Method, system and platform for securing safety of payment based on internet
A payment platform and payment security technology, applied in the payment system structure, transmission system, platform integrity maintenance and other directions, can solve problems such as unsatisfactory effect, weak security awareness, and inability to prevent Trojan programs, so as to inhibit theft of consumption and prevent The effect of stealing consumption and easy installation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
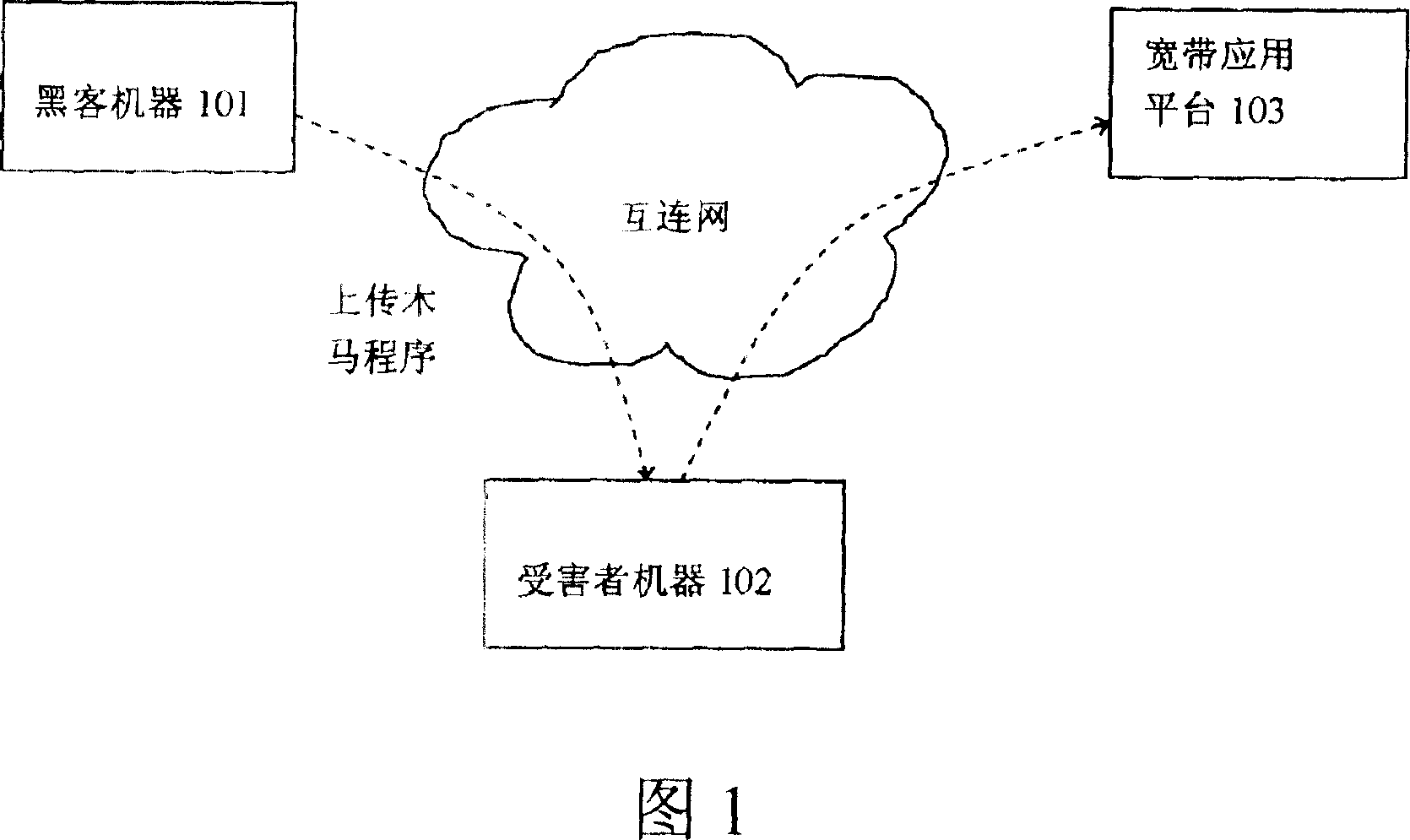
