Active mode digital image content identification method based on wavelet and DCT dual domain
A digital image, active technology, applied in the direction of image coding, image data processing, image data processing, etc., can solve the problem that the complete identification method cannot be reached, and achieve the effect of ensuring invisibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
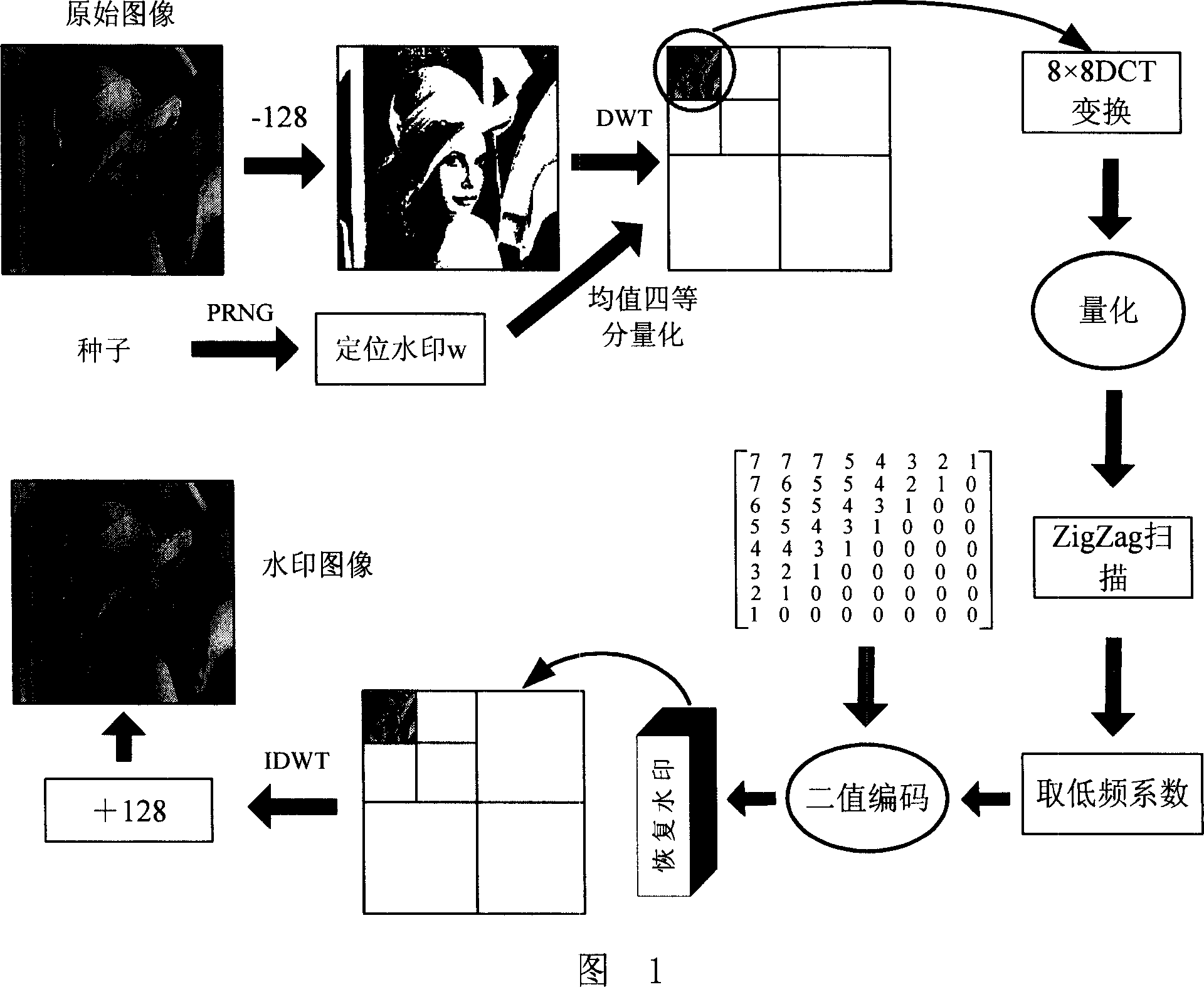
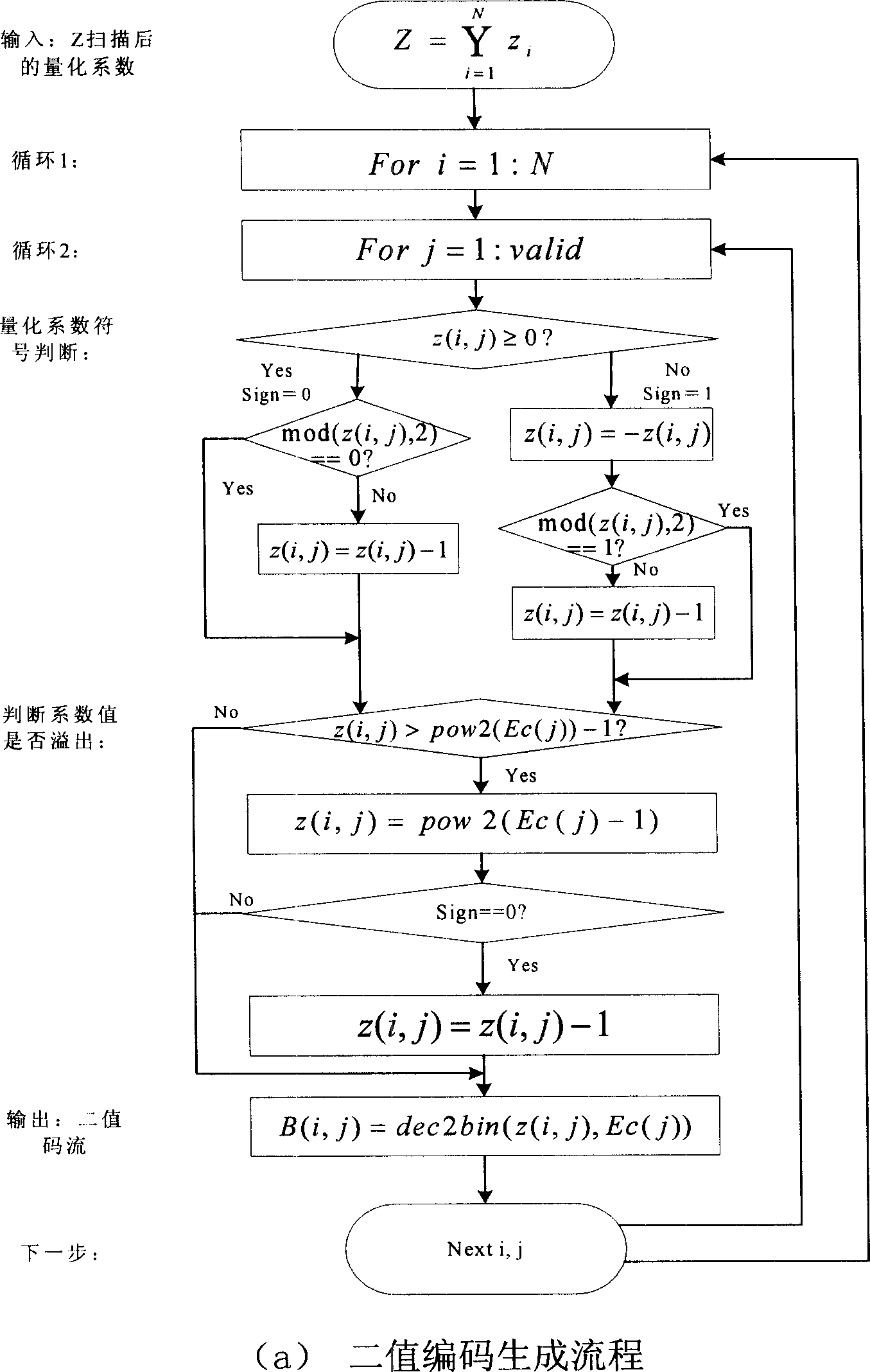
[0126] As shown in Figure 5: the wavelet transform used in the experiment is biorthogonal 9 / 7 wavelet. When embedding the positioning watermark, the number of wavelet coefficients for calculating the mean value is selected to be n=2×2. Both the positioning block and the restoration result are accurate to the order of 8×8. In binary coding, valid=11, that is, the first 11 coefficients after the Z scan are reserved for the DCT quantized coefficients, so that each 8×8 data block is just represented by 64 bits, and the L matrix used to encode the quantized coefficients is :
[0127] L = 7 7 7 5 4 3 2 1 7 ...
