Safety certifying method and its system for facing signature data
A technology for security authentication and signature data, applied in the field of information security, it can solve the problems of inability to simulate or tamper with the transaction content of the authenticated image, and without authentication image security authentication, and achieve the effect of easy and rapid implementation and application, low cost and low complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
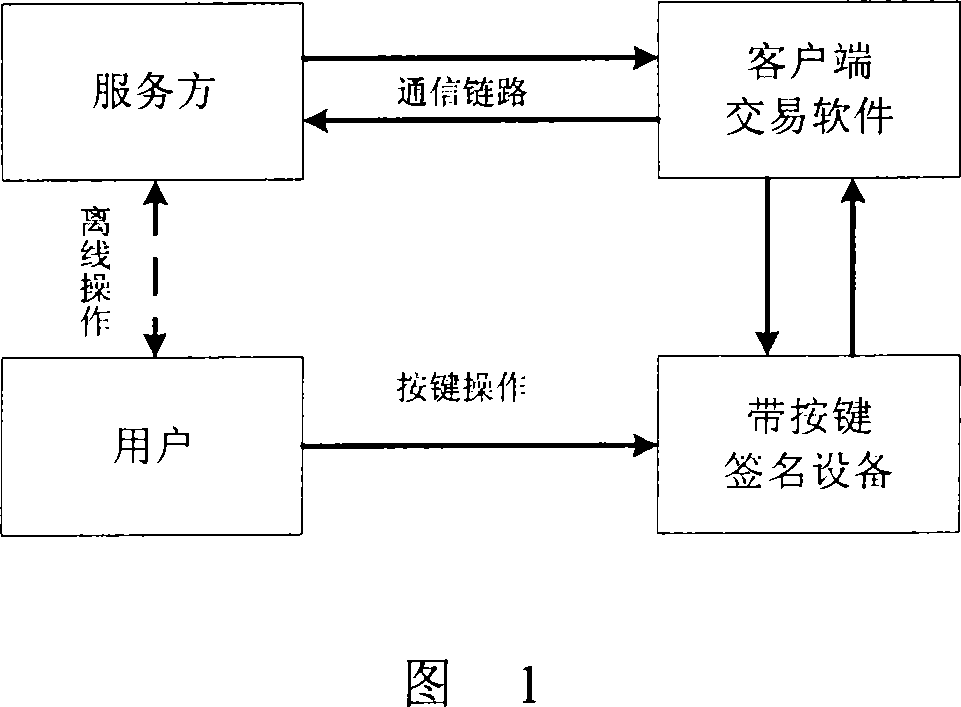
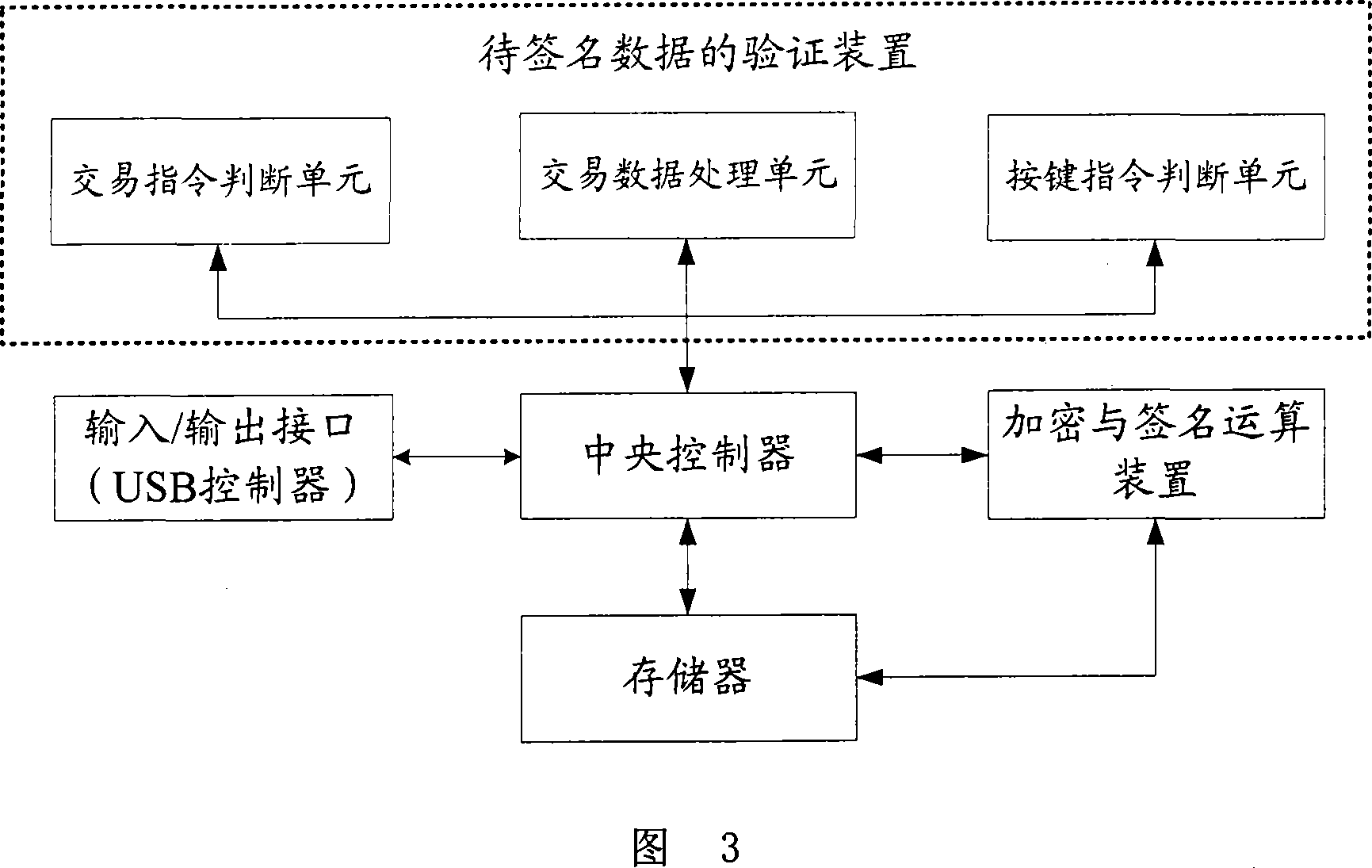
[0035] The authentication picture generated by physical authentication and CAPTCHA technology is combined for security authentication, and the picture containing transaction content generated by CAPTCHA technology is required to meet: 1. Whether the