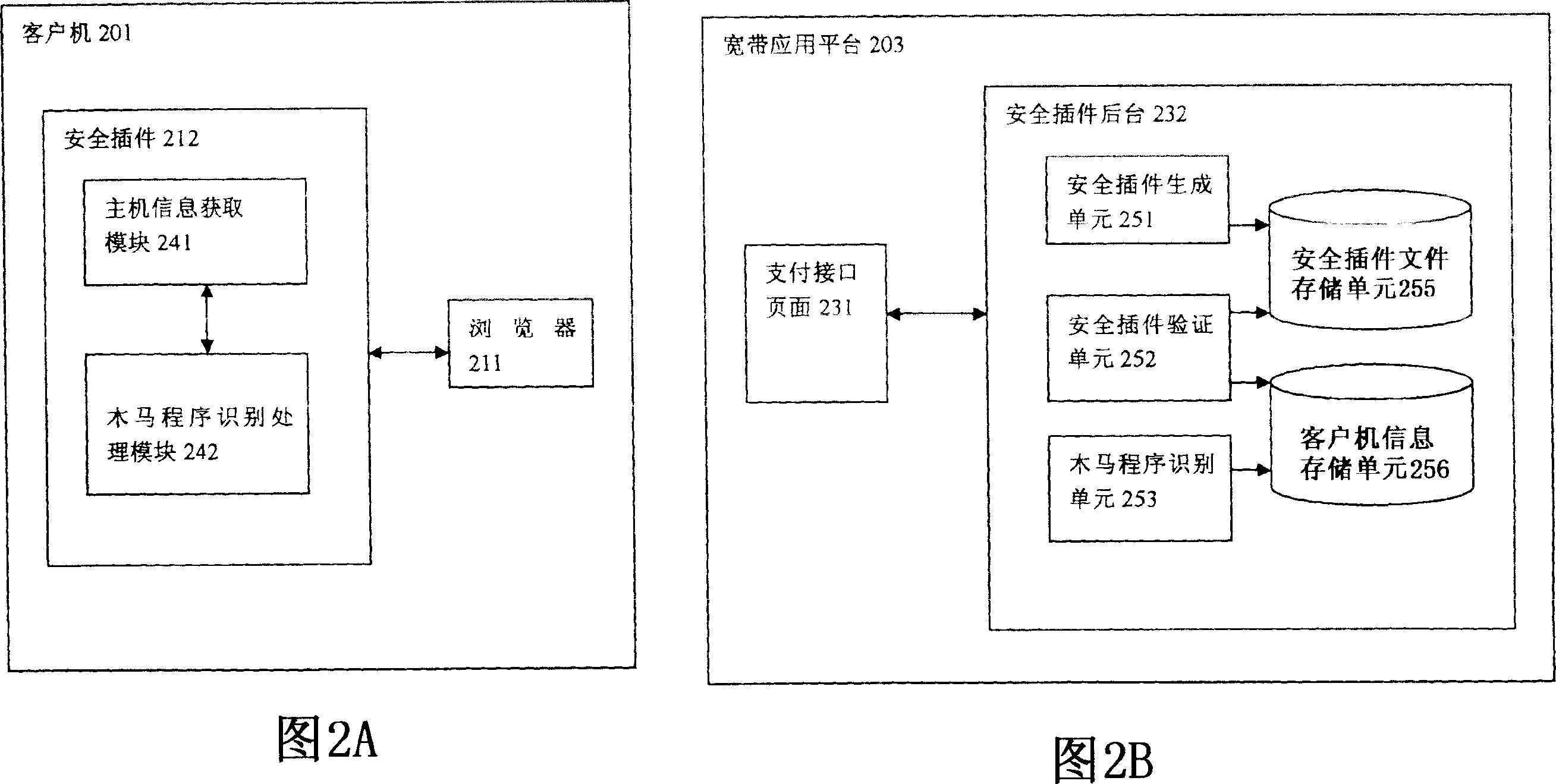
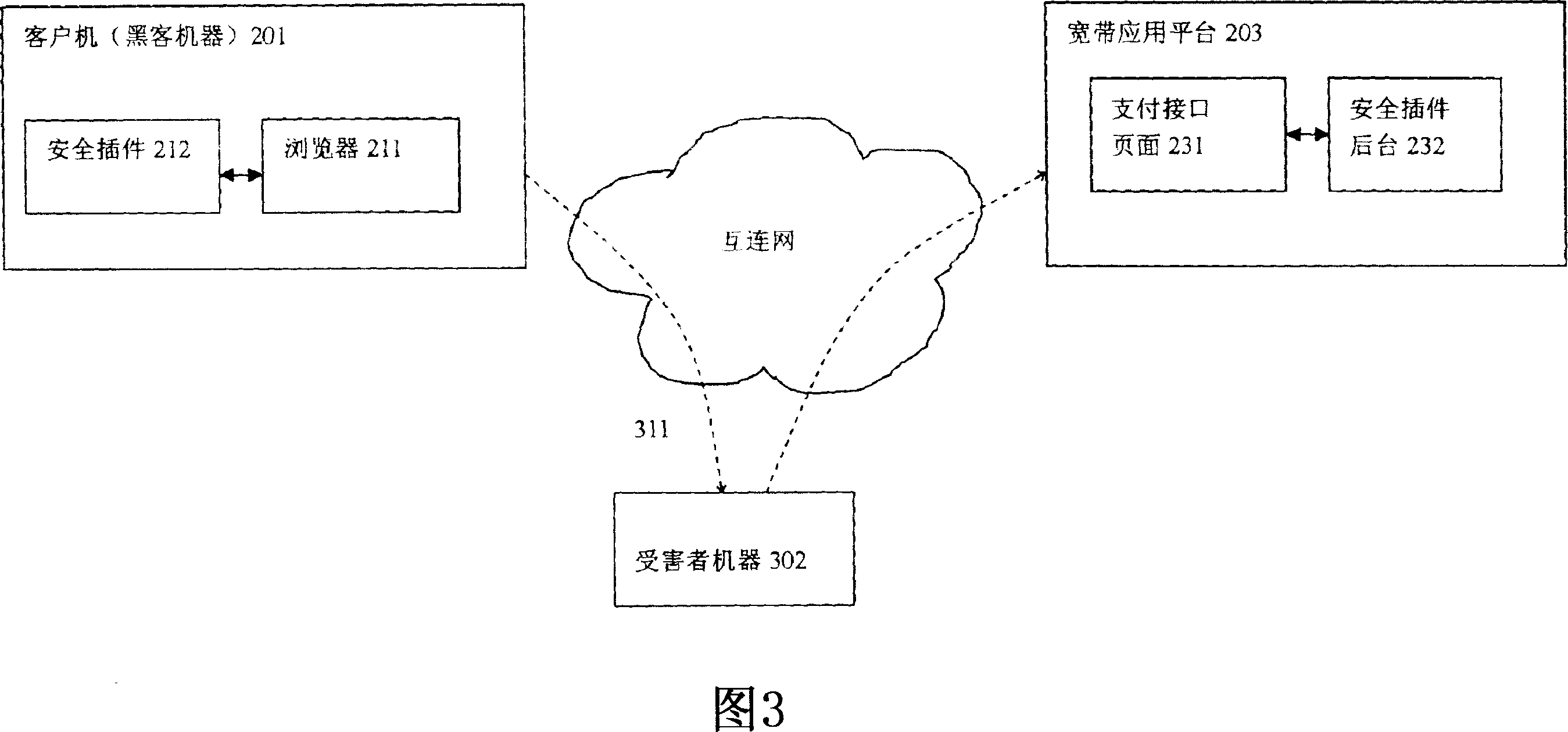
[0023] Fig. 2A and Fig. 2B respectively schematically show the block diagrams of the client side and the broadband application platform side of the payment system according to the present invention.
[0024] As shown in FIG. 2A, the client 201 includes a browser 211, such as Microsoft's IE browser, for communicating with the broadband application platform and downloading a security plug-in 212 from the platform. During the payment process, the security plug-in 212 detects and processes the Trojan horse program on the client 201 side through the interaction with the security plug-in background (to be described later) on the platform side. The security plug-in 212 includes the following components: a host information acquisition module 241 and a Trojan horse program identification processing module 242 . The functions of each component module and its submodules (not shown in the figure) of the security plug-in 212 will be described in more detail below.
[0025] As shown in FIG...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com