Safety telecommunication method
A communication method and technology of secure communication, which is applied in the direction of security device, wireless communication, radio/inductive link selection arrangement, etc., can solve problems such as being vulnerable to attacks, and achieve the effect of low cost, simple function, and improved reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
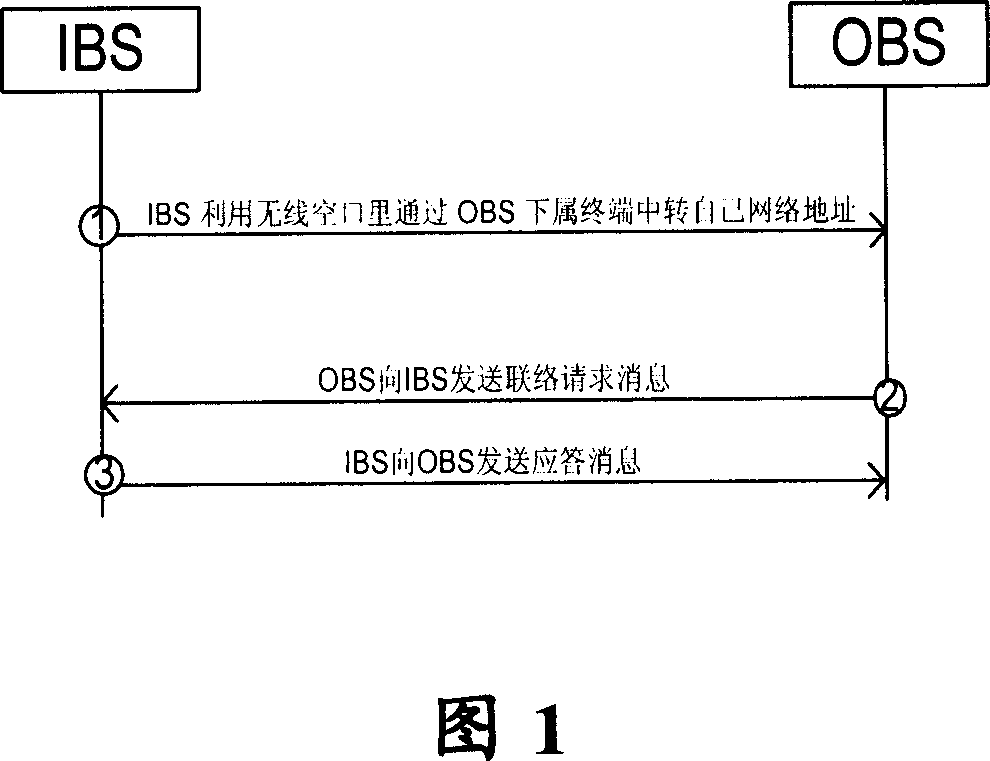
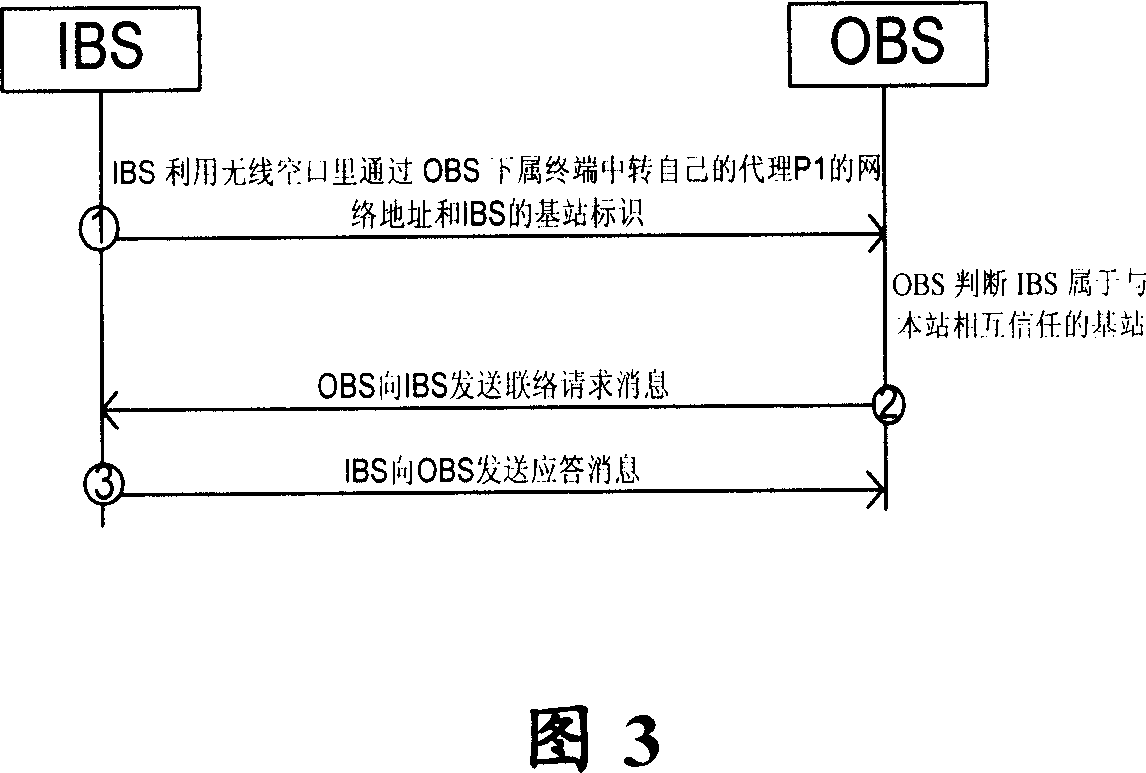
[0045] The present invention will now be explained in detail with reference to the drawings. In the present invention, the IBS does not broadcast the network address used by the base station's own service, but broadcasts the address of its coexistence agent and its own base station identification. The base station identifier here is any mark that can uniquely indicate the base station, for example, it can be a fixedly allocated base station identifier, it can also be the MAC address of the base station, or even the port number of the agent.
