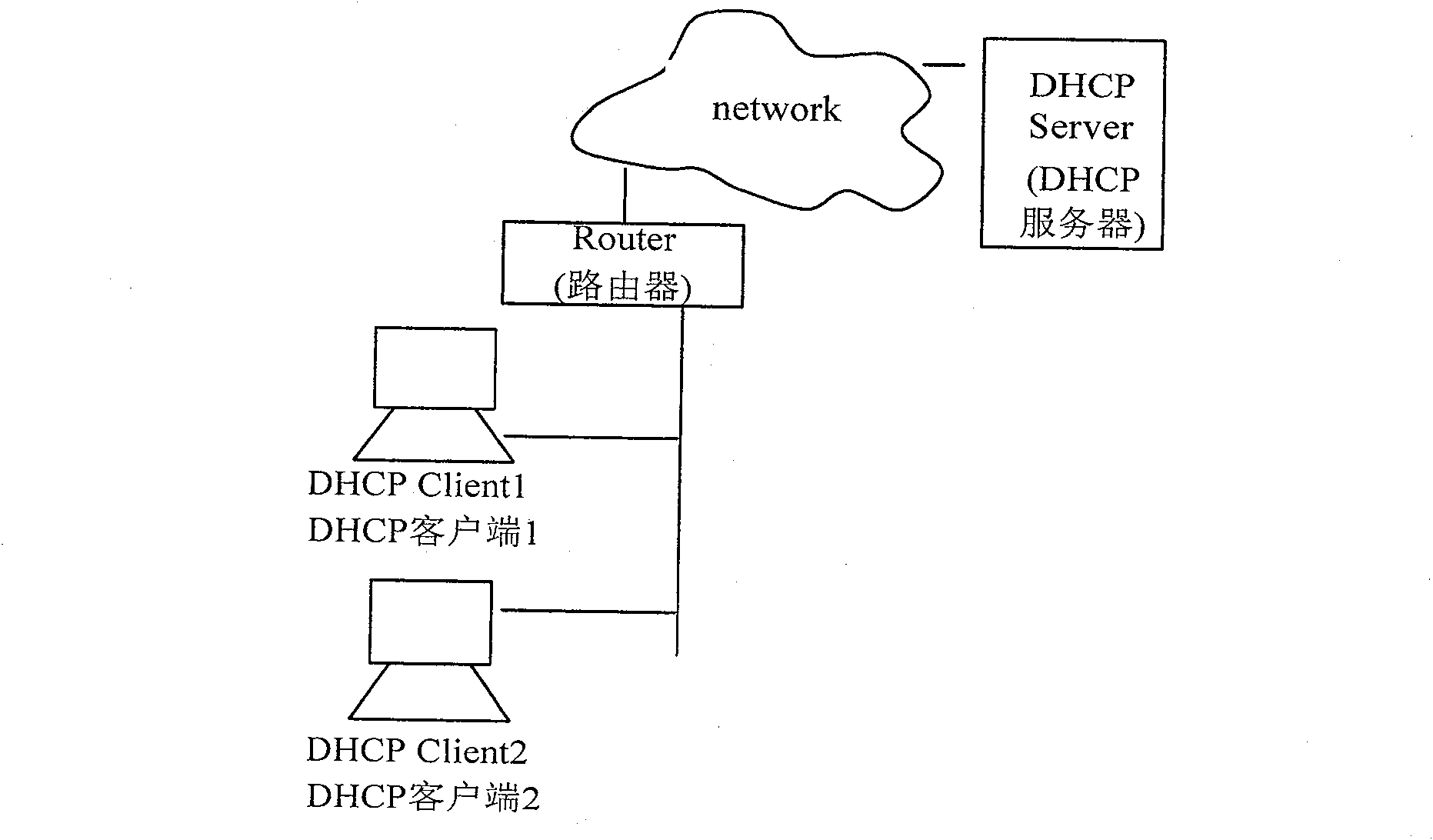
[0063] The present invention utilizes the DHCP authentication mechanism to solve the security problem and realize the authentication of the user to the network; at the same time, in order to solve the roaming problem, the shared key required by the DHCP authentication is used for the authentication of the user accessing the network, and the re-authentication is initiated through the DHCP network device, The DHCP mechanism can be effectively used to support re-authentication. At the same time, a cascading authentication relationship is formed between the authentication server-DHCP network equipment-DHCP CLIENT, and this relationship is used to complete the access authentication of the authentication server to the user. Because the present invention is based on the authentication of each user, the security is fully guaranteed.
[0064] The first embodiment provided by the present invention is the first method for realizing authentication. Its core is: after the DHCP network devi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com