picture content passes the verification must be controlled by the user, and the judgment result of whether it passes, It cannot be input on the user's computer; 2. If the picture is forged by the attacker, the user can recognize it immediately; 3. The picture is difficult to tamper with, and if it is tampered with, the user should be able to recognize it immediately.
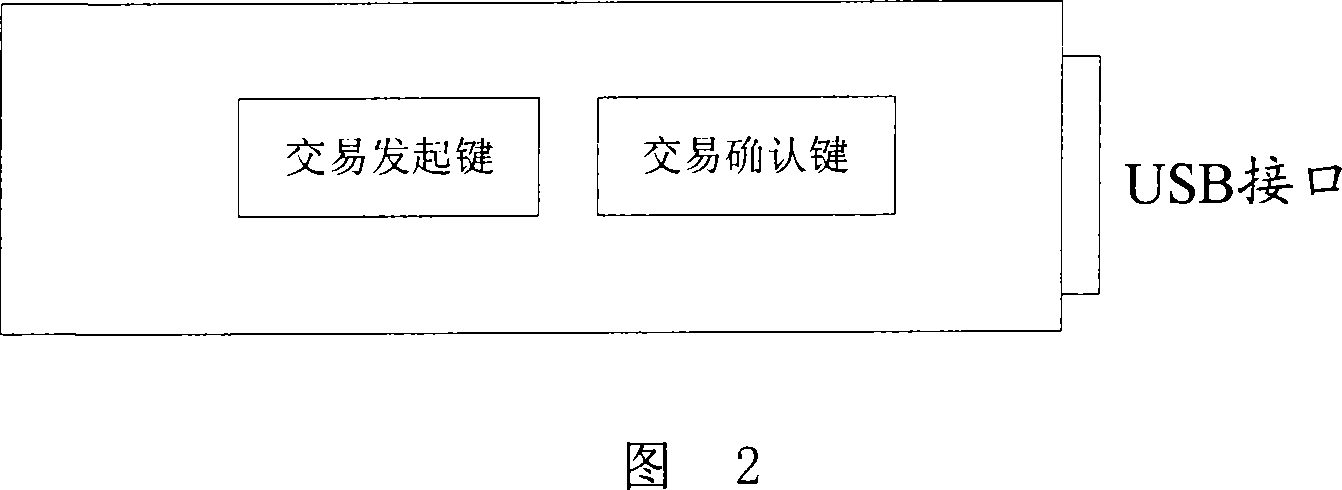
[0036]Referring to the Chinese invention patent application No. 200610113569.4 "Method for Realizing Data Interaction Between Digital Signature Device and Its Peer Device" previously applied by the applicant, the digital signature device USB Key with buttons and operation control list technology can satisfy The first requirement, because the initiation and confirmatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com