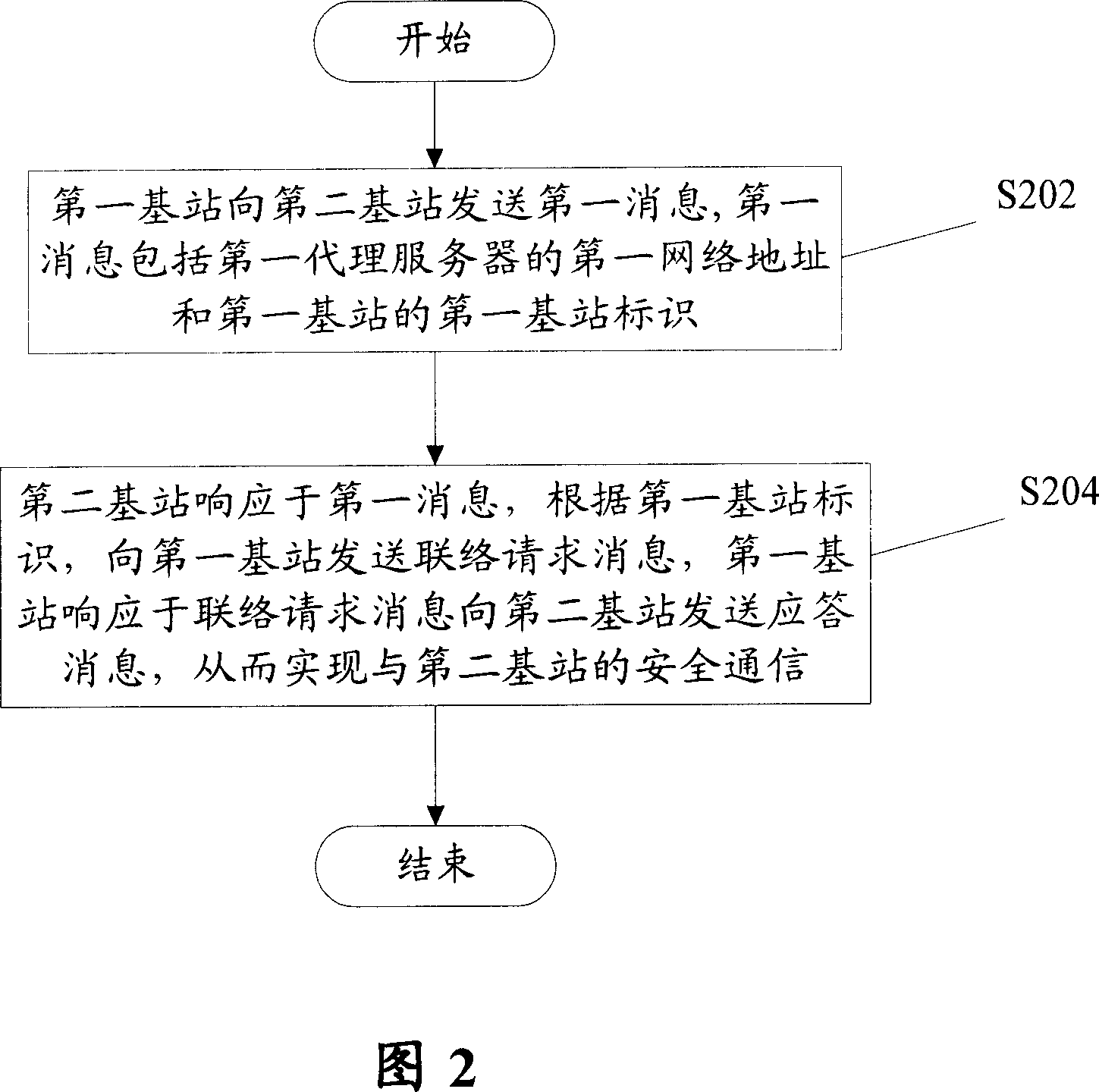
[0046] Fig. 2 shows a flowchart of a communication method according to an embodiment of the present invention. The communication method is used to realize secure communication between at least a first base station and a second base station. The first base station includes at least one first proxy server, and includes the following steps: S202, the first base station sends the The second base station sends a first message, where the first mess...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com