Embodiment 2
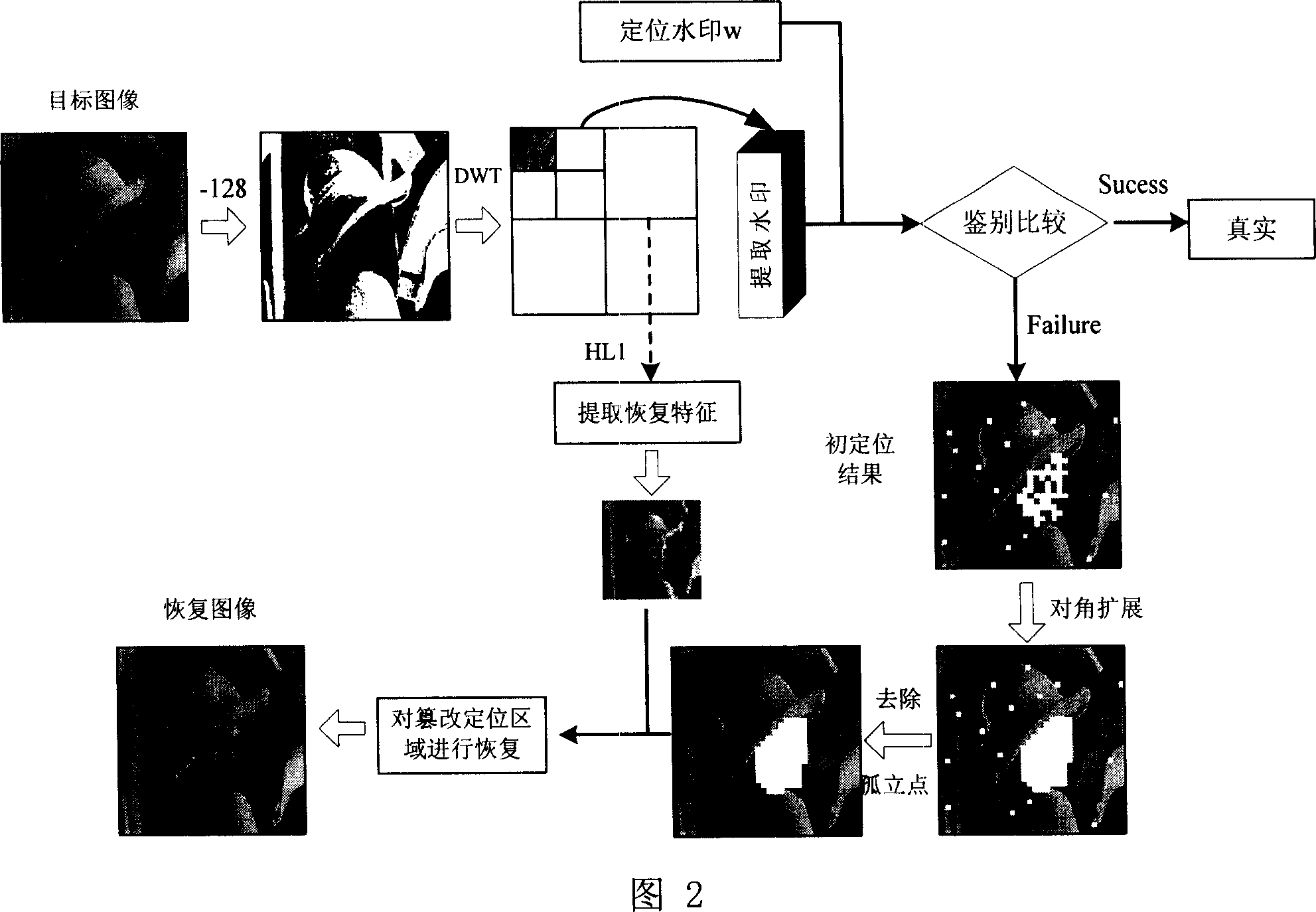
[0136] The malicious tampering mentioned in the present invention mainly refers to that the image has been cut and replaced. As shown in Figure 8, where (a) is the original lena image of 256*256*8; (b) is the watermark image, PSNR=36.18db; (c) is the watermark image after lena’s face has been maliciously tampered with, the following will Use this falsified image to test the image identification method of the present invention.
[0137] The 8(c) image is identified, and the identification result is shown in Figure 9, where (a) is the result of positioning using the positioning watermark embedded in HL2; (b) is positioning using the positioning watermark embedded in LH2 Results; (c) is the initial positioning result of the tampered image formed by merging the positioning results of (a) and (b). It can be seen from (c) that the positioning result is still not good at this time, so the diagonal The expansion operation is very necessary; (d) is the result of one diagonal expansion...
Embodiment 3
[0140] In the following, malicious tampering and accidental distortion are applied to the watermark image at the same time, the purpose is to test whether the authentication method of the present invention can tolerate accidental distortion and detect malicious tampering at the same time. Figure 11(a) is the original sailboat image; (b) is the sailboat watermark image, with a PSNR of 36.02db; (c) is the copy of the boat in the sailboat watermark image, and the scene around the tampered boat is replaced by the surrounding water , and then JPEG compression with an image quality of 60 was performed, and the identification result was that the image suffered malicious tampering and accidental distortion at the same time, and then the positioning operation was performed; (d) is the result of positioning through the positioning watermark embedded in HL2; (e) is the result of positioning through The positioning result of the positioning watermark embedded in LH2; (f) is the initial pos...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com